Increasingly more sophisticated and innovative ways are being developed by cybercriminals to ensure they can break into systems. Here are several obfuscation techniques employed by hackers with ways you can protect yourself from them.
Obfuscation is widely used by malware writers to evade antivirus scanners. It is essential to analyze how these obfuscation techniques are used in malware. With new methods and technologies being developed at an exponential level, it becomes an evergreen issue for cybersecurity researcher to explore.
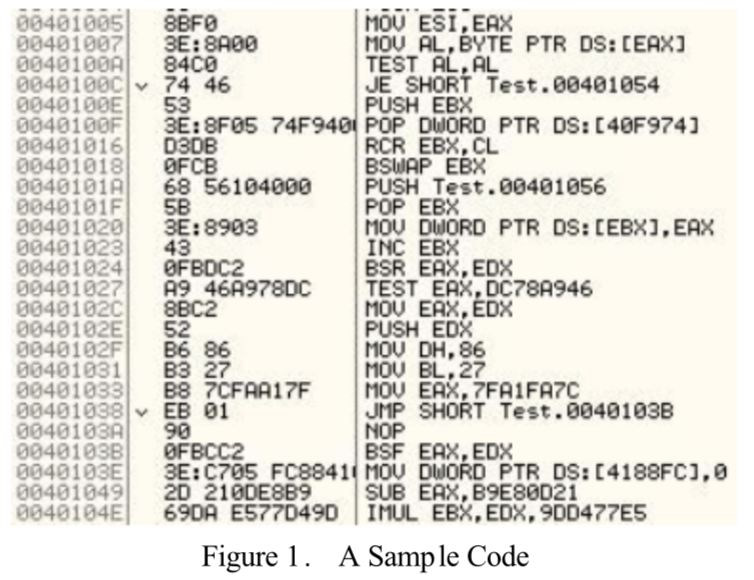
1. Dead-Code Insertion
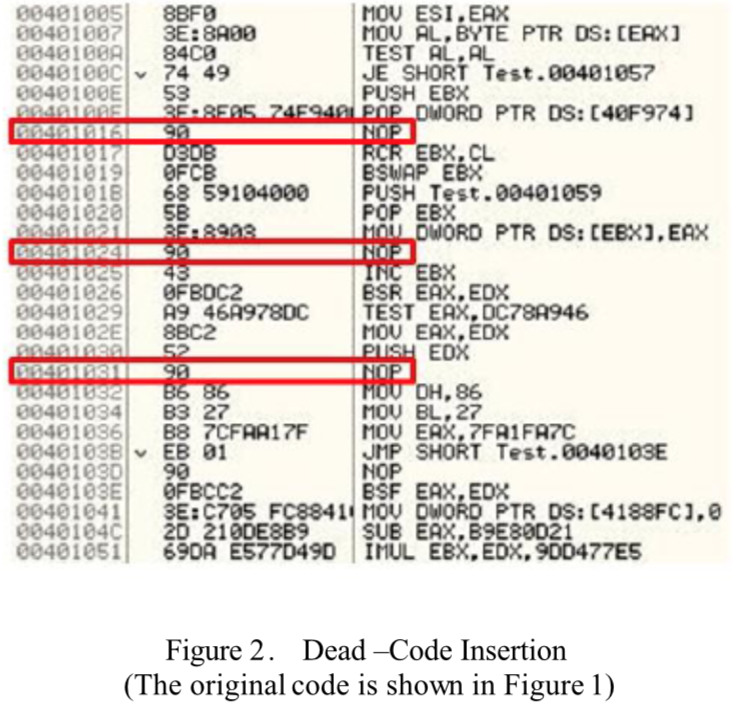
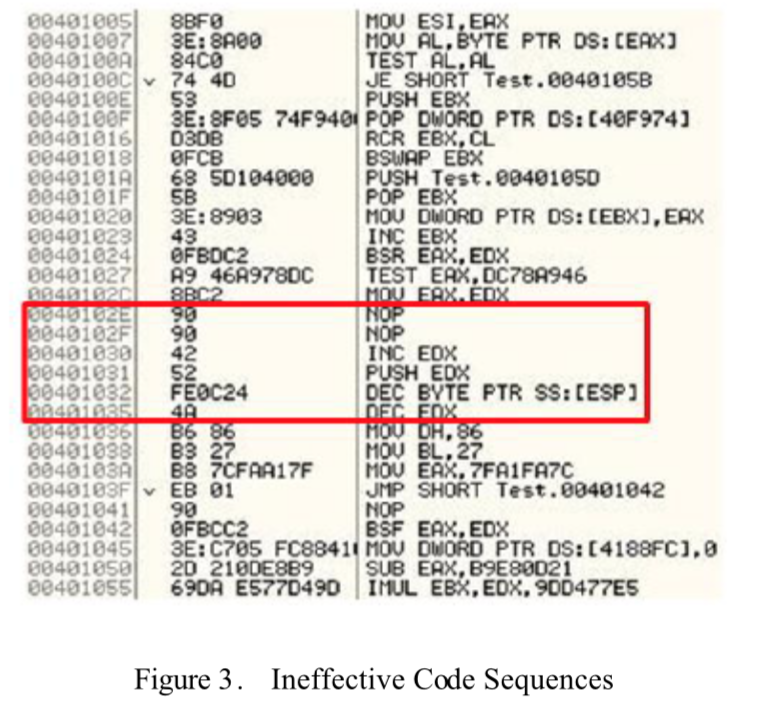
This is a simple rudimentary technique that functions by adding ineffective instructions to a program to change its appearance, however, not altering its behavior. Figure 1 and 2 display how easy it is for the original piece of code to be obfuscated by adding in nop instructions. To combat dead-code insertions, the signature based antivirus scanners should be able to delete the ineffective instructions before