WikiLeaks reported that the CIA is involved in the creation and coordination of a dangerous Android malware called HighRise. The report showcases the full features of HighRise as well as a copy of the Users Guide.
HighRise Android Malware – Yet Another Spying Tool by the CIA
Yesterday (July 13th 2017) WikiLeaks published a document that revealed information about the covert project operated by the CIA. According to the released information and the sourced documentation the second version (HighRise 2.0) is compatible with the Android mobile operating system from 4.0 (Ice Cream Sandwich) to 4.3 (Jelly Bean).
WikiLeaks released the user’s guide for the HighRise Android malware that reveals much of the utility’s functionality. According to the security community this is just another product in a series of coordinated packages utilized by the institution for spying on computer and mobile users. The WikiLeaks site has published information about the case as part of the “Vault 7” collection, attributed as being one of the largest publications of confidential documents on the CIA.
According to the organization the CIA has “lost control of the majority of its hacking arsenal including malware, viruses, trojans, weaponized “zero day” exploits, malware remote control systems and associated documentation”. Several experts have already stated that the intelligence agency does have the resources to operate their own coordinated global covert campaign. The CIA has been involved in developing hacking tools that penetrate popular services and devices. The agency has demonstrated that it has serious intentions to break through many layers of security, a recent example is the OutlawCountry exploit that can compromise Linux systems.
HighRise Android Malware Infection Behavior
The HighRise malware is compatible with Google’s Android operating system, the leaked documents describe a second iteration of the virus. According to the changelog it has been compiled on December 16th 2013 and bears the following note “Initial EDG release. Port to Android 4.0-4.3” and its authority is under “TDR”, probably an internal unit of the CIA. The message states that the code has been ported to the newer (back then) version of the operating system. This gives us a reason to believe that the HighRise Android malware has been developed for an extended period of time over the years. It is very likely that a newer version of it is actively being developed and operated even now. Its functions include a redirector module that is used for manipulating SMS messages. It effectively allows the CIA to perform several actions:
- Proxy “incoming” SMS messages received by HighRise host to an internet LP.
- Send “outgoing” SMS messages via the HighRise host.
- Provide a communications channel between the HighRise field operator & the LP.
- TLS/SSL secured internet communications
Further on the CIA compares v2.0 as having a modified infection flow:
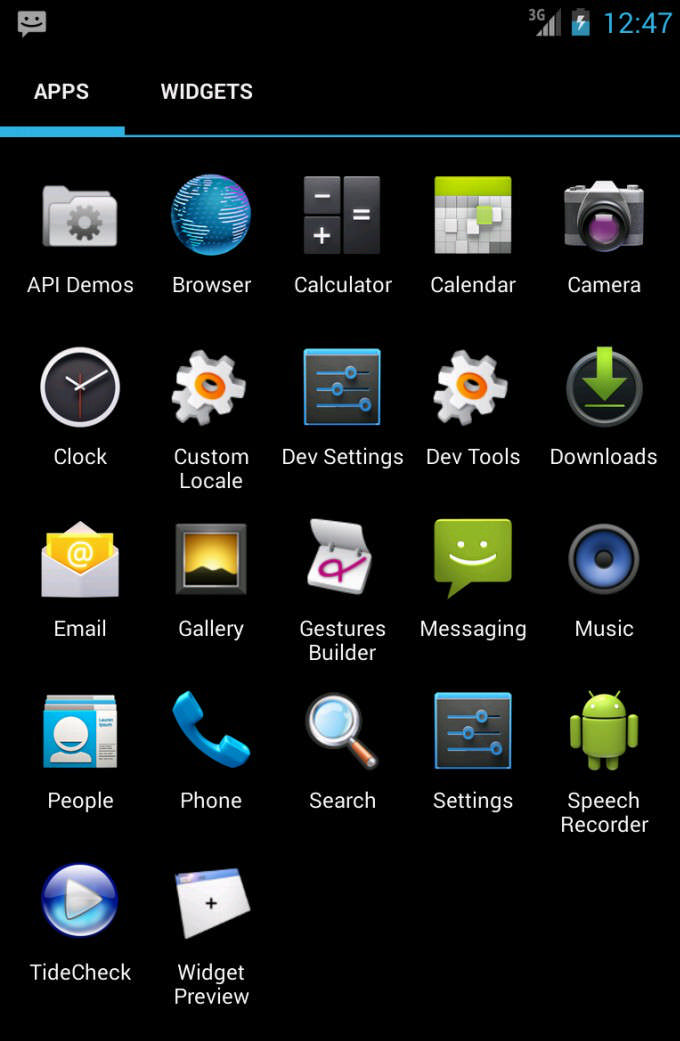
1.The HighRise needs to be manually downloaded and installed on the target device. After this is done the malicious code will run automatically in the background or after a reboot is scheduled. To prevent discovery it masquerades itself as an application called “TideCheck”. The APK installation file is hosted on a download sites or a third-party repository.
