|
1
|
2
|
3
|
||||||||

Blackphone 2
See Review |

BlackBerry DTEK60
See Review |

CopperheadOS Nexus
See Review |

Sirin Solarin
See Review |
Google Pixel
See Review |

K iPhone 7
See Review |

Turing Phone
See Review |

Boeing Black
See Review |

UnaPhone Zenith
See Review |

D4 HTC A9
See Review |
|
|
Lowest Plan (Web)
$735
|
Lowest Plan (Web)
$399
|
Lowest Plan (Web)
Free
|
||||||||
|
Total Score
    
|
Total Score
    
|
Total Score
    
|
||||||||
|
OS
|
OS Support
|
OS Support
|
||||||||
|
VPN
 |
VPN
 |
VPN
 |
||||||||
|
Uptime
AES-128
|
Uptime
AES-256
|
Uptime
AES-256
|
||||||||
|
Tracking Block
 |
Tracking Block
 |
Tracking Block
 |
||||||||
|
VPS
 |
VPS
 |
VPS
 |
|
Looking for newer devices? Check out our new review on Which Are the Most Secure Smartphones in 2018:
Smartphones have become an extension of our hand, a significant part of our daily life. And when it comes to privacy and security, it is always a tricky subject to discuss, especially because of the “revolution” that happened a while back, concerning Wikileaks and ex-NSA employee Edward Snowden. And when you insert Rule 41, a set of laws passed by congress for mass surveillance, smartphone security becomes a very volatile subject to mess with too. So when the security features of smartphones are being discussed, several key areas need to be clear:
- Are you going to use a SIM card?
- Are you going to user accounts and other services that collect information?
- How is your smartphone usage going to be like – privacy focused or disregard for privacy?
- Do you support bio metric security or you are against it?
Unfortunately, we are living in such times that even secure behavior does not necessarily mean smartphone security. It really comes down to what type of security you are interested in. If it is from thieves and cyber-criminals then this article might be able to help you out. However, if you are expecting a completely secure device against all governments and in complete isolation of your data, you should focus more on cryptography or… using a typewriter.
What Threats Exist Out There?
Basically, in the 21st century, every aspect of our data is saved online, for the most part – personal information, financial information and other important stuff, including paying with your smartphone. This has brought a whole new type of cyber-threats in relation to this. The threats nowadays are ranging from financial-stealing malware to viruses that even enable your microphone. Furthermore, ransomware threats have also begun to be seen on Android devices and are likely to be seen on IOS and other widely used devices too. Not to mention multiple other threats, like phishing and scammers that can cost you, if you are careless.
Which Smartphones Are The Most Secure and Private?
There are many smartphones that are secure in a different way. Some have more privacy-oriented features and others are more focused on encryption and secure boot. There are also devices that have different prices and these prices do not necessarily mean more security. In the end, it comes down to the user of the phone. So, let’s begin with our list.
|
Probably what is the most notorious business phone with multiple layers of security and multiple OS’s running on it has recently won awards for it’s security oriented behavior.
Privacy
Regarding privacy, this clever device has a very specific OS which is basically it’s core competence in the sector. The operating system is called Silent OS (or PrivatOS) and is created from the ground to be private. A feature on the phone is embedded and this feature actively encrypts every single text message and app communication. This privacy feature even extends to making calls as well, allowing the information during the phone call to be encrypted, hence preventing prying ears from listening.
In addition to this, for further privacy control, the OS allows to manage each app and decide what type of information this app will extract from you.
Security
For increased overall cyber-security, the operating system of this device uses application pre-loading, meaning that it has the ability to run applications in a controlled environment, giving the ability to be in charge of what you share as information.
Another very interesting aspect of the Silent OS is that it has a feature, called Spaces. This feature includes virtual environments that you can create separate one from another. For example, if you wish to store your personal data on one Android (like a separate phone), you can add a space and call it “Personal”. In this space, you can add your personal information, like photos, documents and this information will stay in this space only. If another space of your phone is compromised or someone has physical access, he or she will not be able to see the personal data in the “Personal” space. This very unique feature of the Blackphone enables a unique method to customize your environment in a secure way and keep the apps and files secure. You can also use Spaces to visit suspicious websites that you do not trust, without compromising the data in your personal space.
