|
PRICE
|
TOTAL SCORE
|
OS
|
VPN
|
ENCRYPTION
|
TRACK BLOCK
|
FINGERPRINT
|
|
|||
| 1 |

|
Blackphone 2
See Review |
$735 |
    
|
PrivatOS |  |
AES-256 |  |
 |
|
| 2 |

|
DTEK60
See Review |
$399 |
    
|
DTEK OS |  |
AES-256 |  |
 |
|
| 3 |

|
Samsung S9
See Review |
~$730 |
    
|
Android 8.0 |  |
AES-256 |  |
 |
|
| 4 |

|
Sirin Solarin
See Review |
$16000 |
    
|
Android 5.1 (Custom) |  |
AES-256 |  |
 |
|
| 5 |
|
Google Pixel 2
See Review |
~$900 |
    
|
Android 8.0 |  |
AES-256 |  |
 |
|
| 6 |

|
K iPhone
See Review |
$4500 |
    
|
iOS |  |
AES-256 |  |
 |
|
| 7 |

|
Turing Phone
See Review |
$1000 |
    
|
Sailfish OS |  |
AES-256 |  |
 |
|
| 8 |

|
Boeing Black
See Review |
$650 |
    
|
Android (custom) |  |
AES-256 |  |
 |
|
| 9 |

|
UnaPhone Zenith
See Review |
$539 |
    
|
UnaOS™ |  |
AES-256 |  |
 |
|
| 10 |

|
D4 HTC A9
See Review |
Depends |
    
|
Android (Custom) |  |
AES-256 |  |
 |
|
|
Looking for newer devices? Check out our new review on Which Are the Most Secure Smartphones in 2019:
The smartphone has become so important for our daily lives that we cannot imagine our life without it. When we talk about secure and private smartphones, the subject always depends. This is primarily because of the changes in 21st century regarding the Internet’s freedom and privacy. Ever since the introduction of the Rule 41 has been passed by the US congress, the smartphone security has become a very interesting subject to discuss. And in the same time, we have malware which is also quite the subject to mess with, because of the variety of malware that Is out there. So when we begin to discuss smartphones, we should point out several areas that you will need to focus on when trying to use a smartphone for security purposes:
- What are you going to use the smartphone for?
- Are you going to use a SIM card or are you only going to use the smartphone for internet connections?
- Are the services that you will be using going to request information from you?
- Do you believe in biometric security and is It important for you?
- Is your smartphone usage going to focus on privacy or malware security more?
And when it comes to the changing and volatile times that we live in, secure behaviour is not restricted to one device only, but comes down to what type of security system are you focused on building for yourself or your enterprise. If you are aiming at a security system that is solely focused on protecting your computer against data thiefs and hackers, then a you should focus more on the entire network that you are running to be developed in a secure manner.
What Types of Malware and Privacy Threats Exist?
In these troubled times, each segment of our data is saved online and most of all our personal information, financial data as well as other important information, including paying with our smartphone has become a target for the cyber-criminals. This has created a whole new type of cyber-threats that are related to this. The malware and privacy dangers that exist out there vary from financial theft viruses to spyware that can even enable your microphone to listen in. In addition to this, ransomware viruses are still continuing to spread with even more alarming rates in 2018, and they hve begun to shift to Android devices. Financial theft malware has also evolved and can now steal your cryptocurrency wallet if it’s stored on your PC. In addition to this, there are the ever-existing types of dangers, like the scammers and the phishing attacks which are conducted by the millions each day and can quickly steal your data if you are not careful.
How to Choose a Secure Smartphone for Your Situation?
There are different smartphones that are secured in a different manner. Some smarthones are more privacy-oriented, while there are other devices that rely more on using encryption and secure boot to secure you against prying eyesand malware. There are also different devices that offer various features for the prices they are offered on, but keep in mind that good prices do not always mean that the device is as secure as the ones that are more expensive. At the end it all leads to you – the user of the phone and your security requirements. So, let’s begin with our countdown of the top 10 most secure phones that you can buy.

