This article sheds light on the sophisticated scam beneath the allure of complimentary gaming currency, diving into the truth behind psnbounty.org’s offers, understanding its operation, and arming you with the knowledge to spot and avoid similar traps. Let us go through the signs of deceit, compare legitimate sources for PSN (PlayStation Network) codes, and outline proactive measures to keep your digital gaming experience secure and enjoyable.

Psnbounty.org – Details
| Name | Psnbounty.org |
| Type | Scam / Phishing / PUP |
| Short Description | May cause redirects to a fake type of page that aims to trick you into believing that this is a legitimate reward and you have to give your information. |
| Symptoms | A scam page that may suddenly appear on your web browser, asking you to fill in your personal details. |
| Distribution Method | Caused by adware or a browser hijacker PUP. |
| Detection Tool |
See If Your Device Has Been Affected by Psnbounty.org
Download
Malware Removal Tool
|
Deciphering the Psnbounty.org PSN Scam: What You Should Know
Understanding the reality behind psnbounty.org and its alluring offer of free PSN gift card codes is crucial for online users. This website promises something that appears too good to be true – and that’s exactly what it is. It’s essential to recognize the signs of such scams and understand why platforms like these cannot deliver on their promises. By familiarizing yourself with how these scams operate, you can protect yourself from falling victim to their deceptive tactics.
Truth Behind psnbounty.or’s PSN Claims
The core promise of psnbounty.org, to freely generate PSN gift card codes, is entirely unfounded. Legitimate businesses undertake thorough processes and partnerships to provide actual codes, and simply put, psnbounty.org is not among these legitimate entities. The website’s claims of a high success rate and easy access to free codes are designed to lure users into a false sense of security and anticipation of benefits that will never materialize.
Several red flags indicate the dubious nature of the site. For example, legitimate services do not require access to personal information like Google accounts or contact details merely for code generation. Moreover, typos, grammatical errors, and a lack of transparency about the site’s ownership further add to the suspicious character of psnbounty.org.
Unveiling How the Psnbounty.org Scam Operates
The operation of the psnbounty.org scam is relatively straightforward but deceptive. Here’s a breakdown of how individuals are tricked:
- You are prompted to select a gift card amount, which then leads you to a webpage filled with so-called offers instead of directly displaying a PSN code.
- These offers vary from downloading mobile applications to signing up for services or filling out surveys, none of which have any real connection to generating PSN codes.
- After completing several offers, as instructed by the site, users find themselves either looped back to the beginning or left with a non-responsive webpage, with no PSN code provided.
- Throughout this process, the website collects personal data through the offers and downloads, posing a risk to your privacy and online security.
- The ultimate goal of psnbounty.org is not to distribute PSN codes but to generate traffic for its affiliate marketing schemes and harvest user data for illicit purposes.
The mechanism employed by psnbounty.org capitalizes on users’ desires for free products while putting their digital security at risk. The requirement to download apps or engage with shady offers introduces malware risks, making users susceptible to further scams and data breaches.
For those concerned about safeguarding their online privacy and security, employing a dedicated security solution such as SpyHunter can provide robust protection against malware and potentially unwanted programs (PUPs) that might stem from deceptive sites like psnbounty.org.
Recognizing the Red Flags: How to Spot the psnbounty.org Scam
The allure of free PlayStation Network (PSN) gift card codes can be irresistible, but it’s crucial to stay vigilant and recognize the signs of potential scams. Psnbounty.org, promising such offers, shows several red flags indicative of scam operations. Understanding these warning signs can help protect your personal information and prevent the risk of malware infections.
Key Warning Signs That psnbounty.org is a Scam
The first step in staying safe online is learning to spot the markers of deceitful websites. Psnbounty.org is riddled with such indicators, from the requirement to download dubious applications to the presence of grammatical mistakes across its pages. Here are some of the most critical warning signs:
- Unauthorized account access requests: Legitimate services will not require access to your Google account or contacts. Such requests are a clear invasion of privacy and a huge red flag.
- Poor website quality: The presence of typos, grammatical errors, and unprofessional website design serve as warning signs of a non-legitimate operation.
- Lack of verified success stories: A legitimate offer should have verified users vouching for its authenticity. The absence of such testimonials from Psnbounty.org raises doubts.
- Anonymous ownership: The use of services to hide the identity of website owners, such as GoDaddy’s Domains By Proxy, is often a sign of someone trying to avoid accountability.
- Exaggerated success claims: Psnbounty.org’s claim of a “95% success rate” in code delivery is unrealistic and unsupported by evidence, pointing towards deception.
- Misleading affiliate marketing: The site’s focus on promoting third-party offers rather than delivering on its promises indicates its primary goal is generating affiliate revenue, not providing PSN codes.
- Risks of malware: The requirement to download applications from unverified sources introduces a significant risk of malware, posing a severe threat to your device’s security.
Comparing psnbounty.org with Legitimate PSN Gift Card Offers
When faced with tempting offers like those from Psnbounty.org, it helps to understand how legitimate PSN gift card offers work.
Genuine offers are direct and do not involve jumping through hoops such as downloading suspicious apps or giving away personal information in exchange for the promise of free codes. Here are elements typical of authentic offers:
- Direct purchase or authorized giveaways: Legitimate codes are usually bought directly or received through official giveaways. They do not require downloading unknown apps or completing dubious tasks.
- Transparency and accountability: Reputable sources are transparent about the terms and conditions of the gift card use. They also provide clear contact information for support.
- Security measures: Established platforms prioritize user security, ensuring that transactions and personal data are protected with proper encryption and privacy policies.
- No exaggerated claims: Authentic platforms do not need to make overstated claims about success rates because their reputation and user testimonials speak for themselves.
To keep your information safe and avoid scams, it is essential only to rely on PSN codes from the PlayStation Store or authorized retailers. In addition, installing trusted security software like SpyHunter can offer an additional layer of protection against malware that might accompany dubious downloads. Remember, if an offer seems too good to be true, it probably is. Exercise caution and conduct thorough research before engaging with any site promising free PSN codes.
Preventive Measures: How to Safeguard Yourself from PSN Scams
In a digital era where online transactions are commonplace, the risk of encountering scams, especially in the gaming community, has surged. Play Station Network (PSN) gift card scams are particularly prevalent, tricking unsuspecting individuals into offering personal information or money in exchange for non-existent codes. Below are effective strategies to protect yourself from falling into these fraudulent traps.
Steps to Avoid Falling Victim to PSN Gift Scams
Staying ahead of scam artists requires awareness and practical steps. Here are actionable measures you can take:
- Scrutinize Offers: If an offer seems too good to be true, it likely is. Always question the legitimacy of free codes or heavily discounted gift cards.
- Official Purchases: Buy PSN cards directly from Sony or authorized retailers. This direct approach minimizes the risk of fraud.
- Ignore Downloads: Legitimate giveaways won’t require you to download apps or software as a condition for receiving gift cards. Avoid any such conditions as they’re a direct path to malware.
- Avoid Sharing Personal Information: Never share your sensitive information like Google account details or phone numbers with unknown websites or entities.
- Perform Due Diligence: Before engaging with any site offering PSN gift cards, conduct thorough checks. Look for credible contact information, professional website presentation, and user reviews.
- Utilize Secure Payment Methods: When making any purchase, use secure, traceable payment methods. If a scam occurs, these methods often offer some recourse.
By adopting these steps, you can substantially reduce the risk of becoming a victim of PSN gift card scams.
How to Secure Your Personal Information Online
The internet is a vast space where personal information is constantly at risk. To ensure your online safety, particular steps should be taken to secure personal and sensitive data:
- Utilize Strong, Unique Passwords: For each online account, create a strong, unique password. Consider using a password manager to keep track of your passwords securely.
