A new and improved variant of the CryptoWall ransomware has been infecting computers worldwide in the past few days. The new CryptoWall 3.0 uses a localized ransom message and passes traffic to a website where the victims can pay for the decryption key needed to unlock their files through Tor and I2P anonymous networks.
CryptoWall is a file-encrypting type of threat, which once activated on the infected machine encrypts certain files on it and demands a fine of $500 in order to provide the victim with the decryption key. The ransom is to be paid in Bitcoin digital currency in the first 168 hours.

Threat Summary
| Name | CryptoWall 3.0 |
| Type | Ransomware |
| Short Description | The user’s files are encrypted and unusable. |
| Symptoms | A ransom note is displayed to the victim. |
| Distribution Method | Via malicious attachments. |
| Detection Tool |
See If Your System Has Been Affected by malware
Download
Malware Removal Tool
|
| User Experience | Join our forum to discuss CryptoWall 3.0. |
The New Features of CryptoWall 3.0
New Tor to Web gateways are used by the new version of CryptoWall: torman2.com, torforall.com, torroadsters.com, and torwoman.com. Either one of them redirects the victim to the same web page containing the payment instructions, but the IDs for tracking the payments are unique.
The payment period is extended from five days to a whole week, after which the fee is raised to $1000.
The crooks have created additional files containing information about the payment and the restoring of the encrypted data:
- HELP_DECRYPT.HTML: uses your web browser to display information about the threat, encryption and payment methods
- HELP_DECRYPT.PNG: contains details about CryptoWall 3.0
- HELP_DECRYPT.TXT: the same as the previous one, but in plain text
- HELP_DECRYPT.URL: uses your current web browser to display the CryptoWall 3.0 Decrypt Service when Windows is loaded
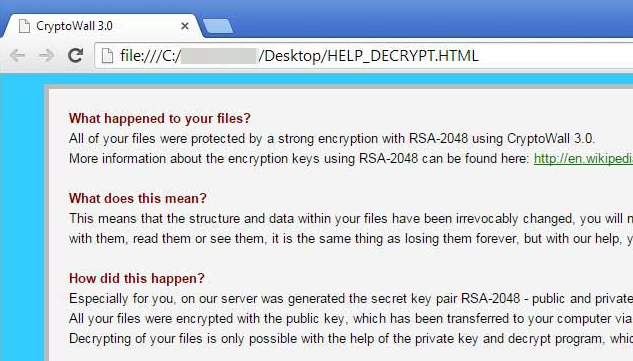
The ransom message displayed by CryptoWall 3.0 reads:
What happened to your files?
All of your files were protected by a strong encryption with RSA-2048 using CryptoWall 3.0.
More information about the encryption keys using RSA-2048 can be found here: https://en.wikipedia.org/wiki/RSA_(cryptosystem)What does this mean?
This means that the structure and data within your files have been irrevocably changed, you will not be able to work with them, read them or see them, it is the same thing as losing them forever, but with our help, you can restore them.How did this happen?
Especially for you, on our server was generated the secret key pair RSA-2048 – public and private.
All your files were encrypted with the public key, which has been transferred to your computer via the Internet.
Decrypting of your files is only possible with the help of the private key and decrypt program, which is on our secret server.
What do I do?
Alas, if you do not take the necessary measures for the specified time then the conditions for obtaining the private key will be changed.
If you really value your data, then we suggest you do not waste valuable time searching for other solutions because they do not exist.
Once the file-encryption process is over, the original files are deleted. In case you do not have a backup of your files, you could use reliable software to restore them or part of them from the Windows shadow copies. Below you will find detailed instructions on how to do so.
Connection to I2P Fails
The new version of CryptoWall has been detected by security experts at Microsoft and the French researcher Kafeine, who has reported that the communication with the C&C (Command and Control) server is encoded with the RC4 algorithm and uses the I2P protocol.
As Kafeine tried to test the sample of the new threat, he received an error message every time he attempted to connect to the proxies. The notification, the researcher received, stated that the I2P website was not available due to various reasons – inability to connect to systems or congested network. The hackers seemed to be ready for cases like this one, because they have provided detailed instructions on how to gain access to the decryption service on the Tor network.

Cryptowall 3.0 New Distribution Methods (September 4, 2015)
How is Cryptowall 3.0 dropped onto the system?