What appears to be the most well-known and purchased business phone with various security layers, the Blackphone 2 is a device, capable of running multipled operating systems and has recently won awards for it’s security-oriented design.
Privacy
When we talk about the privacy of the Blackphone 2, the device has a specific operating system, which is it’s main strenght in this sector. Called Silent OS or PrivatOS, it is created from the core to be private by design. The OS has a privacy feature embedded in it’s device which constantly encrypts each single text message and application for communication. The privacy feature even extends it’s reach to encrypting active calls, making it virtually impossible for the informaition during the phone call itself to be monitored. In addition to this, the operating system also makes it possible to control each application separately and to make an informed decisiona s to what you allow this app to extract from your phone.
Security
The operating system of the Blackphone 2 is created to be secure by design. It includes pre-loading of applications, which means that it has the capability to run apps in a controlled environment, providing the ability to control of what you want to share as data.
In addition to this, SilentOS also has a feature, known as Spaces. It enables virtual environments which you can create separately and let them work divided. To better explain this, let us assume that you want to store your personal information on one Android device, like a separate phone. To do this you can add a “Space” and use this space only to add the specific infomration you want to store, like photos, important documents and other information which can stay on this virtual Android. If another space on your Blackphone 2 is compromised, the information which you have on the separate space will remain safe and secure and you can use it to extract your data and then reset your device. This unique feature of the phone also makes it possible to customize each “Space” separately from the other and remain secure. You can also use another “Space” which you can risk being exposed, if you visit suspicious websites often, without exposing your important data in your space where it is stored.
In addition to this, when it comes to the support, the company promises 72 hours of deadline for patching any form of vulnerability that can compromise your device’s securty and they have also been reported to be very tech savvy, act quick solve issues fast. To conclude, the Blackphone 2018 and other Blackphone models are among the most secure mobile phones you can own, and all other phones in the category are just Blackphone alternatives.

BlackBerry has entered 2018 with it’s two phones one of which the DTEK60, specifically focused on security. The phones run a custom Android OS with various seucrity features, which value privacy as well as security.
Security
When it comes to the competition, BlackBerry is a company that has always been focused on the business user. So one of the benefits that the DTEK60 has in terms of smartphone security is that it’s support is on a vary adequate level and it’s updates are issued ASAP when a big has been reported and the patch comes to all the devices.
Furthermore, besides having a rugged Kernet, the device is also heavily focused on stopping any modificiations that may be done by malware or hackers to it’s firmware. Even though it runs an older version of Android (6), the smartphone has boot security and an extremely safe boot sequence process which it uses. In addition to this, the main purpose for which this smartphone has been create is to perform overview and modification of it’s software. Just like the DTEK50, which is the older model, it also has a DTEK software built in which allows you to monitor security in a user-friendly manner. Furthermore the DTEK software also makes it possible to take the necessary actions if you have detected a security issue on your smartphone.
The bottom line is that when it comes to the features-price graph, this phone would be high up on it, because it is a very decent choice for what it costs, hence it’s position on our list.

When it comes to smartphone security, the Samsung Galaxy is a device which is one of our top picks. The primary reason for that is because the smartphone has the specially modified Android which is highly customizable and with several tweaks can be turned into a mobile fortress.
Security
When we discuss the security of the Samsung S9, the first detail that comes to mind is the Iris scanning feature for the face recognition which samsung has been created to recognize. This new approach towards biometric security surely decreases the likelyhood of the device being unlocked, but it also means that this smartphone can be unlocked in a tripple combination, using a PIN, fingerprint, pattern and Iiris. So the device is really advanced when it comes to the choices it presents you with when it comes to security. And the company quickly patches any security flaw which may occur, especially when it comes down to the iris scanner which was tricked by hackers to unlock the device via contact lenses and a photo. Samsung have quickly come up with new update which improves the iris-scanning feature of the device significantly and makes it harder to unlock it by using a unique pattern of the Iris which acts kind of like a unique key only for your phone.
Furthermore, since payment is often done using Samsung Pay, the company has made it so that the device features military-grade encryption plus has many features that secure the files and data of the device. One of those is the ability to lock separate features of the Samsung device, such as accessing web pages, signing in to use specific web pages, etc. In addition to this, private files and applications can also be stored separately in the Secure Folder feature, in order to grant access only to you.
Privacy
In addition to security, Samsung have also though about privacy, implementing their Samsung Knox, which offers chip-level security that reinfoces multiple different layers of protection which works on hardware as well as software level. This ensures privacy, by using virtualization zones, known as TrustZones, so you can choose the appropriate environment, based on the work which you are doing.

