This article will aid you in removing the AnDROid ransomware fully. Follow the ransomware removal instructions given at the bottom of the article.
The AnDROid ransomware has been discovered by malware researchers from the MalwareHunterTeam. Not only will it encrypt your files, but the cryptovirus also has a lockscreen feature. When a computer gets infected, the AnDROid cryptovirus will display a window with a ransom message after the file-encryption process. Inside that window, there will be an animated skull image along the ransom instructions. The screenlocker can be removed with a specific unlock code. Read on to see how you can recover your files and unlock your screen.

Threat Summary
| Name | AnDROid |
| Type | Ransomware, Cryptovirus |
| Short Description | The ransomware virus will encrypt your files and also put up a screenlocker window that will block access to your computer device. |
| Symptoms | The ransomware will display a window containing payment instructions and will encrypt files while placing the .android extension to them. |
| Distribution Method | Spam Emails, Email Attachments |
| Detection Tool |
See If Your System Has Been Affected by malware
Download
Malware Removal Tool
|
User Experience | Join Our Forum to Discuss AnDROid. |
| Data Recovery Tool | Windows Data Recovery by Stellar Phoenix Notice! This product scans your drive sectors to recover lost files and it may not recover 100% of the encrypted files, but only few of them, depending on the situation and whether or not you have reformatted your drive. |

AnDROid Ransomware – Update

AnDROid Ransomware – Infection Spread
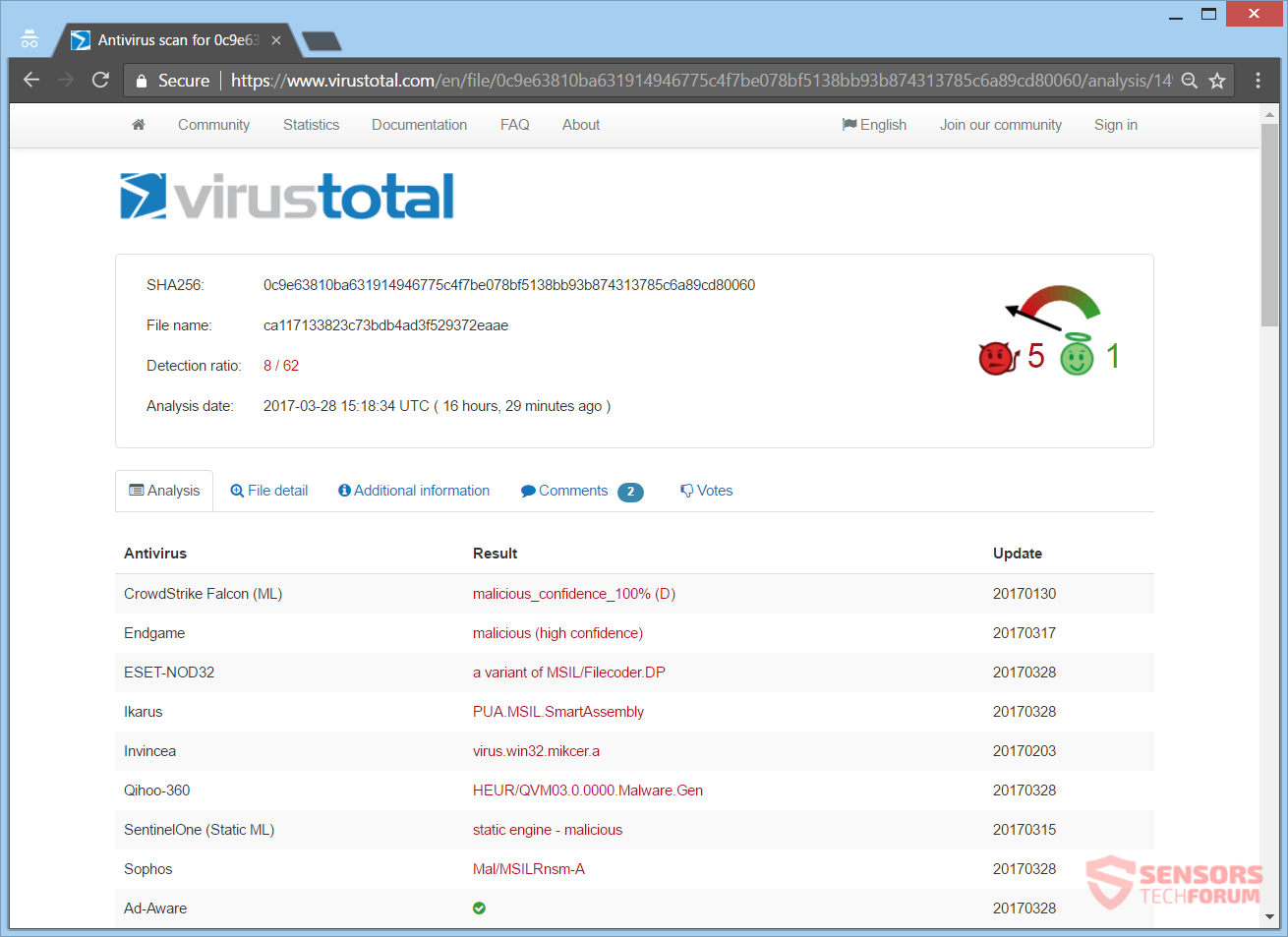
AnDROid ransomware might spread its infection through different ways. The payload file which executes the malicious script for this ransomware, that in turn infects your computer system, is circling around the Internet. Samples of this ransomware have been found by a few different malware researchers. You can see the detections of various security vendors for one such sample by checking the screenshot from the VirusTotal service right here:
AnDROid ransomware could also spread its payload file on social media sites and file-sharing networks. Freeware applications which are found on the Web could be presented as helpful but at the same time could be hiding the malicious script for this cryptovirus. Don’t be opening files right when you have downloaded them, especially if they come from sources such as suspicious links or emails. Instead, you should scan them beforehand with a security tool, while also checking the sizes and signatures of those files for anything that seems unusual. You should read the tips for ransomware prevention in our forum section.