- Two-Factor Authentication (2FA): Whenever possible, enable two-factor authentication. This adds an additional layer of security by requiring a second form of verification.
- Regular Monitoring and Updates: Regularly monitor your accounts for any unauthorized activities and keep your software and applications updated to protect against vulnerabilities.
- Secure Connections: Always use secure connections (look for HTTPS in the URL) and be wary of using public Wi-Fi for transactions or sensitive activities.
- Be Skeptical of Unsolicited Requests: Fraudsters often pose as legitimate entities. Always verify the authenticity of requests for personal information.
- Use Reputable Security Software: Protect your devices with reputable security software like SpyHunter, which can detect and remove malware threats.
Securing your personal information is an ongoing process that requires vigilance and proactive measures. By following these steps, you not only protect your data but also contribute to a safer online community.
Remember, taking proactive steps to protect yourself online isn’t just about safeguarding personal information – it’s about ensuring your digital life remains as uninterrupted and enjoyable as possible, especially when it comes to gaming and online entertainment.
Action Plan: What to Do If You’ve Interacted with psnbounty.org
Falling victim to a scam such as psnbounty.org’s deceit can be unsettling. However, by taking appropriate steps right away, you can mitigate potential damage and bolster your security against future attacks. Below are immediate and essential actions one should take upon realizing they’ve become entangled with psnbounty.org, along with instructions on how to properly report such incidents to authorities for further investigation and to help prevent others from falling victim to similar scams.
Immediate Actions to Take If You Provided Personal Info to psnbounty.org
If you’ve accidentally provided personal information to psnbounty.org, it’s critical to act quickly to protect yourself from possible identity theft or financial loss. Here’s what you should do:
- Contact Credit Bureaus: Immediately reach out to major credit bureaus to place fraud alerts on your reports. This precaution helps prevent identity thieves from opening new accounts in your name.
- Monitor Your Credit: Regularly review your credit reports for any unauthorized activities. If you spot anything suspicious, report it right away.
- Update Passwords: Change the passwords for all your accounts, especially those that you might have shared with the scam site. Consider using strong, unique passwords for each account, and activate two-factor authentication wherever it’s available.
- Scan for Malware: Use reputable security software, like SpyHunter, to run a thorough scan on any device that accessed psnbounty.org. This checks for malware that could have been downloaded unintentionally.
- Contact Your Phone Carrier: If you’ve received unwanted charges on your mobile bill, inform your carrier and inquire about blocking future premium SMS charges.
- File Official Complaints: Document all interactions and file official complaints with the Federal Trade Commission (FTC) to support their investigative and consumer protection efforts.
Contacting Authorities and Reporting the Scam
Reporting your experience to appropriate bodies not only aids in combating fraud but also protects the broader community by raising awareness. Follow these steps to report psnbounty.org:
- Federal Trade Commission (FTC): Submit a complaint to the FTC through their official website. Provide as much detail as possible to help their investigations.
- Internet Crime Complaint Center (IC3): The IC3 is another crucial platform for reporting internet-based scams. Filing a report here ensures the details reach federal authorities for appropriate action.
- Notify Namecheap: Since psnbounty.org’s domain is registered with Namecheap, reaching out to their abuse team at abuse@namecheap.com might prompt them to take action against the fraudulent site.
- Engage with Community Forums: Sharing your experience on social platforms or scam awareness forums can alert others to the dangers of psnbounty.org and similar scams.
Confronting a scam head-on by taking these suggested steps can help minimize harm and serve as a valuable warning to others in the digital community. Always stay vigilant, think critically about unsolicited offers, and utilize trusted security tools like SpyHunter to stay protected online.
Is Your Computer at Risk? Conduct a Security Check
In today’s rapidly evolving tech landscape, ensuring your computer’s safety is more critical than ever. Scammers, hackers, and malware creators are continually developing new methods to infiltrate and compromise your system. Running a thorough security check on your computer can help identify and mitigate these risks. A comprehensive scan with reliable anti-malware software, such as REMOVED, can detect hidden threats that might have slipped past your existing security measures. By staying vigilant and conducting regular checks, you can protect your device from the wide range of digital dangers lurking online.
Why Running a Malware Scan Is Crucial After a Scam Exposure
Exposure to a scam can leave your computer vulnerable to various malware infections, including trojans, adware, and ransomware. Scams, ranging from phishing emails to fraudulent system alerts, often serve as gateways for malware to enter your system. After encountering a scam, running a malware scan becomes an essential step in securing your computer. Scanning your device helps ensure that any malware introduced during the scam is detected and removed promptly, safeguarding your personal information and preventing potential damage to your system. Regular scans, particularly after suspect interactions, are crucial for maintaining a secure and healthy computer.
Using SpyHunter to Detect and Remove Malware Threats
SpyHunter stands as a robust solution for detecting and eliminating malware threats, ensuring your computer’s safety. Its user-friendly interface and powerful scanning engine make identifying and removing malware straightforward and efficient. SpyHunter is designed to comprehensively assess your system for various types of malware, offering peace of mind in the digital age. By integrating SpyHunter into your cybersecurity routine, you can enhance your defense against the myriad of threats present in the digital landscape. Its dynamic updates ensure SpyHunter remains effective against the latest malware variants, making it an invaluable tool in maintaining a secure and clean computing environment.
Expert Advice: Enhancing Your Digital Security Post-Scam
Falling victim to an online scam can be a distressing experience, but it also serves as a critical wake-up call to bolster your digital security and privacy defenses. Whether it’s a phishing scam, malware intrusion, or any unauthorized access to your personal information, the response should be swift and comprehensive. Here are actionable guidelines to strengthen your online security posture and ensure a safer digital environment moving forward.
Best Practices to Maintain Online Security and Privacy
One fundamental step in protecting your digital presence is to adopt best practices that safeguard your online activities and personal information. Begin by regularly updating your passwords and making sure that they are complex and unique for each account. Utilize two-factor authentication (2FA) wherever available to add an extra layer of security. Also, be cautious about the information you share online, especially on social media, as scammers can use this information to target you more effectively.
- Avoid clicking on links or downloading attachments from unknown sources.
- Regularly review the privacy settings on your online accounts.
- Stay informed about the latest online threats and how to avoid them.
- Use a VPN to encrypt your internet connection, especially on public Wi-Fi networks.
Why Regular Security Software Updates Matter
Outdated software is a prime target for hackers looking to exploit vulnerabilities. Ensuring that your operating system and all applications are up-to-date is crucial for closing security loopholes that could be exploited by malware or viruses. Automatic updates should be enabled to ensure that you’re always running the most secure versions of your software. Furthermore, investing in comprehensive security software, like SpyHunter, can provide real-time protection against a variety of threats, including spyware, Trojans, and ransomware. SpyHunter is designed to detect and remove malware, enhancing your system’s defense against current and emerging threats.
- Enable automatic updates for your operating system and software.
- Regularly back up your data to prevent loss in case of a malware attack.
- Consider using cloud services for an additional layer of data redundancy.
- Invest in reputable security software with real-time protection capabilities.
By following these expert-recommended strategies, you can significantly enhance your digital security and protect your personal information from future threats. Emphasizing a proactive approach to security, coupled with the use of advanced tools like SpyHunter for malware detection and removal, plays a pivotal role in ensuring a safer online experience.
Conclusion: Staying One Step Ahead of PSN Gift Card Scams
In a digital age where offers of free PSN gift cards can seem all too tempting, staying informed and cautious is paramount. The allure of receiving something for nothing has led many down a path fraught with scams, such as the one operated by Psnbounty.org. Recognizing these scams’ signs and understanding the legitimate ways to obtain PSN gift cards can protect you from potential losses – both of time and personal information. Let’s explore how to navigate this landscape safely.