Ofcourse, being in the smartphone market, you have to know that the competition is insanly large and there are the ones who are always striving to shed light on a specifically targeted group of customers – the ones with bank accounts, large enough to spend thousands on a highly secure smartphone. Such smartphone is the Sirin Solarin phone which costs over $16,000 dollars and if you are not prepared to pay this price, you should skip it reading this part.
Security
The security featues of the Sirin Solarin have been focused on providing active protection to the user’s mobile device. So, in contrast to other phones with protection features this device is actively protected against different attacks on it’s host or via physicall address and even on the network it is connected to. Such active protection is known as Zimperium and if you have a Solarin smartphone, it will provide the following features:
- Detecting threats and immediate handling of them by security administrators.
- Detecting unknown threats by using highly complex threat analysis.
In addition to this, the service also includes contract with the anonymous e-mail provider Protonmail, which ensures that you have an encrypted e-mail address with two factor authentication and dual password login. This means that you enter one password to login to the e-mail account and another one to decrypt your e-mail box.
Another impressive feature which this phone has is a technology known as Security Shield which is provided by the company KoolSpan. This tech makes it possible for you to conduct a VoIP (Voice over IP) phone calls and send messages which are encoded on the go with an AES-256 encryption and FIPS 140-2 encryption. So basically these ciphers are so strong that they are used by the government to lock top secret files and you have this level of security when you send a simple text. The mode can also be activated and deactivated, using a simple switch, that is located in the back of the device – simple, yet very secure.
Whether you decide to trust this phone or not, when it comes to standard flagship Android devices, it is a very good idea to mention Google Pixel. The phone has the main attention of the company as they are constantly updating it’s latest Android version and the device is likely to remain supported fo a lot of years. However, being a flagship device also means that they are likely to be targeted more by hackers and this is why extra precaution is required when you use those types of devices.
Security
Google has come up with many new security features of their Pixel phone, especially when it comes to it’s latest Android. The company has implemented FBE – file-based encryption for starters which does not reveal what type of encryption is used, but it is likely that one of the strongest out there, the RSA cipher has been used which generates a unique decryption key for each object. This strategy works with the each files that are used by the Google Pixel phones. The files encoded with different keys for unlocking each of them make it impossible for crooks to read them even if they somehow manage to break the security and infect the phone. The company has also combined security with easiness, meaning that they have inserteded various feautres of the phone that can be accessed very fast, despite the strong encryption, like the alarms, phone calls and others.
In addition to this, other security features of this version of Android are always available and those include the direct boot feature of the phone and increased encryption. Furthermore, are relatively new feature for the Android OS is the verified boot security option which stops any corrupted phones from booting in the first place. This makes it difficult to root the devices though.
In addition to those, the support of the Pixel phone has also been made to be very responsive, because the company constantly keeps improving their bug fixing technologies. Take a simple example – you use your Pixel phone and a big occurs. Instead of you having to contact the support team yourself to receive the bug data, the device automatically sends your bug information to the support and the process is handled discretely and automatically, resulting in a privacy oriented update service which extracts the bug information actively and the bugs are fixed without hackers even knowing they existed in the first place.
Privacy
When it comes to privacy, you can rest assured that Google has taken care when it comes to this device. Google gives you complete oversight of each app that you install on your phone and restricts the apps from making any type of modifications on your device, even if the apps have some sort of critical permissions that they require from you. Furthermore, the company has also focused on minimizing the ammount of data which is given away by the device when using different apps, only restricting this to the crucical data required. We feel convinced that these features are very useful, especially when it comes down to malicious apps that use permissions to obtain different information from your device.
Furthermore, if you want to know that you are hidden for sure when browsing the world wide web, the new operating system also has a built-in VPN service which is appropriate for business users who are often targeted by hackers. This is a very good move against the main competitiors, targeting business users as well – BlackBerry. Nice move, Google!

