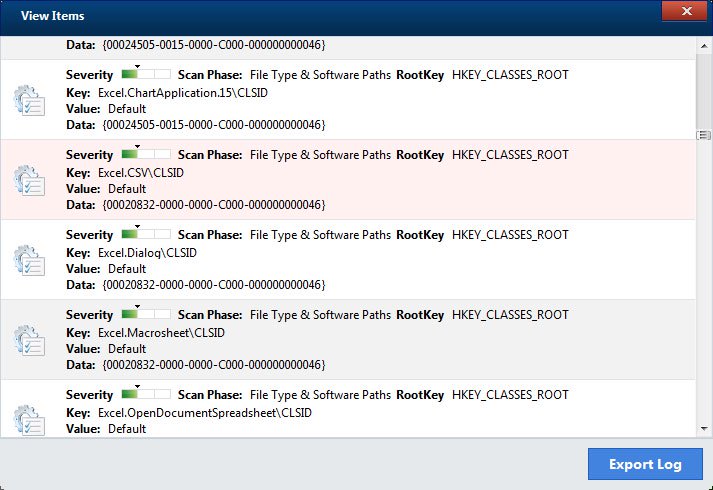
Remove Qbit Clean Pro PUP
This blog post has been created with the main goal to help you detect and remove the Qbit Clean Pro “virus” from your computer. Qbit Clean Pro and as many like to refer to it as a “virus” is actually…

This blog post has been created with the main goal to help you detect and remove the Qbit Clean Pro “virus” from your computer. Qbit Clean Pro and as many like to refer to it as a “virus” is actually…

The Ginp Trojan is an Android malware which has been identified by a security researcher in one of its recent attack campaigns. The samples which are believed to be launched in the attack campaign date to the end of October…

