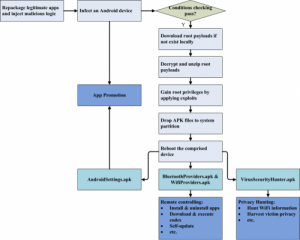
A new Trojan targeting Android devices – Rootnik – has just been analyzed by security vendors. Rootnik is designed to use a customized commercial root tool known as Root Assistant, developed by a Chinese company. Root Assistant was developed to help users acquire root access to their devices.
How does Rootnik take advantage of Root Assistant? The cyber criminals applied reverse engineering techniques, and stole at least five exploits that allowed them root access to Android. Affected systems include Android 4.3 and earlier versions.
Users compromised by the Trojan are located in the US, Malaysia, Thailand, Taiwan and Lebanon. However, having in mind how malicious software moves around, more victims from other locations are expected.
More Android-Related News:
Taomike SDK Library Caught Spying on SMS in 18 000 Apps
How to Remove Lockerpin.A Ransomware from Android
Rootnic Infection Methods Analyzed and Explained
Researchers at Palo Alto explain how Rootnik works. They observed that Rootnik could spread by being embedded in copies of legitimate apps such as:
- WiFi Analyzer
- Open Camera
- Infinite Loop
- HD Camera
- Windows Solitaire
- ZUI Locker
- Free Internet Austria
Researchers also noticed that Rootnik was able to perform a range of malicious actions such as:
- Exploit a customized version of Root Assistant and the following Android vulnerabilities – CVE-2012-4221, CVE-2013-2596, CVE-2013-2597, CVE-2013-6282;
- Achieve a persistent state via installing APK files on the system partition of the attacked device;
- Installing and uninstalling system and non-system application without the user’s knowledge or approval;
- Downloading .exe files from remote locations;
- Displaying malicious pop-up advertisements in full screen, promoting other applications.
- Stealing WiFi details from compromised devices such as passwords, keys and SSID (Service Set Identifiers) and BSSID (Basic Service Set) identifiers.
- Stealing PII (personally identifiable information) such as location, phone MAC address, device ID, etc.
The Rootnik Trojan is also able to connect to several domain names:
applight[.]mobi
jaxfire[.]mobi
superflashlight[.]mobi
shenmeapp[.]info
Palo Alto researchers also warn that at the time of their analysis, those remote locations were active.
Rootnik’s Payload
As already mentioned, the Android Trojan’s distribution consists of repackaging and inserting malicious code into legitimate applications. After execution, Rootnik launches a new threat to obtain root privileges.
In case the compromised device is running Android 4.3 or earlier, and the device is not located in several countries specified in the AndroidManifest.xml file, Rootnik will try to get root access. All analyzed samples were configured to gain such access in all locations expect China. This fact is quite intriguing, since the root tool (Root Access) employed by the Trojan is also developed in China.