When we address the elephant in the room, Apple, we have to note that the company has been a subject to a lot of pressure when ti comes to it’s security and privacy of the devices and it has also gotten in court with the FBI due to that reason. But when it comes to the latest iOS, news have broken that it may be weaker than it’s predecessors.
And not only this, but a lot of private contractors and independent security experts have also put in a great deal of effort to see if Apple’s devices can be actually hacked.
But the company does not sit around and wait while this happens. They react very fast to everything which is thrown at them and quickly add new security features as well as fix old ones in a very fast rate.
Security
When it comes to the fingerprint scanner feature of the iPhone, there are numerous biometric extras added. One of those is to add the ability to recognize you via retina scan and via Face ID as well, although there was some controversy about that. But Apple is not the type company that will wait for things to happen. They have paid and offered jobs to many hackers and crackers to additionally boost security.
In addition to those, the security features of the device that are used so far are very well refined and you can choose among them plus different encryption tools that provide full encryption for various aspects of the device as well as messaging service done via iMessages.
The Modified K iPhone
If you are in doubt for choosing the iPhone 8 as your secure device, you can go for a specifically designed version of the the iPhone for system secururity, created by company, known in the trade as KryptAll. The company has reportedly modified the iPhone and changed it’s firmware by adding their personal VoIP applictions. This makes it possible for the device to conduct encrypted phone calles to absolutely anyone. The downside of this is that for absolutely maximum privacy, all of the KryptAll devices have to participate in communtion. The privacy is guaranteed and even the law and KryptAll themselves cannot tune in to your conversations, so it’s all guaranteed. However, it comes at a pretty significant price – approximately $4,500 US dollars for a K iPhone.

