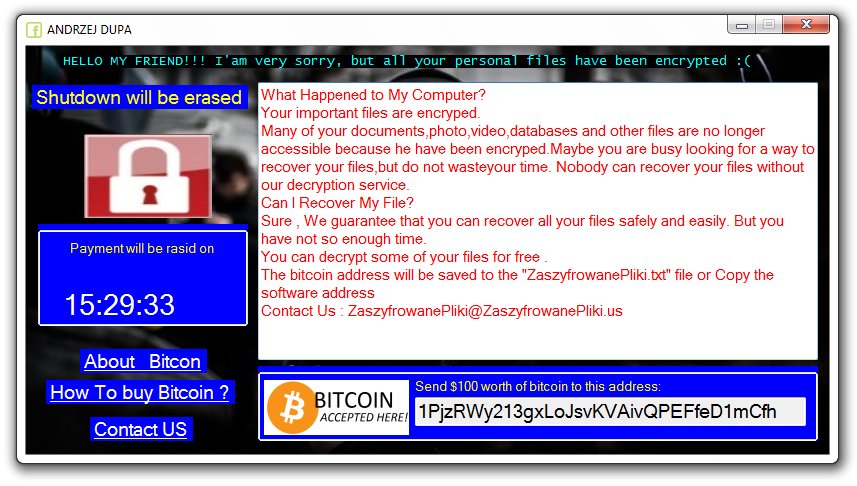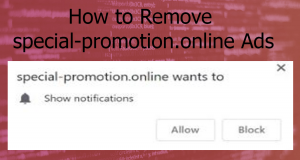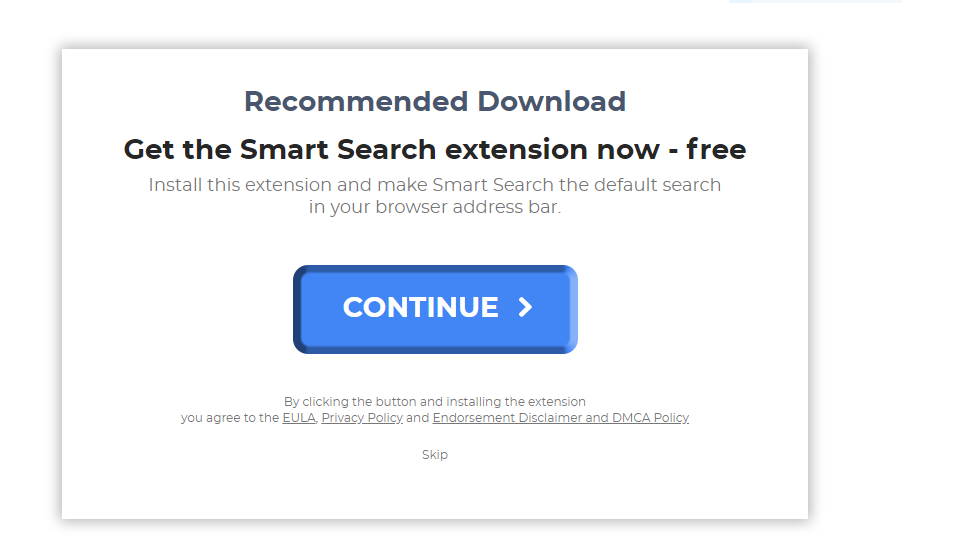
Butler Miner Coin Miner Trojan – How to Remove It
What Is Butler Miner Coin Miner Trojan? This article has been created with the purpose to explain what is the Butler Miner Trojan horse and how to remove this malware from your computer plus how to stop it from mining…