Cryptowall ransomware has been around long enough for researchers to gather detailed information about its methods. The ransomware is distributed primarily via emails with .ZIP attachments. The latter contain executable files masqueraded as PDFs. The files in question can be any form of business communication such as:
- Invoices
- Purchase orders (POs)
- Bills
- Complaints
Once the malicious PDF is launched, CryptoWall will be installed onto the system. The malicious files will be located in one of the two folders %AppData% or %Temp%. Then, the threat will start scanning the system’s drivers to find files to encrypt. All drive letters will be scanned, removal drives, network shares and DropBox mapping included. Any drive letter on the infected system will be checked for data files.
Here is a list of all the locations where CryptoWall 3.0 may be situated:
- %Temp%
- C:\[random]\[random].exe
- %AppData%
- %ProgramData%
- %LocalAppData%

Can I Find the Files Encrypted by CryptoWall 3.0?
Files encrypted by CryptoWall 3.0 will be stored together with their paths in the Windows Registry. The subkey location is in the following format:
→HKCU\Software\[unique computer ID]\[random ID]
An actual example looks like that:
→HKCU\Software\03DA0C0D2383CCC2BC8232DD0AAAD117\01133428ABDEEEFF
The process will be repeated for every encrypted file under the mentioned key.
ListCwall can be used as well. It is a tool created by Bleeping Computer to automate the finding and exporting of the encrypted files. The tool can also backup the locked files to another location, in case the user needs to archive them and reformat the PC.
Also, here is a list with file extensions which CryptoWall 3.0 seeks to encrypt:
→ .3dm, .3ds, .3fr, .mcmeta, .vfs0, .mpqge, .kdb, .db0, .dba, .rofl, .hkx, .bar, .upk, .das, .iwi, .litemod, .asset, .forge, .ltx, .bsa, .apk, .re4, .sav, .lbf, .slm, .bik, .epk, .rgss3a, .pak, .big, wallet, .wotreplay, .xxx, .desc, .py, .m3u, .flv, .js, .css, .rb, .png, .jpeg, .txt, .p7c, .p7b, .p12, .pfx, .pem, .crt, .cer, .der, .x3f, .srw, .pef, .ptx, .r3d, .rw2, .rwl, .raw, .raf, .orf, .nrw, .mrwref, .mef, .erf, .kdc, .dcr, .cr2, .crw, .bay, .sr2, .srf, .arw, .3fr, .dng, .3g2, .3gp, .3pr, .7z, .ab4, .accdb, .sql, .mp4, .7z, .rar, .m4a, .wma, .avi, .wmv, .csv, .d3dbsp, .zip, .sie, .sum, .ibank, .t13, .t12, .qdf, .gdb, .tax, .pkpass, .bc6, .bc7, .bkp, .qic, .bkf, .sidn, .sidd, .mddata, .itl, .itdb, .icxs, .hvpl, .hplg, .hkdb, .mdbackup, .syncdb, .gho, .cas, .svg, .map, .wmo, .itm, .sb, .fos, .mov, .vdf, .ztmp, .sis, .sid, .ncf, .menu, .layout, .dmp, .blob, .esm, .vcf, .vtf, .dazip, .fpk, .mlx, .kf, .iwd, .vpk, .tor, .psk, .rim, .w3x, .fsh, .ntl, .arch00, .lvl, .snx, .cfr, .ff, .vpp_pc, .lrf, .m2, .jpe, .jpg, .cdr, .indd, .ai, .eps, .pdf, .pdd, .psd, .dbf, .mdf, .wb2, .rtf, .wpd, .dxg, .xf, .dwg, .pst, .accdb, .mdb, .pptm, .pptx, .ppt, .xlk, .xlsb, .xlsm, .xlsx, .xls, .wps, .docm, .docx, .doc, .odb, .odc, .odm, .odp, .ods, .odt, .accde, .accdr, .accdt, .ach, .acr, .act, .adb

User Behavior and Ransomware. Phishing Scams
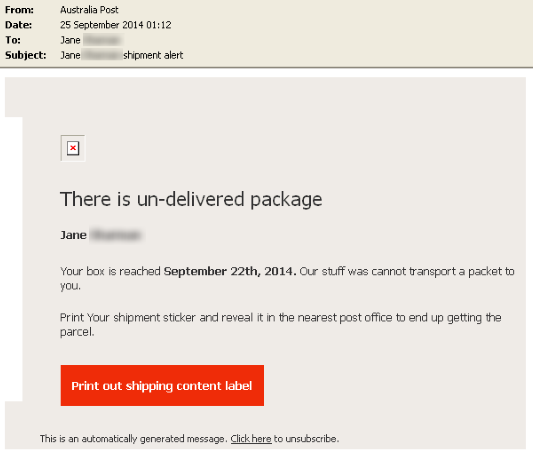
What we described about the distribution methods so far can mean only one thing – the cyber criminals solely rely on the user’s interaction with malicious spam. The method is known as phishing – a form of social engineering often deployed to spread malware or collect user credentials. This is an exemplary email of how the scam may appear to users:
Image Source: Symantec

Cryptowall Precautionary Tips
To bypass malicious infections, avoid downloading archive files such as .zip, .jar, .tar, .7z, .msi, and executable/script files such as .com, .exe, .scr, .bat, .js, .jse, .vb, .vbe, .wsf, .wsh, .cmd. Always bear in mind that real companies would avoid sending such types of files, unless you had a previous arrangement set.
