A recent security notice reveals that a dangerous new malware has hit mobile devices — the Rotexy Android Trojan. The reason why it is deemed a critical threat is that it leads to several different types of abusive actions and is thus classified as a hybrid threat.
Rotexy Android Trojan Classified as a Hybrid and Very Dangerous Mobile Malware
The Rotexy Android Trojan has been found to spread mainly by an organized [wplinkpreview url=”https://sensorstechforum.com/remove-smishing-scam-landing-pages-protect/”]smishing landing pages scam. This is a popular hacker tactic that relies on impersonating well-known companies or services and sends fake notifications via SMS messages. The targets will be coerced into opening up links or downloading certain applications from a repository using different typical scenarios. Popular examples are software update notifications or feature additions to the devices.
Once the Trojan code is deployed it will start the infection engine which runs these two processes:
- Security Bypass — It will scan for any anti-virus or virtual machine hosts and disable their real-time engines. This is done in order to avoid detection.
- Persistent Installation — The Trojan will install itself in a way which makes it very difficult to remove using manual methods. This is done by modifying system components, configuration files and boot options.
Following the successful initialization it will initiate a connection to a hacker-controlled server which will allow the criminal operators to spy on the users in real-time. The analysis shows that all correspondences and phone contacts are forwarded to the hackers in real-time.