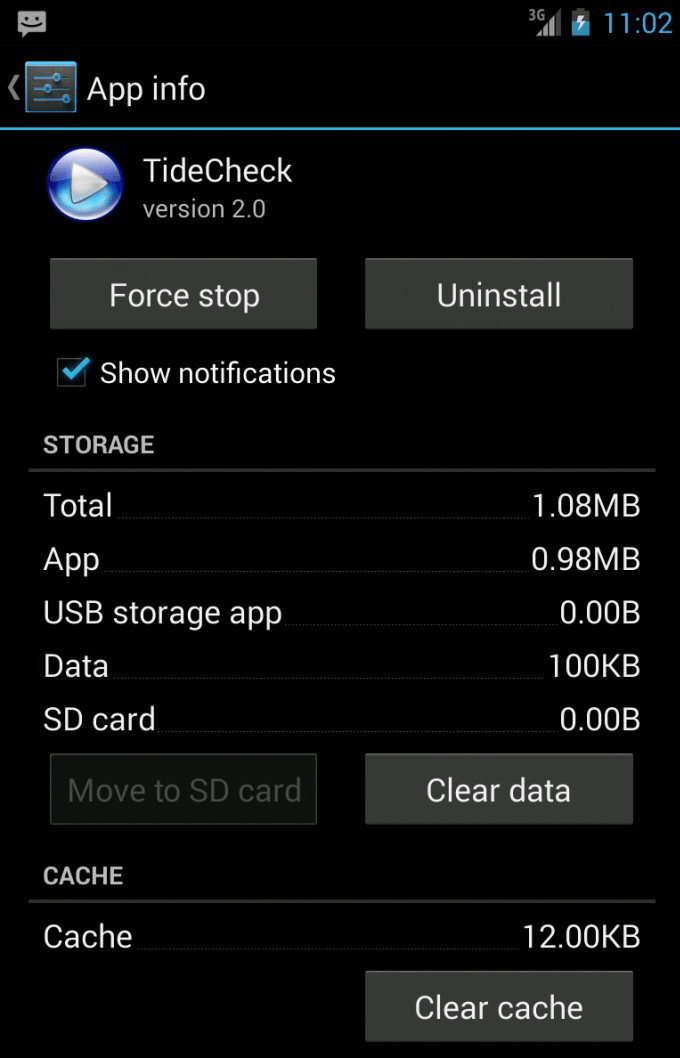
NOTE: The application can be effectively removed by navigating to the Application settings, double tapping on its name (TideCheck) and following a sequence of commands: Force Stop, Clear data and Uninstall.
2.The next step is to manually start the application. This is done by tapping on the application in the Android drawer.
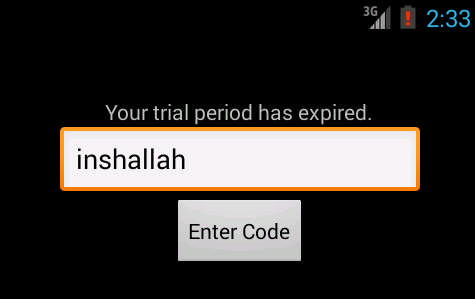
3. The HighRise Android malware will then prompt the users for a password string by displaying a counterfeit prompt “Your trial period has expired”. The hardcoded one is “inshallah” (Arabic for “if God wills”) and then select the “Enter Code” button.