This unique device has still remained to be one of the best smartphones that can deliver security like nothing we have ever seen from it’s competition in this segment.
Privacy and Security
Turing phone initially begun with a modified version of Android, however the company did not believe the device was secure according to their judgement. So later, they have introduced a new software for the Turing phone, called Sailfish OS, which comes from a Finland-based company, named Jolla. The device uses a Micro-SIM card and the card can be connected via GPS, Bluetooth, Wi-Fi, 3G and 4G in a secure manner. The phone also has sensors that are available in most smarthones out there. The mission of Turing Robotic Industries, the company behind this device is to make a device that is focused primarily in protecting the data stored in it from any cyber-threats that it may encounter. This is where Sailfish OS comes to which they have switched later on. The OS is Unix-based and it uses the kernel of Linux, but it is also combined with a Mer core stack. The “patient 0” smartphone which has first received the new Sailfish OS was the Jolla smartphone which was manufactured by the company, who created the OS themselves.
When we discuess the software which is included in the Sailfish OS, the first important detail to outline is that the OS is Linux-based, meaning that it is created to be more secure than convenient by design. However, the company has introduced multiple advantages of the device, like the Mer standard which is compbined with the Linux source code. This allows for the OS to be ported on multiple different third-party devices, unlike some operating systems that are designed only to work on specific devices and cannot be ran on others. This makes the phone universal as well and it also means that it is very suitable to use such porting-enabled devices in organizations. The porting function is achieved primarily via a virtual drive, such as VirtualBox one, with the help of which the Sailfish OS SKD can be implemented. But since the OS can be installed on various third-party devices, this also means that many consumers are likely to focus on Jolla, instead of having to buy a Turing phone, especially since Sailfish OS is also designed to be easy to get used to and learn:
 Image Source: trustedreviews.com
Image Source: trustedreviews.com
Another significant plus of Sailfish OS is that it is also open-source and available for everyone. In addition to this, the operating system also relies on gestures instead of buttons, which is a new and unique approach to smartphone usage. In addition to this the UI of the Turing Phone is closed source, in contrast to the OS being open source, which makes the phone even more secure. In addition to this, the OS is created in a way that it can distribute and work with apps, while in the same time remain secure and rpivate.
The company has a clear strategy as well – they aim at long-term customers, and a clear indicator for that is that back in 2016, they compensated anyone who has pre-ordered one of their phones with a final device in addition to the unfinished one, which they initially sent at the time of pre-order to be used while the actual one is ready. So anyone has gotten an extra device to the initial one they have originally paid for, which is very well-thought.
In addition to this, the phone is different than the compatition, primarily because of it’s stunning looks and sharp details. Secure smartphones generally look ordinary, but not this one. The deivce has actually been created from materials that are significantly more rugged than your average aluminum smartphone device. B ut the Turing Phone is not just beauftiful – the device also offers a unique type of connector which is somehow similar to Apple’s lightning port, and just like Apple, all of it’s connections go through it’s port, including the headphones.
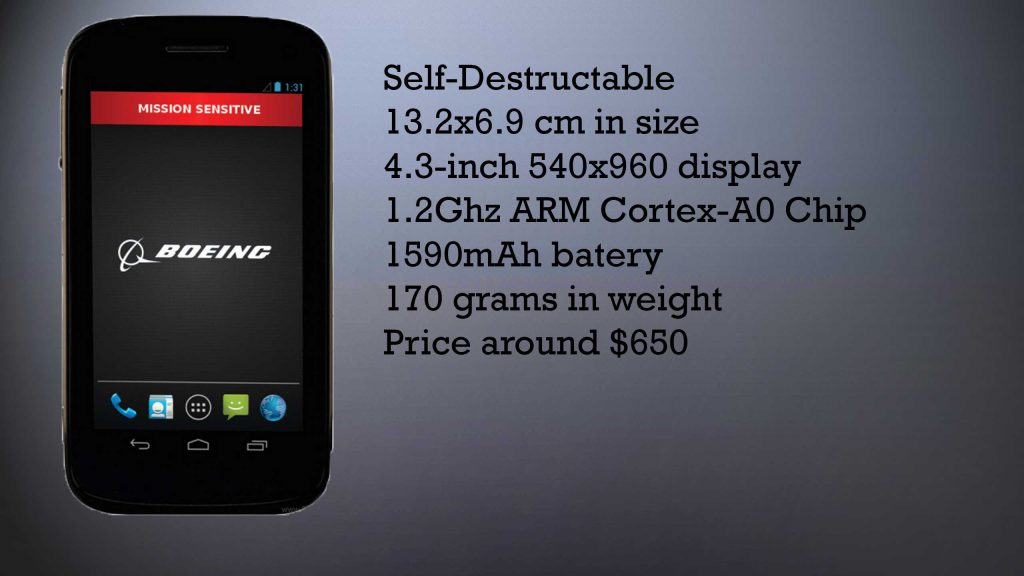
If we discuss smartphoen security, Boeing has always been a big player in this market ever since it’s first devices came out. The airplane manufacturer has gone mental when it comes to the level of secrecy when they are developing these devices. The phone even has some spy-like features, like a self-destructing function if someone tries to tamper with your phone – something that is definitely for advanced users.
Privacy and Security