The BokBot Trojan is a dangerous weapon used against computer users worldwide. It infects via vulnerabilities and other common methods. Our article gives an overview of its behavior according to the collected samples and available reports, also it may be…
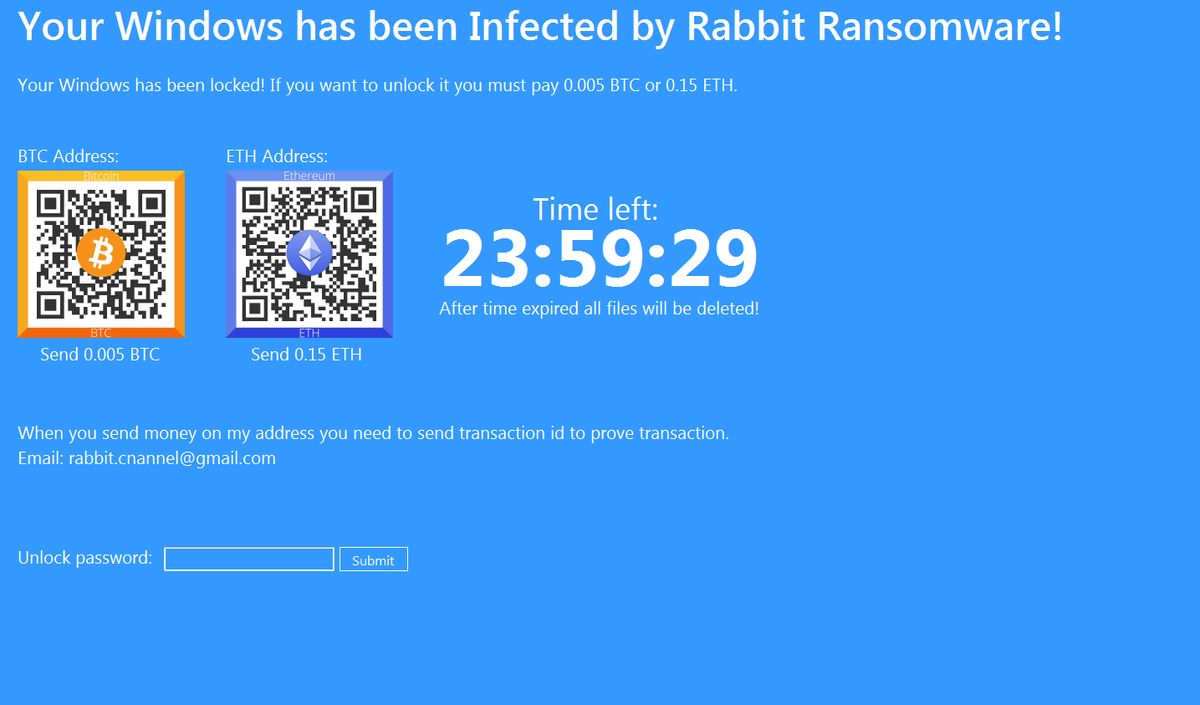
This article will aid you to remove Rabbit Ransomware. Follow the ransomware removal instructions provided at the end of the article. Rabbit Ransomware is one that encrypts your personal data with a strong cipher and demands money as a ransom…
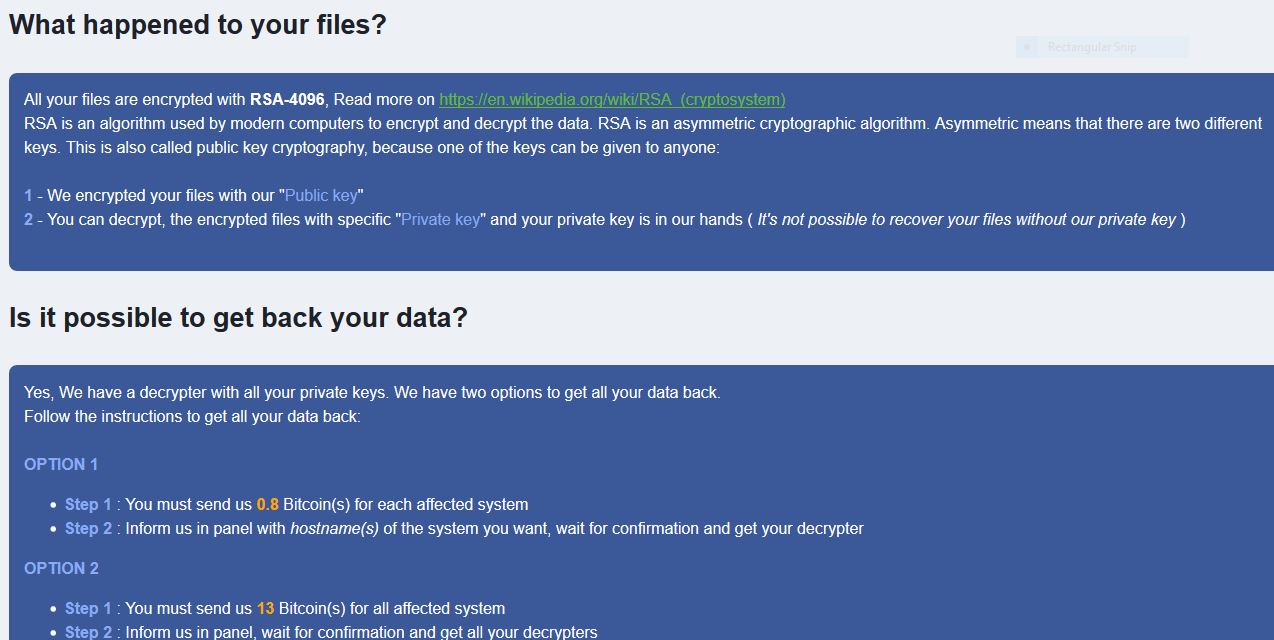
This article will aid you to remove .enc_robbinhood Ransomware. Follow the ransomware removal instructions provided at the end of the article. .enc_robbinhood Ransomware is one that encrypts your data and demands money as a ransom to get it restored. Files…
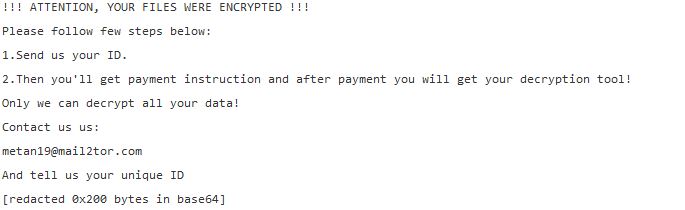
