Cybersecurity researchers recently identified more than 300 phishing campaigns created to harvest personal and banking details from potential victims.
Most of these scams are using sites that are identical to the original ones, made with authentic images and user interfaces.
According to Proofpoint, such phishing campaign templates facilitate the creation of high-quality, malicious web domains. Currently, these are used in phishing campaigns related to the COVID-19 pandemic. But the topic may be changed in the near future, in accordance with the next global or local crisis.
Who is impersonated in these highly professional phishing campaigns?
Organizations such as WHO (World Health Organization), the US Centers for Disease Control, the IRS, HMRC in the UK, and local councils across London.
Where can these phishing templates be found?
On underground forums. The templates also include multiple pages to make them look even more authentic.
What are the phishing pages aiming at?
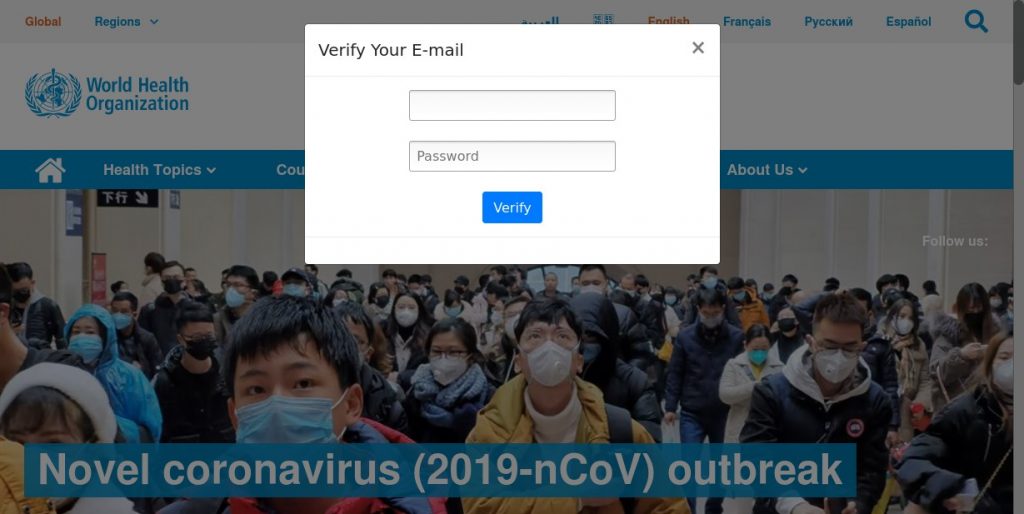
More than half of the 300+ COVID-19 phishing campaigns Proofpoint has observed since January 2020 are focused entirely on capturing user credentials. Here’s an example that illustrates the professionalism of the latest phishing campaigns circling the web:
This example, Proofpoint explains, is a template designed to copy the look and feel of the legitimate WHO site. As visible, the site copies the WHO logo and color scheme and is designed to be deployed as part of a credential phishing campaign. Here, cybercriminals are aiming at obtaining a visitor’s username and password. The malicious motive is hidden behind gaining access to information about COVID-19 safety measures.
Another example perfectly represents the legitimate site of CDC (the US Centers for Disease Control). The template asks the potential victim for their email address and password to receive a Vaccine ID. The modal box of this phishing scam asking for credentials in this case includes logos of Microsoft Outlook, Google Gmail, Microsoft Office 365, Yahoo!, and AOL. The list of included email providers makes the scam a broad web email credential phishing template repurposed for this theme, the researchers point out.
The COVID-19 pandemic has been widely exploited in various malicious campaigns, both phishing and malware-delivering. There were even cases where cybercriminals tried to steal money from people financially impacted by the pandemic. In April, Australians financially impacted by the current pandemic were indeed being targeted by fraudsters attempting to steal their superannuation funds. Scammers were cold-calling people impersonating representatives of organizations that supposedly help to get early access to superannuation funds.