DDoS, or a distributed denial-of-service attack, is one of the most common ways to conceal serious intrusions, extort enterprises or sabotage competitors. We’ve seen many DDoS attacks take place in 2015, and reports have already been released emphasizing on the growth in popularity of these attacks.
DDoS, or a distributed denial-of-service attack, is one of the most common ways to conceal serious intrusions, extort enterprises or sabotage competitors. We’ve seen many DDoS attacks take place in 2015, and reports have already been released emphasizing on the growth in popularity of these attacks.
The Highlights in Kaspersky’s Report
Kaspersky’s researchers have made several important conclusions in their findings based on research on the third quarter of 2015:
- DDoS attacks target financial organizations and extort them.
- DDoS attacks have started employing new tactics to increase the number of attacks by manipulating web pages.
- Linux-based botnets prevail in the distribution of DDoS attacks.
According to data compiled by the infamous lab, at least 45% of detected DDoS attacks were launched from Linux machines. One of the more ‘innovative’ such attacks witnessed this year was the one upon the CloudFare company.
Here’s how it went:
A page that belonged to one of its customers was attacked and went through 275,000 HTTP requests/second. The attackers also used malicious JavaScript embedded in advertisements. An iframe with a malicious advert containing the bad JavaScript was run on the browsers of multiple users. The result was their workstations started sendind XHR requests to the victim. According to some experts, these malicious adverts can also display legitimate applications.
The XOR Attack
A Linux-based, DDoS botnet was continuously observed by security specialists. Its victims were primarily Asian websites that belonged to educational institutions and gaming communities. What differentiates this botnet from others is the extensive use of XOR encryption, applied both in the malware and in the communication with the Command & Control server. Not only does the botnet use XOR encryption but it also can self-propagate by brute-forcing passwords to the root account in Linux systems.
DDoS Attacks’ Duration, Location
Kaspersky also reported an attack against one of its clients which lasted about 2 weeks. Moreover, a company situated in Holland was hit 22 times. It’s only logical that DDoS attacks are becoming more and more sophisticated, and the tools to carry them have been made easily available on the black market.
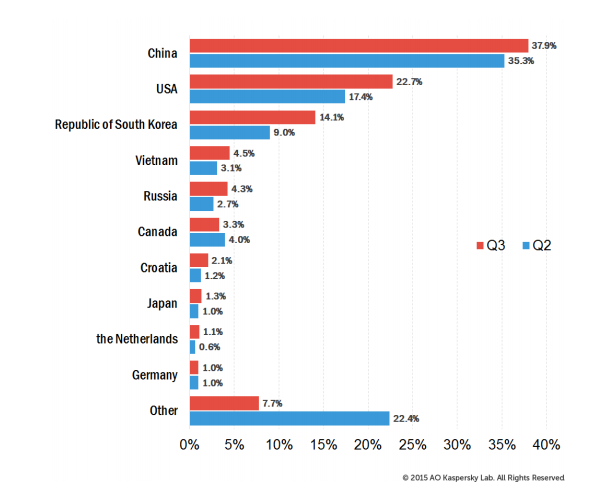
Kaspersky’s data also indicates that the primary victims of such attacks are users living in China, the USA, South Korea, Russia, Vietnam, Croatia, Canada, Japan, Holland, and France. Also, the most common DDoS attack scenarios employed SYN, TCP and HTTP packets.
Even though the number of attacks is uneven throughout the year, one day has shown a notable peak. The highest number of attacks in one single day was 1344, and was recorded on the 24th of September. Curiously, in the third quarter of 2015, Tuesday displayed the highest DDoS activity of all week days.
Have a look at the whole 2015 Kaspersky DDoS report.
More Must-Read 2015 Reports:
Top 3 Ransomware Families, Part I