Remove Searchgst.com Redirect
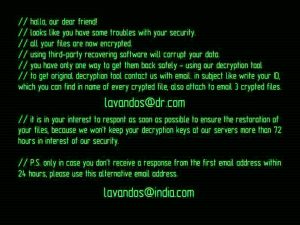
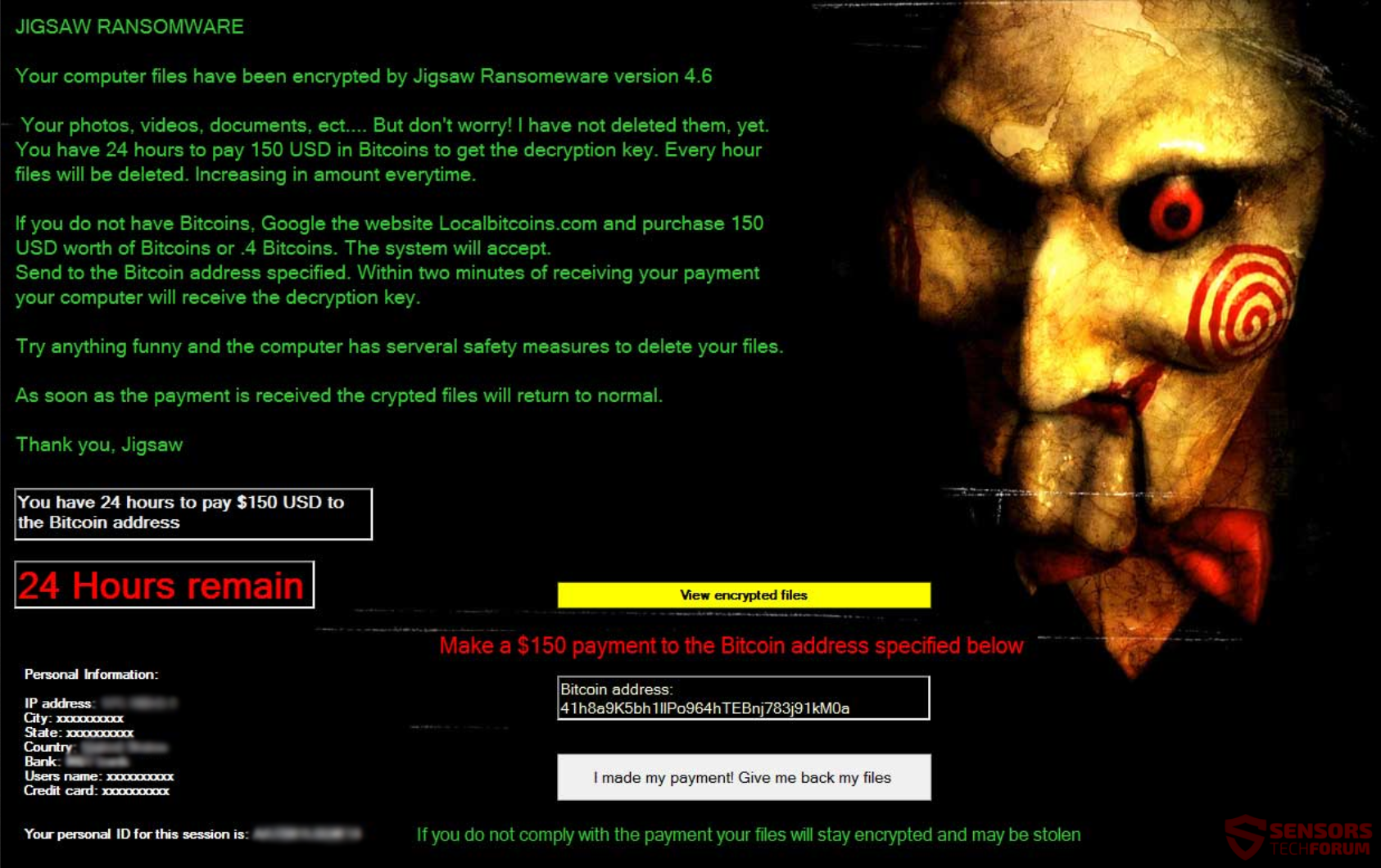