When we discuss security, Boeing have chosen to use an older, but heavily remodified version of Android. And by heavily we mean that the company has restructured the code entirely why taking only the source code of the OS and reibuilding it. And they do not share much about it either. The company does not even share information on where are the bolts and screws that keep the phone together. In addition to this, if you are trying to hack it, the phone will automatically terminate itself, deleting everything in it, kind of like a tripwire trap. Thus, this makes the Boeing the hardest phone to hack of them all.
Furthermore, Boeing have also created those devices primarily for the US and they are relatively small in size too, not larger than any iPhone 4 or 5 you would see. The Boeing Black also has a PDMI port which can be used for USB, HDMI and other types of connections with displays, which is a lot of punch for it’s humble appearance.
In addition to this, the Boeing Black is also created to work with multiple modules that can be added to it via it’s ports. These can ensure it to serve a different purpose, while maintaining the look of a cheap smartphone that would not bat anyone’s eye. The device can be modified to work with the following modules that can be physicall connected to it:
- Custom radio channels.
- GPS tech.
- A more powerful battery bank.
- Satellite radios.
- Solar-powered attachments.
- Biometric scanner key.
So, if we judge by what Boeing have created, it all becomes clear – the company targets customers that have a lot to hide. This customer base is wide and there are a lot of people who would use this device, like governmer officials as part of their EDC kits (Every Day Carry) or business people who have chosen it to protect private conversations, concerning their security or the security of their enterprise. If we had to sum up the Boeing Black in few simple word, it would definitely be the “Kalashnikov” of the smartphone market. The phone is rugged, simple and swift and can work with a variety of attachments to ehnacne it’s capabilities, while remaining humble looking – one of the best secure smartphones out there if you want to stay hush hush.
This phone is not just any phone from a startup company – the company LG stands behind it’s production. It runs a specifically modified Android which is 6.0 version, known as UnaOS. The phone delivers advanced security features, but it also offers accessibility by providing dual-sim connectivity as well as advanced network connections, making it suitable for tech-savvy users who favor security.
Security and Privacy
When it comes to the network of this phone, the UnaPhone Zenith supports a variety of connection speeds and connections of up to 150 Mbps. The device is also secure when it comes to it’s hardware functions, meaning that it has functions like biometrik security and a Black Screen Wake Up function plus AppLock that are tied up to your fingertip. Futhermore, the OS also has key features, embedded in it, such as restricting any daata leaks plus mining. These ammount to better privacy and stop attacks plus any hacking attempts, which results in much higher security in overall.
The downside of the strict security of the UnaOS is that there are no Google applications support, which is completely understandable, considering the risks some shady Google apps bring on an Android device. In addition to this, UnaOS™ has also had the libs of traditional Android devices removed from it, because they have come to a conclusion that they are used as an area of vulnerability exploits of up to 90% of the Android attacks conducted nowdays. Furhtermore, if new vulnerabilities, like Fake ID, Certify-gate, installer hijacking, Stagefright and Master Key appear, they are patched quickly by the company and the ones we just mentioned are only the beginning. In addition to them, other less known vulnerabiltites are also patched by them.
In addition to this, other strong security features have also been implemented in terms of privacy as well. The phone can now automatically restrict connection to suspicious IP addresses during web surfing. Futhermorre, IP addresses which are somehow related to the Department of Defense as well as Google addresses, related to information aggregation, are banned by default from the device, which means that automated spying is less likely to occur with this device.
Furthermore, the custom OS of the UnaPhone Zenith also has been configured to prevent privilege escalation conducted by third-party apps as well as malware, if you install them on the device. But you do not even have to worry about third-party apps being installed on your Zenith phone without your consent, because third-party installation of apps has been disabled by default and cannot be re-enabled.