Additionally, you can use online website rating services such as Norton Safe Web to determine if a website is safe or unsafe to visit. With file-encrypting threats, the best precautionary advice is a very simple one. Back-up your files. Aways think of this, especially when your data is valuable and you keep a lot of business documents on your PC.
You can also check out the general precautionary tips we have on our forum about ransomware, which come full force for CryptoWall 3.0 as well.
- IMPORTANT
CryptoWall 3.0 can encrypt files on a network share in case it is mapped as a drive letter. If the network share is not mapped as such, CryptoWall 3.0 will not affect the files located there. To secure open shares, users can allow only writable access to the needed user groups or authorized users. The tip is quite important when it comes to threats such as CryptoWall.

Remove CryptoWall 3.0 and Restore the Encrypted Files
Follow the instructions provided below to remove all traces of this ransomware. Keep in mind that the best and most secure way to do that is by using a strong anti-malware program.
- Step 1
- Step 2
- Step 3
- Step 4
- Step 5
Step 1: Scan for CryptoWall 3.0 with SpyHunter Anti-Malware Tool



Ransomware Automatic Removal - Video Guide
Step 2: Uninstall CryptoWall 3.0 and related malware from Windows
Here is a method in few easy steps that should be able to uninstall most programs. No matter if you are using Windows 10, 8, 7, Vista or XP, those steps will get the job done. Dragging the program or its folder to the recycle bin can be a very bad decision. If you do that, bits and pieces of the program are left behind, and that can lead to unstable work of your PC, errors with the file type associations and other unpleasant activities. The proper way to get a program off your computer is to Uninstall it. To do that:


 Follow the instructions above and you will successfully delete most unwanted and malicious programs.
Follow the instructions above and you will successfully delete most unwanted and malicious programs.
Step 3: Clean any registries, created by CryptoWall 3.0 on your computer.
The usually targeted registries of Windows machines are the following:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
You can access them by opening the Windows registry editor and deleting any values, created by CryptoWall 3.0 there. This can happen by following the steps underneath:


 Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Before starting "Step 4", please boot back into Normal mode, in case you are currently in Safe Mode.
This will enable you to install and use SpyHunter 5 successfully.
Step 4: Boot Your PC In Safe Mode to isolate and remove CryptoWall 3.0





Step 5: Try to Restore Files Encrypted by CryptoWall 3.0.
Method 1: Use STOP Decrypter by Emsisoft.
Not all variants of this ransomware can be decrypted for free, but we have added the decryptor used by researchers that is often updated with the variants which become eventually decrypted. You can try and decrypt your files using the instructions below, but if they do not work, then unfortunately your variant of the ransomware virus is not decryptable.
