After the first variant of Cerber ransomware struck, it became clear that this is an extremely effective money making malware on the unsuspecting user’s expense. Unfortunately at this stage there is no relevant decryption method besides the Cerber file decryptor which is being sold by the cyber-crooks behind the malware. Not only this but this particular malware is using two encryption algorithms and it even encrypts the decryption key of the AES encryptor with an RSA cypher. Users are left with nothing but to helplessly beg on security forums to have their files decrypted and malware researchers – oh well, they still try to find a solution to cope with this malware.

Cerber Ransomware and Its Distribution
To spread out into the open, Cerber may use several different-types of malware as well as helping tools:
It really depends which strategy will be used by this malware, because it is sold as a service online and every cyber-crook who buys it has the ability to customize it’s preferences. The Trojan droppers and exploit kits may be obfuscated by using advanced cryptors which will conceal the malware from the latest definitions of antivirus software. This will ensure the successful activation of Cerber ransomware and for its encryption process to be executed without any hic-ups.
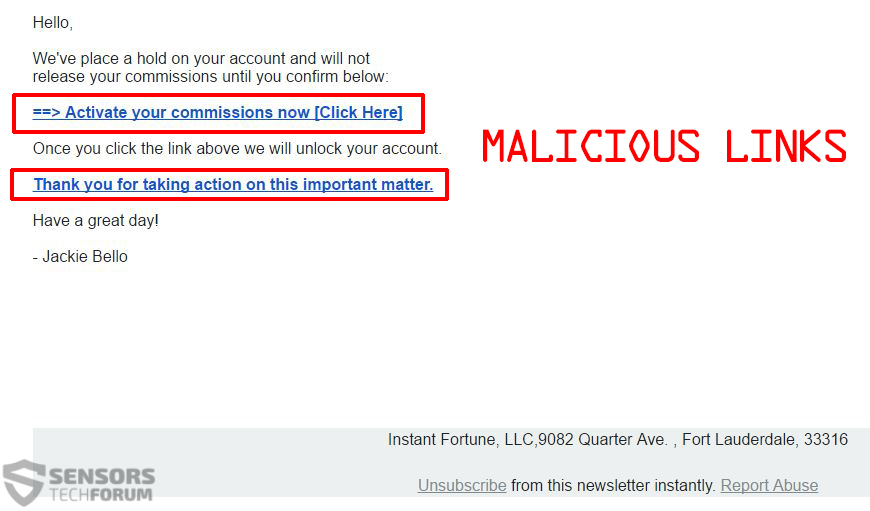
The malicious files may either be distributed using drive-by downloads and injectors via a malicious URL or might be featured on various websites as comments, or as reply’s on forums. It is also quite possible that users get infected via malicious links, such as the ones on the example below:
Not only this but the malicious software can be carried as an e-mail attachment as well. Once its malicious .exe is ran on your computer, it immediately begins to modify Windows’s file system as well as the Registry Entries of the OS. Then it begins a two-algorithm encryption process, looking for a wide variety of file extensions to encrypt. What is worse is that Cerber also encrypts larger than average files cyphering the first portion of the data of the large file.
How Do I Protect Myself from Cerber and Other Ransomware
To protect yourself from any type of threat, first you must know what you are dealing with and how does it work. However, we also have the human factor involved because cyber-criminals behind ransomware are masterminds of changing the methods of infection and obfuscation of the malware. Not only this, but they also tend to make other improvements to make they make income steadily from this cyber-crime.
The infection process of Cerber ransomware includes several scripts that help it achieve what it aims for. One of them includes pre-set commands that will help it to immediately start modifying the Windows Registry editor and creating files without permission. The logic behind this is to seek software that will not enable it to make such unauthorized modifications. This is why we suggest using sandboxing software, which will make sure you are a bit more protected.
One of the programs we have tested to counter the malicious exe’s is called Sandboxie. The software was successful in stopping an executable by closing it in a sandbox of encrypted code and thus not allowing it to make any modifications in the Windows file system. The ransomware’s executable was left with nothing else but to close itself.
This is a good tool, but it only serves well as a first line of defense against it. Sanboxing software is known to let some malware slip past it and still wreak havoc on your PC. This is why you will need an extra layer of protection. Fortunately, BitDefender have come up with an anti-ransomware software that looks for the specific actions ransomware performs and stops it from encrypting data. The software is constantly updated with the latest Ransomware coming out in the wild, and experts highly recommend it for basic home protection against ransomware.
Software Review of BitDefender Anti-Ransomware
However, it is important to know that ransomware is not only limited to its own executables. As previously mentioned, it also extends to other malware, which it uses to download itself. Such malware may disable any of the software that is preventing the ransomware from successfully encrypting your data and then download the ransomware on your PC. This is why we highly recommend using an advanced anti-malware tool which is frequently updated with the latest PUPs(Potentially Unwanted Programs) that may redirect you or display ads linking to malicious URLs and stopping malware in real time.
Also, as an additional layer of protection, we advise using a backup service. But when we say backup service, we mean that you should avoid using Volume Shadow Copies in and any other Windows default backup service on your PC. This is because ransomware nowadays usually deletes the shadow copies of the Windows machines that it infects. This is the main reason why you should orient towards using an external backup service. You may manually save your files on a USB drive or write them on a CD or a memory card. However, we recommend using automatic cloud backup service, such as SOS Cloud Backup.
Software Review of SOS Cloud Backup
These programs may be sufficient for you to be protected even if you belong to the unsafe users group. However, if your paranoia tells you that it is not enough, we suggest using an external firewall to increase your protection level. Such tools can be set to a maximum security mode and will detect any new process that tries to modify Windows. It is extremely useful, however it will constantly annoy you with pop-ups every time you start a program. Fortunately for you, you can set several programs you are using to trusted ones and stop it from asking you again. This works in general with all firewall programs. Most anti-malware tools have firewall embedded in them as an extra features, but companies like ZoneAlarm are using a separate firewall and what is better is that it is absolutely free.
What to Consider When Using Protection Tools
As a bottom line, not system is 100 percent safe. And if you want to invest in security go ahead. But bear in mind that it may not make your device 100 percent safe. This is why we recommend implementing several tips and recommendations that we have prepared and that will protect your from ransomware and other malware in the future:
As a bonus, we have prepared a report for top 10 free antivirus software, because we know that not every user has the availability to invest in such programs. This is why we have tested 10 of the biggest names in free antivirus to make sure users know what they are downloading. You can check the report below:
Top 10 Free Antivirus Software Report (2015)
Conclusion
As a conclusion we would say that there is no system that is 100 percent safe. This is why we strongly recommend to follow blog and our forum as well as other security blogs that are independent and provide free assistance to stay updated with the latest updates on malware and hence remain 1 step ahead of today’s cyber-crooks.