A company, known as Cog Systems D4 has chosen a phone no other than the HTC One A9 inorder to implement their security software and turn the device into a fortress. If you are happy with HTC’s hardware and performance of their flagship devices, then this is the phone to choose.
Privacy and Security
In terms of how private and secure it is, the company has taken a proactive approach. Ths results in some incremental changes to the mobile device as well. For starters, the D4 HTC has changed it’s default encryption with a stronger one which is implemented by D4 and has been thoroughly tested against being bypassed. In addition to this, a strong VPN service is also added to the device, making it impossible for third-parties to detect you activity. Furthermore, the company has also added nested VPNs for maximum efficieny as well as choice. In addition to this, D4 have also create separate protection of the Kernel of the HTC A9 which can catch a hacker on his track to hack your phone. Another important improvement is also a secure boot feature which is added to prevent attacks exploiting boot. Arguably, but not in a long shot, HTC may have made the most secure phone in the world.
But D4 does not stop there. The device also has implemented secure communications that enable it to meet customers demands with higher requirements as well. For usability, the device has still remained easy to use meaning that new features are also added to automatize security. It also has Isolated Key Store implemented and if you make an order you also have the ability to add and remove security features based on your budget and requirements.
As far as the bottom line when it comes to those smartphones, you should know that there are different smartphones out there which provide various security features. but if you are a standard user who does not require a lot of security and just want the latest patches against malware, you can feel free to go ahead with any of the flagship devices from Google or Apple, since they are updated on a most regular basis. However, if your business revolves around security and privacy, you should think about more sophisticated options, like the ones which we have suggested in this article. If you want a cheaper solution, you can definitely go ahead and purchase a Galaxy, iPhone or an HTC and have them modified by the security companies which we have suggested in this article- they all provide top-notch level of security and privacy. And of course if money is not an issue for you, you should focus on the more expensive choices in this list, since they are guaranteed to secure you and have an excellent system that has been built to last.
Legal Disclaimer: Be advised that the opinions expressed on this website are solely ours and they are not biased towards any specific software company or any other organization. The opinions are also based on our research, which includes first-hand data as well as second-hand information and it took place approximately 30 days before this article was published.
Ventsislav Krastev
Ventsislav is a cybersecurity expert at SensorsTechForum since 2015. He has been researching, covering, helping victims with the latest malware infections plus testing and reviewing software and the newest tech developments. Having graduated Marketing as well, Ventsislav also has passion for learning new shifts and innovations in cybersecurity that become game changers. After studying Value Chain Management, Network Administration and Computer Administration of System Applications, he found his true calling within the cybersecrurity industry and is a strong believer in the education of every user towards online safety and security.
- Which Are The Best Budget Smartphones In 2019 PRICE TOTAL SCORE OS CPU RAM BATTERY FINGERPRINT 1 Oukitel...
- Which Are The Best Gaming Smartphones in 2018 PRICE PRICE/VALUE RATING OS LED HDR CPU RAM & STORAGE...
- Facebook Virus – How to Remove It (for PCs and Smartphones) This article will help you remove all types of Facebook...
- The Most Secure Web Hosting in 2018 (Speed, Security, Support, Uptime) *Following recent data breach of the company DomainFactory, which is...
- The Best Smartphone for Oct 2014 The review for the best smartphone for October 2014 will...
- Most Secure VPN for Turkey RATING ENCRYPTION DNS Leak Protection LOGGING SERVERS 1 Hotspot ShieldSee...
- The Most Secure Smartwatches List This is a comprehensive Top 10 list that summarizes the...
- Remove Android Flashlight Malware This article will help you to remove Android Flashlight malware...






Is Blackphone still in business?
Amazon – sells them – a customer comment claims it is no longer in business. Can’t verify it on Google.
The company is called Silent Circle. You can find their site here, Tom Slick:
silentcircle.com
Did the UnaOs phone ever actually become available?
Hello Aj.
More information about the Unaphone Zenith and UnaOS can be found in:
unaos.com
As far as I know, i cannot find it anywhere for sale.
Thanks! Yeah, I had found the site… but no ways to purchase.
Yeah, I checked up on that thoroughly and it seems that the UnaOS phone is still a crowdfunding project. You can back it here:
indiegogo.com/projects/unaphone-zenith-secure-and-private-smartphone-security#
Hvor er Sailfish henne af i testen? Et styresystem bygget på Debian Linux…
Har selv kørt Sailfish siden den allerførste Jolla, der ramte markedet i 2013.
Jeg vil til hver en tid påstå at den er mere sikker endnu nogen af de telefoner på den liste, samtidigt skruer de snart endnu mere op for sikkerheden med den nye Sailfish OS 3
Boy! This certainly does not answer my question for a list of icons on cell ph..