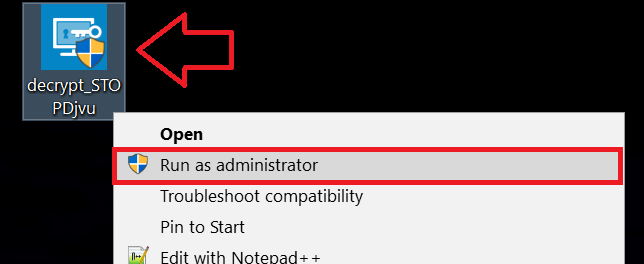
Follow the instructions below to use the Emsisoft decrypter and decrypt your files for free. You can download the Emsisoft decryption tool linked here and then follow the steps provided below:
1 Right-click on the decrypter and click on Run as Administrator as shown below:
2. Agree with the license terms:
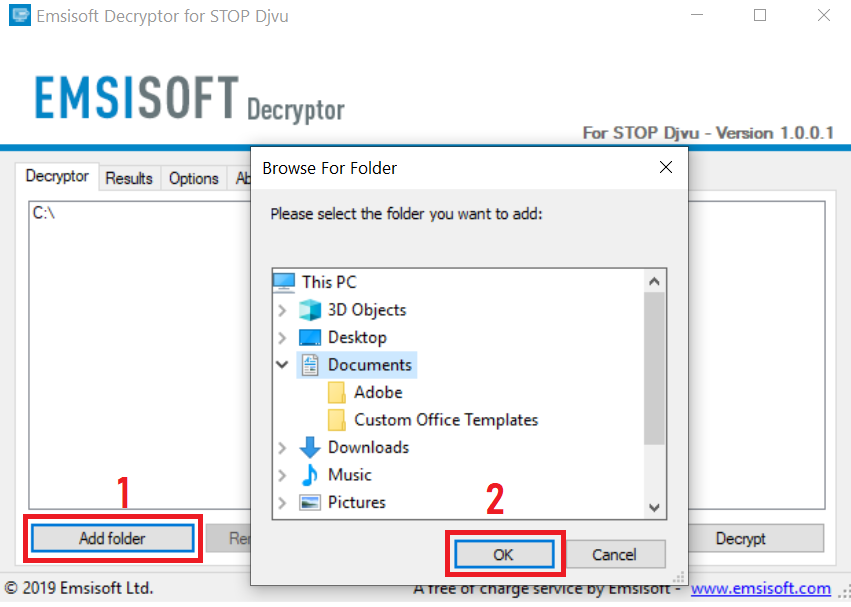
3. Click on "Add Folder" and then add the folders where you want files decrypted as shown underneath:
4. Click on "Decrypt" and wait for your files to be decoded.
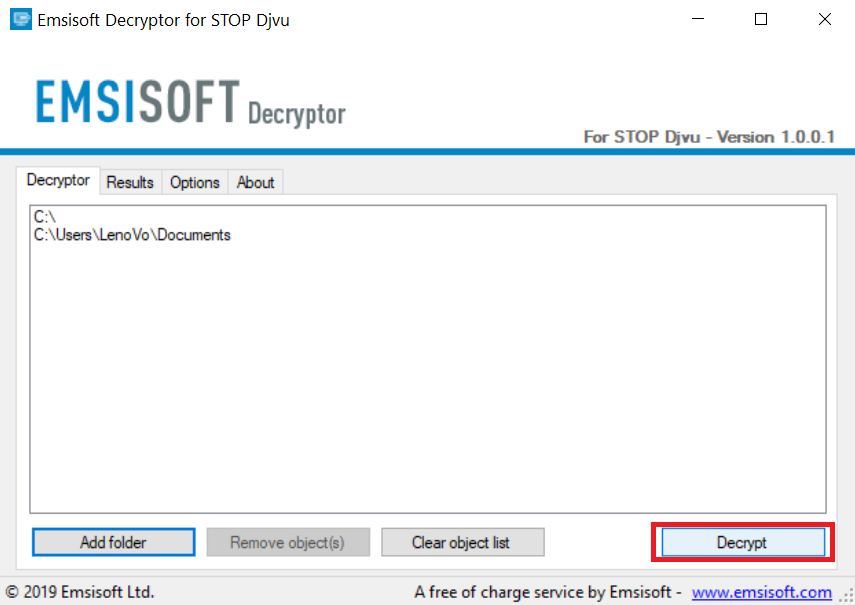
Note: Credit for the decryptor goes to Emsisoft researchers who have made the breakthrough with this virus.
Method 2: Use data recovery software
Ransomware infections and CryptoWall 3.0 aim to encrypt your files using an encryption algorithm which may be very difficult to decrypt. This is why we have suggested a data recovery method that may help you go around direct decryption and try to restore your files. Bear in mind that this method may not be 100% effective but may also help you a little or a lot in different situations.
Simply click on the link and on the website menus on the top, choose Data Recovery - Data Recovery Wizard for Windows or Mac (depending on your OS), and then download and run the tool.
CryptoWall 3.0-FAQ
What is CryptoWall 3.0 Ransomware?
