The popular messaging platform of Twitter is a very important resource for the cyber criminals. Recent research showed that more than 20 000 Twitter accounts have been used for different phishing campaigns in order to spread malicious links.
How are the Twitter accounts used?
The cyber criminals are using a simple scheme. They work through just one compromised account, which spreads bad URLs, misguiding the users to provide keys to their Twitter service on specially made fake login pages.
How many Twitter accounts have been used?
According to the malware researchers, more than 13 000 different addresses were used in the phishing links. After one account is hijacked, then the cybercriminal sends a message to the friend of the victim with an invitation to click on a link that leads to a phishing page.
Then, as this address is accessed, it loads a Twitter login page which is fake, leaving the impression that the user has been signed out and needs to enter one’s Twitter account as well. When the user tries to check the URL content, he find out about its malicious nature and tries to log back in. However, the information that has been entered in the fake Twitter log in page has been already sent to the cybercriminals and the account makes a new message containing the phishing link.
The phishing scheme duration
This phishing scheme has been observed for a period of 3 months, from the beginning of March until the beginning of June. The security company TrendMicro has issued a report, based on the results from the peak days of the attack. According to that report, the cybercriminals have used more than 20 000 accounts in order to send links to more than 13 000 addresses.
The malware researchers say that half of the clicks on the phishing links during these 3 months came from the United States, followed by Japan users with 15 % of the clicks. The other countries that were affected include Australia, the United Kingdom, Canada, Malaysia, France and Philippines, Indonesia and the Netherlands, all with less than 10% of the clicks.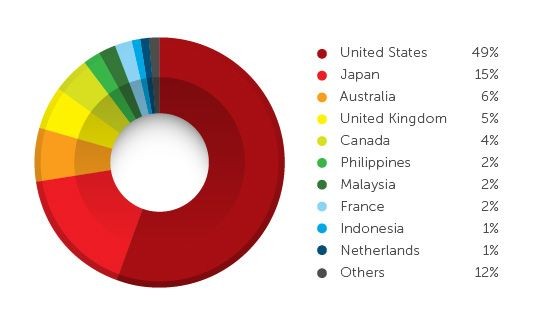
How are the experts identifying the malicious tweets?
The security researchers have managed to find a way and identify the malicious tweets when they see them. In order to do that they need sender data, content, hashtags and the embedded URLs.
The Twitter situation now
Twitter got on the top of the phishing campaign in June, when the phishing attacks on Twitter dropped in number. The malware experts say that the phishing and other malicious activity on Twitter are difficult to catch, since it is impossible for the experts to use automated tools to catch the malware.
The malware specialists can use sandboxes, honeypots and other web instruments, however they cannot catch the bad messages, since they are sent from one legitimate used to another and have a shorter URL.

