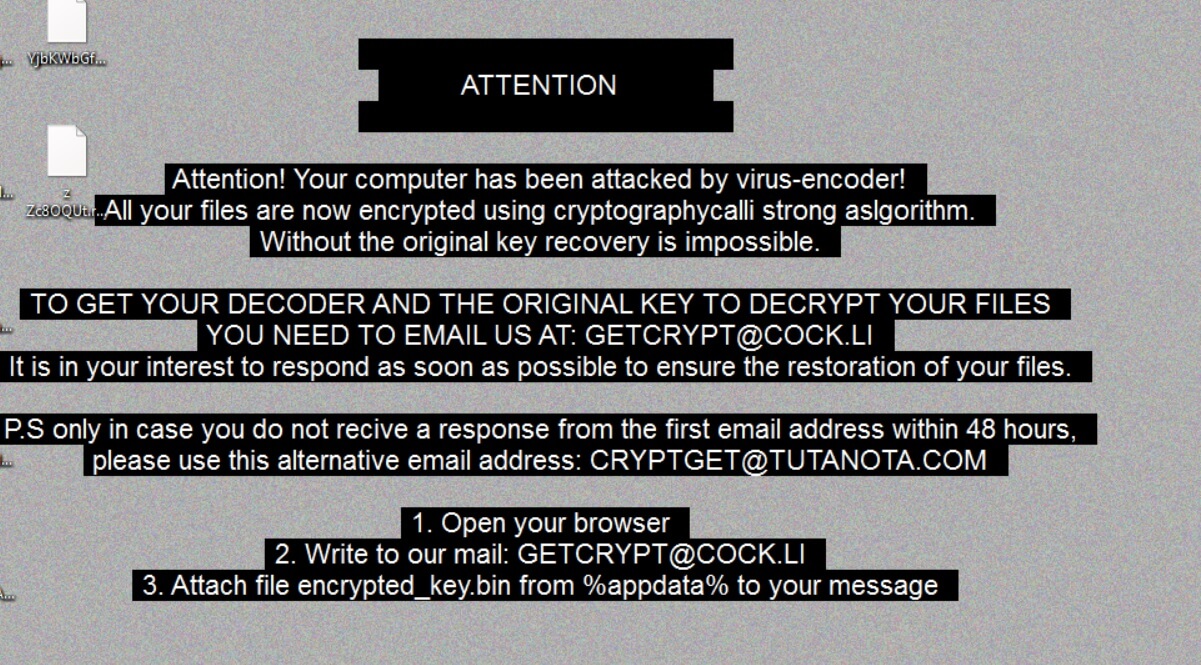
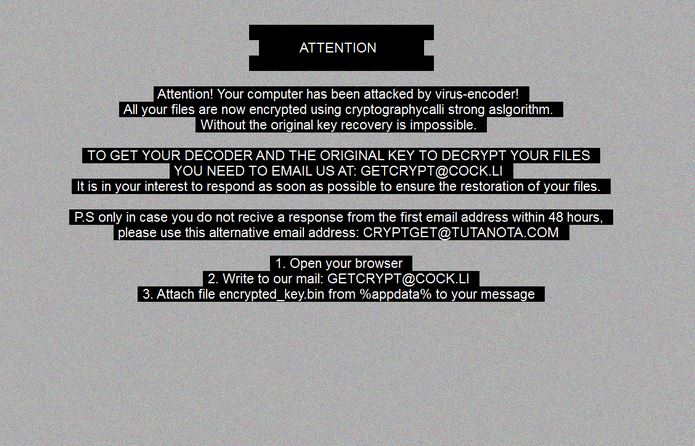
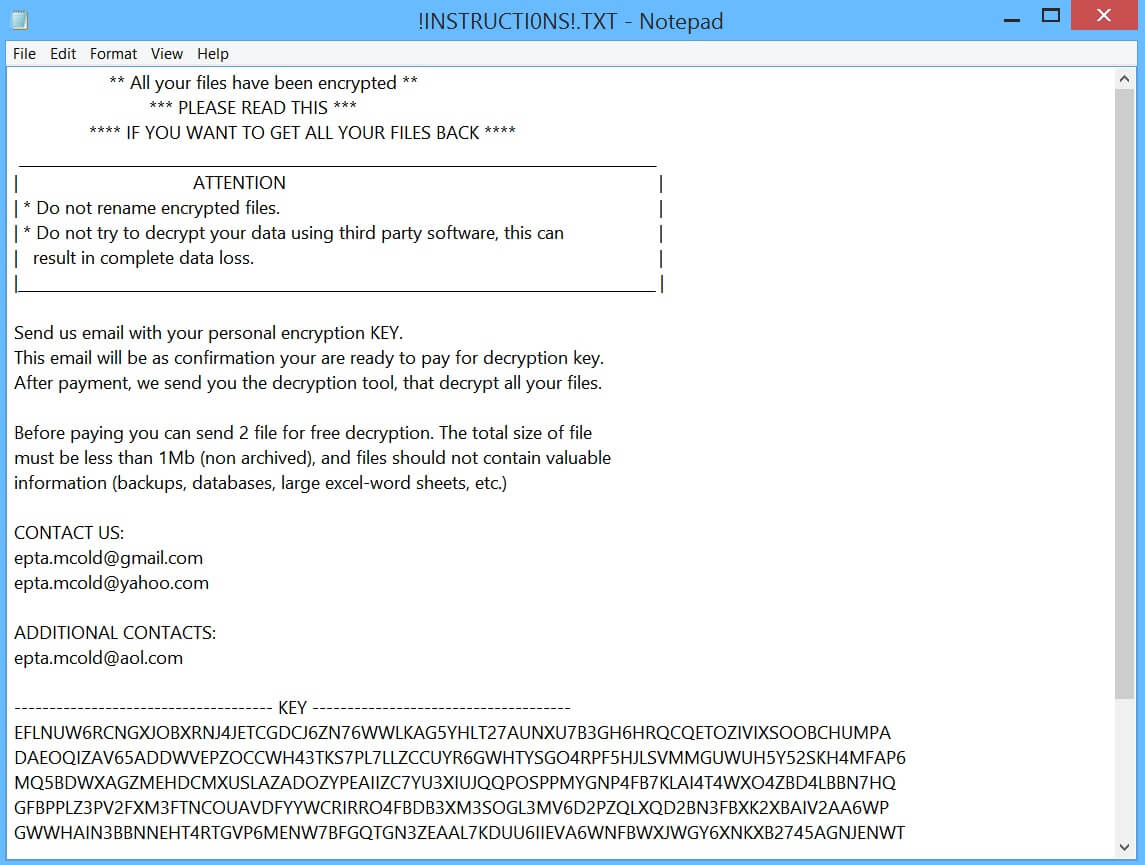
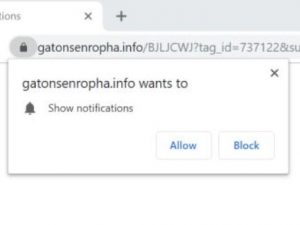
CVE-2019-8541: SensorID Attack Technique Overcomes Android and iOS Security
Criminals have devised a new malware tactic which is known as the SensorID attack and it is capable of overcoming the security of Android and iOS devices. It is designed to track users by abusing the sensors of these devices.…