CryptoWall 3.0 is a ransomware infection - the malicious software that enters your computer silently and blocks either access to the computer itself or encrypt your files.
Many ransomware viruses use sophisticated encryption algorithms to make your files inaccessible. The goal of ransomware infections is to demand that you pay a ransom payment to get access to your files back.
What Does CryptoWall 3.0 Ransomware Do?
Ransomware in general is a malicious software that is designed to block access to your computer or files until a ransom is paid.
Ransomware viruses can also damage your system, corrupt data and delete files, resulting in the permanent loss of important files.
How Does CryptoWall 3.0 Infect?
Via several ways.CryptoWall 3.0 Ransomware infects computers by being sent via phishing emails, containing virus attachment. This attachment is usually masked as an important document, like an invoice, bank document or even a plane ticket and it looks very convincing to users.
Another way you may become a victim of CryptoWall 3.0 is if you download a fake installer, crack or patch from a low reputation website or if you click on a virus link. Many users report getting a ransomware infection by downloading torrents.
How to Open .CryptoWall 3.0 files?
You can't without a decryptor. At this point, the .CryptoWall 3.0 files are encrypted. You can only open them once they are decrypted using a specific decryption key for the particular algorithm.
What to Do If a Decryptor Does Not Work?
Do not panic, and backup the files. If a decryptor did not decrypt your .CryptoWall 3.0 files successfully, then do not despair, because this virus is still new.
Can I Restore ".CryptoWall 3.0" Files?
Yes, sometimes files can be restored. We have suggested several file recovery methods that could work if you want to restore .CryptoWall 3.0 files.
These methods are in no way 100% guaranteed that you will be able to get your files back. But if you have a backup, your chances of success are much greater.
How To Get Rid of CryptoWall 3.0 Virus?
The safest way and the most efficient one for the removal of this ransomware infection is the use a professional anti-malware program.
It will scan for and locate CryptoWall 3.0 ransomware and then remove it without causing any additional harm to your important .CryptoWall 3.0 files.
Can I Report Ransomware to Authorities?
In case your computer got infected with a ransomware infection, you can report it to the local Police departments. It can help authorities worldwide track and determine the perpetrators behind the virus that has infected your computer.
Below, we have prepared a list with government websites, where you can file a report in case you are a victim of a cybercrime:
Cyber-security authorities, responsible for handling ransomware attack reports in different regions all over the world:
Germany - Offizielles Portal der deutschen Polizei
United States - IC3 Internet Crime Complaint Centre
United Kingdom - Action Fraud Police
France - Ministère de l'Intérieur
Italy - Polizia Di Stato
Spain - Policía Nacional
Netherlands - Politie
Poland - Policja
Portugal - Polícia Judiciária
Greece - Cyber Crime Unit (Hellenic Police)
India - Mumbai Police - CyberCrime Investigation Cell
Australia - Australian High Tech Crime Center
Reports may be responded to in different timeframes, depending on your local authorities.
Can You Stop Ransomware from Encrypting Your Files?
Yes, you can prevent ransomware. The best way to do this is to ensure your computer system is updated with the latest security patches, use a reputable anti-malware program and firewall, backup your important files frequently, and avoid clicking on malicious links or downloading unknown files.
Can CryptoWall 3.0 Ransomware Steal Your Data?
Yes, in most cases ransomware will steal your information. It is a form of malware that steals data from a user's computer, encrypts it, and then demands a ransom in order to decrypt it.
In many cases, the malware authors or attackers will threaten to delete the data or publish it online unless the ransom is paid.
Can Ransomware Infect WiFi?
Yes, ransomware can infect WiFi networks, as malicious actors can use it to gain control of the network, steal confidential data, and lock out users. If a ransomware attack is successful, it could lead to a loss of service and/or data, and in some cases, financial losses.
Should I Pay Ransomware?
No, you should not pay ransomware extortionists. Paying them only encourages criminals and does not guarantee that the files or data will be restored. The better approach is to have a secure backup of important data and be vigilant about security in the first place.
What Happens If I Don't Pay Ransom?
If you don't pay the ransom, the hackers may still have access to your computer, data, or files and may continue to threaten to expose or delete them, or even use them to commit cybercrimes. In some cases, they may even continue to demand additional ransom payments.
Can a Ransomware Attack Be Detected?
Yes, ransomware can be detected. Anti-malware software and other advanced security tools can detect ransomware and alert the user when it is present on a machine.