The Rotexy Android Trojan exhibits an interesting scam tactic of enticing the victims into thinking that they have received a money transfer. They are requested to “validate” their credit card information by presenting a field. To make it look like a legitimate service it includes a credit card validation check which makes sure that the entered details are correct. As soon as they are entered correctly the details will be sent to the criminal operators.
Some configurations and samples of the Trojan have been found to also institute a lockscreen which displays a phishing page and extorts the victims to pay a “fine for viewing prohibited videos”. This is a typical scareware tactic that is often used by ransomware infections.
How To Remove Rotexy Android Infections
The security reports indicate that it is possible to remove active infections of the current configuration associated with the Rotexy Android Trojan. This means that any updates or future releases will probably use a different mechanism and will require specialist help. However taking advantage of the fact that the infected devices are controlled via SMS messages the analysts have developed a way to remove active infections.
Preparation before removal of malware.
Before starting the actual removal process, we recommend that you do the following preparation steps.
- Turn off your phone until you know how bad is the virus infection.
- Open these steps on another, safe device.
- Make sure to take out your SIM card, as the virus could corrupt it in some rare cases.
Step 1: Shut Down your phone to win some time
Shutting down your phone can be done by pressing and holding its power button and choosing shut down.
In case the virus does not let you do this, you can also try to remove the battery.