First and foremost, always question the legitimacy of offers that seem too good to be true. Genuine promotions or giveaways involving PSN gift cards will typically come directly from well-known retailers, the official PlayStation Store, or established gaming communities. These offers do not require you to download third-party applications, provide sensitive information, or complete extensive tasks. When encountering websites or services promising free PSN codes, it is crucial to conduct thorough research. Look for credible reviews, verify the website’s authenticity, and search for real-world contact information or social media engagement that confirms the site’s legitimacy.
An effective strategy for safeguarding against such scams is to opt for secure, tried-and-tested methods of obtaining PSN content. Purchasing prepaid PSN cards from reputable retailers or directly from the PlayStation Store ensures that your gaming experience remains uninterrupted by fraudulent schemes. Additionally, applying a critical eye to any online promotion and refraining from engaging with suspicious links on social media or pop-up ads will significantly reduce the risk of falling victim to scams.
In instances where you may encounter a scam, taking immediate action by exiting the webpage and reporting the scam to authorities such as the Federal Trade Commission (FTC) or the Internet Crime Complaint Center (IC3) can help in the fight against online fraud. For those seeking an added layer of security for their devices and personal information, integrating a reputable security tool like SpyHunter can provide real-time protection against malware and phishing attempts that often accompany such scams.
- Windows
- Mac OS X
- Google Chrome
- Mozilla Firefox
- Microsoft Edge
- Safari
- Internet Explorer
- Stop Push Pop-ups
How to Remove Psnbounty.org from Windows.
Step 1: Scan for Psnbounty.org with SpyHunter Anti-Malware Tool



Step 2: Boot Your PC In Safe Mode





Step 3: Uninstall Psnbounty.org and related software from Windows
Uninstall Steps for Windows 11
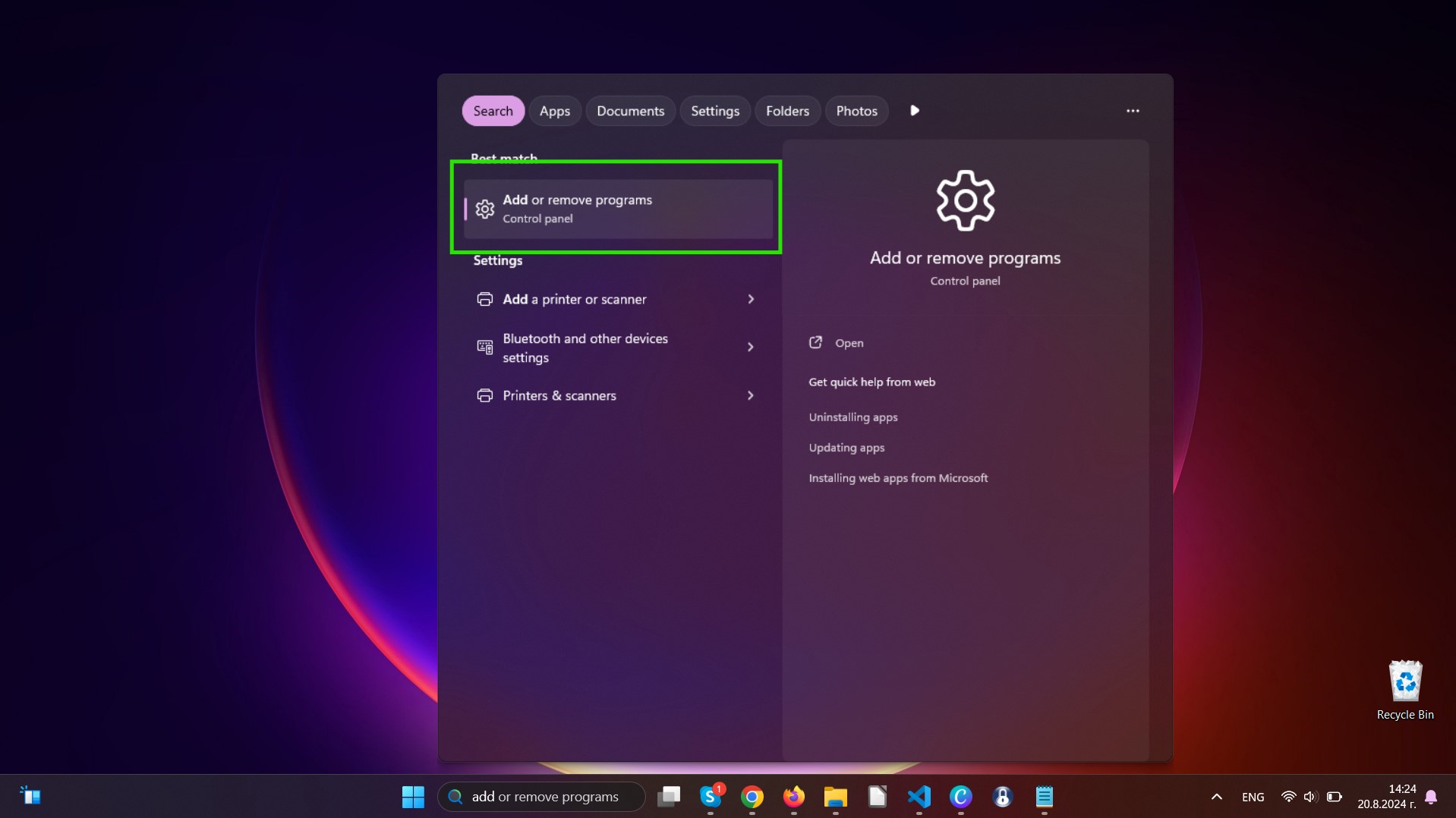
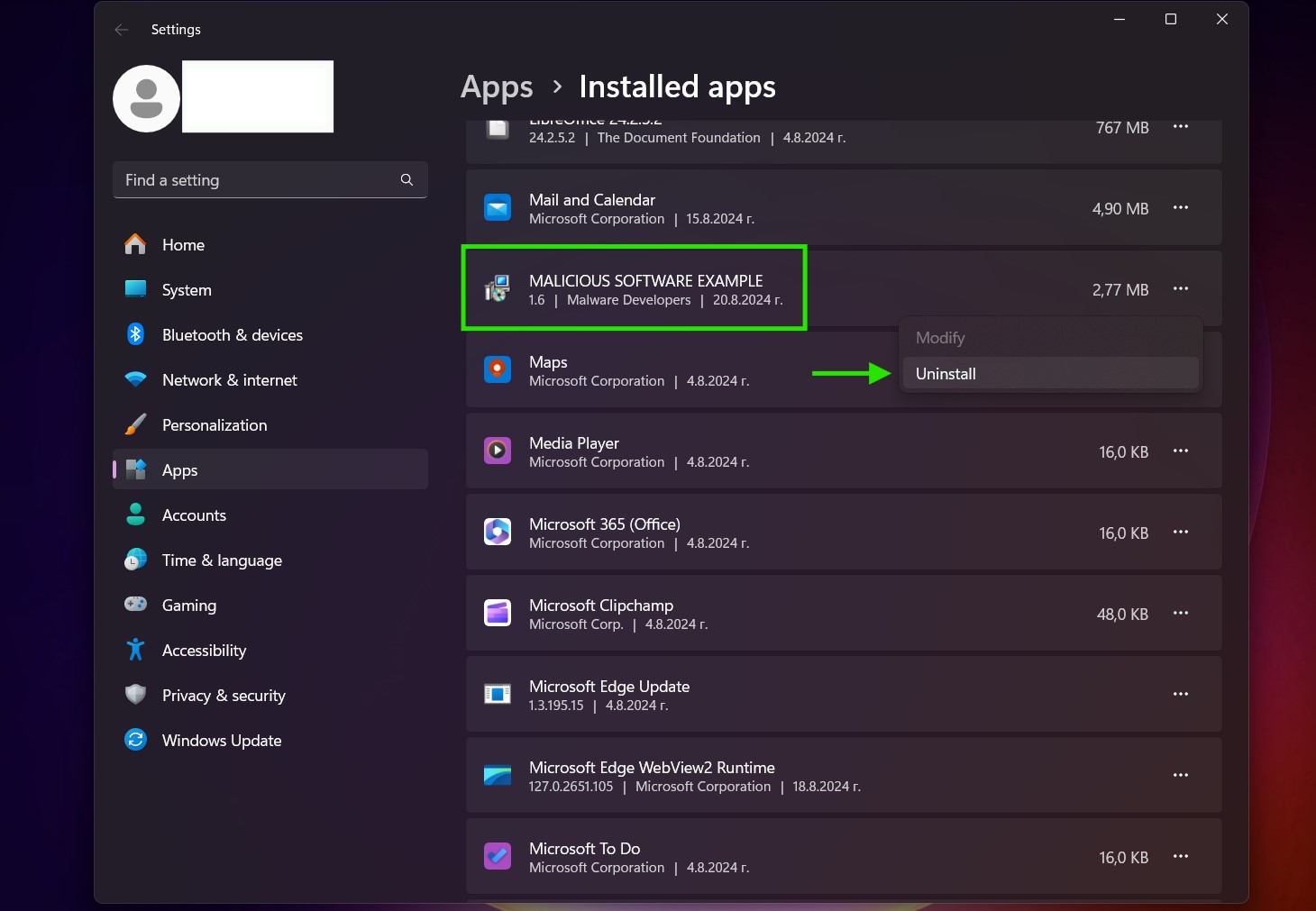
Uninstall Steps for Windows 10 and Older Versions
Here is a method in few easy steps that should be able to uninstall most programs. No matter if you are using Windows 10, 8, 7, Vista or XP, those steps will get the job done. Dragging the program or its folder to the recycle bin can be a very bad decision. If you do that, bits and pieces of the program are left behind, and that can lead to unstable work of your PC, errors with the file type associations and other unpleasant activities. The proper way to get a program off your computer is to Uninstall it. To do that:


 Follow the instructions above and you will successfully uninstall most programs.