It is important to stay up-to-date on the latest security measures and to keep security software updated to ensure ransomware can be detected and prevented.
Do Ransomware Criminals Get Caught?
Yes, ransomware criminals do get caught. Law enforcement agencies, such as the FBI, Interpol and others have been successful in tracking down and prosecuting ransomware criminals in the US and other countries. As ransomware threats continue to increase, so does the enforcement activity.
About the CryptoWall 3.0 Research
The content we publish on SensorsTechForum.com, this CryptoWall 3.0 how-to removal guide included, is the outcome of extensive research, hard work and our team’s devotion to help you remove the specific malware and restore your encrypted files.
How did we conduct the research on this ransomware?
Our research is based on an independent investigation. We are in contact with independent security researchers, and as such, we receive daily updates on the latest malware and ransomware definitions.
Furthermore, the research behind the CryptoWall 3.0 ransomware threat is backed with VirusTotal and the NoMoreRansom project.
To better understand the ransomware threat, please refer to the following articles which provide knowledgeable details.
As a site that has been dedicated to providing free removal instructions for ransomware and malware since 2014, SensorsTechForum’s recommendation is to only pay attention to trustworthy sources.
How to recognize trustworthy sources:
- Always check "About Us" web page.
- Profile of the content creator.
- Make sure that real people are behind the site and not fake names and profiles.
- Verify Facebook, LinkedIn and Twitter personal profiles.



great information! I was infected with the “CRYPTOWALL 3.0” virus recently, it was downloaded from my need to download Google Chrome and the latest Chromecast. It continued to download malware which was very disturbing. If you have heard about this happening when Google Chrome was installed, would you please pass it on to all of your followers.
thank you and best regards!
greg
Bonjour tout le monde voici une solution, comment protéger vos fichier et documents de ce virus CryptoWall
youtube.com/ watch?v=kRpJEpJzK1U
Hi Anticryptowall,
Are you sure that your method works?
Hi Milena Dimitrova
i did that experience so many times on image disks by various viruses especially by crypto viruses and The result was always positive…
Hi again,
What about CryptoWall 3.0, in particular?
my boss got hit and his memory stick was encrypted. he purchased a new memory stick from sandisk that came with a one year subscription to “RescuePRO”and he was prompted to recover files-he inserted his infected stick and the software restored his files onto his new stick and now his files are in a safe VAULT on the new stick.
please let me know if there is some solution. I was also caught by this while trying to upgrade Chrome. I am in desperate need of a solution as I don’t have any back ups. Every Microsoft file is infected and decrypted
me too. all my files can’t be open.
With me also and I also do not restore because this feature is not turned on my computer.
Please someone?
please helppppppppp all my files were protected by a strong encryption with RSA-2048.
Hello, Tony!
CryptoWall is indeed a nightmare and we are sorry to read that you have been affected by it. RSA algorithm has been deployed by many ransomware threats. You can be sure that many users and security specialists have been trying to break the RSA-2048 encryption. More about the RSA-2048 encryption key that has been targeting computers find here: sensorstechforum.com/remove-rsa-2048-encryption-key-from-cryptowall-3-0/
RSA-2048 can be broken if someone finds a way to create collisions that inherently reduce the expected number of combinations to crack the cipher. Being a cipher, the RSA-2048 algorithm can be cracked by brute force. Brute force cracking can be described as a trial-and-error technique employed by programs to decipher encrypted data like passwords and DES (Data Encryption Standard) keys via extensive effort instead of intellectual force.
RSA encryption is a type of language that alters the normal code of the file with a unique key. This key can be decrypted via specific software, but it requires a powerful machine. More on the RSA encryption topic and how to remove CryptoWall manually: sensorstechforum.com/restore-files-encrypted-via-rsa-encryption-remove-cryptowall-and-other-ransomware-manually/
Finally, our research team has compiled several easy steps to follow to protect your files from ransomware threats: sensorstechforum.com/cryptowall-aaa-files-ransomware-description-protection-and-removal/
Additionally, if you want to learn more about the methods employed by CryptoWall and the cyber criminals behind it, you can refer to this article: blog.trendmicro.com/trendlabs-security-intelligence/cryptowall-3-0-ransomware-partners-with-fareit-spyware/
Thanks, I removed the virus with SpyHunter but my files are still corrupted and i cannot open them. Please help me… how to repair them????
