 This article has been created in order to explain what is the Android Red Alert malware and how to remove it from your computer.
This article has been created in order to explain what is the Android Red Alert malware and how to remove it from your computer.
New malware for Android has been detected by malware researchers to perform series of unwanted activities on the Android devices that have been affected by it. The malware has further been reported to cause numerous different issues on the victim’s computer, such as steal important information from it and possibly install other malware on it. In addition to this, the malware has been reported to come in the form of an update and to slither completely unnoticed on the victim’s device. In the event that your device has been infected by the Android Red Alert malware, we advise that you read the following article to learn how to remove it from your device and protect it against future Android viruses as well.

Threat Summary
| Name | Android Red Alert Malware |
| Type | Android Malware |
| Short Description | May perform malicious activities while remaining undetected on Android devices. |
| Symptoms | New files dropped on your pone’s flash memory. |
| Distribution Method | Via applications uploaded on Google Play store, containing malicious JavaScript code. |
| Detection Tool |
See If Your System Has Been Affected by malware
Download
Malware Removal Tool
|
User Experience | Join Our Forum to Discuss Android Red Alert Malware. |

Android Red Alert 2 Malware – Infection
The Android Red Alert 2 malware infection is the type of malware whose primary purpose is to slither onto your android device without you even noticing it. To achieve it’s goal, the Android Red Alert 2 malware may use a variety of techniques, including apps, which while only seem to be legitimate, may contain malicious files, embedded directly among their system files. In addition to this, the malware may also be spread via advertisements and other ad-supported software, whose primary purpose is to deceive the victim into clicking on them, after which the malicious software may be automatically downloaded on their computers. The malicious files, related to this virus are reported to be slithered via different method on victims’ computers and among those the most reports have been received in association with fake updates:
Red Alert report 1
Red Alert report 2

Android Red Alert 2 Virus – Analysis
After the malicious files of the Android Red Alert 2 virus have been downloaded, the malware begins to perform it’s malicious activities on the victim’s PC. The way this happens is by triggering possibly a JavaScript code which may get the malware to obtain administrative permissions over the Android user.
This results in the Android Red Alert malware to begin with the malicious deeds on your computer. The main of those are believed to be:
- Steal passwords of Google Accounts, associated with the infected device.
- Obtain logins for social media and other apps (Facebook, Twitter, etc.)
- Obtain the keystrokes tapped by the victim.
- Take screenshots of the infected device without the victim noticing.
- Open or close apps on the infected device.
- Download other malicious files while remaining unnoticed.
In addition to this, the malware has also been reported by TrendMicro to be able to intercept SMS messages for verification attempts to make it possible for the cyber-criminals to login using your device, but not only this, the Red Alert virus can also block such attempts on your phone, so you can only remain to wonder why you do not receive activation codes for your account. In addition to this, the malware has also been detected to be sold for around $500 on the black market, making it attractive as well as effective.

Remove Android Red Alert 2 from Your Android
For you to remove this malware, the Android Red Alert virus cannot be simply deleted, since it runs multiple different files which may deny you access to various different administrative settings on your device. The Red Alert 2 malware aims to remain persistent on your device and this results in the virus to have strategies that make it to come back on your device, even if you feel convinced you have removed it. What you can do is to follow the instructions provided below.
Preparation before removal of malware.
Before starting the actual removal process, we recommend that you do the following preparation steps.
- Turn off your phone until you know how bad is the virus infection.
- Open these steps on another, safe device.
- Make sure to take out your SIM card, as the virus could corrupt it in some rare cases.
Step 1: Shut Down your phone to win some time
Shutting down your phone can be done by pressing and holding its power button and choosing shut down.
In case the virus does not let you do this, you can also try to remove the battery.
In case your battery is non-removable, you can try to drain it as fast as possible if you still have control over it.
Notes: This gives you time to see how bad the situation is and to be able to take out your SIM card safely, without the numbers in it to be erased. If the virus is on your computer, it is espeically dangerous to keep the sim card there.