Follow the instructions above and you will successfully uninstall most programs.
Step 4: Clean Any registries, Created by Psnbounty.org on Your PC.
The usually targeted registries of Windows machines are the following:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
You can access them by opening the Windows registry editor and deleting any values, created by Psnbounty.org there. This can happen by following the steps underneath:


 Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Video Removal Guide for Psnbounty.org (Windows).
Get rid of Psnbounty.org from Mac OS X.
Step 1: Uninstall Psnbounty.org and remove related files and objects
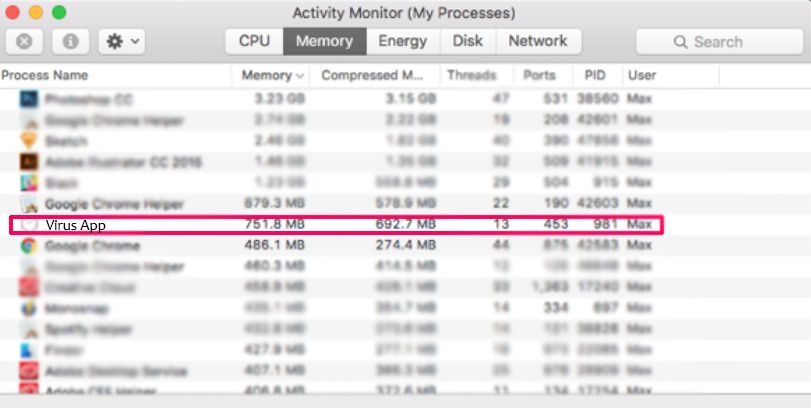
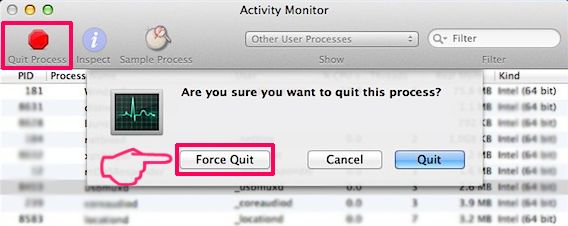
Your Mac will then show you a list of items that start automatically when you log in. Look for any suspicious apps identical or similar to Psnbounty.org. Check the app you want to stop from running automatically and then select on the Minus (“-“) icon to hide it.
- Go to Finder.
- In the search bar type the name of the app that you want to remove.
- Above the search bar change the two drop down menus to “System Files” and “Are Included” so that you can see all of the files associated with the application you want to remove. Bear in mind that some of the files may not be related to the app so be very careful which files you delete.
- If all of the files are related, hold the ⌘+A buttons to select them and then drive them to “Trash”.
In case you cannot remove Psnbounty.org via Step 1 above:
In case you cannot find the virus files and objects in your Applications or other places we have shown above, you can manually look for them in the Libraries of your Mac. But before doing this, please read the disclaimer below:
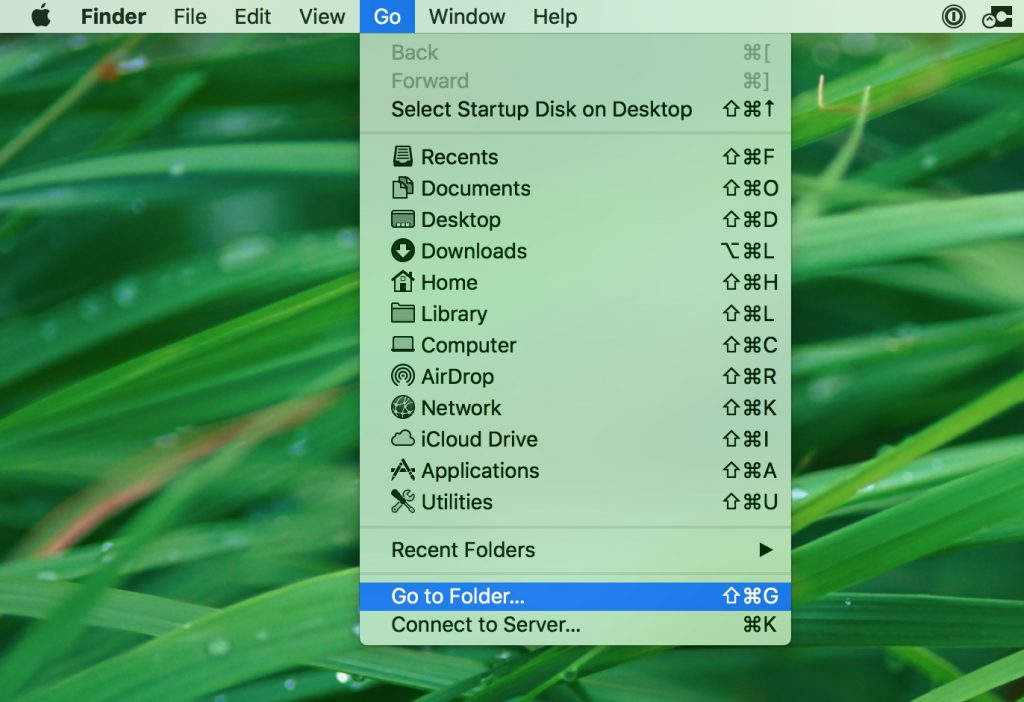
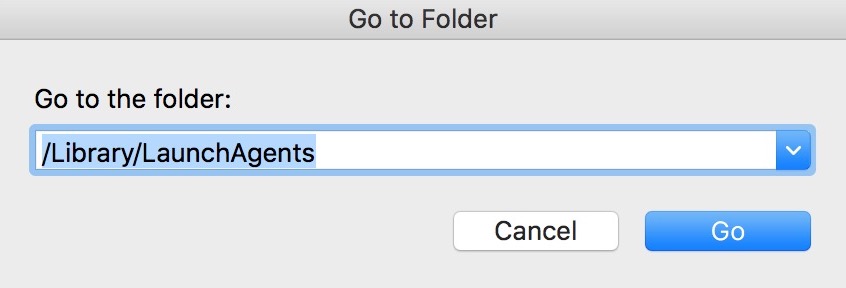
You can repeat the same procedure with the following other Library directories:
→ ~/Library/LaunchAgents
/Library/LaunchDaemons
Tip: ~ is there on purpose, because it leads to more LaunchAgents.