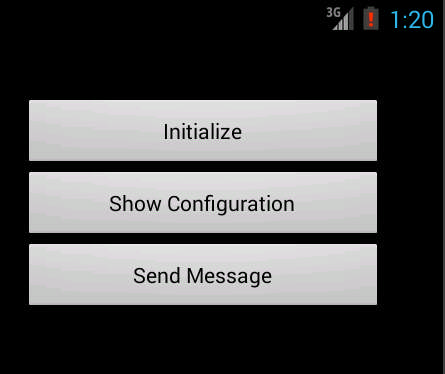
4. The HighRise Android malware can then be activated by clicking on “Initialize”. This effectively configures the malware into running in background mode.
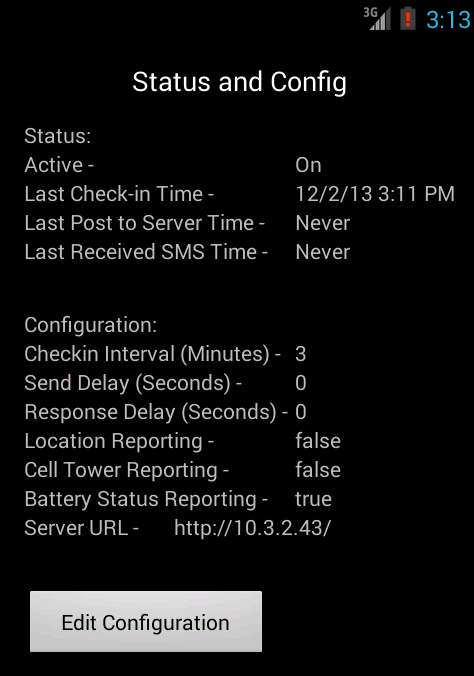
5. By clicking on “Show Configuration” the users can access the internal settings of the application. They reveal several values that are related to the network report function. Modifications can be manually entered by clicking on the “Edit Configuration” button.
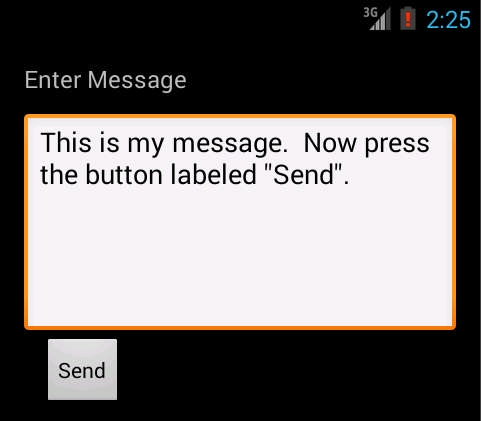
6. The HighRise Android malware can be used to send SMS messages to the CIA operatives by tapping on the Send message command.
Impact of the CIA HighRise Android Malware
WikiLeaks revealed that currently there is no information available on newer versions of the HighRise Android malware. It is not known if it still being used, developed or updated. Effectively the app acts as a messages proxy by relaying the incoming and outgoing SMS to CIA listening posts operated on the Internet. HighRise operators were able to spy on millions of users worldwide by implementing the virus in payloads. Possible automated infection scenarios can include the following:
- The HighRise Android Malware can be configured to auto install as part of a malicious payload. This can include various apps and components distributed on the Google Play store or third-party repositories. Usually counterfeit apps are uploaded by using anonymous and fake developer identities. The CIA operatives may pose as an independent programmer or company and use images and graphics to lure potential victims into downloading and running their application.
- A web script can trigger pop-ups or other malicious tricks to trigger the HighRise Android malware installation.
- CIA operatives can utilize social engineering tricks by posting counterfeit system optimization or recovery instructions to try and confuse the targets into infecting themselves with the virus.
Whatever happens it is likely that WikiLeaks will continue to report on other tools created and used by spying and intelligence services. The provided information reveals just how much the government agencies infiltrate into the privacy and security of computer users all over the world. The HighRise Android malware is not made for a specific region. In practice it can be used to extract data and relay sensitive information from Android devices all over the world.