The cyber criminals are getting more and more inventive. They are making different attempts to disguise the malware they have created and present it as useful application. Gomal developers however, went an extra mile when creating the new mobile Trojan. The camouflage they used was really creative since they added to their malicious program a game of Tic Tac Toe. Further to that, they implemented modern and interesting techniques, which are new to that type of malware.
How we learned about that? A game of Tic Tac Toe was sent to the malware researchers for analyses. At first, everything looked ok and the app seemed harmless.
The malware analyzers were set on the alert by a list of several permissions that were requested by the game. Questions were raised – Why do we need internet to play the game? Why does this application request access to the user’s contacts? Why does it need access to the SMS archive or to the process calls?
After a careful research, the malware specialists found out that this is not a game, but a creative multi-purpose spyware. After that the malicious app was marked as Trojan-Spy.AndroidOS.Gomal.a in the Kaspersky Lab products.
The detailed analysis of the game later revealed that the malicious program takes 30 % of the executable file’s size and the rest of the file is used for stealing of personal data and for spying on the user.
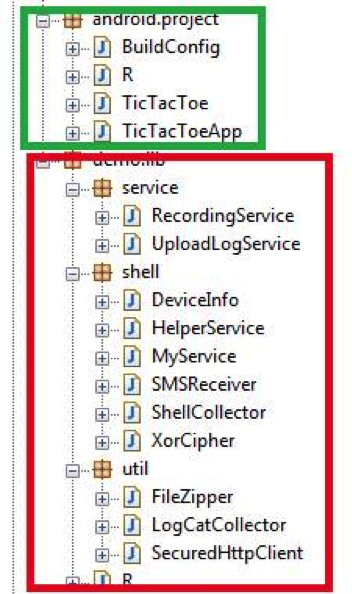 The game code is marked in green, the malicious functionality is marked in red.
The game code is marked in green, the malicious functionality is marked in red.
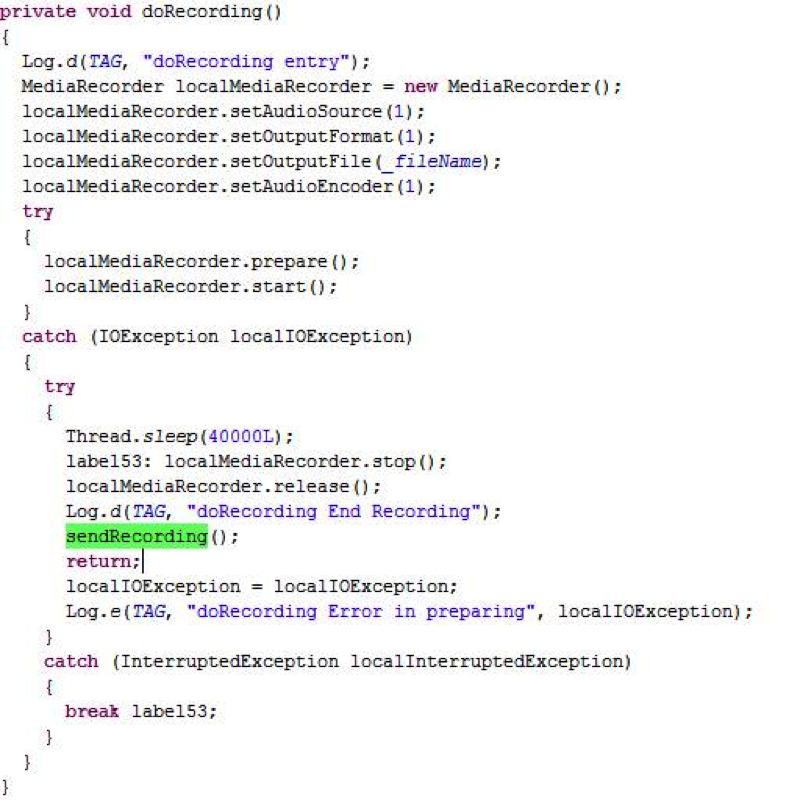
The users have certain questions concerning the functionality of the malware and what does it include. The experts say that this malware has sound recording functions, which are standard for the mobile spyware.