The company also outlines the device as having very responsive support. They promise up to 72 hours of deadline for patching a detected vulnerability that is critical to device security.
|
Recently, BlackBerry has come out with two phones specifically focused on security. They also run Android OS, but with multiple security features and are focused primarily on the business users who value privacy and security.
The Security
Similarly, to all the companies in this list, BlackBerry also outlines their phone as being a top-notch security one. However, this is very relative, especially in the cyber-security field. One of the benefits of this phone in terms of security is that the device itself is supported very well and updates are immediately being issued regarding bug fixes and vulnerability patches.
Besides the hardening of the Kernel of the phone, the device is also focused on preventing any modifications to its firmware. Despite it runs Android 6 in it, the boot is secured more than just the regular encryption sequence it goes through.
The primary purpose for which this phone is created is overview and modification. Just like the older model (DTEK50), it features a DTEK software which provides insight on the state of security of the device and information and tools to take necessary action if a security issue has been detected.
In short, for the price of this device, its performance and security features that come out of the box with it, it is a very decent choice indeed.
|
When we talk about smartphone cyber-security, there is definitely a discussion of the Operating System above all. In connection with this, we have included a very interesting solution, despite being a bit of tech savvy – an operating system focused completely on security and available for all the Nexus devices. This very cheap solution can be implemented if you have the technical skills and patience to do it. The files of the OS are even available for download for different specific factory releases of the devices.
Security
For security, the creators of the operating system have also used several interesting security features that do not step back by anything to even more expensive solutions. One of them is the AES-256-XTS encryption algorithm that is military-grade and is used to encrypt all data in the file-system of the phone. In addition to this, for the metadata the cipher block chaining version (CBC mode) of the AES-256-XTS is being used.
To additionally improve security, the OS features a verified boot of its firmware modules and the partitions of the operating systems.
Furthermore, a service, called Zygote for Android is also used to start different processes. The difference with this usage is that not only the fork commands are used like it is typically for Android, but also the exec commands as well. In short, this is a type of service that is solely made to launch apps and this OS has additionally enhanced its usage thus improving app launch security.
But the operating system by far does not stop there. It includes other necessary features, like sandboxing of applications and services that are running in the background. This sandboxing feature is supported by the SELinux engine and has multiple improvements In it too.
There is also a very particular feature related to the allocation of the system. The CopperheadOS is using a port from what is still believed to be the most secure OS in the world – OpenBSD.
The operating system also has active support that patches zero-day exploits and other vulnerabilities if discovered. These patches make it difficult to manipulate it and get administrative access to the device, even if it’s targeted.
Basically, as a bottom line, this operating system can be installed if you look at beginner guides online. Other than that the installation is no difficult than reinstalling any other custom Android on a rooted Nexus device. Very tech-savvy and cheap security solution which is as powerful as they come.
|
The smartphone market is a very competitive one and people are always looking to “shine” differently and succeed this way. Sirin Labs is one of those organizations that offer highly secure smartphones, but for a price that is not the cheapest, to say the least.
Security
Regarding the security features of the phone, Sirin Labs have focused on providing active protection of the mobile device. This means that the device is not just any other phone with protection features. It is continuously protected against different attacks on it’s networks, it’s host or attacks via physical access. The active protection is real-time and is offered by a company known as Zimperium. It’s service includes:
- The detection of threats and their handling by experienced security administrators.
- Detection of previously unknown threats by including sophisticated behavior analysis.
Another active security feature coming from collaboration with the notorious Protonmail ensures that the user has an encrypted e-mail address featuring 2 password encryption – one to log in to the account, the other to decrypt the mailbox itself.
Also an amazing security feature of this phone is a technology called Security Shield provided by a company called KoolSpan. This technology makes it possible for encrypted voice over IP (VoIP) phone calls and sending messages that are encrypted with AES-256 as well as FIPS 140-2 encryptions. These ciphers are often used by the government to lock top secret files that are eyes only. This mode is activated by a simple switch on the back of the phone. Military-grade secure and very elegant indeed.
|
Believe it or not, when it comes to Android devices, it is not a bad idea to mention the most commercialized flagship devices, primarily because they have the incentive to be secure. This is due to the fact that being widely known and famous, the devices are a target for all types of hackers to crack. This is why extra precaution and care must be taken when managing those devices. And Google Pixel’s iPhone’s 7’s competition is no exclusion from this.
Security
The company has come up with multiple security features of the Pixel, primarily related to the latest Android OS – the Nougat 7.1. Google has implemented what many refer to as an FBE – file-based encryption. It is not known what type of algorithm is used, but the working of this encryption is very similar to the RSA cipher which generates a unique key. The same way this works is with the files used by the Google Pixel device. These files are encoded with a different key for unlocking, corresponding to the specific file. The company has also combined security with convenience, meaning that they have inserted different features of the phone that are often used, like alarms, phone calls, and other that can be accessed much faster, despite encryption.
Other security features of the Nougat version of Android include the direct boot feature of the phone and as mentioned, the much stronger encryption. A relatively new thing for the Android OS is the verified boot security extra that can stop any corrupted devices from booting at all. This may make it a bit more difficult to root through.
Also, the support of the Pixel has been made to be quite responsive, primarily because the company has implemented new technology regarding bug fixing. Imagine you are using your Google Pixel phone and a bug happens. Now, you do not have to send the bug information, but the Google support team receive the bug data and the bug data only, as soon as you get an internet connection on the device. Instead of having to send manually bug info, or being requested to send info, now the process is handled automatically and discretely. And the whole process is privacy-oriented, meaning that only the bug information is extracted and nothing else from your phone.
Privacy
Regarding privacy, Google has taken good care of this device. It gives complete oversight on any type of permissions that are requested by different apps. The apps are also restricted to make any form of modifications on the device, even if they have some sort of permissions. In addition to this, the company has focused on reducing the amount of data which the device gives away when used by different apps. We believe that this feature is very useful, because there were many reports of malicious apps that were even using malware to obtain permissions and hence different tracking information.
Furthermore, regarding hiding you, the new operating system also features a built-in VPN service which is very suitable for business users, a segment targeted by the previously mentioned BlackBerry device. Good thinking, Google!
|
If it isn’t the elephant in the room – Apple. The company has been a subject to a massive pressure regarding the security and privacy of their devices and it has even come to involving themselves in court with FBI. But what about the latest iOS and the news of it’s security being weaker than the previous versions.
Not only this, but many private security firms as well as independent experts have also invested a great deal of effort to see if Apple’s devices can be actually hacked or not.
But Apple has not just stood by while this was happening. The company immediately and swiftly reacts to everything that was thrown at them, resulting in a phone with security features that are pretty astounding.