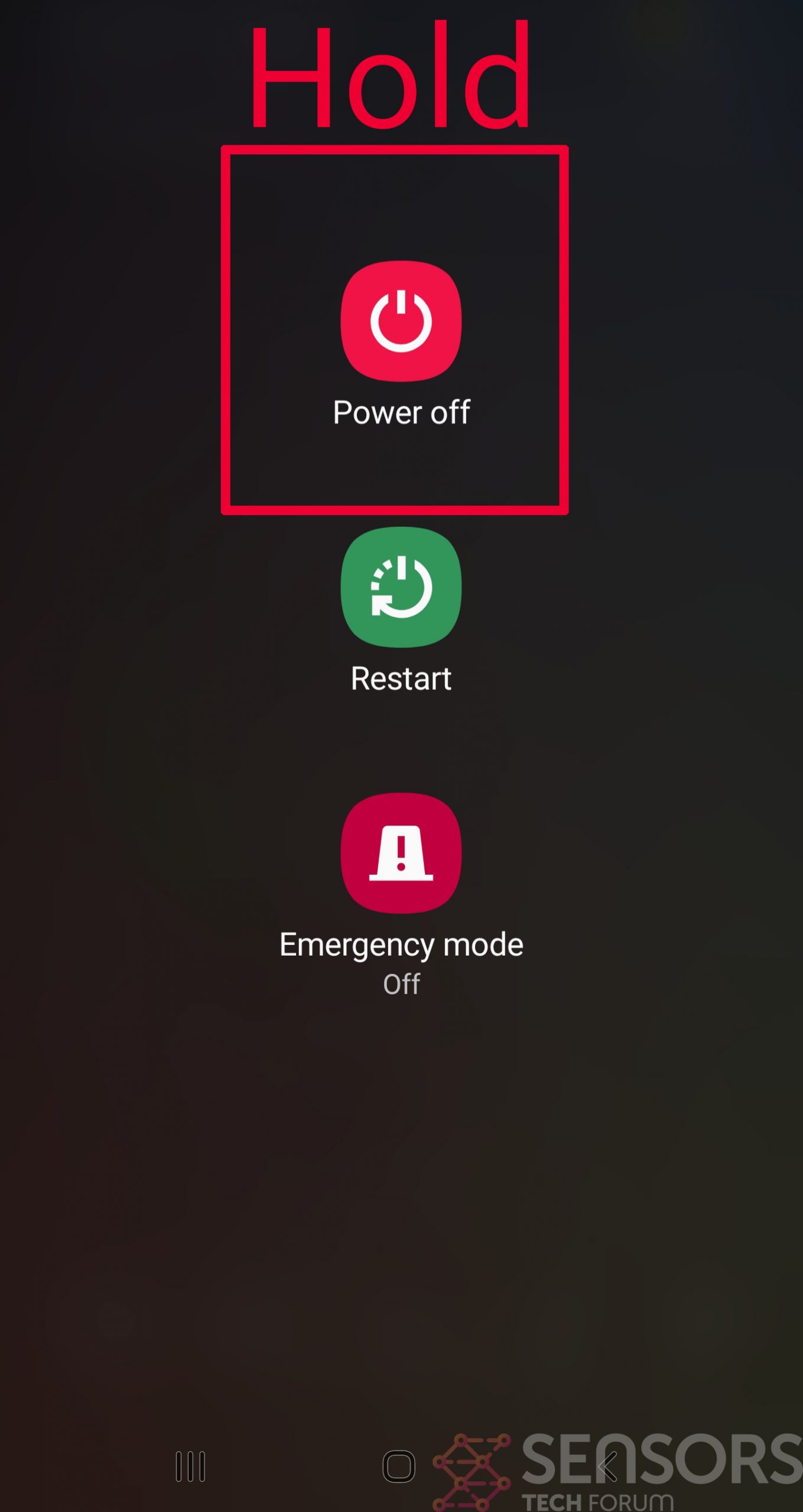
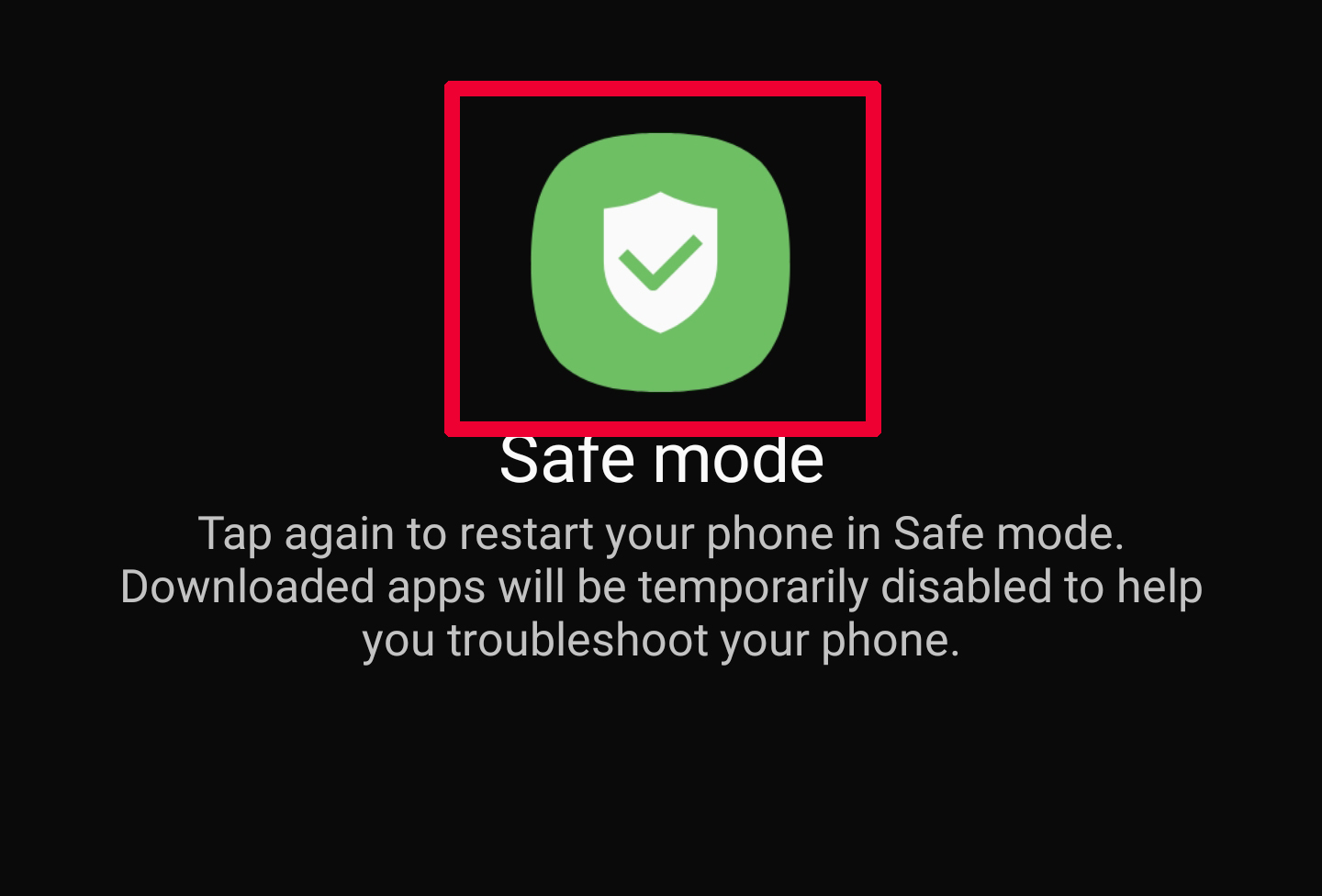
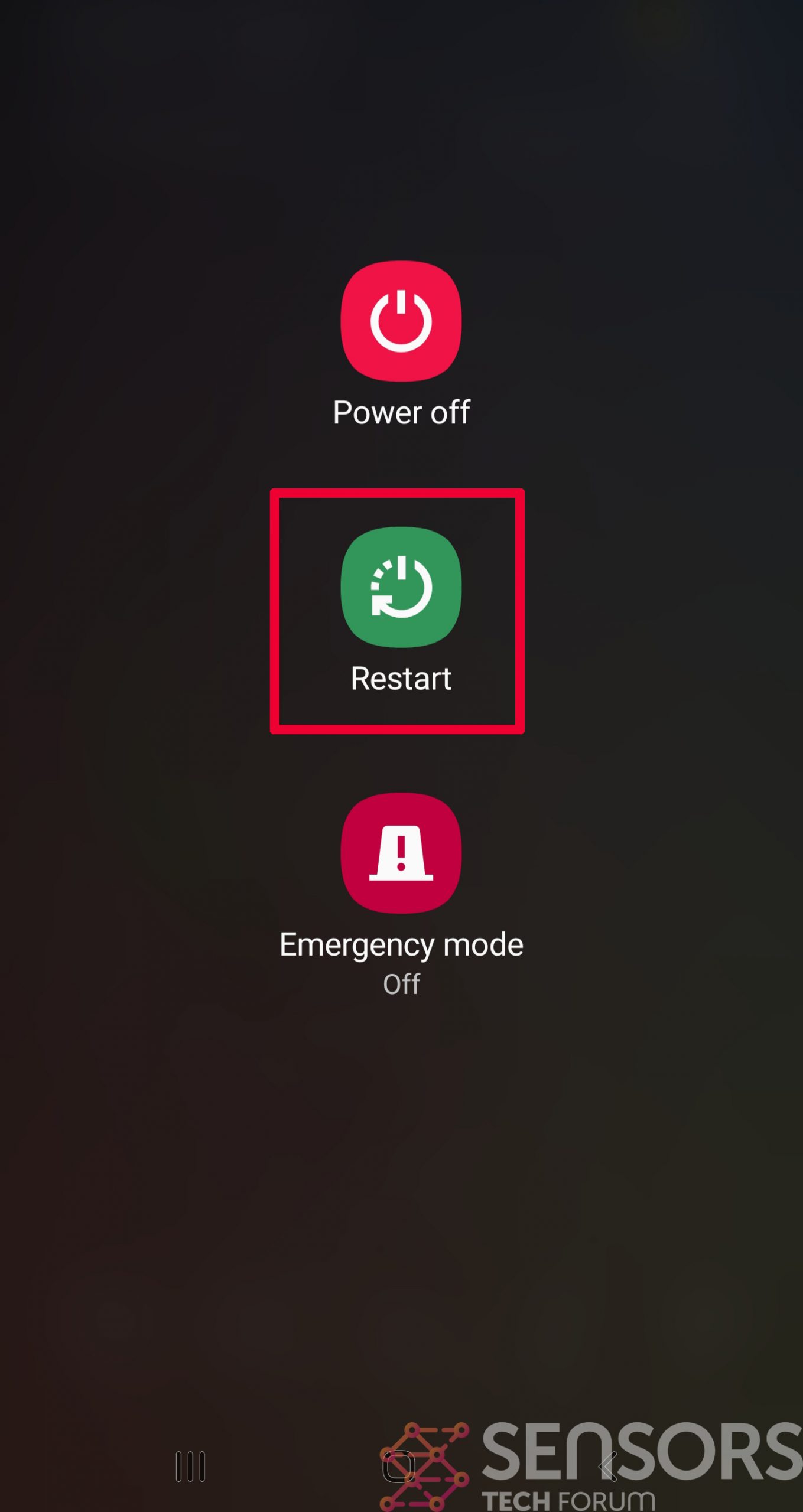
