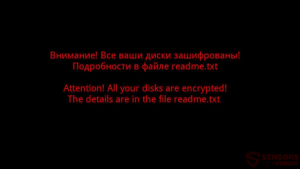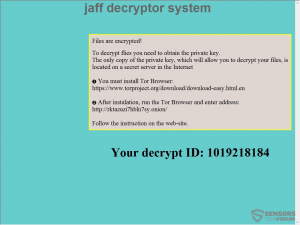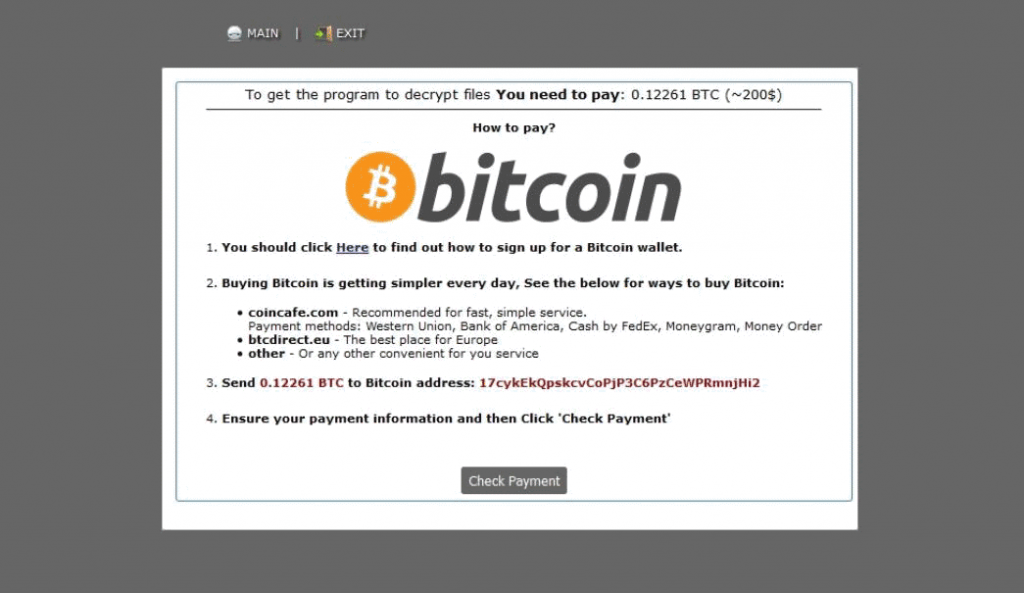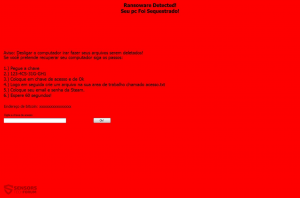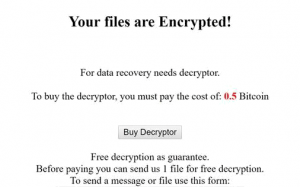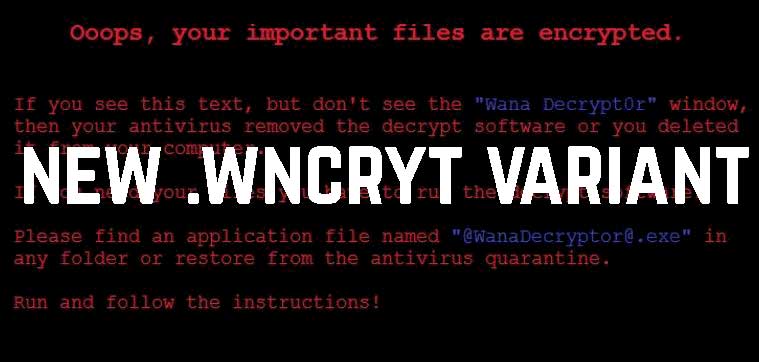
.WNCRYT (Wana Decrypt0r 2.0) File Virus (Restore Files)
NEW UPDATE MAY 2017 This article is created to help you cope with the latest Wana Decrypt0r update. It will show how to remove the .WNCRYT file virus and restore files encrypted by this threat. The greatest ransomware threat seen…