Security
Besides the usual features and fingerprint scanning feature of the iPhone, there are multiple other biometric extras added as well. One of them is the ability to perform a retina scan to unlock your device. In addition to this, Apple has also offered a job to the primary iPhone hackers and crackers, like Luca Todesco, Nicholas Allegra, and Patrick Ward, Betanews report. This is done with the purpose to increase the security of their products and boost their bug bounty program.
Besides having the regular security features which are very well refined, the phone also includes different encryption tools which are also full encryption for the different files on the device as well as encrypted messaging service, done via the iMessages application.
The Modified Version for Even More Security – K iPhone
In case you are still in doubt about iPhone security, a company known as KryptAll has reportedly modified the iPhone, changing it’s firmware and adding their personal voice over IP application. This allows to make encrypted phone calls to anyone and conduct anonymous calls. The downside of this is that for maximum security a KryptAll device should only communicate with another KryptAll device in order to be private. But the privacy is certified and even the law and the company themselves cannot listen in on your calls. And it has to be, the devices cost approximately $4,500 dollars for the K iPhone 7.
So, if you want more than the advanced security of the iPhone 7 and want to be supreme in those terms, the K iPhone is for you, if you have the extra buck, that is.
|
The uniqueness of this phone is its key strength which differs from the competition. The Turing phone was the first secure smartphone created by the Turing Robotic Industries.
Privacy and Security
The bold device initially started out with a custom modified version of Android OS, but it turned out that they did not believe it was secure enough, so later on a switch was made for the software of this device. The new operating system is called Sailfush OS and it comes from the Finland-based company Jolla. The phone uses a Micro-SIM card and it can connect via GPS, Bluetooth, Wi-Fi, 3G, and 4G. It also has the standard sensors, such as compass, accelerometer, ambient light sensor as well as gyroscope. The mission of the company for the phone, regarding security, is primarily oriented in creating it so that it protects the data from cyber-threats, new or old. The operating system Sailfish OS to which they switched is a Linux-based OS and it uses the kernel of Linux in combination with a Mer core stack. The first smartphone which has received the OS was the Jolla smartphone which is manufactured by the company who also made the OS.
When we take into consideration the software part of the OS, the first thing that springs to mind is the Linux architecture of the Sailfish OS, which is deemed as a generally safe environment. There are multiple advantages of this device’s Mer standard which it has in combination with the Linux kernel. The primary of those is that the OS can be ported (installed) on a variety of devices that are third-party ones. This is contrary to some OS’s, such as Ubuntu mobile which is designed only to work on specific hardware and can be installed only on certain smartphones. It is achieved primarily via a virtual environment (VirtualBox) with which Sailfish OS SKD is implemented. However, since the OS can be installed on a number of third-party devices, this may drive consumers to focus on the OS, rather than the phone using it.
 Image Source: trustedreviews.com
Image Source: trustedreviews.com
Another advantage of this operating system is that it is a free one, and relies on gestures instead of buttons, which is rather unique, interesting, and new. And while it is free and open-source, it’s the user interface (UI) is a closed source, further increasing security. Furthermore, the OS is designed in a way that user of various phones can distribute apps, and there are also multiple app stores that can be used at the same time, which is convenient because you get to use your favorite applications and have security simultaneously.
The company however is aimed at long-term users as we saw back in 2016 when they gave everyone who has pre-ordered a Turing phone, a free unfinished device, and when the final device came out, they did not have to return the unfinished one. So they have gotten more than they paid for, which is amazing.
When it comes to the phone itself, we understand what makes it so different than the competition. The looks of the phone are surely stunning and full of sharp details. But the phone does not look only, it is actually made from an indestructible material, called liquidmorphium, which is stronger than steel and aluminum and is likely to be the next new trend in terms of smartphone production. For maximum security, the phone also has a changed port, similar to the Apple devices’ lightning port. It does not have a headphone jack or anything else that is standard and all goes through this unique port.
