![Remove Everbe Virus – Restore .[thunderhelp@airmail.cc].thunder Files](https://cdn.sensorstechforum.com/wp-content/uploads/2018/07/stf-everbe-ransomware-thunderhelp-airmail-thunder-extension-virus-how-to-remove.png)
Remove Everbe Virus – Restore .[thunderhelp@airmail.cc].thunder Files
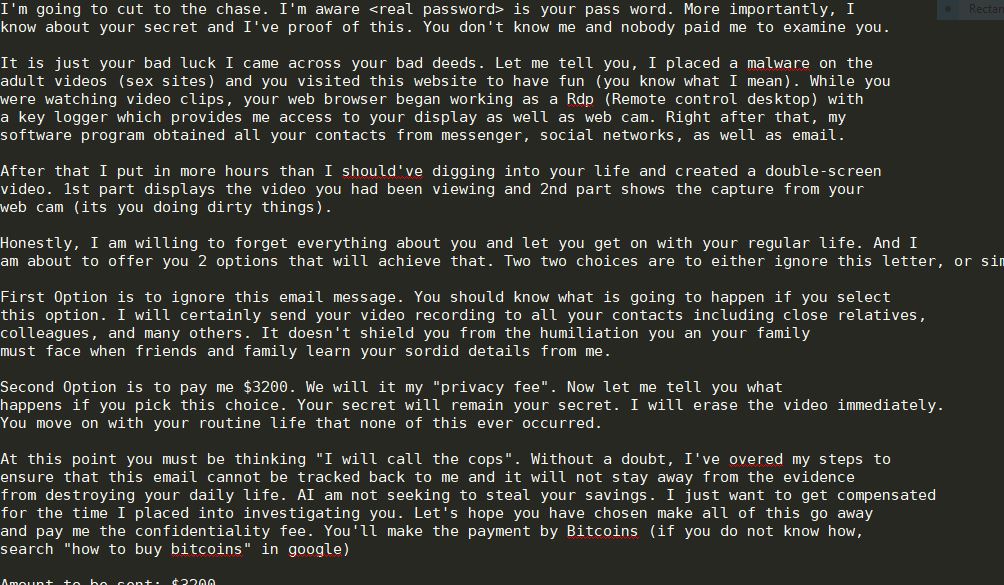
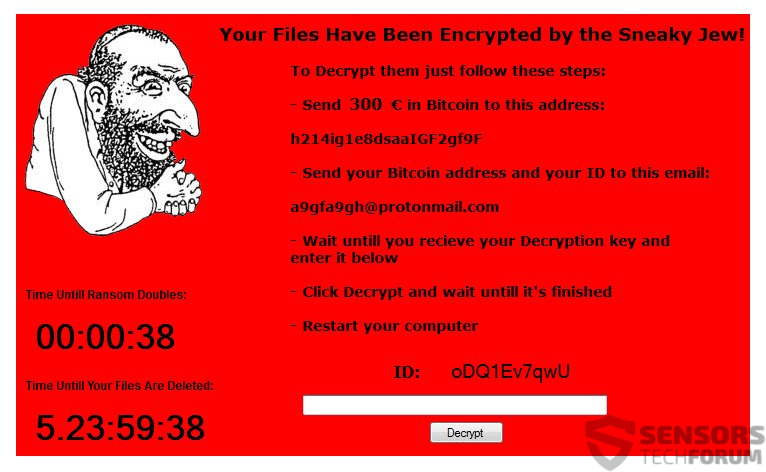
This article will aid you to remove Everbe ransomware effectively. Follow the ransomware removal instructions provided at the end of the article. Everbe is a virus that encrypts your files and demands money as a ransom to get your files…