Step 2: Scan for and remove Psnbounty.org files from your Mac
When you are facing problems on your Mac as a result of unwanted scripts and programs such as Psnbounty.org, the recommended way of eliminating the threat is by using an anti-malware program. SpyHunter for Mac offers advanced security features along with other modules that will improve your Mac’s security and protect it in the future.
Video Removal Guide for Psnbounty.org (Mac)
Remove Psnbounty.org from Google Chrome.
Step 1: Start Google Chrome and open the drop menu
Step 2: Move the cursor over "Tools" and then from the extended menu choose "Extensions"
Step 3: From the opened "Extensions" menu locate the unwanted extension and click on its "Remove" button.
Step 4: After the extension is removed, restart Google Chrome by closing it from the red "X" button at the top right corner and start it again.
Erase Psnbounty.org from Mozilla Firefox.
Step 1: Start Mozilla Firefox. Open the menu window:
Step 2: Select the "Add-ons" icon from the menu.
Step 3: Select the unwanted extension and click "Remove"

Step 4: After the extension is removed, restart Mozilla Firefox by closing it from the red "X" button at the top right corner and start it again.
Uninstall Psnbounty.org from Microsoft Edge.
Step 1: Start Edge browser.
Step 2: Open the drop menu by clicking on the icon at the top right corner.
Step 3: From the drop menu select "Extensions".
Step 4: Choose the suspected malicious extension you want to remove and then click on the gear icon.
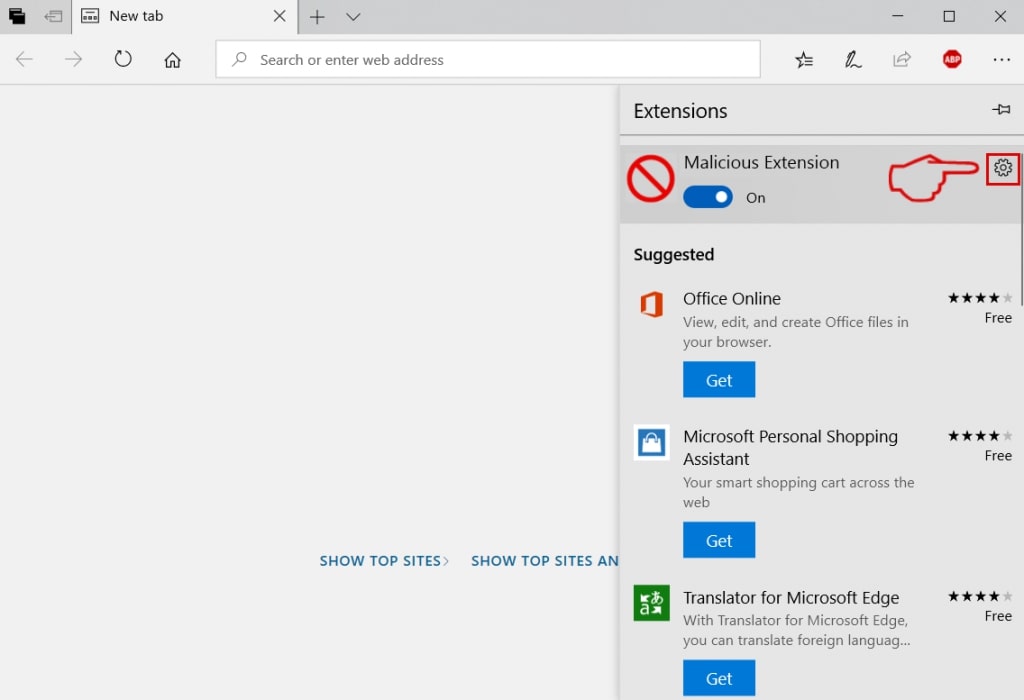
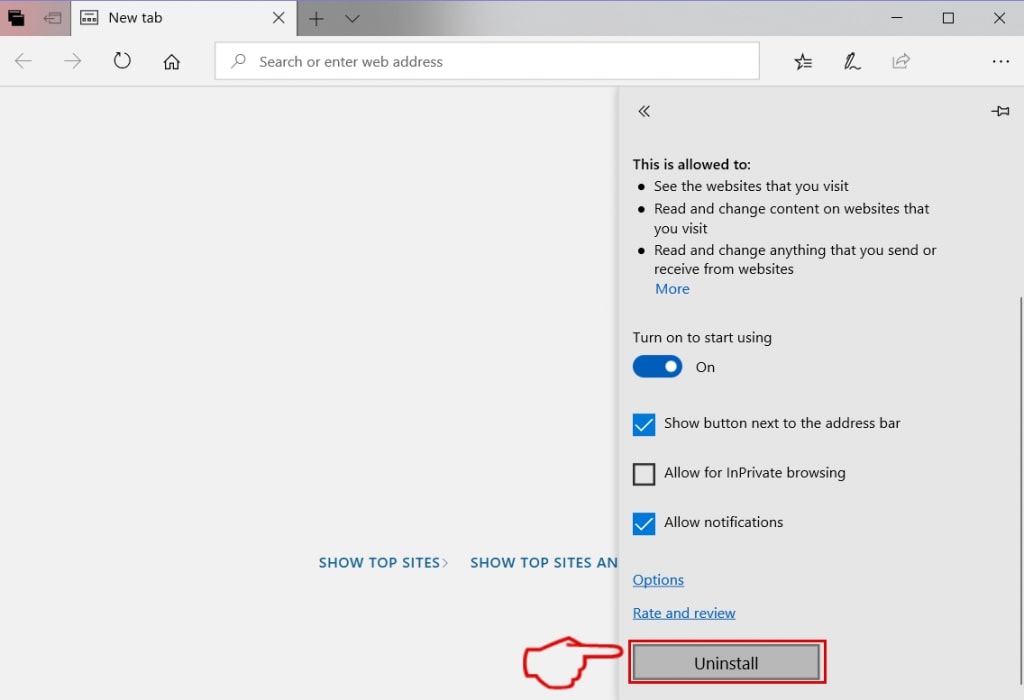
Step 5: Remove the malicious extension by scrolling down and then clicking on Uninstall.
Remove Psnbounty.org from Safari
Step 1: Start the Safari app.
