 Spear phishing attacks have turned into one of the biggest threats organizations are currently facing. Spear phishing attempts are typical for targeted attacks which aim at financial gain or trade secrets. This particular social engineering pattern can be followed by a range of sophisticated malware intrusions. It is indeed a matter that should be addressed by enterprises.
Spear phishing attacks have turned into one of the biggest threats organizations are currently facing. Spear phishing attempts are typical for targeted attacks which aim at financial gain or trade secrets. This particular social engineering pattern can be followed by a range of sophisticated malware intrusions. It is indeed a matter that should be addressed by enterprises.
According to a recent survey in which data from 300 companies (from the US and the UK) was analyzed, only 20% of the participants identify the outcomes of spear phishing and believe it is a top security issue.
What exactly is spear phishing?
Spear phishing is any attempt of email fraud that appears to be sent by an individual or an entity known to the recipient. In fact, the email was sent by an attacker. The purpose of spear phishing attacks is either stealing financial or personal data, or seeking access to confidential information.
What is the difference between phishing and spear phishing?
The ‘spear’ word pretty much illustrates the difference. Phishing attacks can be perceived as non-targeted attacks, aimed at a broad group of users. Phishing involves a social engineering scheme and a form of technical fraud. A phishing email is still sent with the purpose to trick users into clicking on malicious links or downloading malicious files. However, with spear phishing, certain individuals are targeted. Such individuals are known to have access to classified information, and in most cases, they are employees in big companies.
Spear phishing may be perceived as the evolution of phishing, as its next level. Many spear attacks have taken place throughout 2015, and if companies don’t learn their lesson, they will continue to suffer from huge financial loss.
More on Targeted Attacks:
Trochilus Remote Access Trojan
Cyber Space Implications 2015
Spear phishing in targeted attacks throughout 2015
What triggers most targeted attacks is usually just an innocently looking email that contains malicious files. The statistics prove it. According to the survey we mentioned in the beginning, those 300 companies have lost $1.6 million per security incident.
The survey has been carried out by Cloudmark, a San-Francisco-based company, and Vanson Bourne, an intelligent market research provider. What experts have discovered is quite alarming. The past two years have seen many high profile damaging data breaches that have been activated by a smartly crafted spear phishing email. The rule applies to both financial profit attacks and hacks on governments and private companies.
No business is safe against spear phishing – companies from various business sectors have fallen victims just because one of their employees has made a ‘small’ mistake.
The survey is the first to gather enterprise data specifically on the percentage of cyberattacks overall that spear phishing represents. Respondents said that in the past 12 months 84 percent reported that a spear phishing attack had penetrated their security defenses. These statistics point to a widespread inability to defend against these attacks.
Furthermore, spear phishing emails turned out to be the most common method, with 90% of the attacks being started by such a trigger. The second most likely way of penetration was spear phishing on mobile platforms (48%). The third place is taken by social networks (40%). Removable media has been targeted by 30% of spear phishing attacks.
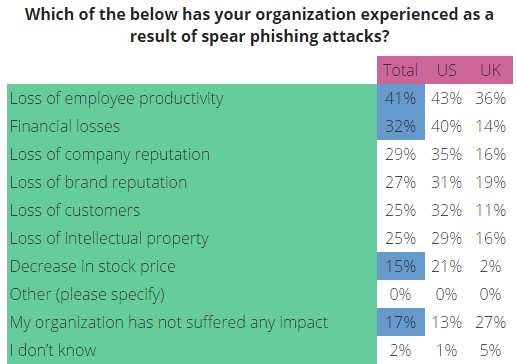
Image Source: https://blog.cloudmark.com/
What follows after a successful spear phishing campaign?
According to the survey’s results, a spear phishing attacks was followed by:
- Malware (34%);
- Authentication credentials discovery (30%);
- Corporate information requests (25%);
- Fraud attacks (9%).
Another interesting discovery was that IT professionals were mostly targeted by spear phishing (44%), followed by finance personnel (43%). It’s only logical that those two departments would suffer the most – they are the ones with most access to data and money.
Are companies taking precautionary measures against spear phishing?
71% of the companies that took part in the survey said that they have already implemented proper protection against ‘spears’. In addition, 56% of the companies have conducted trainings to prevent spear phishing from happening in the future.
Have a look at the whole Cloudmark survey.