This article will aid you to remove .metan Ransomware. Follow the ransomware removal instructions provided at the end of the article. .metan Ransomware is one that encrypts your data and demands money as a ransom to get it restored. Files…
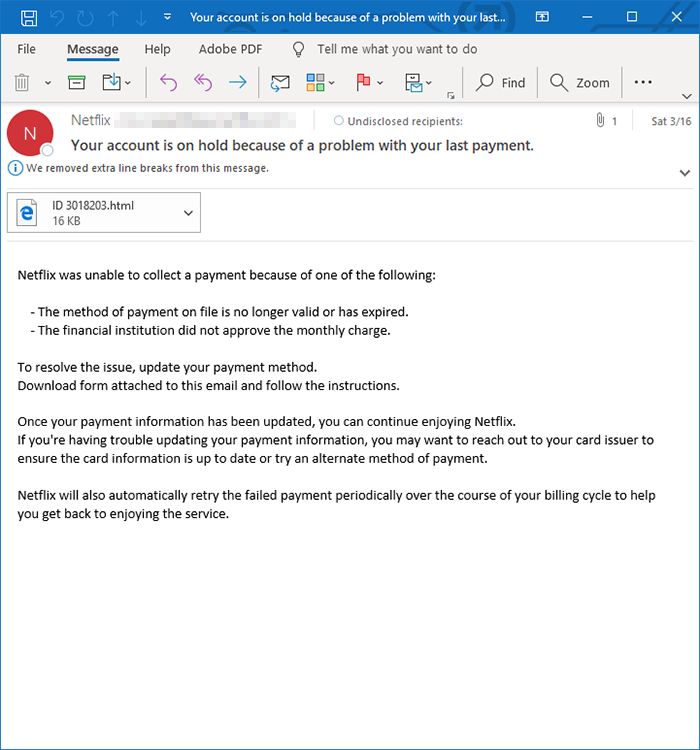
This article has been created to help you understand what is the “Netflix was unable to collect a payment” scam page and what is the “virus” app causing such pages to appear and how to remove it entirely. “Netflix was…

The Tinba Trojan is a dangerous weapon used against computer users worldwide. It infects via vulnerabilities and other common methods. Our article gives an overview of its behavior according to the collected samples and available reports, also it may be…
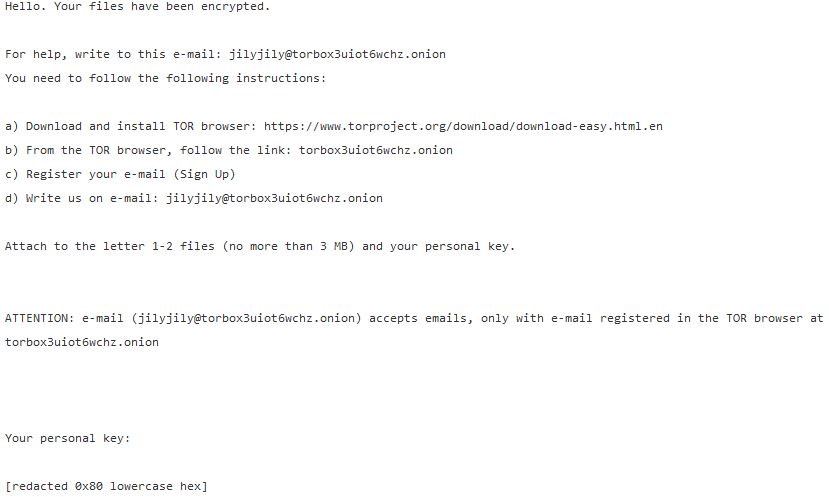