|
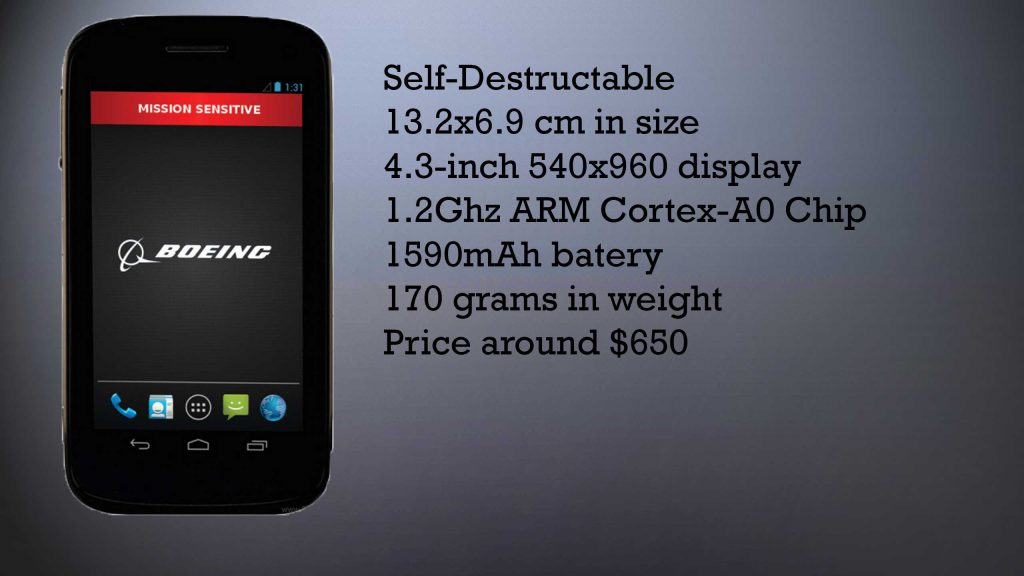
When it comes to smartphone security, the aircraft manufacturer has taken it to a savage and mental level, creating this incognito looking machine of secrecy. The smartphone has insane features, among which are the self-destructing function if someone tries to tamper with your phone – not for beginners indeed.
Privacy and Security
For the security, of the phone, Boeing has chosen to use Android. This is particularly interesting because the mobile OS is not difficult to hack. So this is why the company has only taken the source code of the OS and rebuilt it from scratch. And the company does not share much info about the security software in it. They are even hush-hush on the screws used to hold the phone together. Another frustration for hackers, if they are optimists is that the phone basically terminates itself if someone tries to access it, besides you.
The phone is produced primarily in the US and its size is a bit larger than the iPhone 5 (13.2×6.9 centimeters). The phone also has dual-SIM usage and it is sealed upon manufacturing with tamper-proof casings. The phone also has a PDMI port which can be used for USB, HDMI, Display, and other connections all via this port, which is not very commonly met.
What is interesting is that the Boeing Black is configured to work with numerous add-on modules on it’s back side which can ensure it to serve it’s purpose and be effective in some particular situations. Some of the devices that can be attached to the Boeing Black are:
- Biometric scanners.
- Custom radio channels that are secured.
- GPS receivers.
- Satellite radios.
- More powerful battery.
- Solar-powered attachments.
It is very clear what customer base are Boeing looking for and these are people with secrets. When we start at government officials who absolutely need such devices in their EDC (Every Day Carry) kits, to businessmen and other privacy-sensitive individuals. Basically, if we have to sum this phone up in a few words, it would be “the M4 carbine with Picatinny rail” of the smartphone market. The phone has few technical specifications which reveal that it is not top-of-the-notch in terms of technical specifications. But, the purpose of it is not this one, right?
|
This “clean, elegant and awesome” phone as the company behind it describes it runs on a specially modified Android 6.0 version, called UnaOS™. It promises advanced security features, it also offers dual sim and advanced network connectivity, perfect for system or network administrators who want to stay interconnected and secure at the same time.
Security and Privacy
Regarding the network of the phone, the UnaPhone Zenith supports connectivity of up to 150 MBPS. In terms of hardware security, the device has a fingerprint with a Black Screen Wake up function and AppLock using the very same fingerprint. When we talk about the privacy and security of the OS itself, there are several key features to address. The UnaOS is a heavily modified operating system which restricts any data leaks and mining to ensure better privacy and stops attacks and hacking, ensuring higher security.
The downside of this is that there are no Google apps which is understandable, because of the privacy and spyware concerns of some shady Google Applications. In fact, the company has also removed the framework and libs of Google on the device, because they have established that almost 90% of the Android devices in use today are vulnerable to such attacks. Other vulnerabilities which exist with android devices such as Fake ID, Certify-gate, hijacking of installers, Stagefright, and Master Key are also patched. But the company does not stop there and it has also patched and continuing to patch less known vulnerabilities that come out.
Another strong security feature of this is that the company has made sure to enhance privacy by restricting connection to suspicious IP addresses during web surfing. All IP addresses that are somehow related to US DoD and DoJ as well as Google connections related to information tracking are banned from the phone, meaning the government is significantly less likely to spy on you with this device.
Another security feature of the OS is that it has a custom configuration that prevents rooting and escalating privileges by third-party apps and malware. But you cannot install third-party applications anyway, so you won’t need to even worry about that. So, an interesting strategy for the security-oriented user – removal of features at the expense of privacy.
|