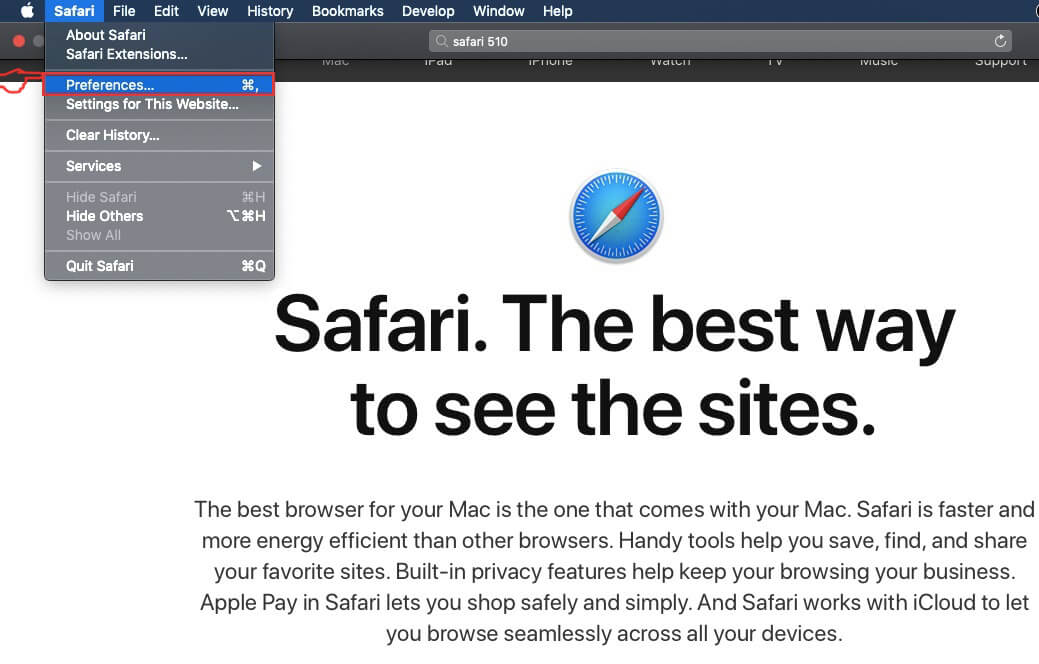
Step 2: After hovering your mouse cursor to the top of the screen, click on the Safari text to open its drop down menu.
Step 3: From the menu, click on "Preferences".
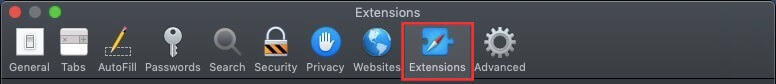
Step 4: After that, select the 'Extensions' Tab.
Step 5: Click once on the extension you want to remove.
Step 6: Click 'Uninstall'.
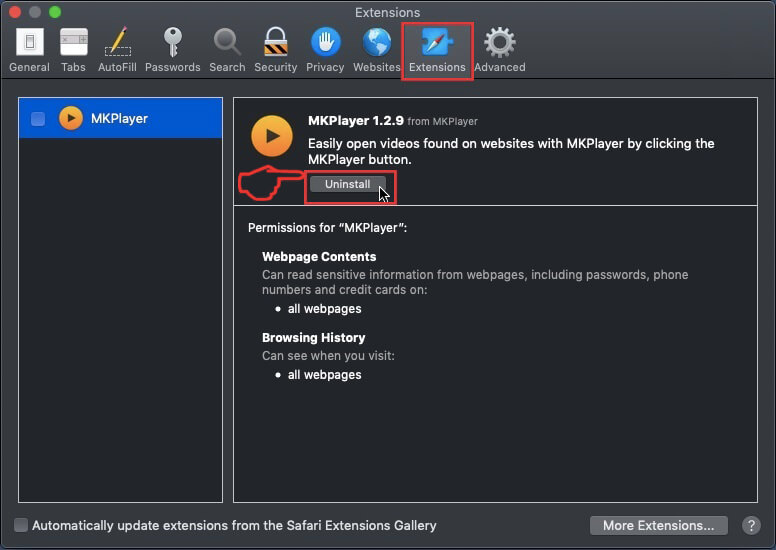
A pop-up window will appear asking for confirmation to uninstall the extension. Select 'Uninstall' again, and the Psnbounty.org will be removed.
Eliminate Psnbounty.org from Internet Explorer.
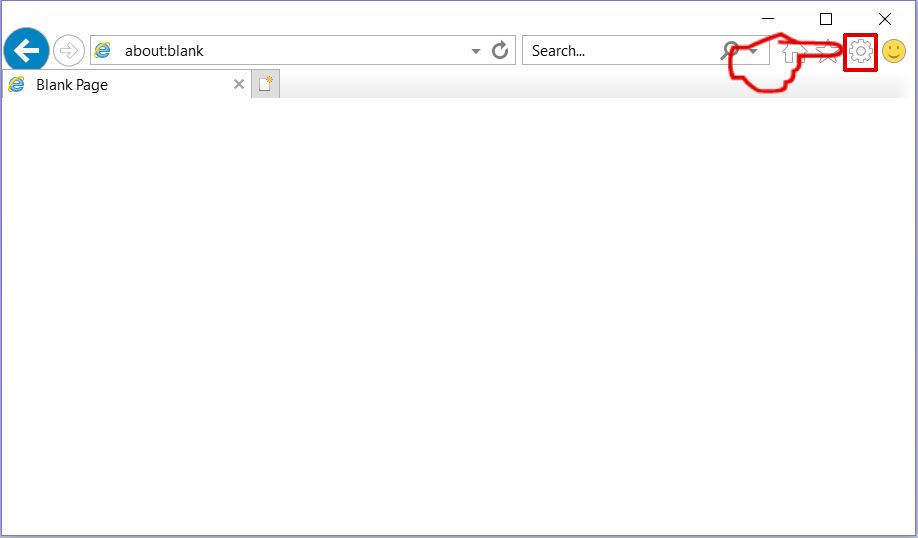
Step 1: Start Internet Explorer.
Step 2: Click on the gear icon labeled 'Tools' to open the drop menu and select 'Manage Add-ons'
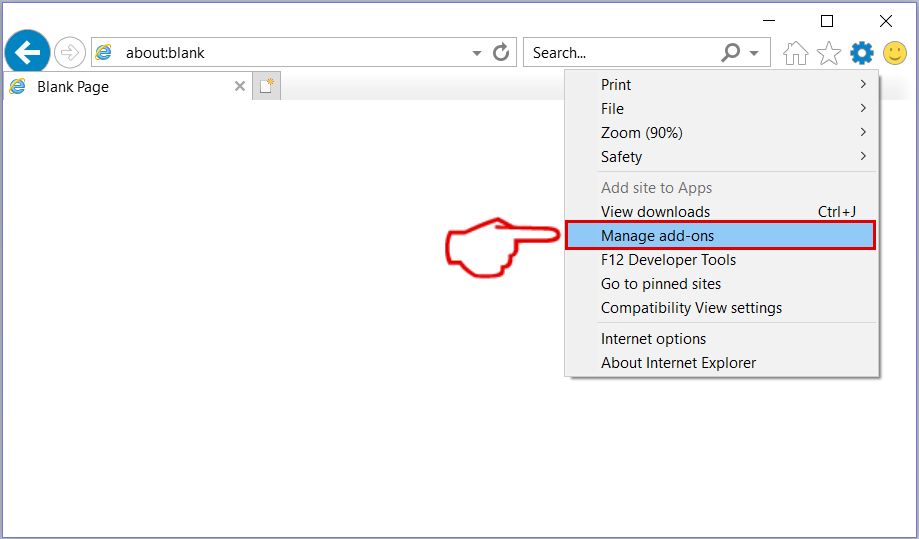
Step 3: In the 'Manage Add-ons' window.
Step 4: Select the extension you want to remove and then click 'Disable'. A pop-up window will appear to inform you that you are about to disable the selected extension, and some more add-ons might be disabled as well. Leave all the boxes checked, and click 'Disable'.
