The researchers from Tel Aviv University and Weizmann Institute of science, called Daniel Genkin, Adi Shamir, Eran Tromer were able to break the toughest encryption used by most ransomware viruses – RSA – 4096 bits. The revolutionizing cyber-attack was performed in the most simplistic manner – by using a microphone that listens to very low frequencies (under 20 kHz). The researchers have also demonstrated in their report a mean to ‘sniff’ out a decryption, using a smartphone. This attack raises many questions, regarding the future of cyber security and file protection.
How Did They Do It?
What the researchers did was called an acoustic cryptanalysis. This is a side channel type of attack that is essentially scanning the ‘fingerprints’ of the noises which a processor makes. To make it simple, let’s say that you use a fingerprint scanner, but you also leave fingerprints of your same finger on other places. If someone copies those same fingerprints using a unique method and applies them, he will hack the fingerprint scanner. The situation with the acoustic cryptanalysis is somewhat the same – the researchers use the ‘fingerprint’ of the vibrations of the computer when dealing with the decryption. They claim that they were able to listen via VGA, USB Port, Ethernet Port and any other jacks that have metallic parts in them and are connected to the laptop chassis.
The researchers have divided their report into several phases:
1. Vibrations observation and collection.
2. RSA key distinguishing.
3. RSA key extraction.
They have also established another method to sniff out the RSA keys, in which a simple smartphone was employed. The interesting part is the ability to listen to the information using a special microphone that was was placed close to the the ventilation of the laptop.
Another method the researchers demonstrated was tuning into the vibrations into an ethernet cable connected to the computer’s chassis. It was called Far-end-of-cable attack. The researchers have used three types of microphones, varying from 0-18kHz, 0-20kHz and 0-100kHz to listen to low-frequency impulses from the computer. More so, they have employed a power supply, a preamplifier and a Data Acquisition Device (DAQ) to digitalize the collected data.
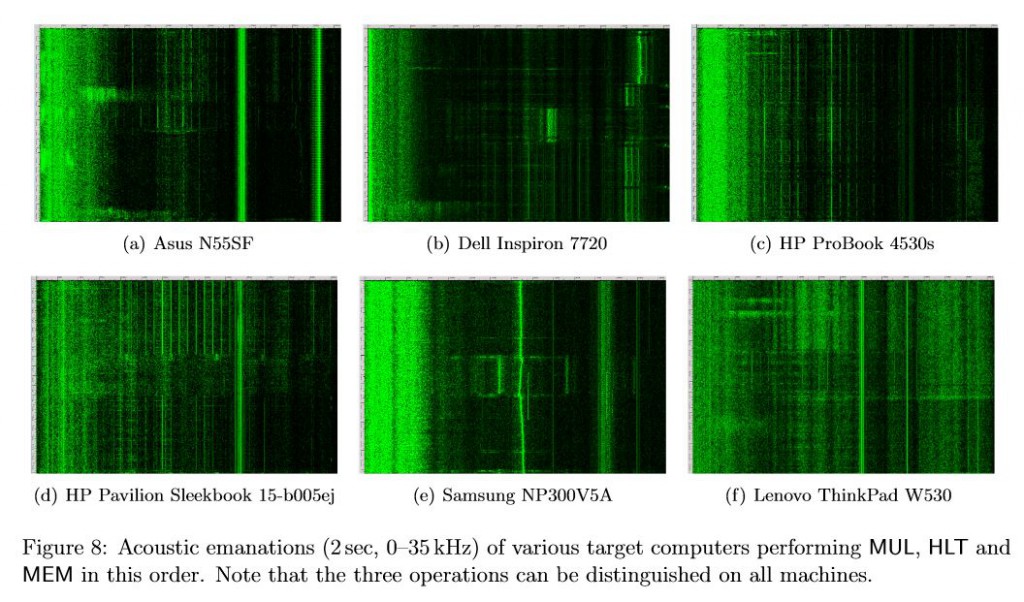
Using the devices, the researchers were able to distinguish between different signal patterns from different PC models:
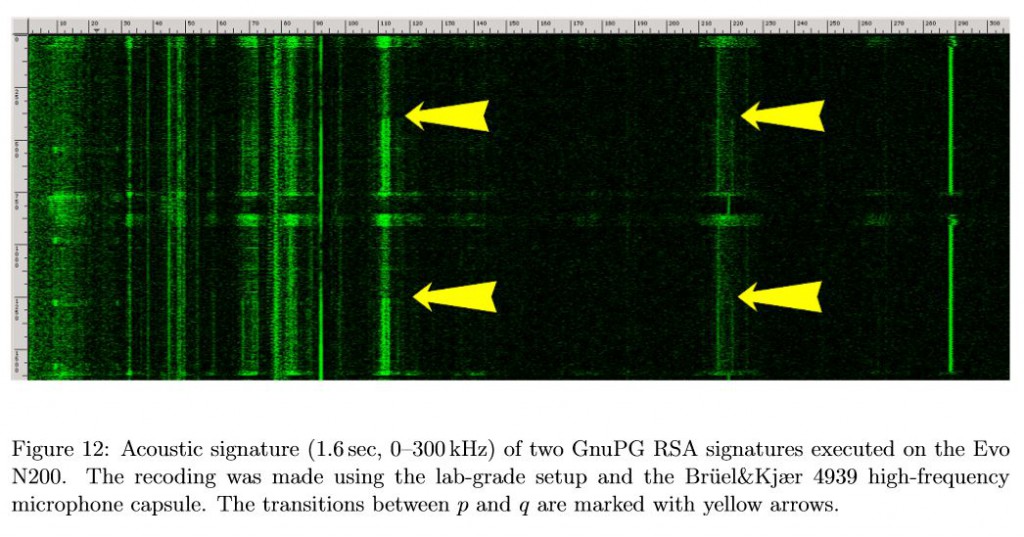
Also, a significant discovery was that the researchers were able to find secret keys in the form of bright horizontal lines in the acoustic signature of the laptop. This was an essential component in establishing the decryption keys.
Conclusions
This is a crucial discovery, and it is not to be disregarded because it is directly related to online security. More to it than that, in case you want to keep your information secure, it is important to keep your PC in a sound-proof environment. Also, for best security do not disregard the good old method of sniffing – do not allow people next to your computer while you are performing a decrypting operation. An excellent way to protect yourself is to use a low-frequency sound that will deafen any close by PC microphones.