A company going by the name of Cog Systems D4 has chosen the platform of the HTC One A9 to implement their security kit and make the device into a mobile fortress. If you have used HTC and are happy with it’s design and hardware, then this is definitely a secure choice for you.
Privacy and Security
The company has taken modular approach to incrementally change the mobile device. At first, D4 has of course changed the default encryption of the A9 with a significantly stronger one that has been tested for bypassing and so far it cannot be bypassed. Another impenetrable feature which they have used is add a stronger VPN service, making it unable for prying eyes to detect you. Along with the VPN service, the company has added nested VPNs for maximum efficiency and choice. In addition to this, in terms of security, the company has created a separate protection of the device’s Kernel which should be able to catch a hacker unprepared. And another improvement which is made is in the booting area, adding a secure boot.
In addition to this, D4 has also added secure communications channels to meet customers with high requirements. For usability, the device has still retained it’s easiness of usage, meaning that the new features are easy to operate with and as automatic as possible. Throw in the Isolated Key Store they have implemented and you get an awesome HTC device which can even help government employees do their job.
Honorable Mentions
Katim by DarkMatter

The security company DarkMatter aims to ensure cyber-security in several layers with their latest smartphone Katim. The phone itself has ability to work with an app-store with it’s own secured applications as well as support encryption and self-deleting images after some time.
According to the company DarkMatter, it has become more than evident that the cyber-threats are rapidly expanding and a secure phone developed by cybersec experts which can secure your mobile communications from any prying eyes is of high importance. In addition to this we have the IoT devices which are entering even more in our world and their interconnection with mobile device is also to be considered. But at what cost?
Smartphones are used more for online usage these days than actual phone calls they were made to perform several years ago. The phone is yet to be revealed in it’s full price and features, but at the moment it remains a honorable mention in our review, because it is yet to be released by the end of 2017, packed full of new security features which will be very interesting to see. Some of them, like the self-destructing messages and the self-destruction of the phone upon tampering seem pretty attractive for government officials or other individuals who live in secrecy.
The New iPhone X (November 2017)
And while the encryption and other security measures of the latest IOS combined with features of the iPhone X are all-new and brave, we cannot help but notice other confusing security elements as well. One of those is the iOS Mail which does not display headers of e-mails when you are receiving them, so you cannot even see who is sending you the e-mail, increasing the chances of you becoming a victim of a spear-phishing e-mail attack. And while the IOS is a very secure mobile operating system by default, this surely is something that Apple should consider.
Another weakness with the latest iPhone is with Safari, Apple’s web browser by default. It has come to light that the Safari team have actually removed some security measures, such as manually viewing what is the certificate of the website that you are trying to access. This security indicators are a must in other web browsers, but we have yet to understand why you cannot check if the website you are visiting is the real one or a fake one that aims to steal your information.
The quality of the iPhone is high and this goes for the cameras of the device as well with their new algorithms that calculate in real time. When we take a look at the front and the back cameras from a security standpoint, however, it is important to know that the metadata of each image taken from the latest iPhone X may include the physical location as to where this photo has been taken, meaning that someone can know where you are located just by taking a look at the metadata of your selfie. Overall and all, security experts would not reccomend this phone if you are a paranoid person.
InfoWatch TaigaPhone
Image Source: Mir24.tv
So far the company has not share much about the phone itself, but at this point we know that TaigaPhone will have:
- 5 inch display with an HD resolution.
- 2GB of RAM and 16 GB of internal storage.
- Rear camera will be 8 MP and from will be 4MP.
- The phone will work with 2 SIM cards.
- The LED indicator lights will become active if you are being recorded or tracked.
- The phone will only cost around $250.
InfoWatch do not reveal much about the TaigaPhone, but we do know so far that the device will run a heavily modified operating system which will be Android based and will have a lot of integrated applications for security, most likely connected with Kaspersky as well. It will be interesting how the phone performs in terms of security in comparison to the other devices on this list, especially with the bold claims that it will be the “most secure” one, according to the company.
Conclusion
As for how the bottom line goes, there are different devices that provide different types and layers of security via different standards and various services and they are all very secure. If you are a user who is not so sensitive on security and privacy and are not tech savvy, you should go with a less sophisticated option, like the iPhone. However, if you want high-end security and you like modification and oversight, we advise going with the Blackphone, which is our choice for the most secure device here. If you want a cheaper solution, you can just use the CopperheadOS, especially if you have a Nexus. It is a much cheaper solution, especially if you know how to install it. And if you don’t, you can easily pay an expert. It will cost you much less than $16000 dollars, for sure. In the end, we cannot say that one device is by far superior than the other, despite that there are very expensive phones in this list. This is primarily because it comes down to you, the user and how you behave and what you demand. Because even the safest device in the world cannot rescue you if you are careless.
Legal Disclaimer: Be advised that the opinions expressed on this website are solely ours and they are not biased towards any specific software company or any other organization. The opinions are also based on our research, which includes first-hand data as well as second-hand information and it took place approximately 30 days before this article was published.
























the list seems to be outdated and some providers left the market, and at least one new came in. last week, i migrated to ano-phone (EU version). it’s good so far.
Hey Juliane,
It is a 2017 list :) Have you checked the 2018 one? sensorstechforum.com/which-are-the-most-secure-smartphones-in-2018
Hi Milena,
Thanks for your reply.
However, looks the same, still missing current devices on the market.