analysis. Thus, the obfuscating code, trying to ensure its survival and making detection more difficult, some code sequences could present themselves as shown in Figure 3.
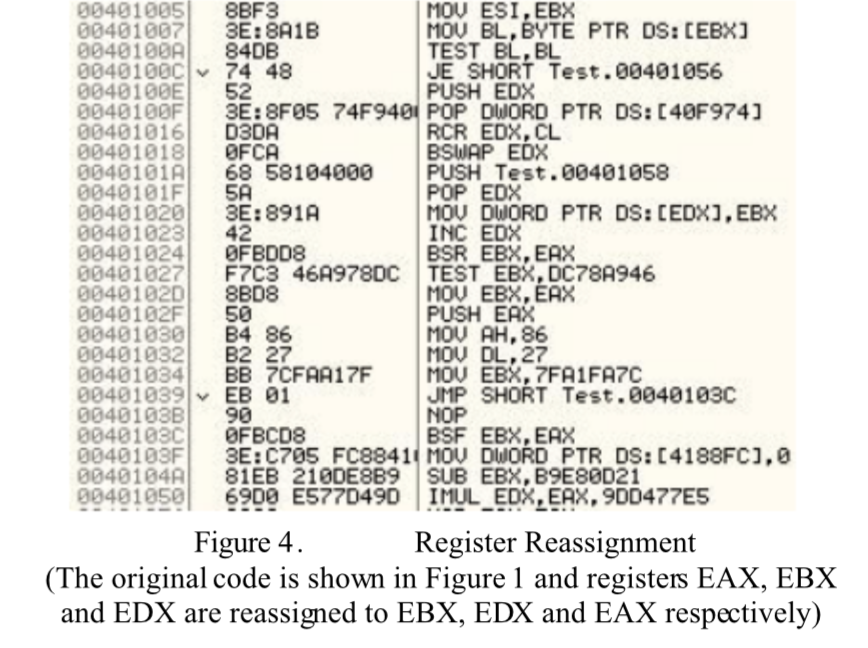
2. Register Reassignment
Register reassignment is a technique which switches registers from generation to generation while in the meantime it keeps the program code without altering its behavior. Figure 4 illustrates an example whereby the original code used in Figure has evolved through switching the registers. (employed by Win95/Regswap virus)
Note that the wildcard searching can render this obfuscating technique useless.
3. Subroutine Reordering
Subroutine reordering is an obfuscating technique which makes the original piece of code harder to detect by antivirus programs by changing the order of the code’s subroutines in a randomized manner. It is a very clever way of saying that this technique can generate n! different variants, whereby n is the number of subroutines, e.g., Win32/Ghost had ten subroutines, meaning 10! = 3628800 different generations of the code.