This article will aid you to remove .L1LL Ransomware. Follow the ransomware removal instructions provided at the end of the article. .L1LL Ransomware is one that encrypts your data and demands money as a ransom to get it restored. Files…
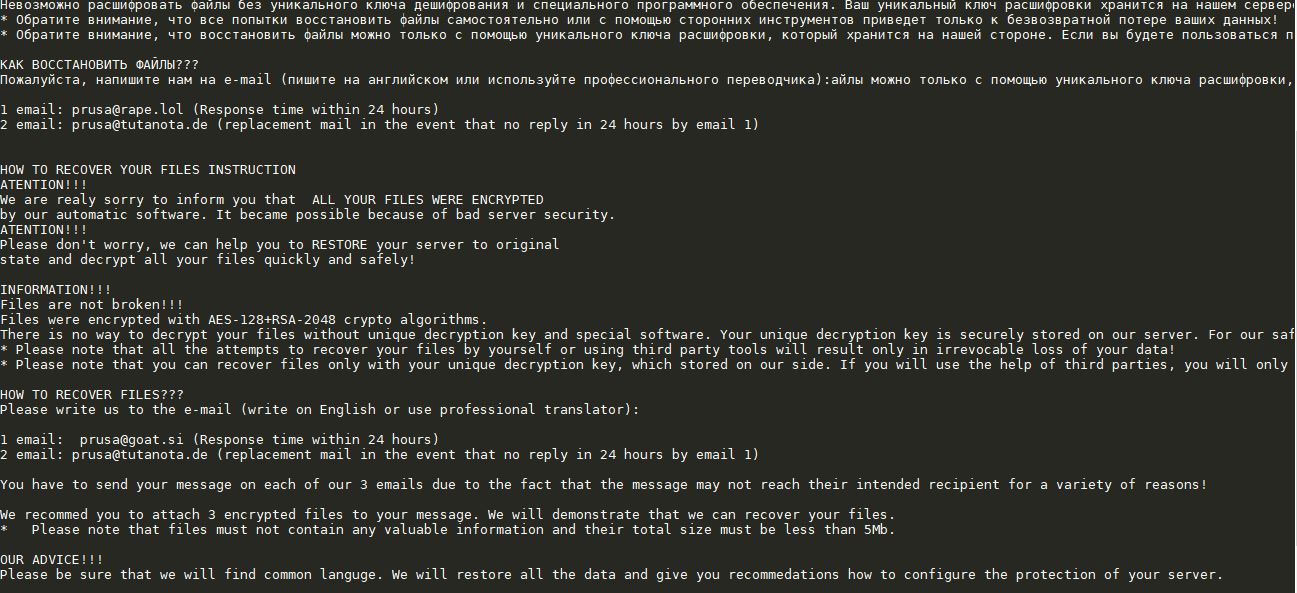
This article will aid you to remove .prus Ransomware. Follow the ransomware removal instructions provided at the end of the article. .prus Ransomware is one that encrypts your data and demands money as a ransom to get it restored. Files…

The Mi_unlock_en.exe is a dangerous weapon used against computer users worldwide. It infects mainly via phishing email messages. Our article gives an overview of its behavior according to the collected samples and available reports, also it may be helpful in…
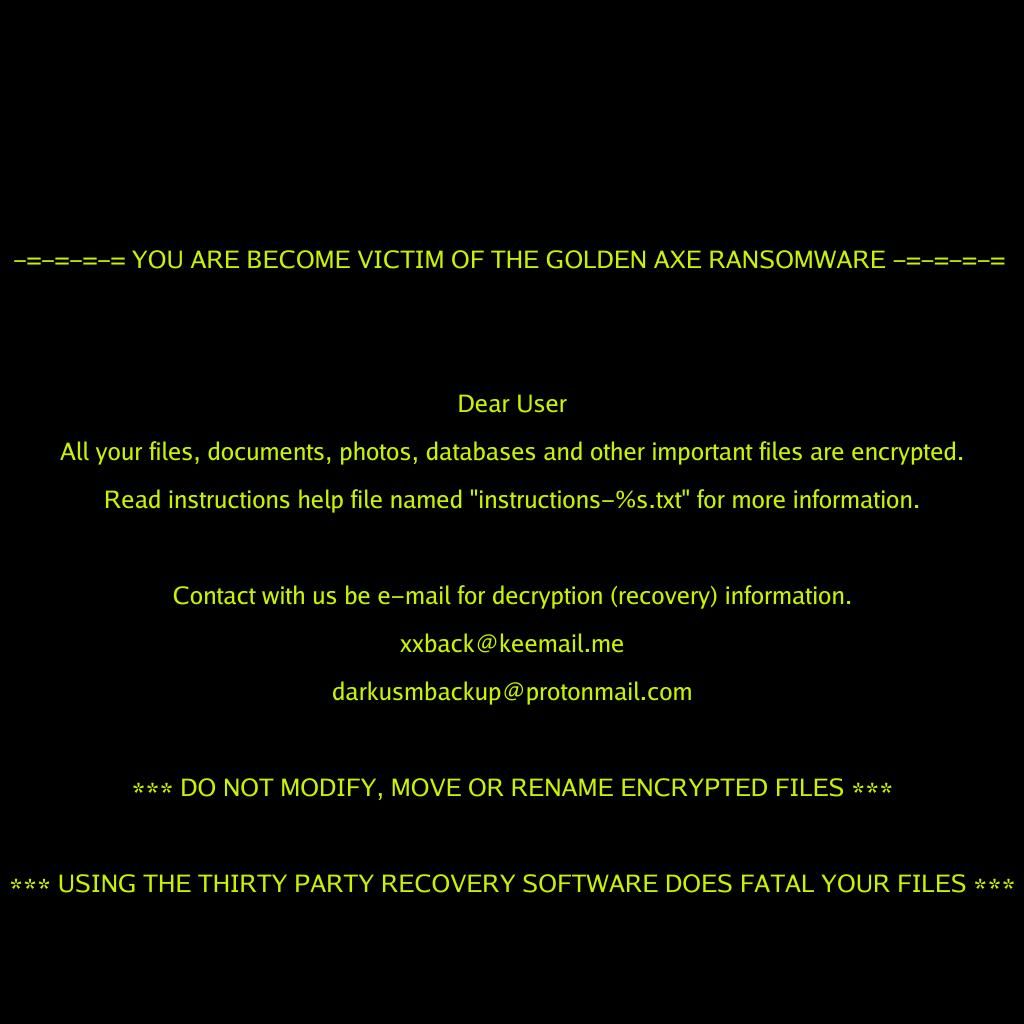