YOU ALL SOOO SCREWED…
With original file, encrypt file and public key used to encrypt file, can you decipher other files that used that public key?
jeg fik hele mit data drev krypteret af cryptowall 3.0 igennem ransomware(conhost) og den havde enda kryptere min gendanelsespunkter og backup den eneste måde jeg fik mine filere igen var ved hjælp af recuva da cryptowall sleter original filen og overskriver dem med en krypteret
I have files that cannot be opened too.
I am going to pay the ransom today or tomorrow.
I have heard that if we pay the ransom the unblock all the files for sure (99% sure).
They don’t want the files. They just want the money.
I try everything to unblock my files. Even new karpersky software. Nothing works.
Did some one have the same experience?
Did someone pay the ransom before?
What happened?
I will leave my experience here soon.
Hi joao,
First of all, sorry to hear you’ve suffered a CryptoWall 3.0 attack!
Can you please start a topic in our forum – sensorstechforum.com/ forums/malware-removal-questions-and-guides/? We will try and help you with whatever we can. The forums are more convenient for such discussions :)
Stay tuned,
the STF team
Hi joao,
Did you pay it? What the result?
I have the same problem but i’m trying to solve it..
Hola Joao, trabajo como técnico en una empresa y unos de los gerentes, fue ataco por este virus, me gustaría saber si pudiste recuperar la información luego de realizar el pago, y que cantidad de información, pudieron recuperar?
have you paid them >?? and recovered your files or not ?
buenas tardes, mi caso es que el equipo fue infectado con el virus, formatee el equipo pero toda la información abre. tengo informacion de vida o muerte y me urge recuperarla. alguien que me pueda colaborar. por favor
hmm..
si può restituire il sistema indietro, ma è possibile solo in caso che abbia fato il backup prima.
Se no- puoì scaricare quelche programma di ricuperazione come recuva ,getdatabach o diskdrill..però, purtroppo tali software non recuperanno il 100% ,solo i dati eliminati recentemente . ecco uno dei tali programma cleverfiles.com/disk-drill-windows.html
forse ti aiuti,
Hello, Fornerino
In case you have been infected with Cryptowall, it is important to know that it uses a VERY strong algorithm, called RSA-2048. Its decryption may take years to complete. We advise you to try restoring your files by going to a professional data recovery expert or attempting to use on of the aftermentioned tools:
Kaspersky Rector Decryptor
This decryption tool is very simple to use and
support.kaspersky.com/viruses/utility#rectordecryptor” support.kaspersky.com/viruses/utility#rectordecryptor
EaseUS Data Recovery Wizard Free
Here is a free program which uses different methods to search through your computer and recover files that are even deleted beyond all saving. It is no guarantee that it will work, but some say they have recovered at least 10 percent of their files and some other files were partially broken. So in case you want to try it out, here is the download link for the tool:
easeus.com/datarecoverywizard/free-data-recovery-software.htm
easeus.com/datarecoverywizard/free-data-recovery-software.htm
Shadow Explorer
You may as well try running Shadow Explorer in case you have File History or backup enabled. You can download it from here, but note that TeslaCrypt may as well have malicious scripts that delete any backups and previous file versions. Here is the download link for Shadow Explorer:
shadowexplorer.com/downloads.html
shadowexplorer.com/downloads.html
Look for the latest version and you may as well download the portable one since it saves you time.
This is as far as I can suggest, try it and reply whether or not you have been successful. Again, there is absolutely no guarantee that any of the methods are working, but we are talking about encrypted files here, after all so it may be worth the try.
My all files are encrypted with RSA-4096.
I can not open any file.They are asking for 500 USD for decryption key. Please anybody can help me to decrypt my files as i don’t have any backup restore.
Hi Sham,
First, can you please tell me how you got to know that RSA-4096 was used in your case?
Slt Milena!
Comment tu vas? j’aimerais avoir des notions sur le cryptage, comment cela se passe, avoir un cas pratique!
Merci d’avance! je laisse mon mail ou si je peux avoir le tien cela me sera d’une très grande utilité
hi Milena..
I found a ransomware file in my every folder…
Hi Sham, looking into your case as we speak!
Dear Milena,
Waiting for your help….your earlier response will be favorable.
Thanks
Hi Sham,
A topic has been started in our forum about the particular encryption: sensorstechforum.com/forums/malware-removal-questions-and-guides/help!-my-files-were-encrypted-with-strong-rsa-4096-encryption!/msg679/#msg679
Please provide us with the following information there (it’s easier to discuss in the forum than here) – your system, exact file extensions added to the encrypted files, ransom notes, etc. Also, have you removed the Trojan that has dropped the ransomware?