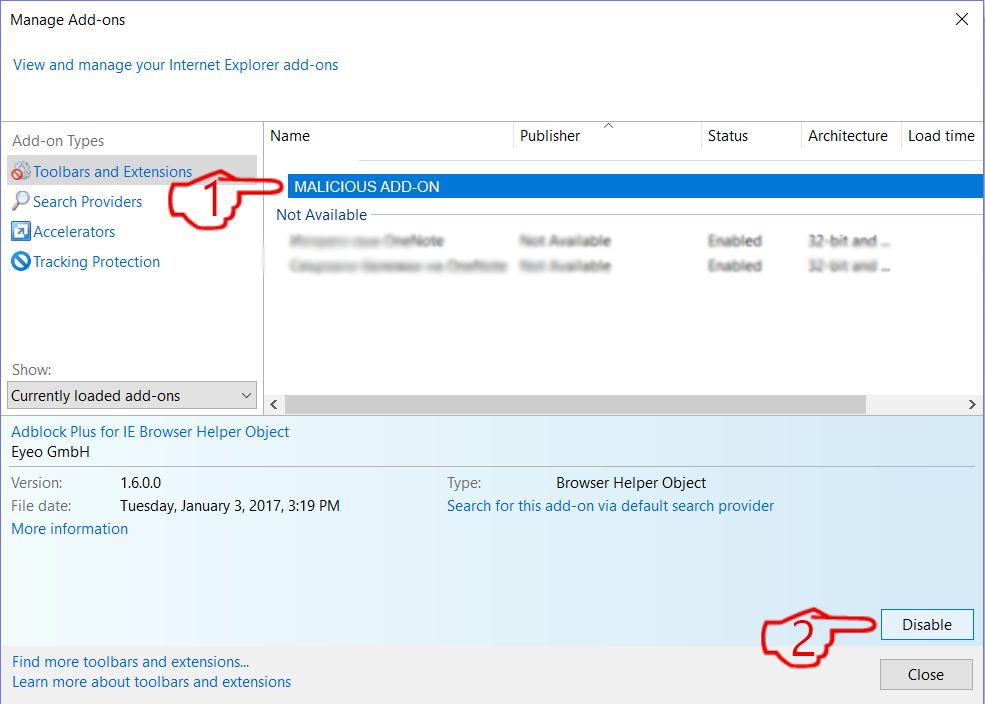
Step 5: After the unwanted extension has been removed, restart Internet Explorer by closing it from the red 'X' button located at the top right corner and start it again.
Remove Push Notifications from Your Browsers
Turn Off Push Notifications from Google Chrome
To disable any Push Notices from Google Chrome browser, please follow the steps below:
Step 1: Go to Settings in Chrome.
Step 2: In Settings, select “Advanced Settings”:
Step 3: Click “Content Settings”:
Step 4: Open “Notifications”:
Step 5: Click the three dots and choose Block, Edit or Remove options:

Remove Push Notifications on Firefox
Step 1: Go to Firefox Options.
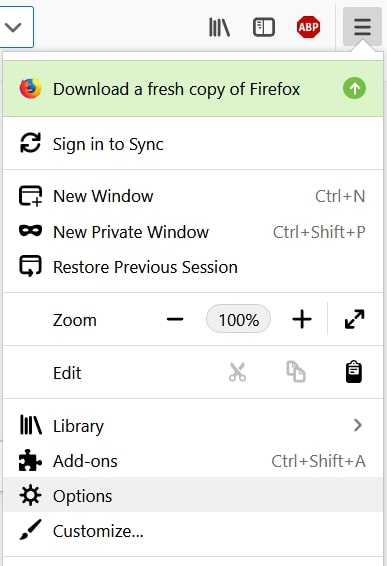
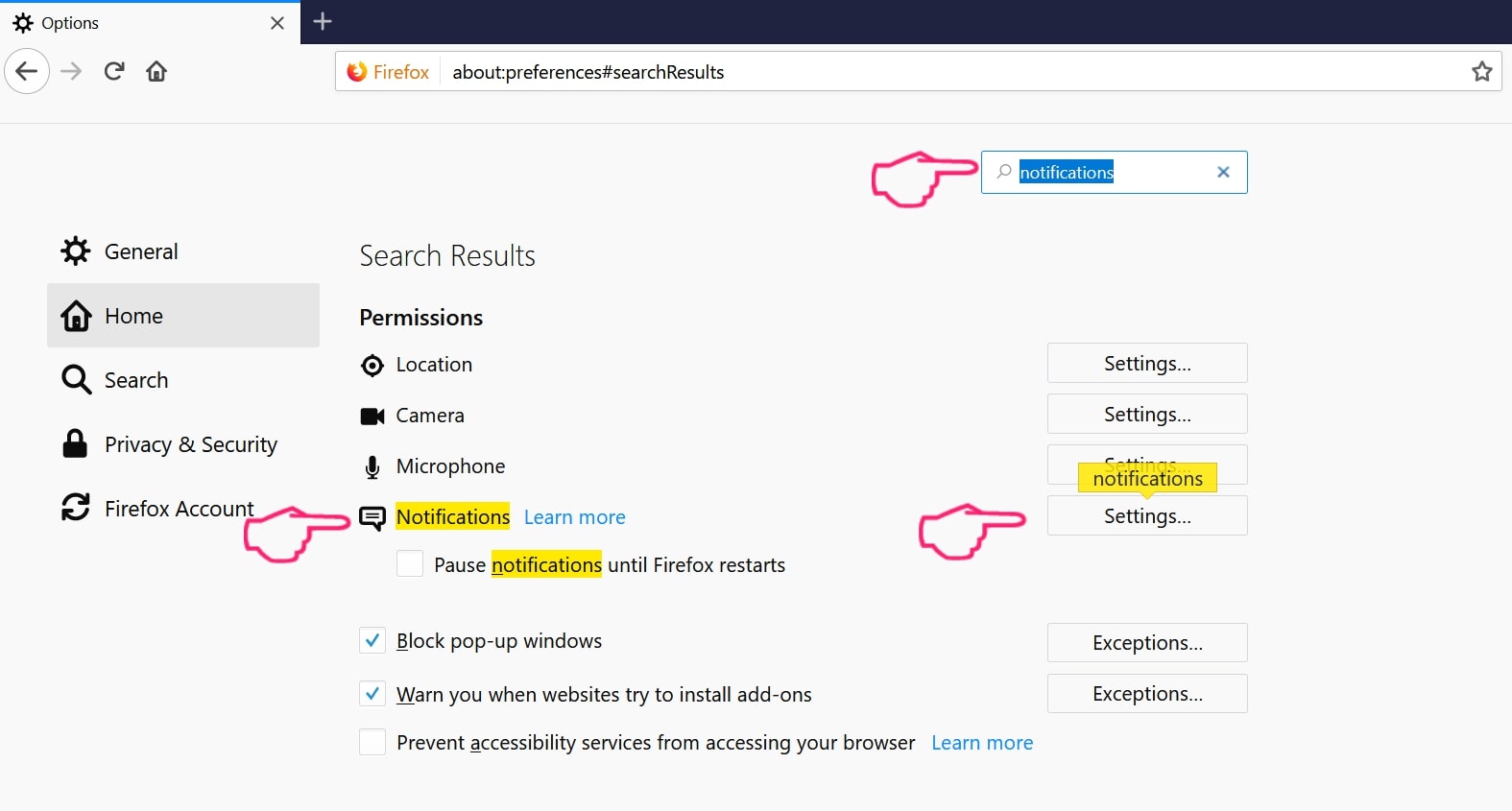
Step 2: Go to “Settings”, type “notifications” in the search bar and click "Settings":
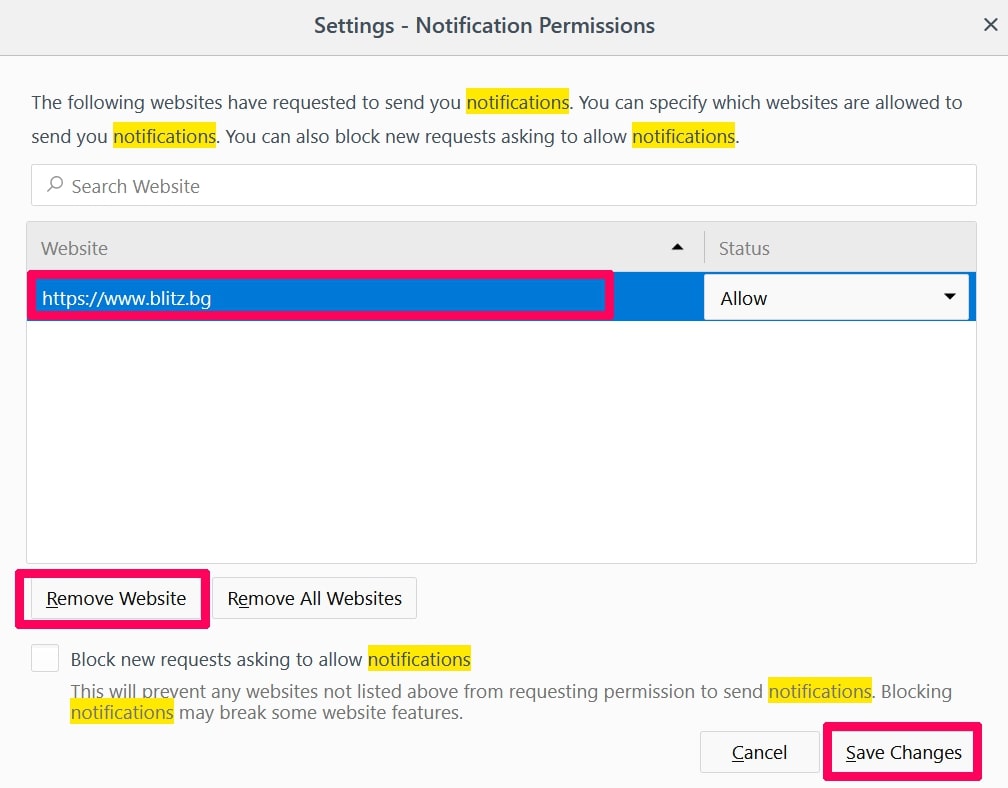
Step 3: Click “Remove” on any site you wish notifications gone and click “Save Changes”
Stop Push Notifications on Opera
Step 1: In Opera, press ALT+P to go to Settings.
