A new version of the well-know Troldesh ransomware (also known as Encoder.858 and Shade ransomware) was just discovered by researchers at Microsoft Malware Protection Center. This latest version appears to be extensively updated.
Other Versions of Troldesh:
- Remove Ransom:Win32/Troldesh.A (.xtbl Ransomware)
- Remove Troldesh Ransomware and Restore .Better_call_saul Encrypted

Threat Summary
| Name |
New Troldesh |
| Type | Ransomware Virus |
| Short Description | Encrypts files and demands payment. |
| Symptoms | .da_vinci_code and .magic_software_syndicate extensions are appended to the victim’s files. |
| Distribution Method | Not known yet, but most likely in spam campaigns, via exploit kits, malicious attachments, etc. |
| Detection Tool |
See If Your System Has Been Affected by malware
Download
Malware Removal Tool
|
| User Experience | Join our forum to discuss Troldesh ransomware. |
| Data Recovery Tool | Windows Data Recovery by Stellar Phoenix Notice! This product scans your drive sectors to recover lost files and it may not recover 100% of the encrypted files, but only few of them, depending on the situation and whether or not you have reformatted your drive. |

New Troldesh Ransomware July 2016 Technical Specifications
What’s New in Troldesh’s Latest Version?
- Tor functionality;
- Glyph/symbol errors on the wallpaper ransom note;
- Modified extension names for encrypted files;
- Updates in the ransom note that cover the added Tor functionality.
- New malware being downloaded to the victim’s PC – Trojan:Win32/Mexar.A;
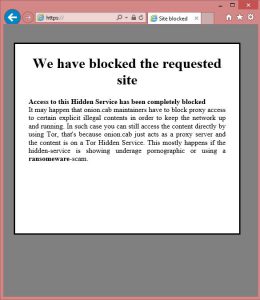
The most notable modification in this version is the addition of Tor links. Using Tor addresses as the ransom payment method (as opposed to standard www addresses) is the current fashion among ransomware, Microsoft researchers explain.
A Tor address is now included in the ransom note, as opposed to the older Troldesh where an email address was the only way to provide decryption keys.
However, the Tor payment website is not functioning as it is reported to be down (see image above). This means that there’s no way to pay the ransom and recover the files through contacting the cyber criminals.
Other changes in the code of this new Troldesh are the “creative” file extensions – .da_vinci_code and .magic_software_syndicate.
Also, the crypto virus is now capable of encrypting even more file type categories and delivers an additional piece of malware – Mexar (Trojan:Win32/Mexar.A). This is a completely new malware, detected by Microsoft for the first time on July 7. No technical information is available at the moment, but it’s highly likely that the Trojan is an infostealer. We will update the article when we have more information.
Microsoft recently revealed that Troldesh is the tenth most active ransomware family in the past 30 days.

Troldesh Ransomware Removal and Restoration of .da_vinci_code and .magic_software_syndicate Files
Like we already said, paying the ransom is not possible because the Tor website is currently down. You can still remove the threat and try to get your files back via alternative methods. To do this, we advise you to carefully follow the removal instructions below and boot your computer in Safe Mode. From there, you may want to go over and take a look at the Manual and Automatic options for removal below.
In case Troldesh has modified various registry entries and has created additional files, experts strongly advise using an advanced anti-malware program to automatically remove the virus in Safe Mode without damaging your computer.



Leave a Comment