 Banking malware has been evolving and transforming into one of the greatest threats on the malware scene, despite the international, collaborative efforts on behalf of law enforcement and cyber crime experts. A new report released by Dell Secure Works Counter Threat Unit (CTU) perfectly illustrates the growth of banking malware, and particularly banking botnets.
Banking malware has been evolving and transforming into one of the greatest threats on the malware scene, despite the international, collaborative efforts on behalf of law enforcement and cyber crime experts. A new report released by Dell Secure Works Counter Threat Unit (CTU) perfectly illustrates the growth of banking malware, and particularly banking botnets.
The report focuses on 2015 and provides detailed, in-depth analysis on the nearly impeccable banking botnet structure, and the emergence of botnet-as-a-service and mobile botnets.
Botnets-as-a-service and Mobile Botnets Entered the Market
This model (botnet-as-a-service) has gained popularity throughout 2015, with more malware actors renting subsets of their botnets for other malicious operations such as:
- DDoS (distributed denial-of-service) attacks;
- Click fraud;
- Crypto currency mining;
- Targeted attacks.
In addition, mobile botnets have also shown increased usage for a range of malicious activities, including DDoS, click fraud, and impersonation attacks. Nonetheless, according to the research, the demand for the ‘regular’ botnet-as-a-kit service is still bigger, simply because it gives cyber criminals the chance to fully control and monitor the malware’s operation.
Banking Botnets 2015: Old versus New
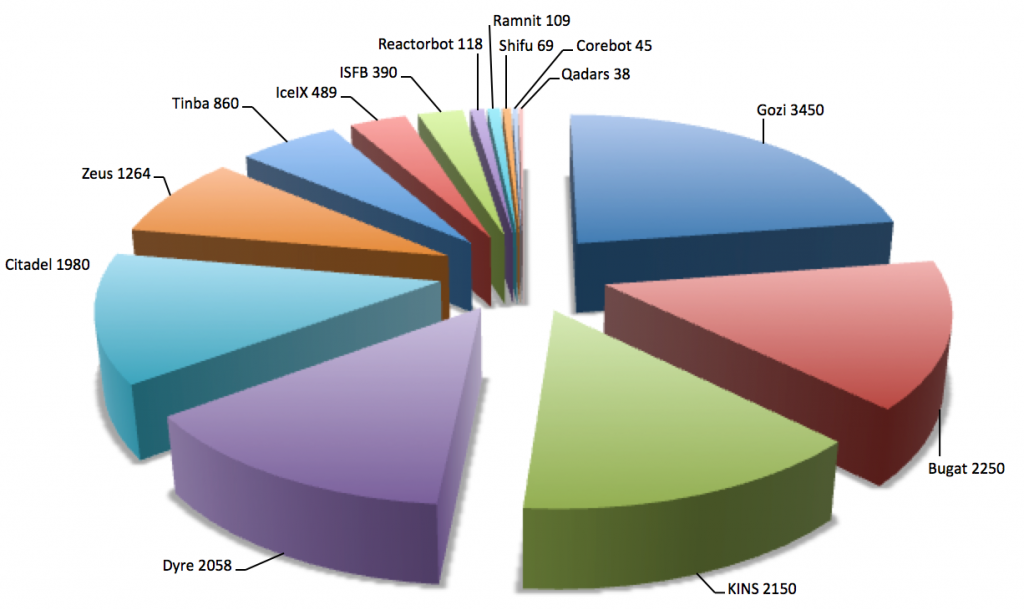
Image Source: https://www.secureworks.com
Researchers have observed that several botnets from 2014 continued to function. However, new additions entered the botnet infrastructure:
- Shifu
- Corebot
- Reactorbot
2015 also saw an increased activity from several other botnets such as Qadars, Tinba, Gozi Neverquest. Overall, banking botnets showed unprecedented activity throughout the past year, with Ramnit and Bugat’s reappearance after they were taken down in 2014.
Fortunately, botnet takedown operations didn’t stop, despite cyber criminals’ resilience. Last year witnessed increased collaboration between law enforcement and security vendors, all struggling to seize botnets’ servers and infrastructures. Only one success, however, was recorded, and it was the success takedown of the infamous Dyre, after Russian authorities raided the offices of a movie distribution company located in Moscow.
Banking Botnets 2015: Features
Banking botnets usually are sophisticated in structure and implement various features. Even though botnets typically aim at obtaining financial information and using compromised systems for financial gain, they target personal information as well. Email credentials are often harvested in botnet-powered operations. Throughout 2015, banking botnets reached a new high point; most of them were observed to integrate backup command and control solutions via backup DGA (domain generation algorithm).
In addition, most botnets now use compromised routers as proxy servers to hide the real command and control servers, take advantage of p2p networks to bypass monitoring, and, not surprisingly, use Tor and I2P to resist disclosure.
Banking Botnets 2015: Targets
Financial institutions and banks continued to be a primary target for banking botnets. However, criminals showed interest in corporate finance and payroll services and stock trading organizations, mainly situated in developed regions with wealthy residents. Researchers observed malware actors targeting countries with weak account protection and difficulties in international transactions. Interestingly, criminals were also interested in countries that required local interference in terms of money laundering. In other words, primary targets for 2015 were banks and various financial institutions in the Asia-Pacific region, the Middle East, and Eastern Europe.
Banking Botnets Delivering Ransomware
2015 saw an interesting turn of events – banking botnets were observed to deliver not only banking Trojans but also ransomware pieces. Dell’s CTU team explains the shift with the expanding need of organized cybercrime groups to find new ways to steal money from their victims. That simple explanation also illustrates the intensity in mobile malware and botnet-as-a-service.
Have a look at Dell CTU’s report.