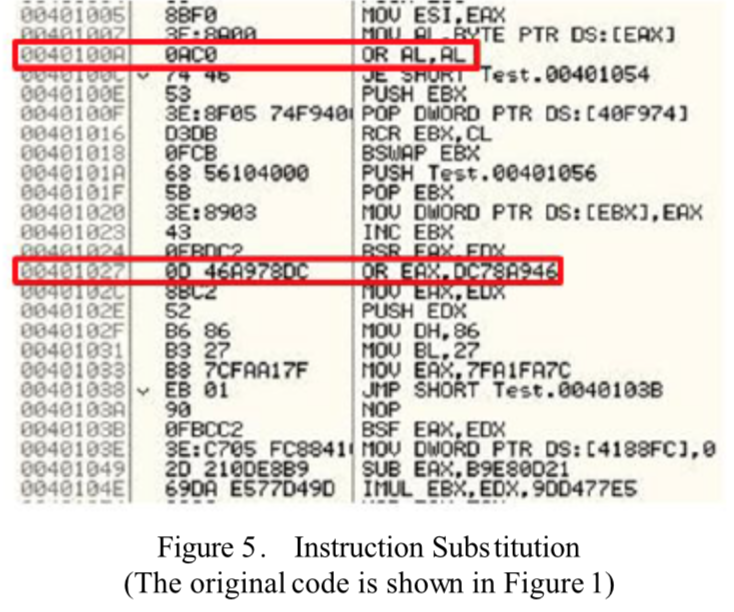
4. Instruction Subroutines
This kind of obfuscation technique makes sure the original code evolves by replacing some instructions with other equivalents to the original instructions ones. To take an example from Figure 5, xor can be replaced with sub and mov can be replaced with push/pop. This technique can change the code to a library of similar instructions.
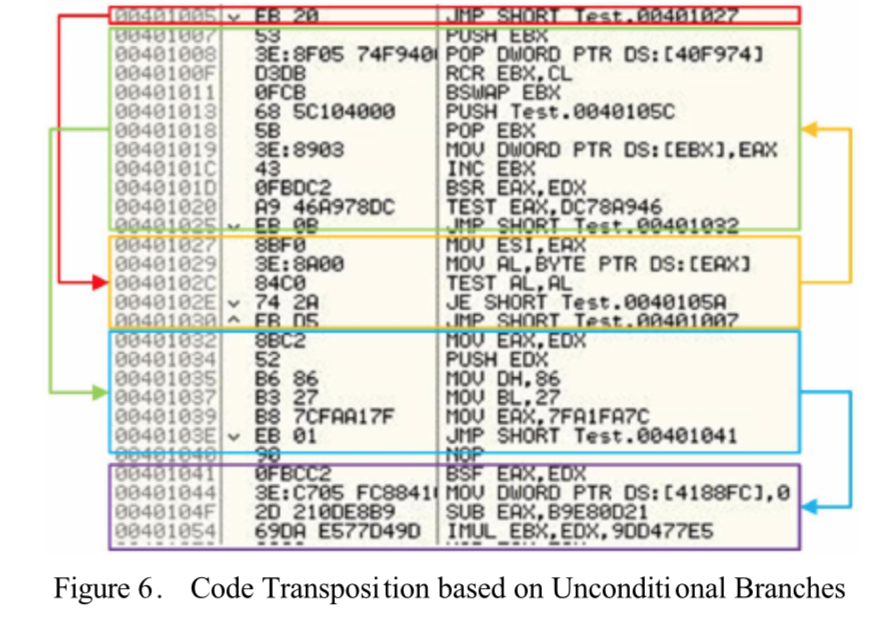
5. Code Transportation
Code transposition employs a reordering of sequences of the instruction of an original code without having any visible impact on the code’s behavior. Essentially, there are two methods to deploy this technique into action.
