 Cyber-criminals are continuing their “raids” on the blockchain and this time they target Nodes which are exposed and based on the Ethereum blockchain.
Cyber-criminals are continuing their “raids” on the blockchain and this time they target Nodes which are exposed and based on the Ethereum blockchain.
Researchers by Qihoo 360 have previously discovered a flaw back in March which included using an unsecure port to take control of non properly secure Ethereum nodes by using a transaction and a malicious JavaScript code embedded within it to take control of the Nodes. Back in March, hackers were able to steal almost 4 Ethers (Tokens of the Ethereum Cryptocurrency), which should have raised awareness to the team behind the platform and all of the ERC-20 tokens out there. But with no effect, since researchers have recently found out that cyber-criminals were successfully able to steal 38,642 Ethers, which now ammount ot around $20,5 million by hijacking ETH wallets of users who have installed clients on their devices with an open 8545 port on the Ethereum client, called Geth.
Geth is likely the most popular Ethereum client so far and it is used to run Ethereum nodes and enabling the Ethereum JSON interface, allowing remote access to the blockchain network and it’s functions. This basically means that via this client you can manage and see different transactions. However, while the researchers were browsing, they have seen that almost 40 thousand Ethers were credited to the following Ethereum wallet as reported by The Hacker News:
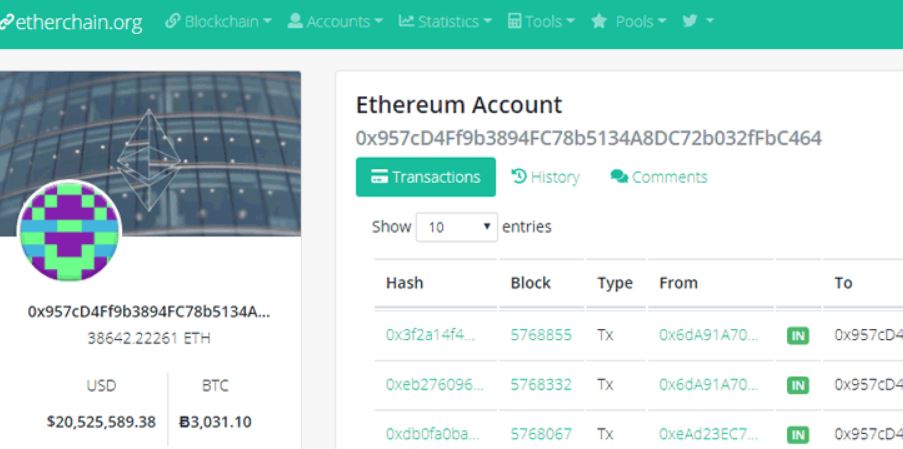
And not only this, but reports related to the same very address appeared on a lot of forums with users having their funds missing as a result of theft and the reports were coming from usrs who have left their JSON-RPC interface on computers with enabled internet connections.
Researchers have warned users that the hackers are heavily scanning the internet connection for unsecure JSON-RPC types of interfaces in order to obtain funds from crypto wallets. If you are using the Geth client on your local computer, reccomendations are to implement all of the security authorization measures and if you are running some type of remote protocol to strengthen it’s validation plus add a whitelist where possible.
Not The First Problem With Ethereum
Over time, the Ethereum network has also seen a lot of other situations and incidents even though as we predicted, it has become the next big cryptocurrency. It is likely just that fact that has resulted in Ethereum to e the target of so many hackers out there. But with several bugs already taken place on the Ethereum’s blockchain, like the $170 million Ethereum bug which resulted in a lot of money to be lost in a matter of minutes. And this is just because there are not strong enough measures to focus on security of crypto, which does hint that it still has a long way to go and Ethereum sure has a lot of work to do as well.


