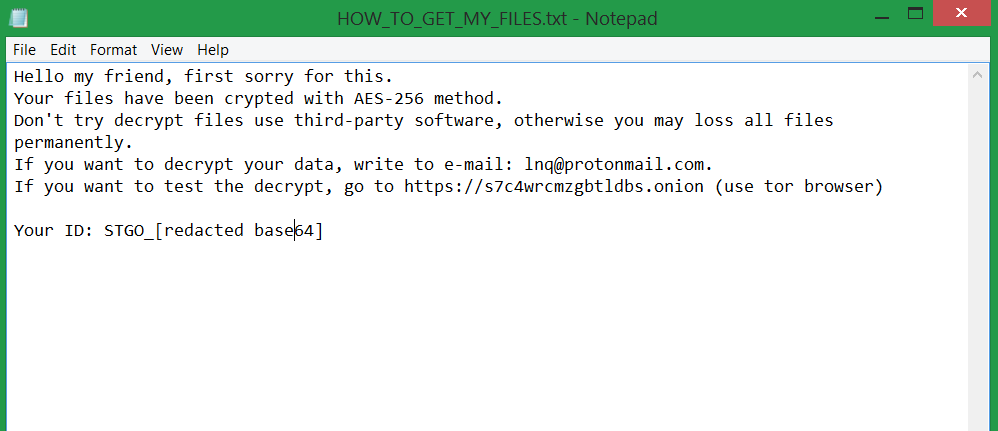
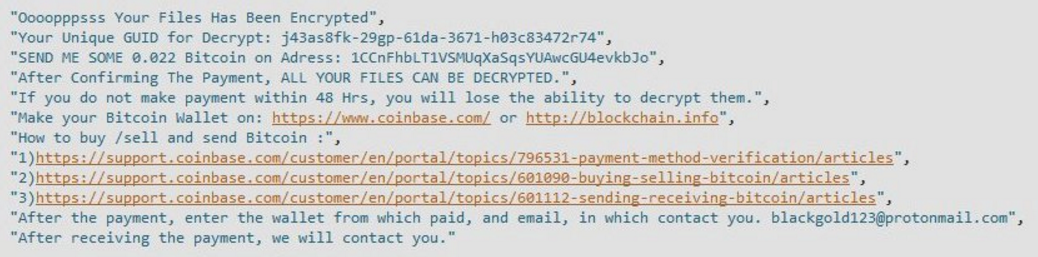
Search.searchleasy.com Redirect Removal
Search.searchleasy.com is the domain of a suspicious browser redirect that may occur due to a potentially unwanted program installed on the PC. It can be classified as a browser hijacker as once it penetrates the system some essential browser settings…