Created in 2007, Pawn Storm is the name of a cyber-espionage operation whose main aim is targeting military, governments and media entities.
The name Pawn Storm comes from a chess action where the pawns are organized into a massive defense against the adversary. The name corresponds to this operation as the attackers use multiple downloaders in order to avoid being caught and to continue their work undisturbed. According to experts at Trend Micro, a specialized blog about threat and security information, the cyber criminals behind the Pawn Storm work with several attack tactics to penetrate the victims’ defense. And they are:
→ spear-phishing emails with malicious Microsoft Office documents lead to SEDNIT/Sofacy malware, very selective exploits injected into legitimate websites that will also lead to SEDNIT/Sofacy malware, and phishing emails that redirect victims to fake Outlook Web Access login pages,’ as per Trend Micro.
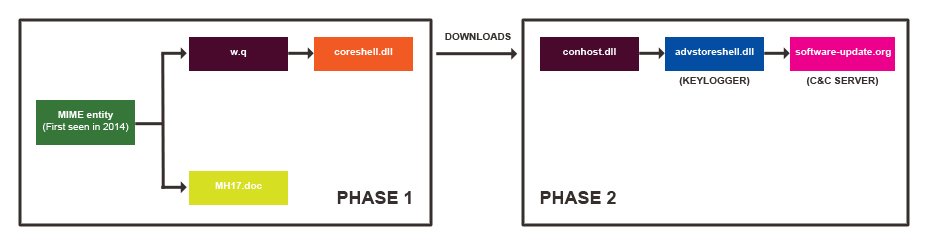
The researchers have noticed that the piece of malware called SEDNIT is used quite often, specifically through spear-phishing emails. After a closer look at SEDNIT malware and how the cyber criminals utilize it, Trend Macro have concluded that the attackers are quite experienced indeed. SEDNIT appears to be very flexible – it’s designed to break through the victims’ defense easily, after which it continues to capture as much information as possible.
In one of the recent attacks involving SEDNET, the cyber criminals attacked Polish websites through the browser and threatened the payload hosting. Apparently they intended to make it look like they were targeting multiple users, when in fact, they had a far smaller list of targets.
In addition to the espionage tactics, the attackers have other methods to compromise the victims’ systems such as malware for exploiting and data-stealing.
‘SEDNIT variants particularly proved useful, as these allowed the threat actors to steal all manners of sensitive information from the victims’ computers while effectively evading detection,’ said researchers at Trend Micro.