Hello SERAS,
I am fine but really sorry to see so many people falling victims to ransomware. You can send us information about your ransomware case on idunn0 @ abv.bg.
Todos mis archivos está con extensión vvv no sé cómo desencriptar los estoy muy angustiado por favor ayuda ya elimine Cryptowall tengo encriptados toda mi información de 20 años de trabajo por favor ayuda
Hi Jorge,
I am deeply sorry to let you know that without a clean copy of your files, you most likely will not be able to restore your information. You can try using TeslaDecoder and Rakhnidecryptor. However, reports indicate that these decoders won’t help with the .vvv extension that belongs to TeslaCrypt ransomware: sensorstechforum.com/remove-teslacrypt-and-restore-vvv-encrypted-files/
Have you removed the ransomware with an anti-malware program?
E’ successo anche a me. Il problema e’ che ogni file ha un’estensione diversa 0A/0A1/OMF ECC
Si puo’ fare qualcosa?
Hi, I also caught this virus but it was only too late that I realized it and now all my files are encrypted with RSA-2048. The file extensions were changed and it seems that the extension for each file is different from any other and none are the same. Some of the file extensions I see now are .p468t,.16G, .n7r0, .us7m, .25sq, .xo3r4 and so many more. I need help.
Hello @dbgn
This is typical for Ransomware infections such as CTB Locker and CryptoWall 4.0. In order for me to be able to adequately provide you with assistance I would like you to send me a snip or a screenshot of any ransom message that you may see. It may be a .txt file on your desktop or a picture.
sensorstechforum.com/forums/malware-removal-questions-and-guides/files-encrypted-with-random-file-extensions/
hello , I invierei a file , but I do not know ‘ how to attach it to this message
hello vencislav
mz laptop is infected with thee teslacrzpt virus and all mz files are encrzpted with RSA-4096 key
could zou help me_ please
Hi, Friends! My Pc was infected, i do eliminate ransomware using spyhunter, but muy files stay encrypted with .MICRO extention. ¿How i can decrypt the files? Thanks!!
Hello Ter,
You have been infected with a variant of TeslaCrypt. For more information check the following article:
sensorstechforum.com/remove-teslacrypt-3-0-and-restore-micro-encrypted-files/
You may also send files so that we can try and help to decrypt them. Here is the address:
idunn0 @ abv.bg
We will disclose your files and send them back to you if successfully decrypted. Bear in mind that since we receive a lot of files it may take some time.
Hi Milena , one of our system got infected with this cryptowall 3 and encrypted the files with .micro extension. I was able to remove the malware but after two days, one of our Network attached storage got affected as well. Now I am wondering how that is possible ? I thought only personal files got affected by this script.
Hello Shihas,
Ransomware is often used in attacks on companies. The bad news is there’s still no solution for .micro encrypted files. We assure you however that security experts (us included) are doing their best to fight this threat and beat its encryption.
i was installed a software .after my .jpg,.mp4 files are changed into a .micro extension .pls help to how to get my old file format .
Hi Nani,
Unfortunately, you have been attacked by the latest version of TeslaCrypt ransomware. We are still trying to figure out how to decrypt files encrypted by it. Once we find a solution, we will share it.
Have you removed the ransomware from the infected computer?
Hello! My laptop is infected with Cryptowall3.0. I’ve cleaned it, but all my files are encrypted. Any news on how to dectrypt them?
Thank you!
Il est à noter qu’Europol a pris conscience du problème des ransomwares et propose dorénavant un portail en ligne pour aider les victimes secuweb.fr/europol-portail-lutter-ransomwares
Merci beaucoup :)
I have removed the ransomware but now i have encrypted files ending with .albigec. Does anybody now how to decrypt the files? (Cryptowall 3.0)
My files are encrypted with RSA2048 algorithm ransomware. I need a decryptor for this immediately. Please help
Hi,
My files were encrypted way back in 2015 ( by Cryptowall 3.0) I still have the files with me and the instructions to pay up and retrieve my files. Is there any way to retrieve these files through free or paid means?
Hi Naveen,
Unfortunately, this ransomware case remains unsolved, as no official decrypter has been released to this day.
Hi, there is some good solution to encrypt my files please before sending them to my collaborators as you know we’re obliged to work home ? Many thanks.