This article will aid you to remove .UIK1J! Ransomware. Follow the ransomware removal instructions provided at the end of the article. .UIK1J! Ransomware is one that encrypts your data and demands money as a ransom to get it restored. Files…
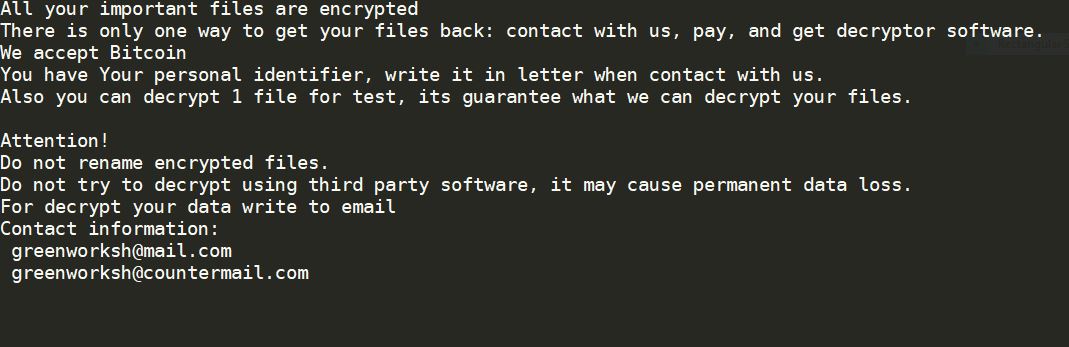
This article will aid you to remove .jamper Ransomware. Follow the ransomware removal instructions provided at the end of the article. .jamper Ransomware is one that encrypts your data and demands money as a ransom to get it restored. Files…
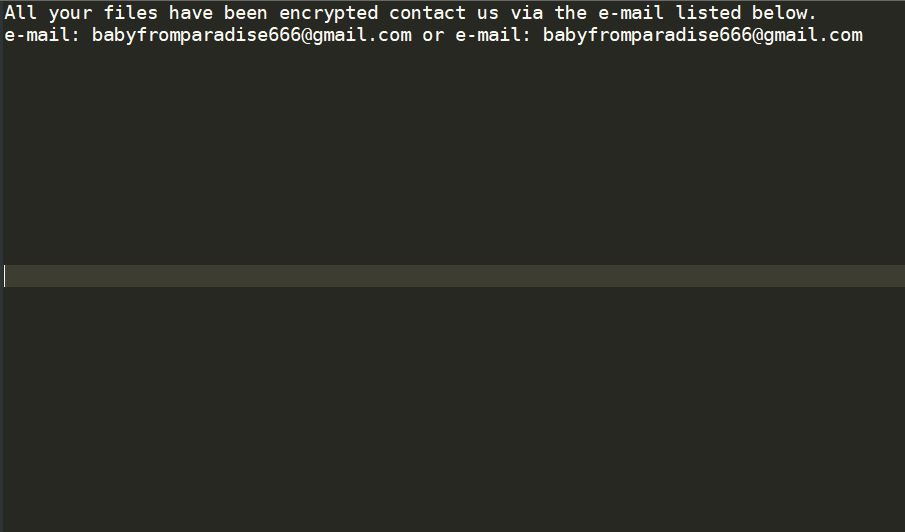
This article will aid you to remove .p3rf0rm4 Ransomware. Follow the ransomware removal instructions provided at the end of the article. .p3rf0rm4 Ransomware is one that encrypts your data and demands money as a ransom to get it restored. Files…
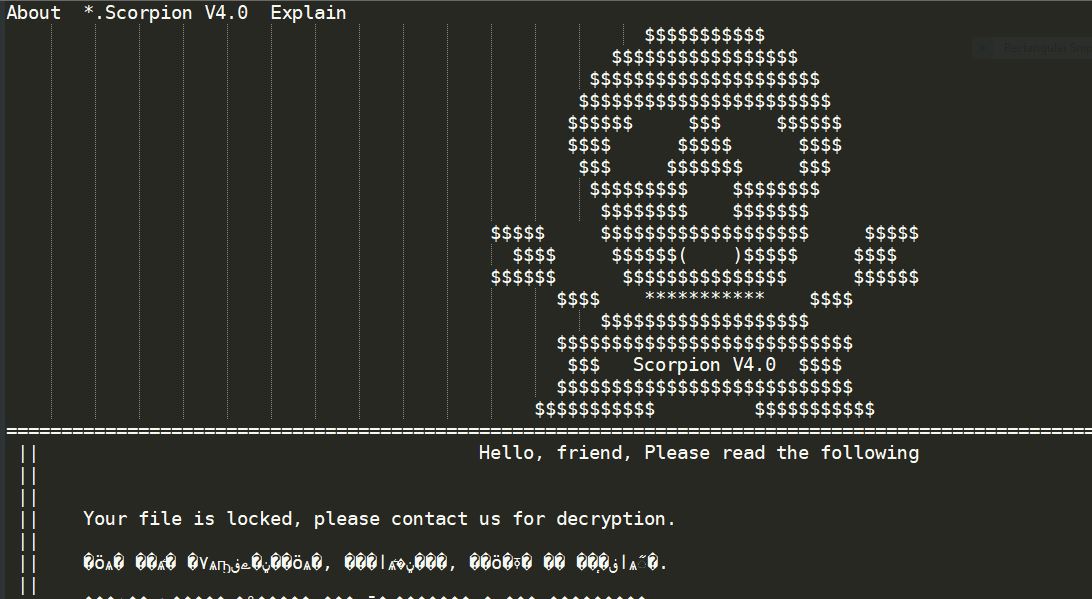