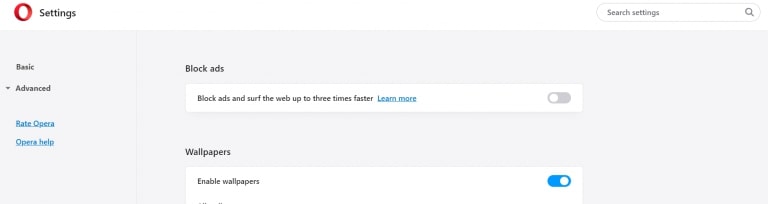
Step 2: In Setting search, type “Content” to go to Content Settings.
Step 3: Open Notifications:
Step 4: Do the same as you did with Google Chrome (explained below):
Eliminate Push Notifications on Safari
Step 1: Open Safari Preferences.
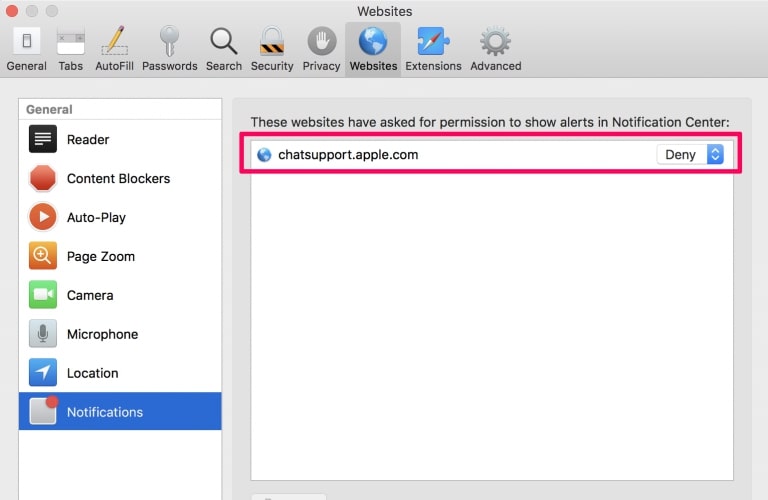
Step 2: Choose the domain from where you like push pop-ups gone and change to "Deny" from "Allow".
Psnbounty.org-FAQ
What Is Psnbounty.org?
The Psnbounty.org threat is adware or browser redirect virus.
It may slow your computer down significantly and display advertisements. The main idea is for your information to likely get stolen or more ads to appear on your device.
The creators of such unwanted apps work with pay-per-click schemes to get your computer to visit risky or different types of websites that may generate them funds. This is why they do not even care what types of websites show up on the ads. This makes their unwanted software indirectly risky for your OS.
What Are the Symptoms of Psnbounty.org?
There are several symptoms to look for when this particular threat and also unwanted apps in general are active:
Symptom #1: Your computer may become slow and have poor performance in general.
Symptom #2: You have toolbars, add-ons or extensions on your web browsers that you don't remember adding.
Symptom #3: You see all types of ads, like ad-supported search results, pop-ups and redirects to randomly appear.
Symptom #4: You see installed apps on your Mac running automatically and you do not remember installing them.
Symptom #5: You see suspicious processes running in your Task Manager.
If you see one or more of those symptoms, then security experts recommend that you check your computer for viruses.
What Types of Unwanted Programs Are There?
According to most malware researchers and cyber-security experts, the threats that can currently affect your device can be rogue antivirus software, adware, browser hijackers, clickers, fake optimizers and any forms of PUPs.
What to Do If I Have a "virus" like Psnbounty.org?
With few simple actions. First and foremost, it is imperative that you follow these steps:
Step 1: Find a safe computer and connect it to another network, not the one that your Mac was infected in.
Step 2: Change all of your passwords, starting from your email passwords.
Step 3: Enable two-factor authentication for protection of your important accounts.
Step 4: Call your bank to change your credit card details (secret code, etc.) if you have saved your credit card for online shopping or have done online activities with your card.
Step 5: Make sure to call your ISP (Internet provider or carrier) and ask them to change your IP address.
Step 6: Change your Wi-Fi password.
Step 7: (Optional): Make sure to scan all of the devices connected to your network for viruses and repeat these steps for them if they are affected.
Step 8: Install anti-malware software with real-time protection on every device you have.
Step 9: Try not to download software from sites you know nothing about and stay away from low-reputation websites in general.
If you follow these recommendations, your network and all devices will become significantly more secure against any threats or information invasive software and be virus free and protected in the future too.
How Does Psnbounty.org Work?
Once installed, Psnbounty.org can collect data using trackers. This data is about your web browsing habits, such as the websites you visit and the search terms you use. It is then used to target you with ads or to sell your information to third parties.
Psnbounty.org can also download other malicious software onto your computer, such as viruses and spyware, which can be used to steal your personal information and show risky ads, that may redirect to virus sites or scams.
Is Psnbounty.org Malware?
The truth is that PUPs (adware, browser hijackers) are not viruses, but may be just as dangerous since they may show you and redirect you to malware websites and scam pages.
Many security experts classify potentially unwanted programs as malware. This is because of the unwanted effects that PUPs can cause, such as displaying intrusive ads and collecting user data without the user’s knowledge or consent.
About the Psnbounty.org Research
The content we publish on SensorsTechForum.com, this Psnbounty.org how-to removal guide included, is the outcome of extensive research, hard work and our team’s devotion to help you remove the specific, adware-related problem, and restore your browser and computer system.
How did we conduct the research on Psnbounty.org?
Please note that our research is based on independent investigation. We are in contact with independent security researchers, thanks to which we receive daily updates on the latest malware, adware, and browser hijacker definitions.
Furthermore, the research behind the Psnbounty.org threat is backed with VirusTotal.
To better understand this online threat, please refer to the following articles which provide knowledgeable details.