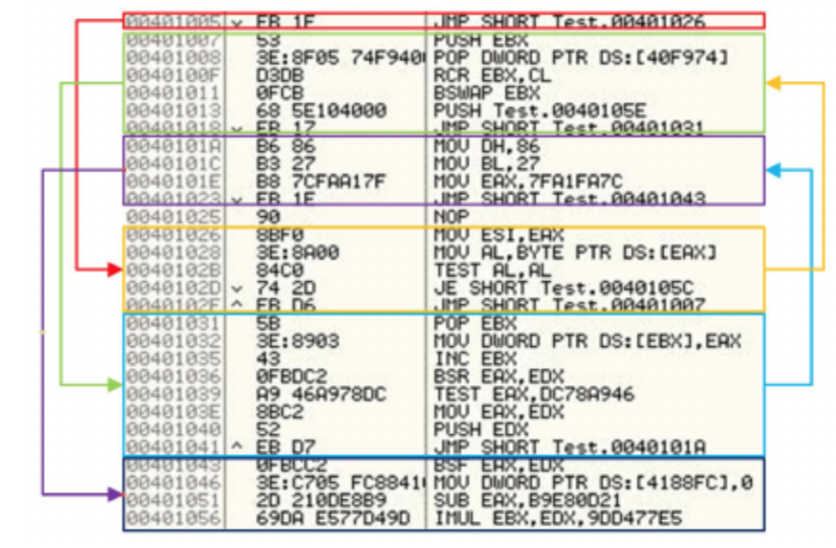
The first method, exemplified in Figure 6, randomly shuffles the instructions, proceeding on to recovering the original execution order by inserting the unconditional branches or jumps. A way to combat this type of obfuscation is to restore the original program by removing the unconditional branches or jumps. In comparison, the second method creates new generations by choosing and reordering the free instructions which have no impact on one another. It is a sophisticated and complex problem to find the free instructions. This method is hard to implement, however, it can also make the cost of detection high. Figure 7 illustrates the second method.
6. Code Integration
Code integration was firstly introduced by the Win95/Zmist malware also known as Zmist. The Zmist malware binds itself to the code of its target program. In order to execute this technique of obfuscation, Zmist must firstly decompile its target program into small manageable objects, and slot itself between them, proceeding on to reassembling the integrated code into a new generation. By far this is one of the most sophisticated obfuscation techniques and can make detection and recovery very difficult, as well as costly.
Ways to Protect Yourself From Advanced Malware Obfuscation
Many of the obfuscating techniques discussed above either involve changing malware code to avoid signature-based detection or using behaviours that are malicious, albeit we conclude so in hindsight. Malware obfuscation is a complex issue in cybersecurity and although it may be able to change how it represents itself to the user, it cannot nonetheless change its malicious behaviour, hence much of antivirus software and advanced detection solutions base their core detecting principle on suspicious behaviour. Malware can also hook processes with known network capabilities in order to help mask any malicious traffic.
Such solutions play the role of the victim with all the normal software that comes with the average user in a term coined as “sandbox”. When the system detects a suspiciously acting file, it executes them in these closed of simulated sandbox environments to test their credibility. Such systems can accurately tell if any suspicious file entering the system is malicious by monitoring for hundreds of known typical malware behaviours.
That is not to say criminals are not aware of sandboxes. As a matter of fact, some of the latest evasion tactics function solely with the purpose to evade sandboxes. Such tactics include fingerprinting sandbox systems – using techniques ranging from CPU timing checks known registry entries. Other techniques include even human interactions meaning going to the lengths of checking whether the mouse has been moved recently, hence, check if the computer is being used by a human being or whether it is automated.
Hackers may seem like the passive enemy, but malware distributors have already created protectors that are able to detect some sandboxes. Nonetheless, there have been some advanced solutions developed which take this into full consideration. Hence, some solutions make use of full system code emulation and therefore create sandbox environments where they are able to observe every instruction a malicious piece of software sends to the CPU or memory. This kind of visibility allows for more advanced malware solutions in detecting malware obfuscation.
To stay protected against malware threats utilizing advanced obfuscation techniques, using a powerful anti-malware solution is a must.
Spy Hunter scanner will only detect the threat. If you want the threat to be automatically removed, you need to purchase the full version of the anti-malware tool.Find Out More About SpyHunter Anti-Malware Tool / How to Uninstall SpyHunter




Hey can you suggest a free available tool for this ? I want to create malware test scenarios – I am looking to use these teqniques to create undetectable EICAR test files.
Hello, it is not exactly a good Idea to suggest such tools, but I would ask in hacking forums (Russian, for example) for any tool that might work for you. Such forums are similar to the following darkpro.ws.
And also if you want something undetectable, it is next to impossible, because most zero-days are often in the databases of most anti-malware and anti-virus companies and if you want to remain undetectable, you will need to pay for it on underground forums.