Step 2: Turn on Safe Mode of your Android device.
For most Android devices, switching to Safe Mode is the same. Its done by following these mini-steps:

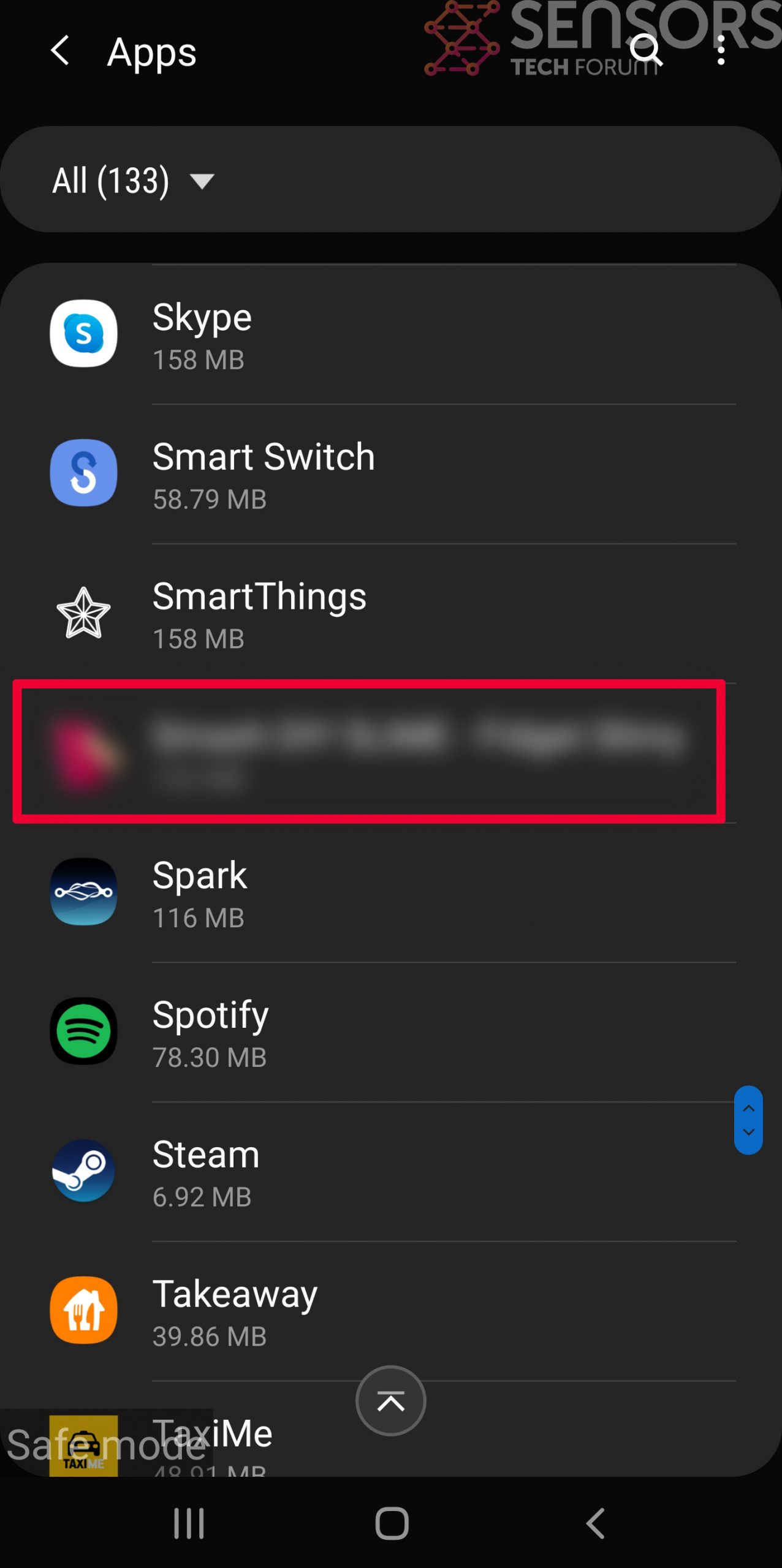