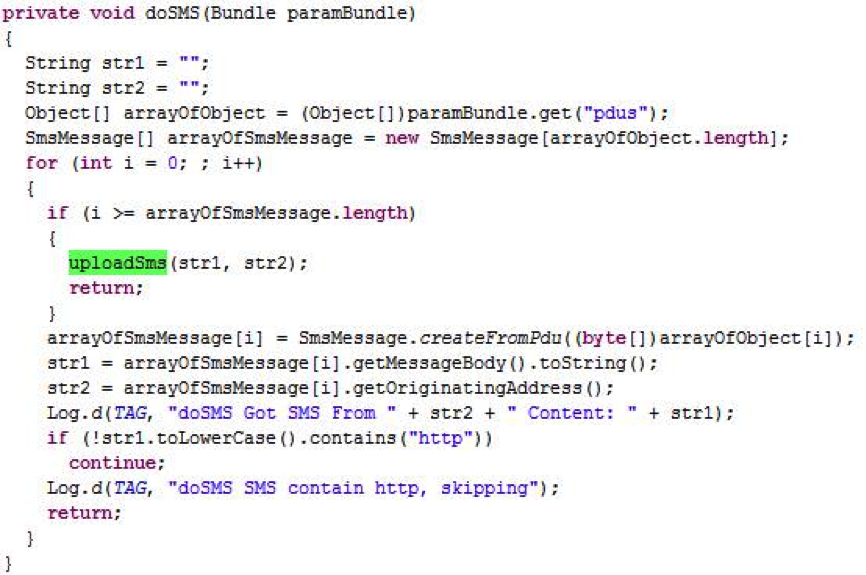
The malware further has functionality for stealing of SMS:
Besides that, this Trojan is also collecting information about the device that is used and sends the data that has been collected to the server of the cyber criminals.
Trojan-Spy.AndroidOS.Gomal.a further delivers interesting libraries that are distributed with it.
What does this mean? The package of libraries that comes features an exploit that is applied in order to get root privileges on the Android device. These additional privileges allow the app access to different Linux services plus the ability to read process memory and /maps.
When the Trojan gets root access, it can do various mischiefs. For example, it can steal emails from the Good for Enterprise app (if it is installed on the smartphone). In this way it can steal important corporate data. The Trojan uses a console to attack the Good for Enterprise app and to get hold of the ID of the process, then it reads the virtual file and maps. In the file is set information concerning the memory blocks that are allocated to the application.
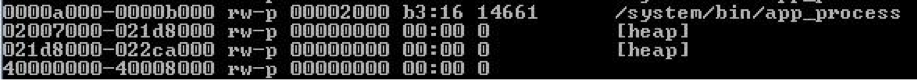
Once the Trojan gets the memory blocks list, it finds the block that keeps the string data of the applicant and creates its dumb by using a library from the package. The dumb file that is created by the malware searches for emails’ signatures characteristic of and then the messages that are found are sent to the server of the cybercriminals.
Gomal is also capable of stealing data using logcat – this is the logging service that is built into Android and is used for debugging of the applications. In fact, the applications of the developers are often outputting important data to Logcat, both before or after the apps have been released. This allows the Trojan to steal confidential data from the other programs.
The Verdict
Tic Tac Toe looks like a harmless game and yet in this case it gives the cyber criminals an access to a large amount of personal data and corporate data. The Gomal malware techniques that are applied here were first implemented in Windows Trojans, however now they are applied in the Android malware as well. This technique can be used to steal data from various applications besides Good for Enterprise – it can attack messengers, emails and programs.
How to reduce the risk of mobile malware infection?
In order to successfully reduce the risk from mobile malware infection, the users should do the following:
- Never activate the option “Install applications from third-party sources”.
- Install applications from official channels only (Google Play, Amazon Store, etc.).
- Study the rights that the new apps request when they are installed.
- In case the requested rights are not in correspondence to the intended functions the app’s, do not install it.
- Work with protection software.