This article will aid you to remove .Scorpion Ransomware. Follow the ransomware removal instructions provided at the end of the article. .Scorpion Ransomware is one that encrypts your data and demands money as a ransom to get it restored. Files…

Update June 2019! What is Driver Fixer? What does Driver Fixer do? Is Driver Fixer safe? Can you trust Driver Fixer? Is Driver Fixer a virus? SIDENOTE: This post was originally published in May 2019. But we gave it an…

The PirateMatryoshka Malware is a dangerous weapon used against computer users worldwide. It infects mainly via The Pirate Bay torrent trackers. Our article gives an overview of its behavior according to the collected samples and available reports, also it may…
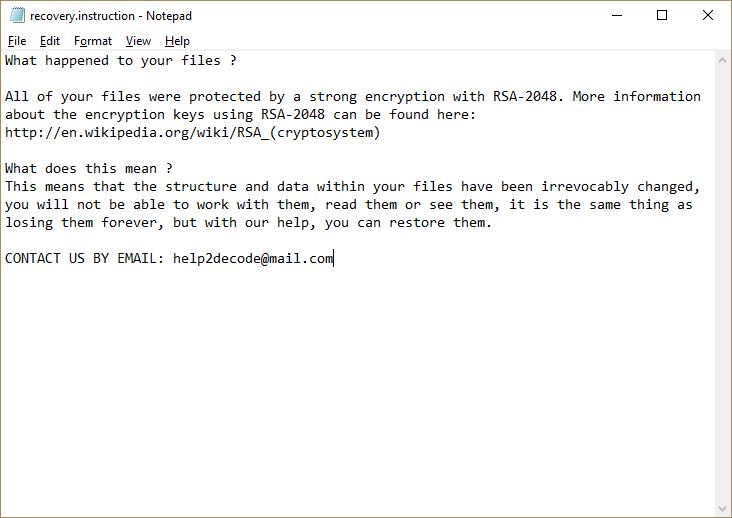