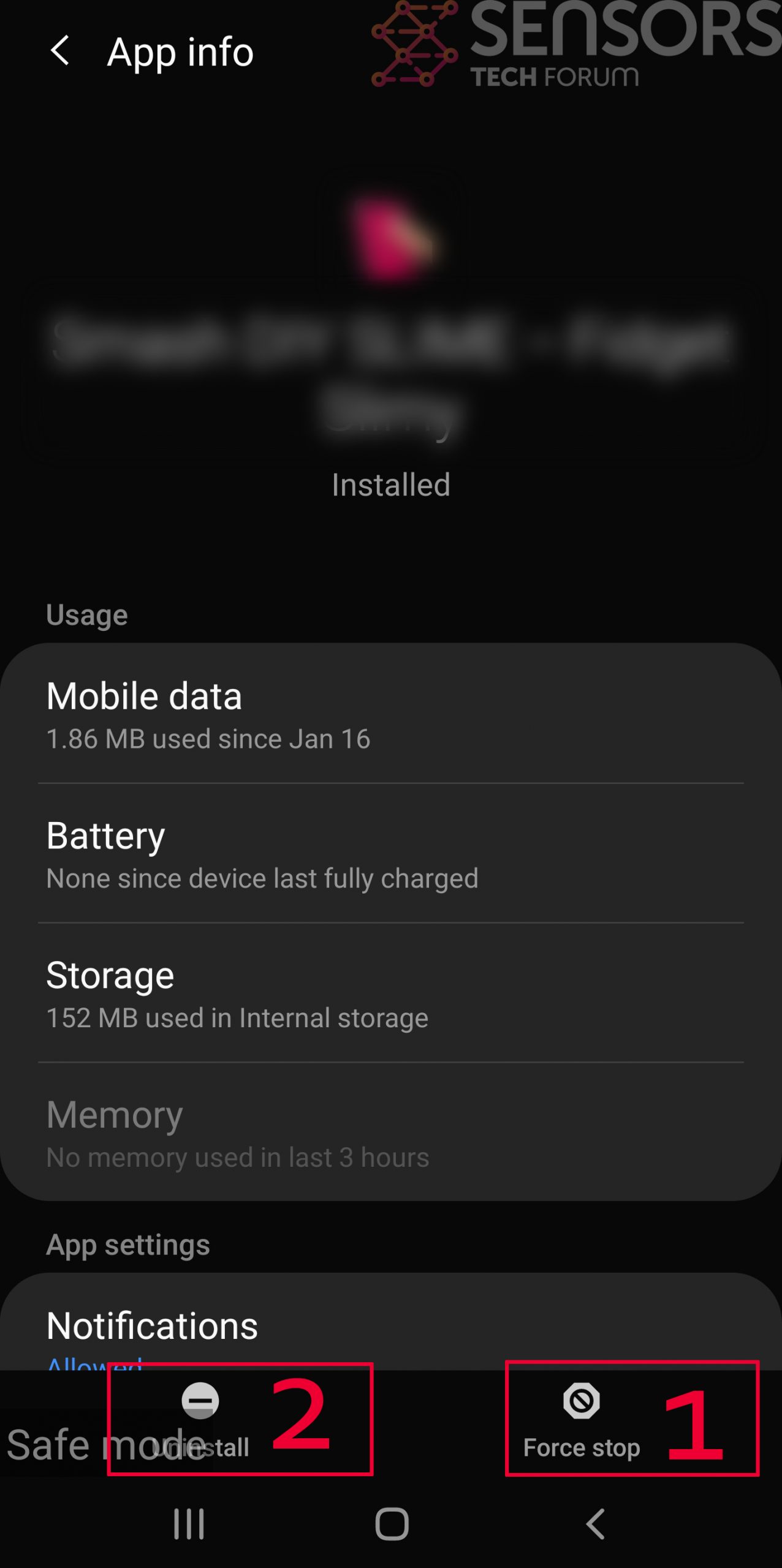
Step 3: Eliminate the App that Your Believe is the Virus
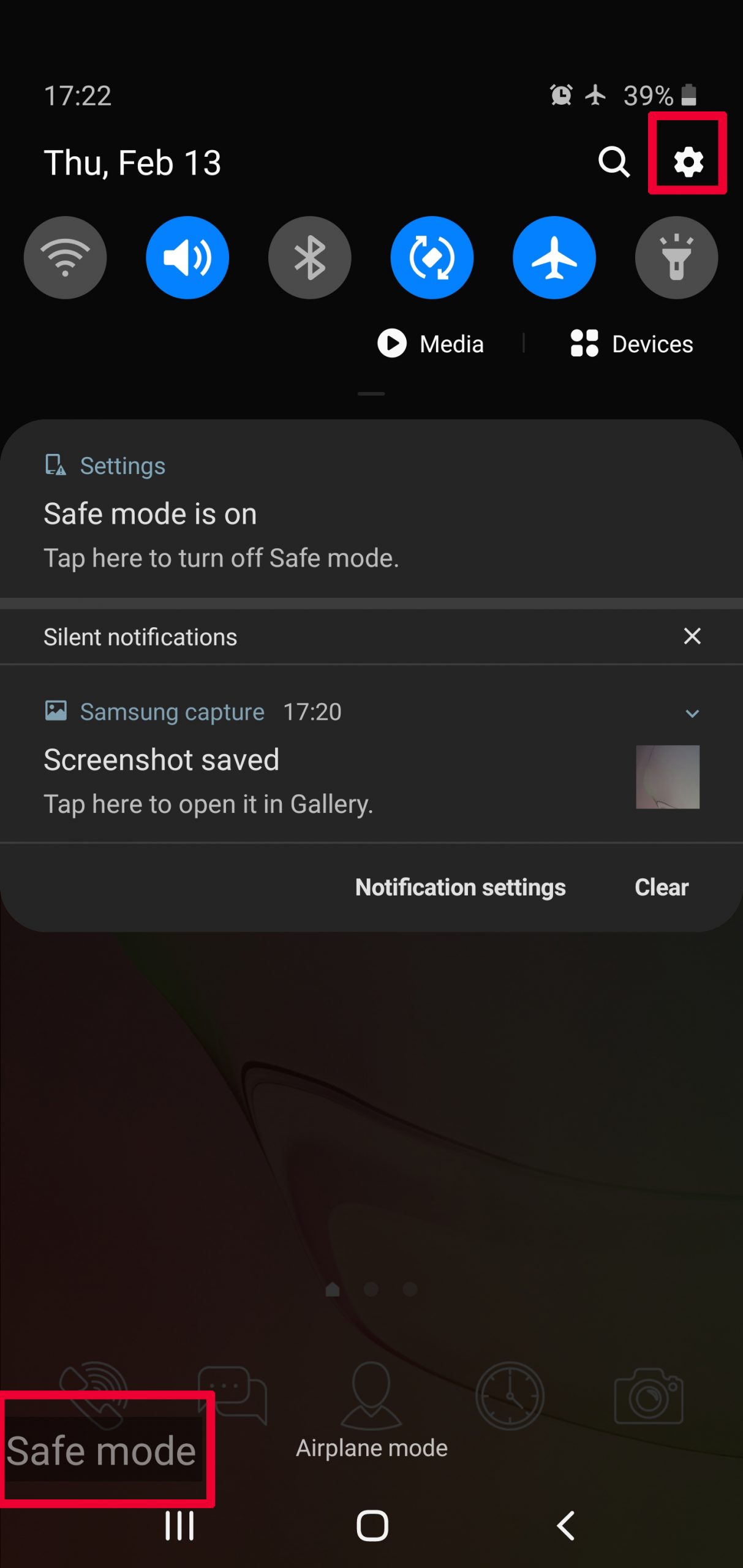