In case your battery is non-removable, you can try to drain it as fast as possible if you still have control over it.
Notes: This gives you time to see how bad the situation is and to be able to take out your SIM card safely, without the numbers in it to be erased. If the virus is on your computer, it is espeically dangerous to keep the sim card there.
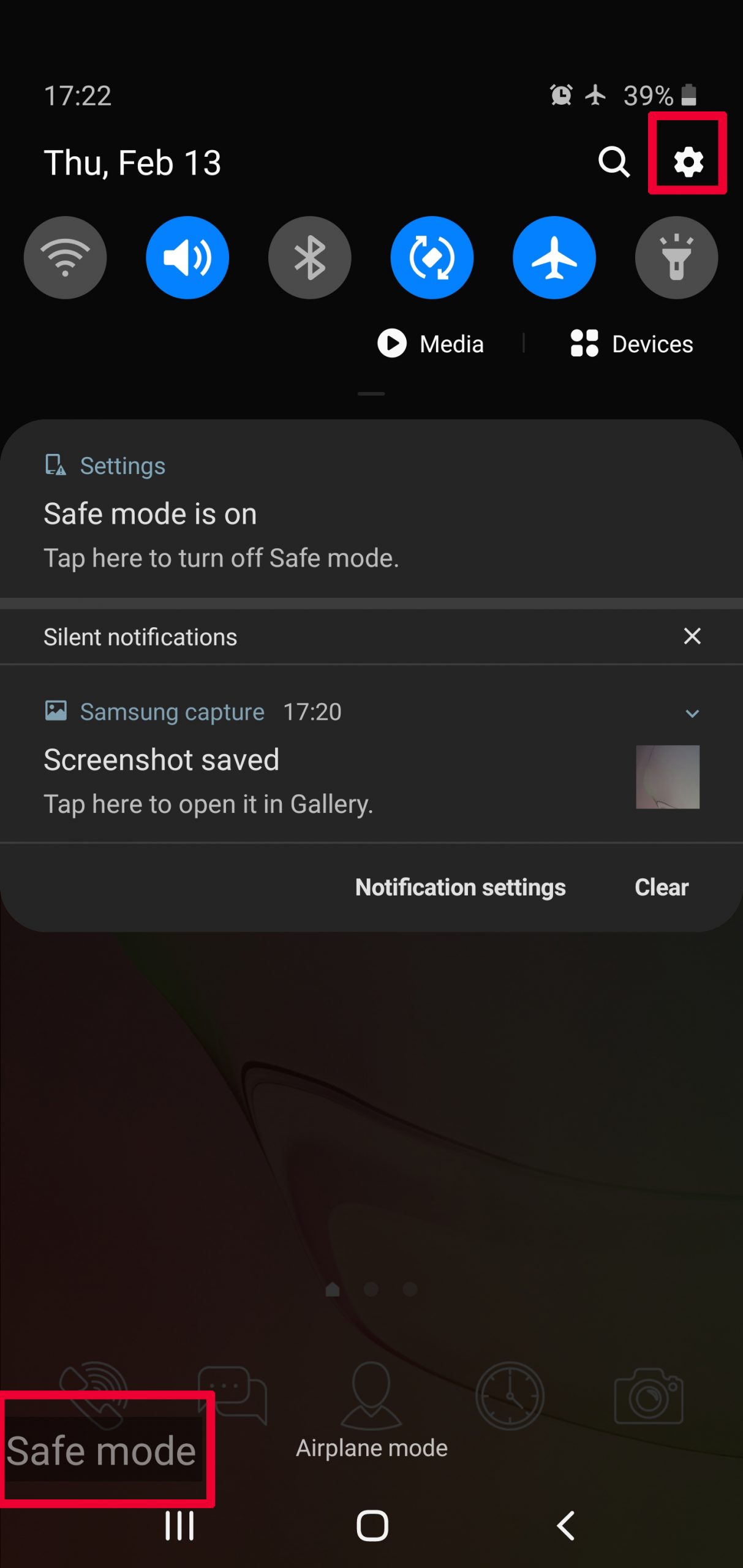
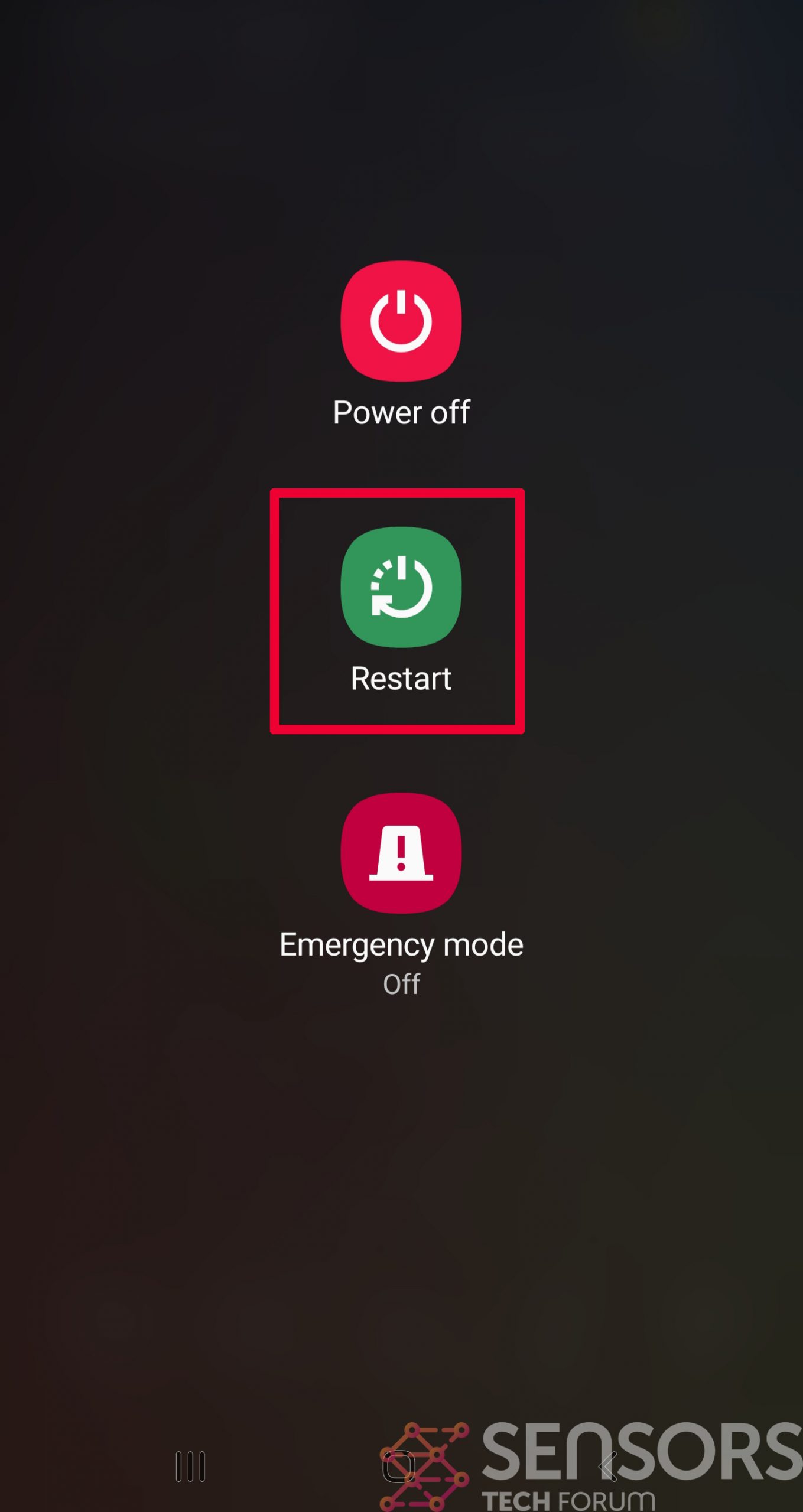
Step 2: Turn on Safe Mode of your Android device.
For most Android devices, switching to Safe Mode is the same. Its done by following these mini-steps:
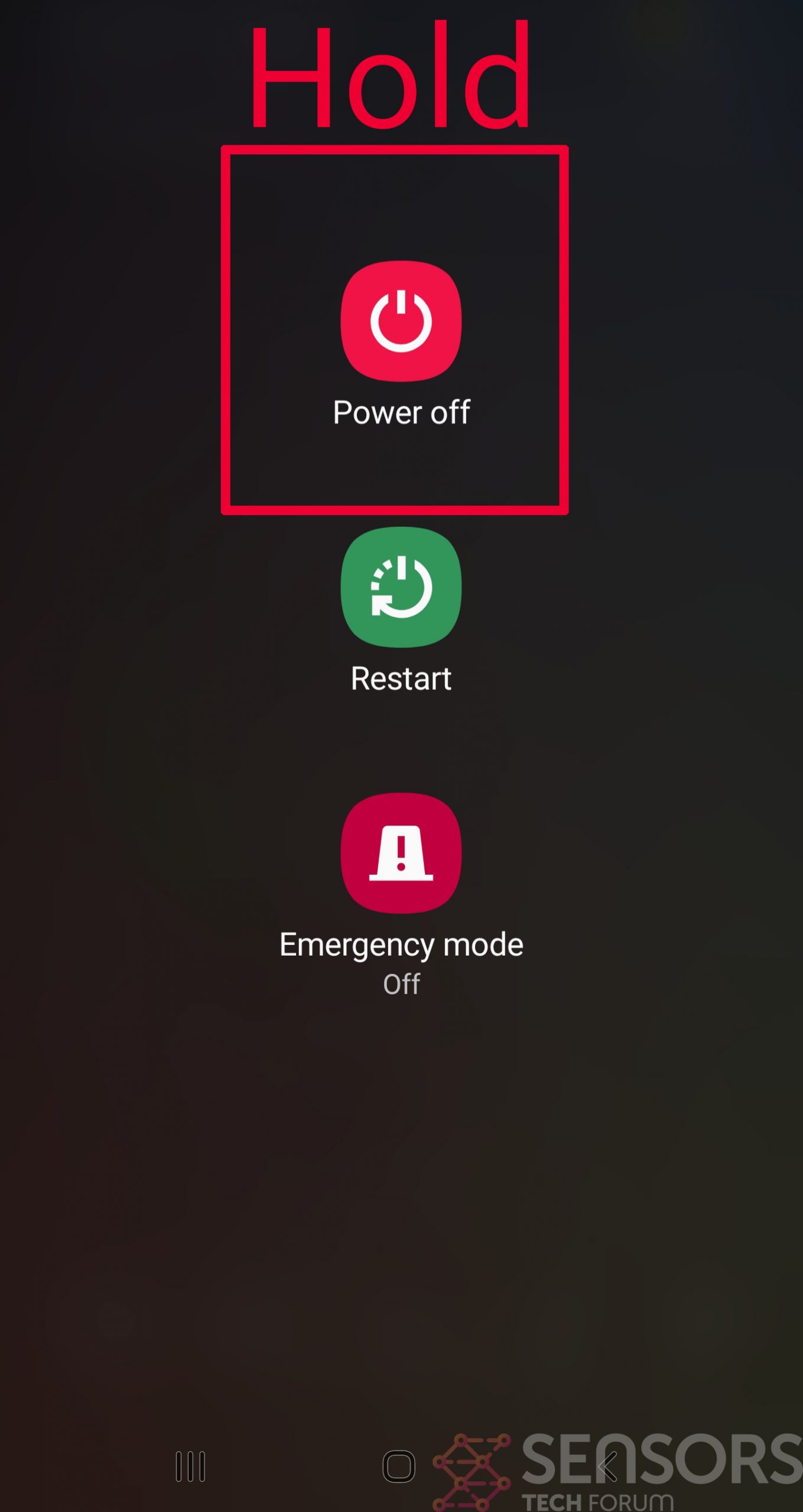
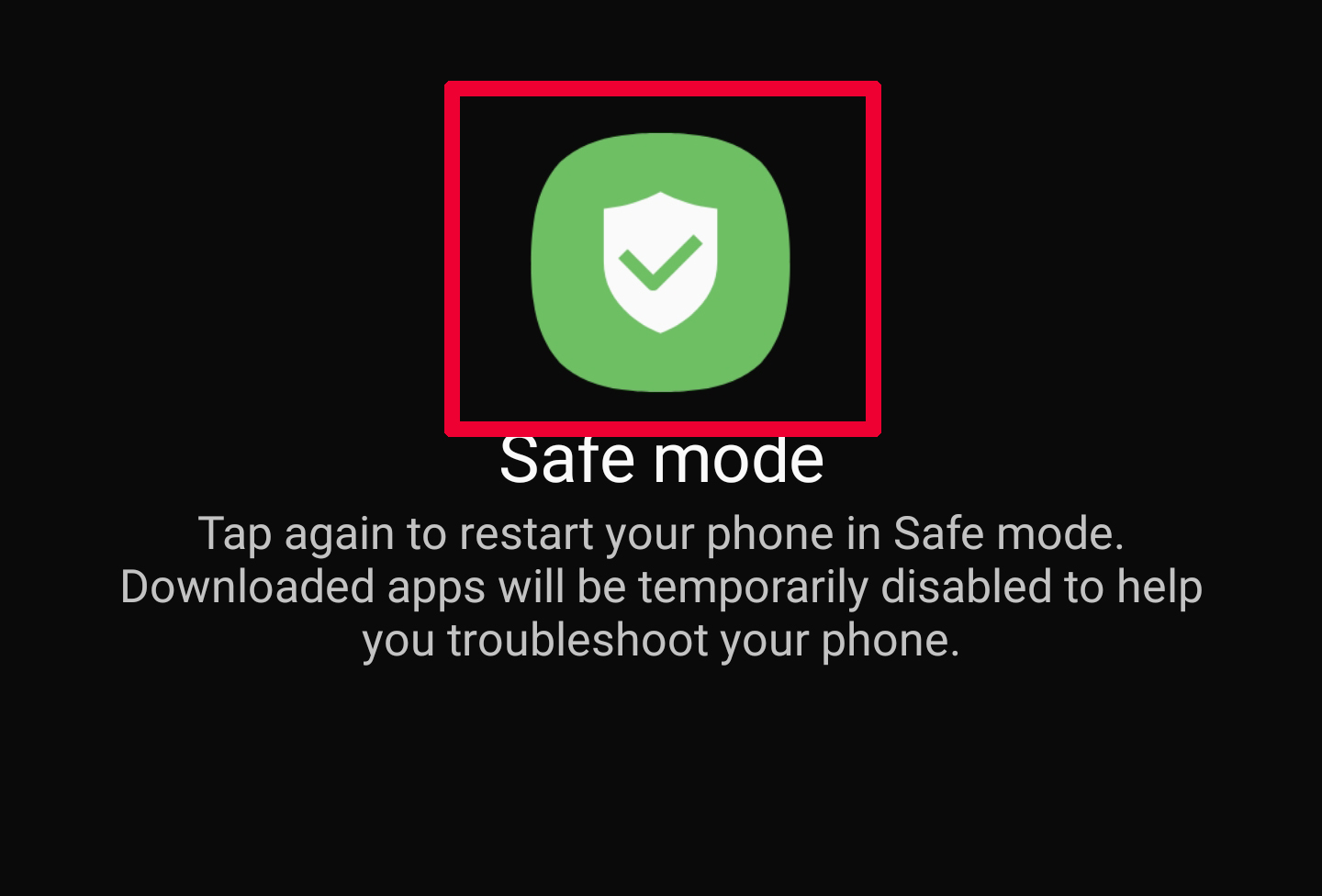

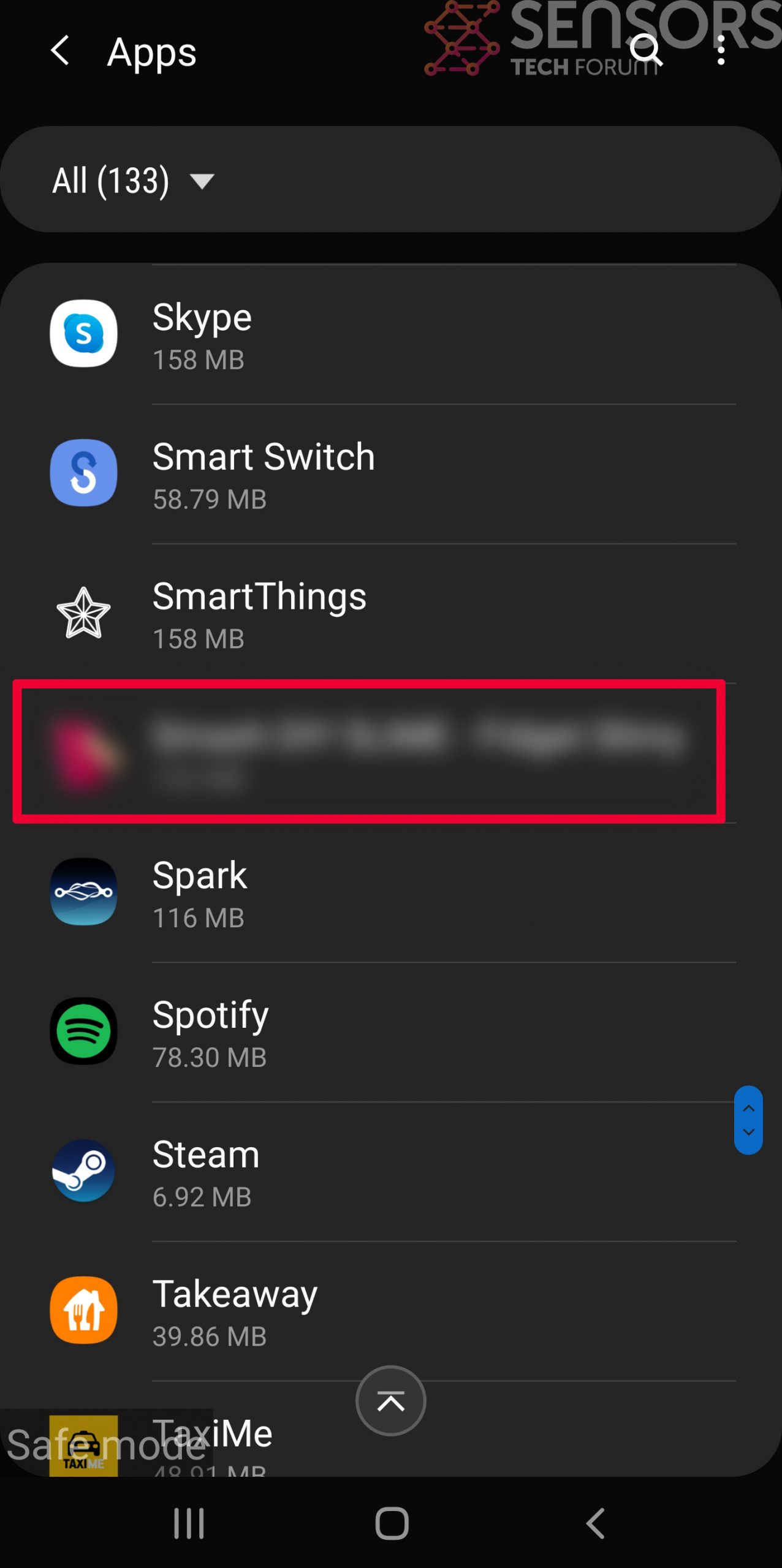
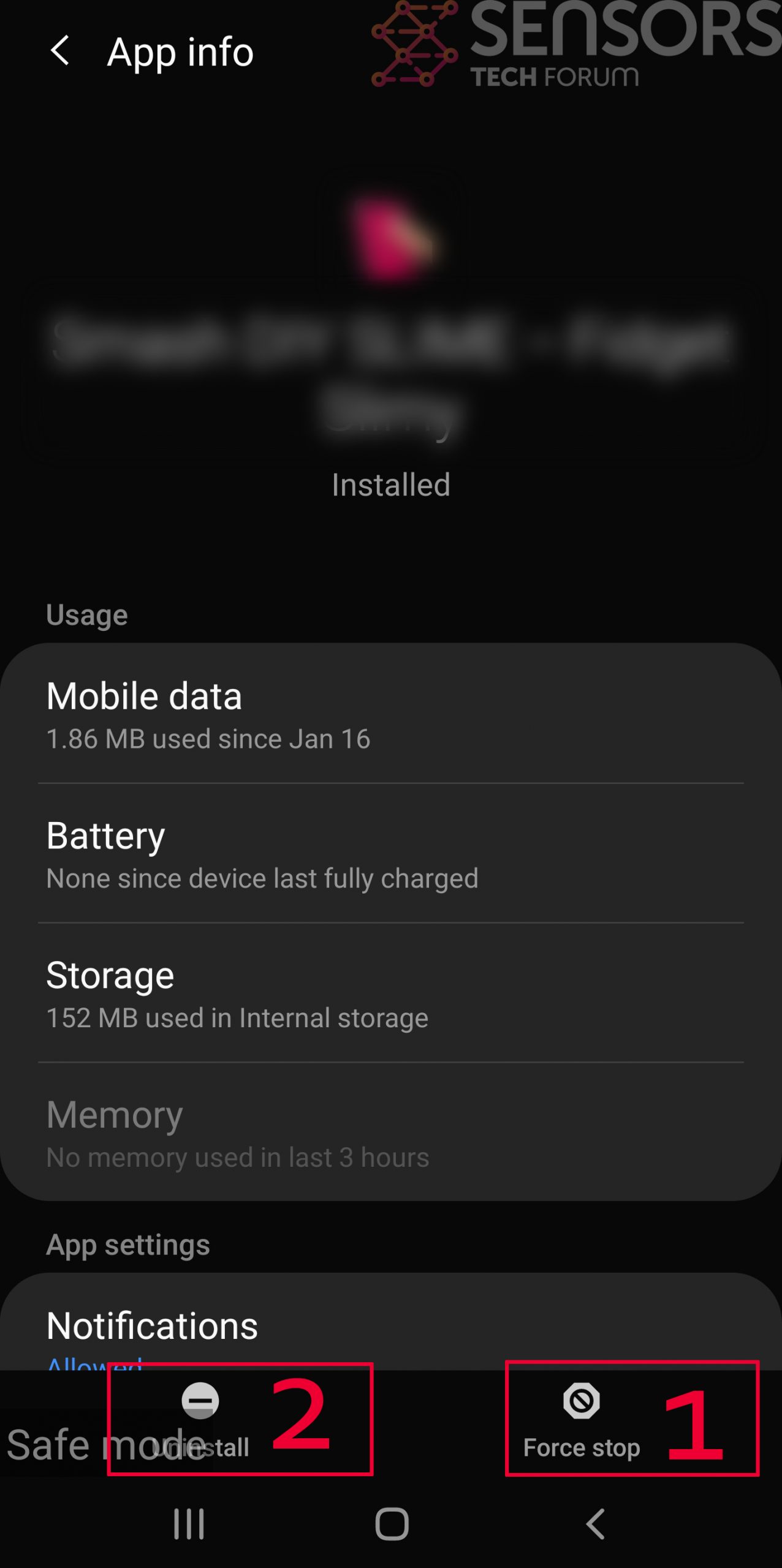
Step 3: Eliminate the App that Your Believe is the Virus
Usually Android viruses get masked in the form of applications. To eliminate apps, follow these mini-steps:
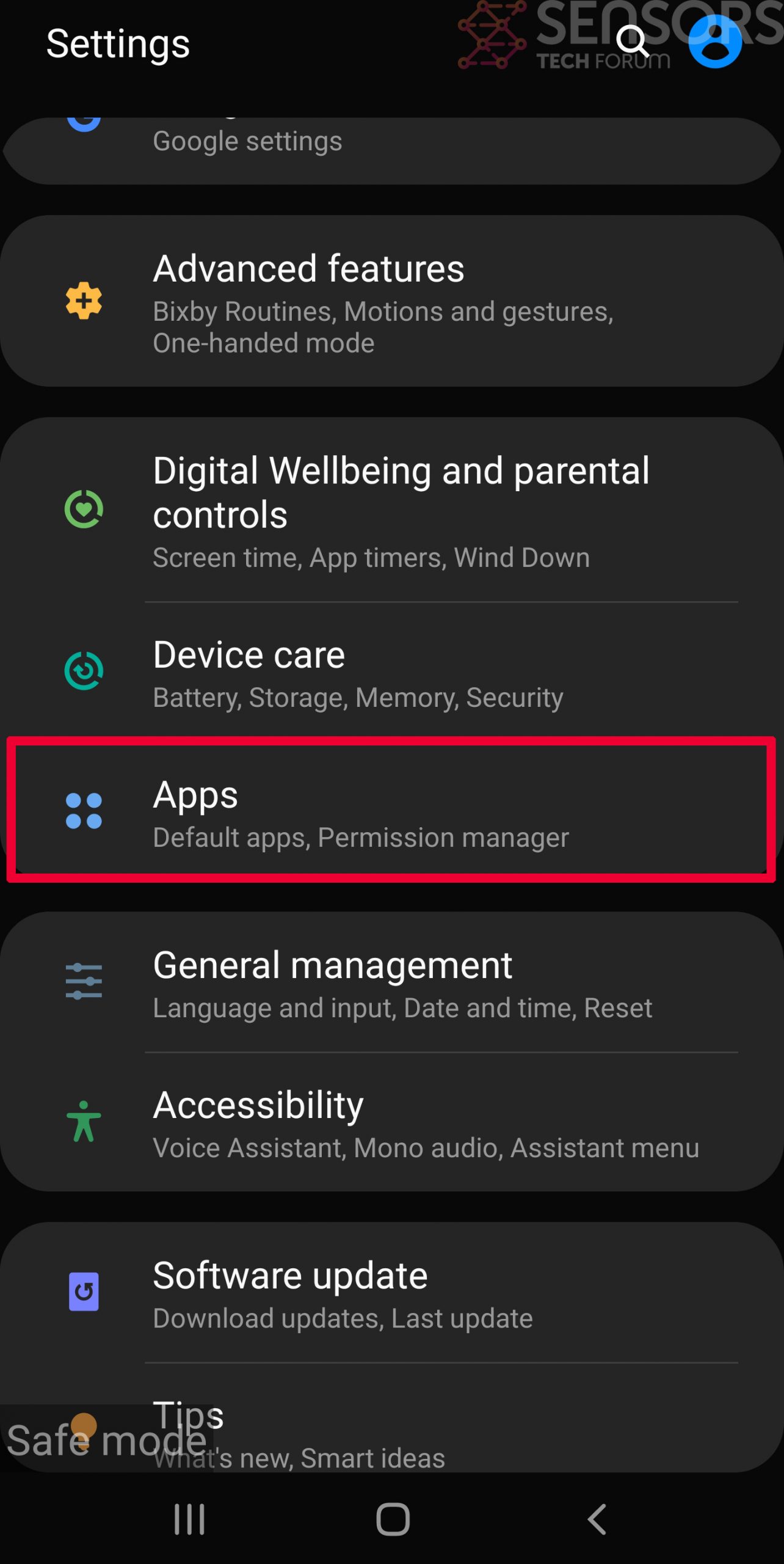
Step 4: Find Hidden Virus Files on Your Android Phone and Remove Them
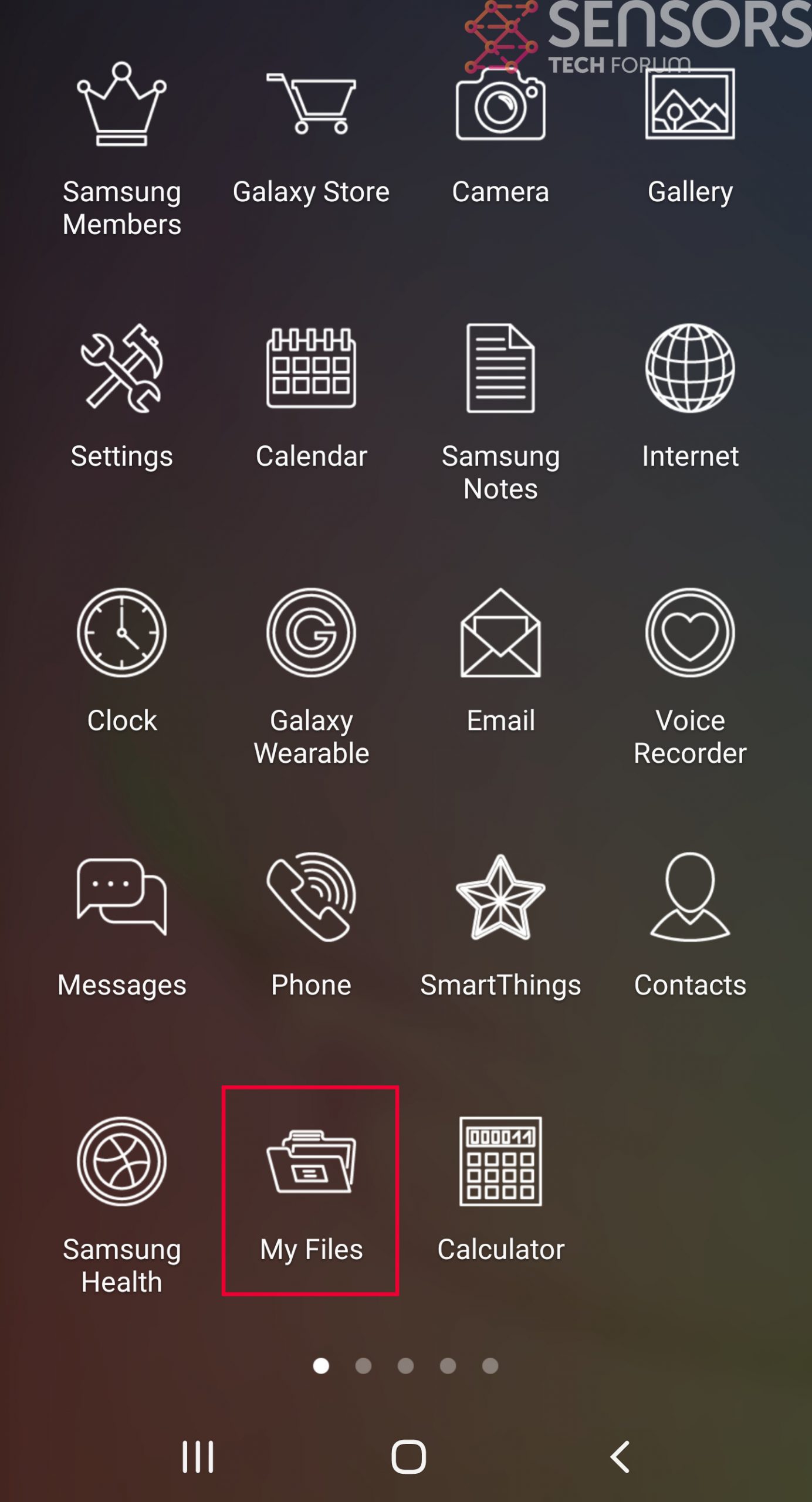
Simply locate the virus and hold-tap on the virus file to delete it.