AnDROid Ransomware – In Detail
AnDROid is what a new ransomware cryptovirus is called. Once your files get encrypted, they will receive the .android extension. The AnDROid ransomware could make entries in the Windows Registry aiming to achieve a higher level of persistence and to keep the screenlocker function on top of all other windows. Those registry entries are typically designed in a way that will start the virus automatically with each launch of the Windows Operating System.
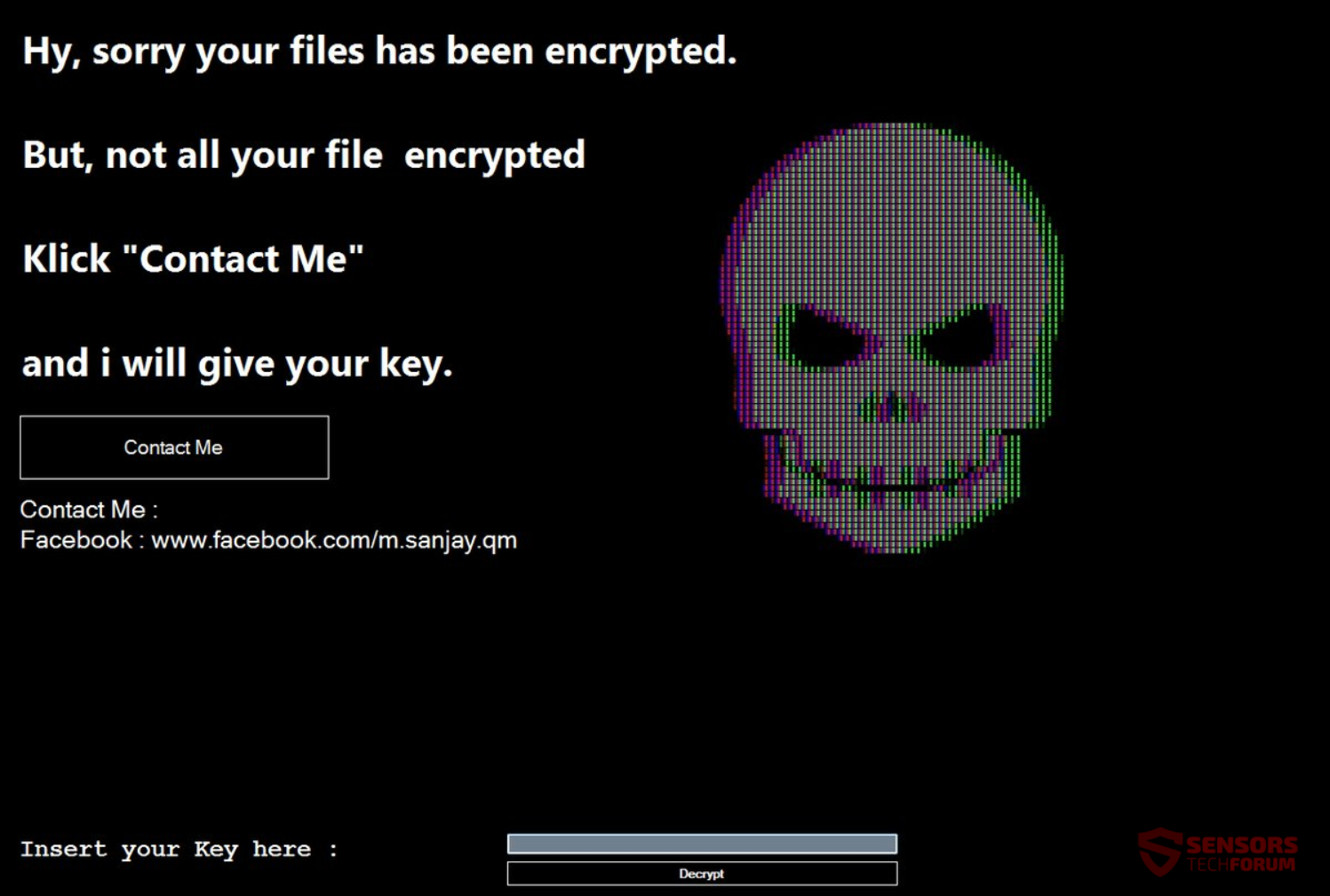
The ransom note will appear after the encryption process is set and done. The note provides instructions on how you might get your files back. The note of AnDROid opens in a window, which also activates the screenlocker feature. You can see the message from that note in the snapshot provided below:
The ransom message inside that window reads the following:
Hy, sorry your files has been encrypted.
But, not all your file encrypted
Klick “Contact Me”
and I will give your key.
Contact me
Contact Me :
Facebook : www.facebook.com/m.sanjay.qm
Insert your Key here :
Decrypt
As clearly seen from the ransom message above, the developer of the AnDROid cryptovirus has provided a facebook page as a contact. If you get your computer infected with the malware, you should NOT under any circumstances pay any sum of money to the cybercriminal who is behind it. Nobody can guarantee that you will get your files back to normal upon payment.
AnDROid Ransomware – Encryption Process
AnDROid ransomware has quite a high probability to search and encrypt files, which have the following extensions:
→.doc, .docx, .pdf, .db, .jpg, .png, .ppt, .pptx, .txt, .xls, .xlsx
The extensions mentioned above are for file types which are still the most commonly used among Windows users and Windows is the predominant operating system.
If you want to remove the lock on your screen and get the ransom message window down, all you have to do is type in the following unlock code:
Be aware that a defense mechanism might be in place, that could break your files if the wrong unlock code is entered, as it was the case with the Noob Ransomware virus.
The AnDROid cryptovirus might be set to erase the Shadow Volume Copies from the Windows Operating System with the help of the following command:
→vssadmin.exe delete shadows /all /Quiet
The execution of that command usually makes the encryption more viable, since it eliminates one of the prominent ways for the restoration of your files.

Remove AnDROid Ransomware and Restore .Android Files
If your computer got infected with the AnDROid ransomware virus, you should have a bit of experience in removing malware. You should get rid of this ransomware as quickly as possible before it can have the chance to spread further and infect other computers. You should remove the ransomware and follow the step-by-step instructions guide provided below.