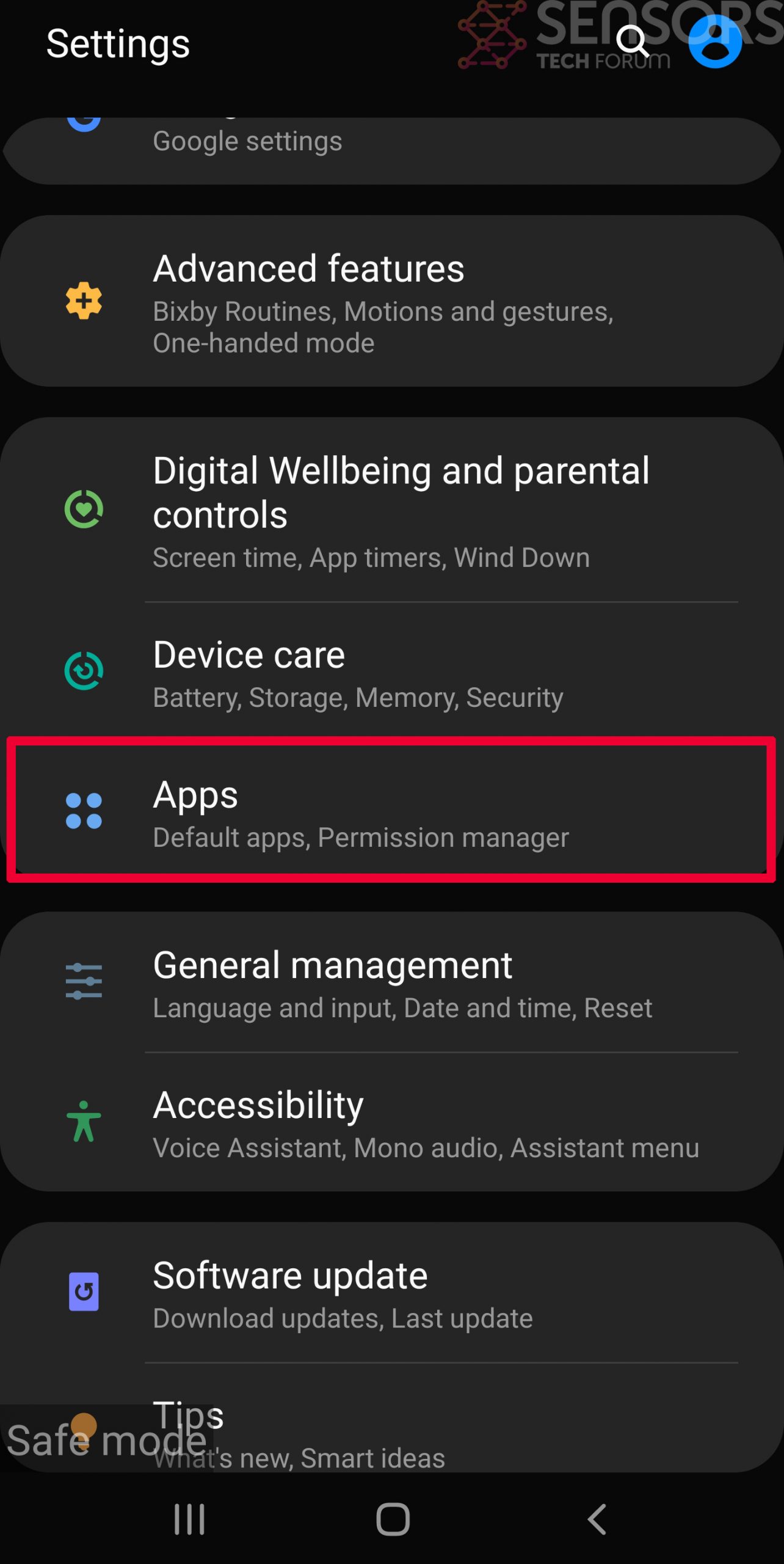
Usually Android viruses get masked in the form of applications. To