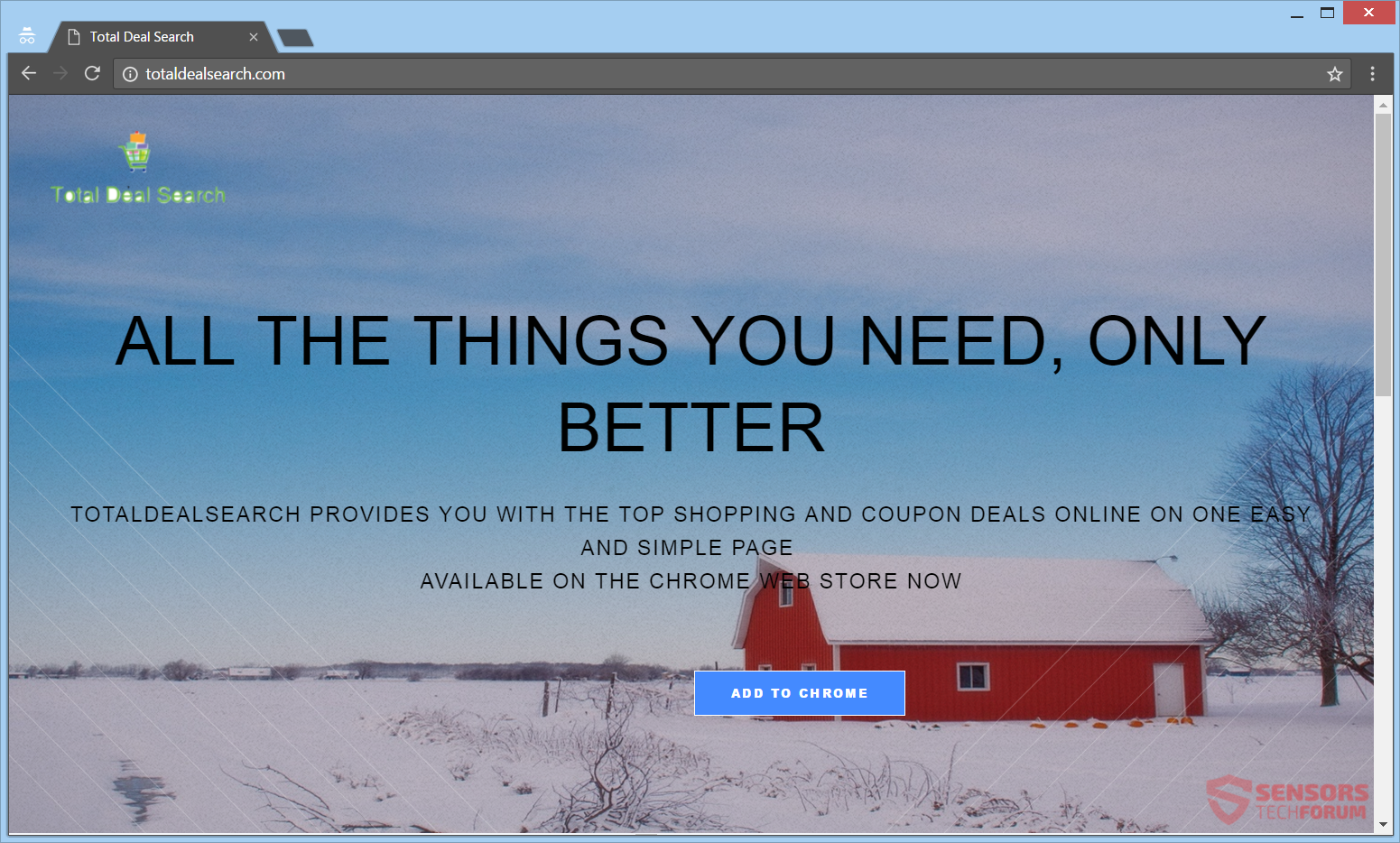
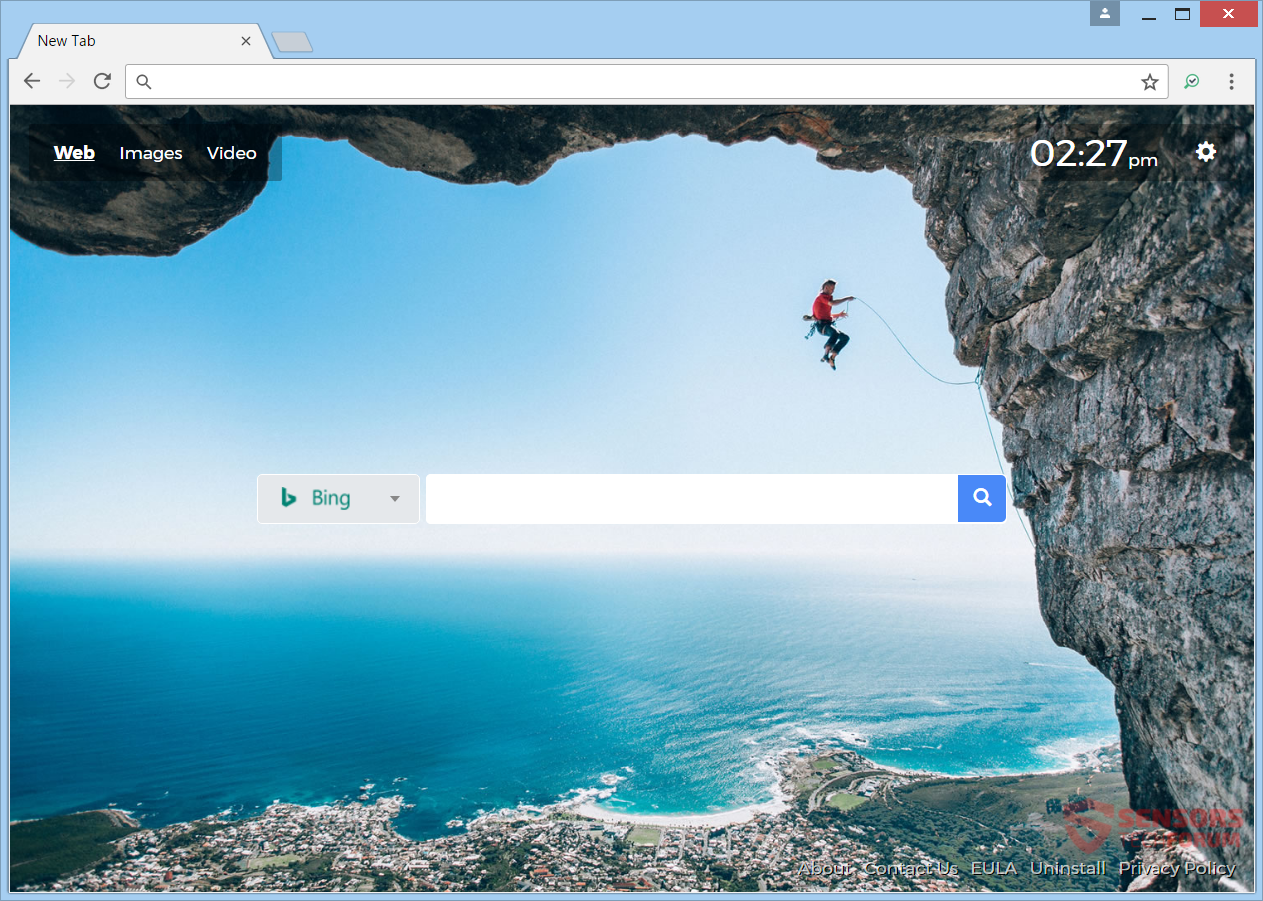
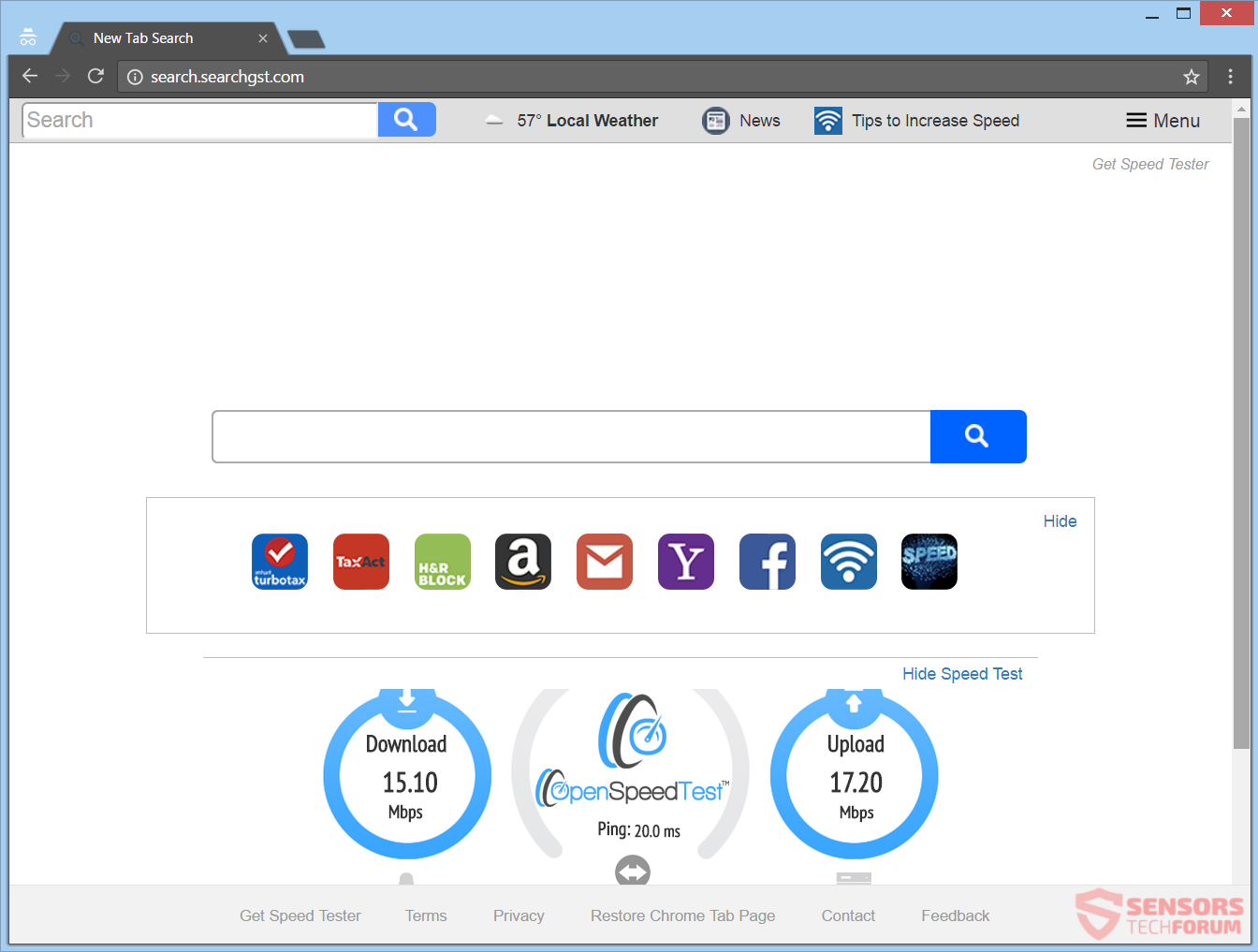
This article will help you remove Searchgst.com absolutely. Follow the browser hijacker removal instructions at the end of this article. Searchgst.com is the primary Web address and the new tab page for a browser hijacker redirect that is named Get…