DanaBot Trojan Removal — Restore Your PC From Infections
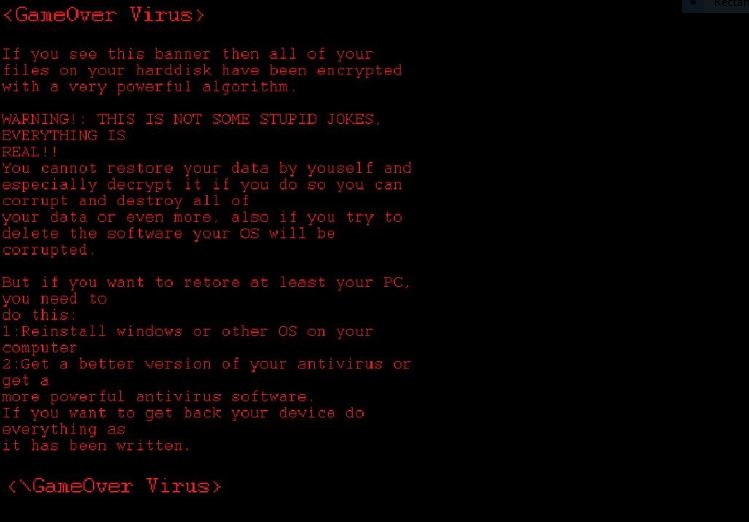
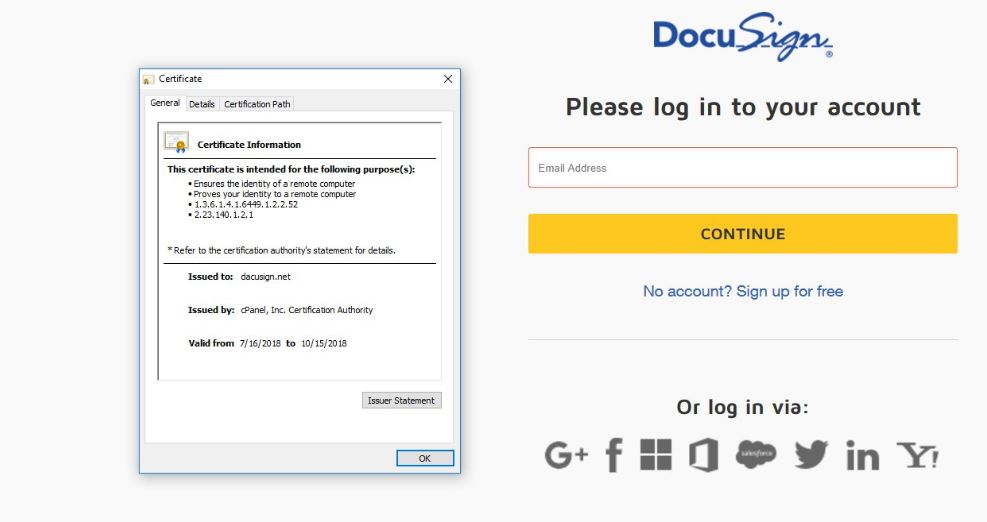
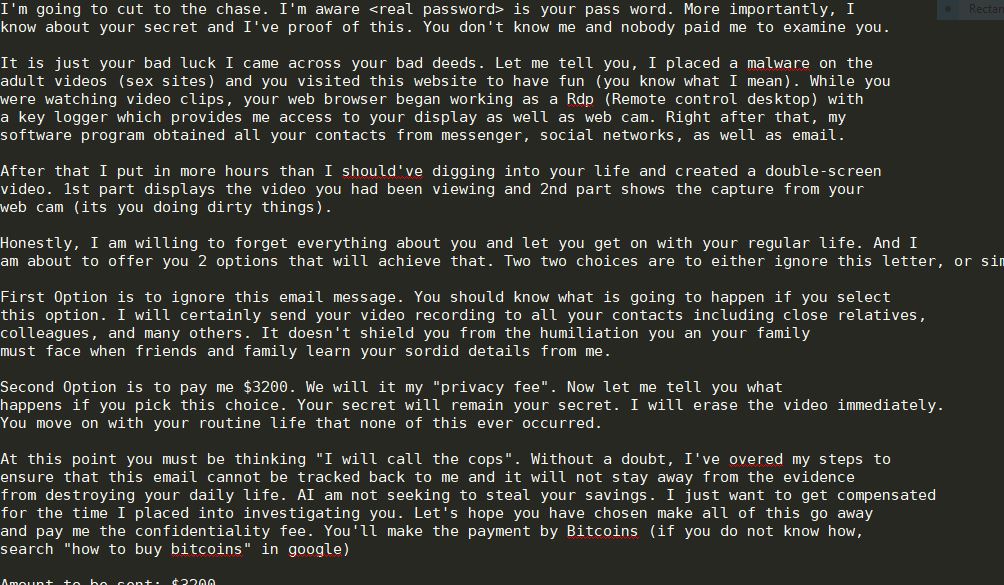
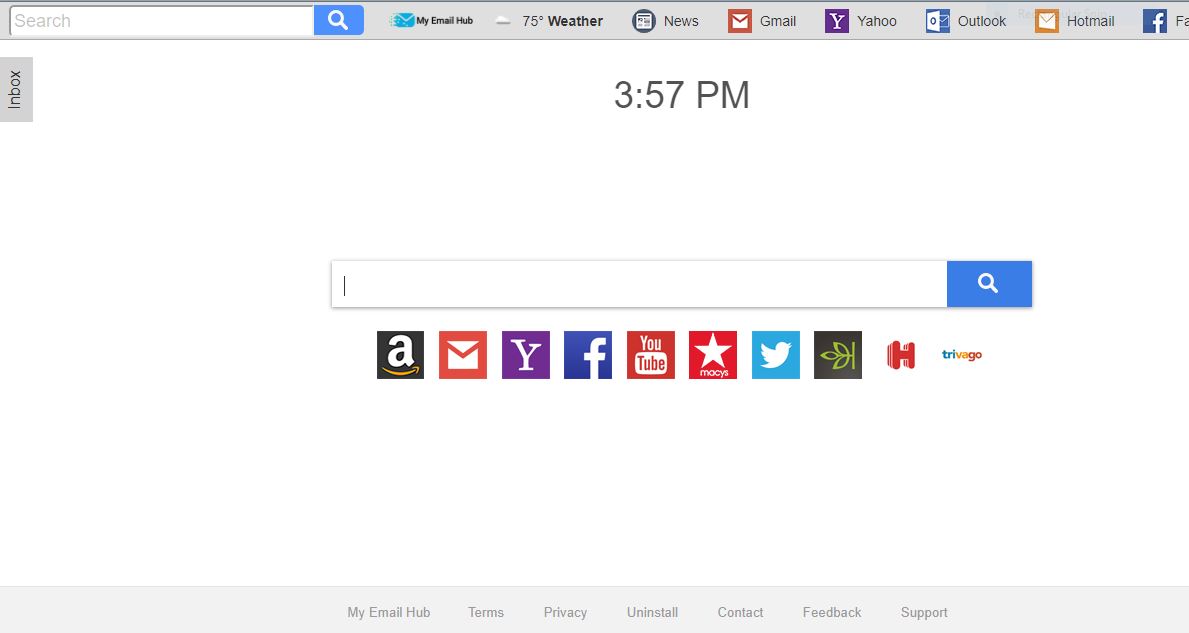
The DanaBot Trojan is a dangerous virus infection that specifically targets online banking users. It can cause many system modifications, spy on the users and also deploy other viruses, including ransomware. Read our complete analysis and removal guide to learn…


![Scarab-Turkish Virus (Scarab Ransomware) – Remove and Restore .[email] Files Scarab-Turkish Virus image ransomware note .[email] extension](https://cdn.sensorstechforum.com/wp-content/uploads/2018/07/Scarab-Turkish-virus-image-sensorstechforum-com.jpg)