eliminate apps, follow these mini-steps:
Step 4: Find Hidden Virus Files on Your Android Phone and Remove Them
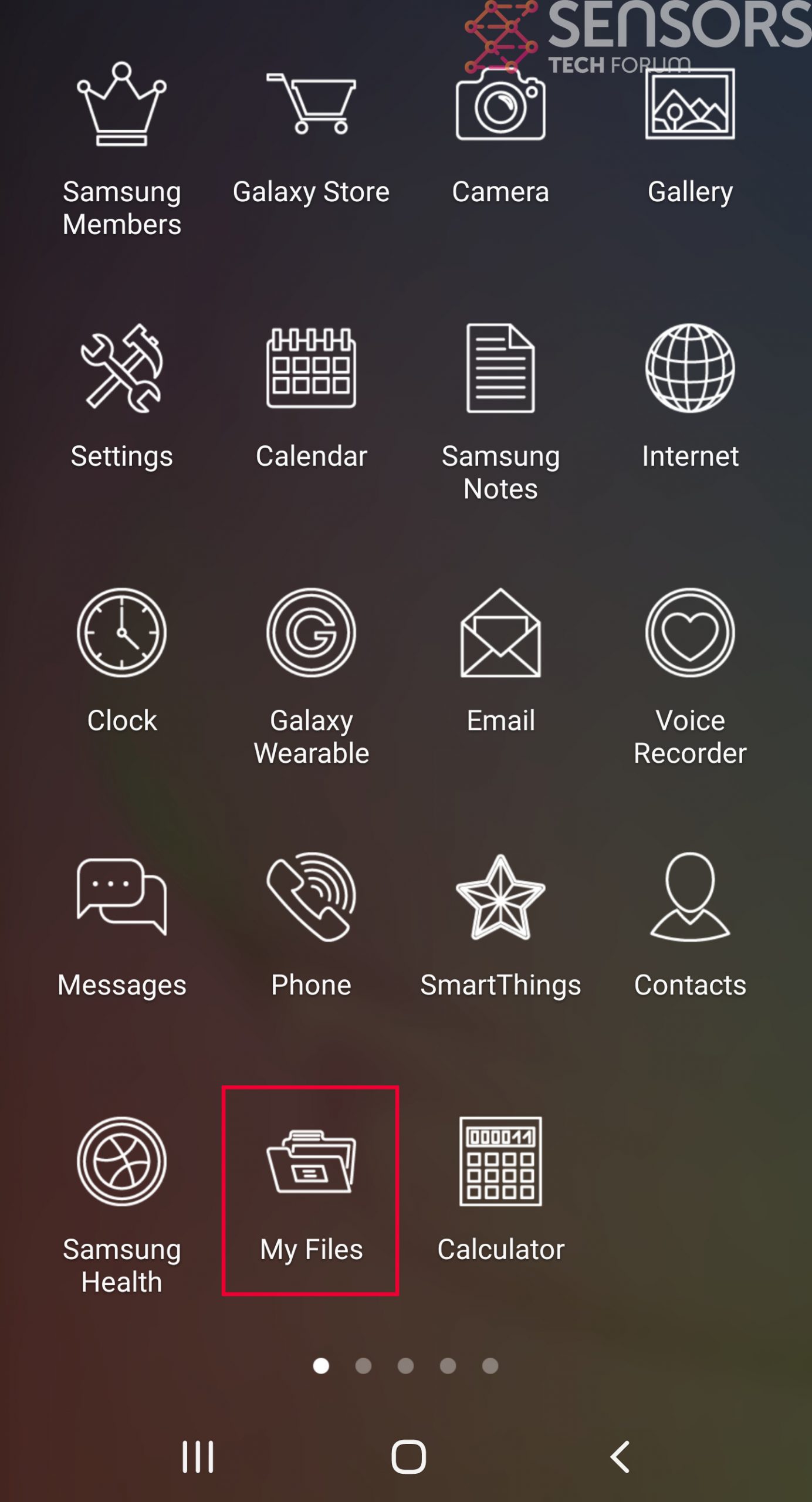
Simply locate the virus and hold-tap on the virus file to delete it.