This article will aid you to remove .a800 Ransomware. Follow the ransomware removal instructions provided at the end of the article. .a800 Ransomware is one that encrypts your data and demands money as a ransom to get it restored. Files…

The Belonard Trojan is a dangerous weapon used against computer users worldwide. It infects mainly via Counter Strike in-game client vulnerabilities. Our article gives an overview of its behavior according to the collected samples and available reports, also it may…
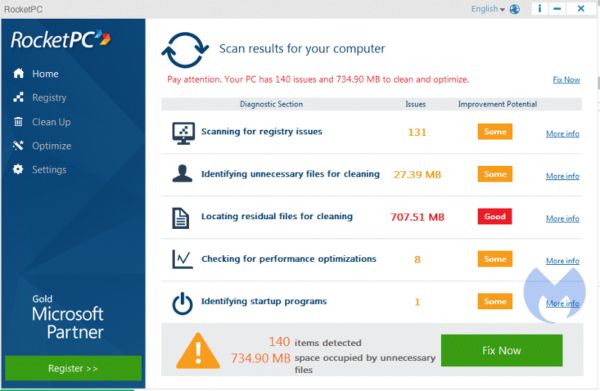
What Is RocketPC Performance Monitor? The RocketPC Performance Monitor is a suspicious, trojanized program targeting computer users worldwide. It infects mainly via phishing email messages. Our article gives an overview of its behavior according to the collected samples and available…