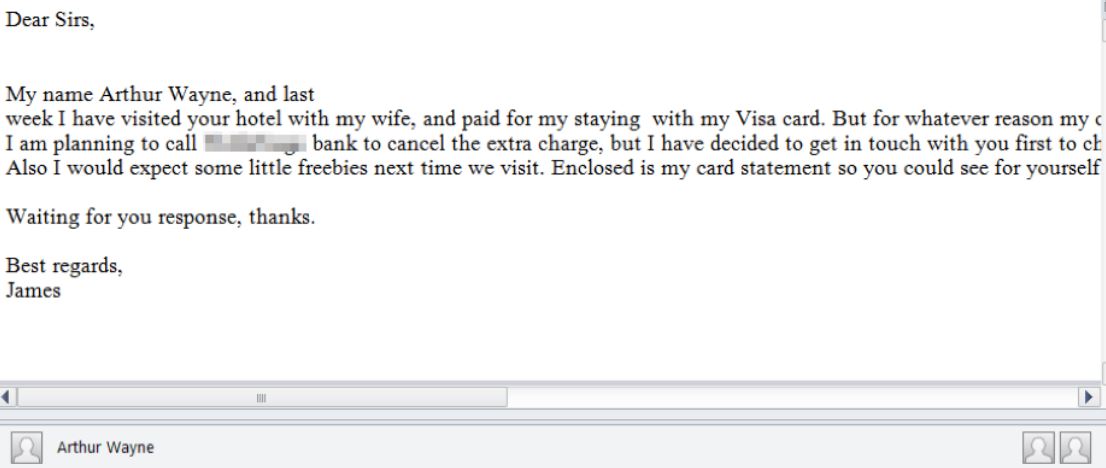
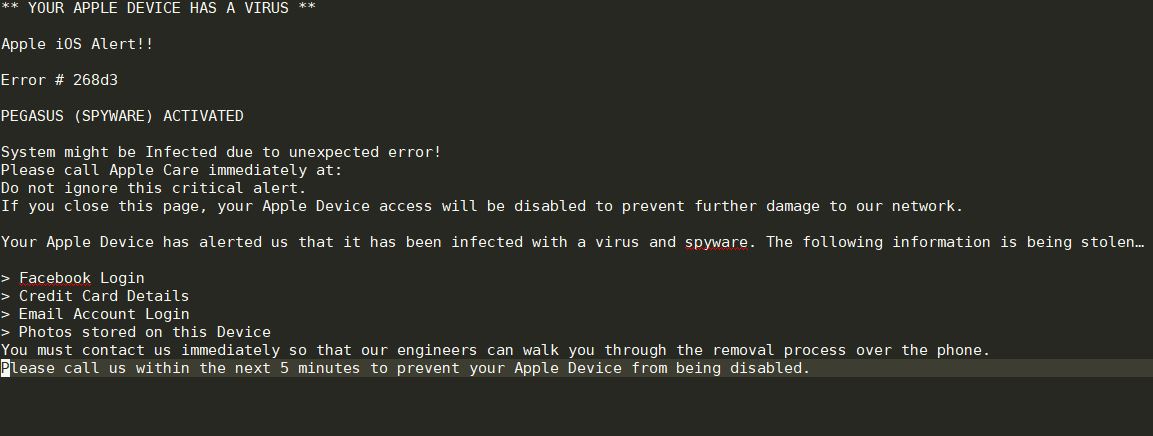
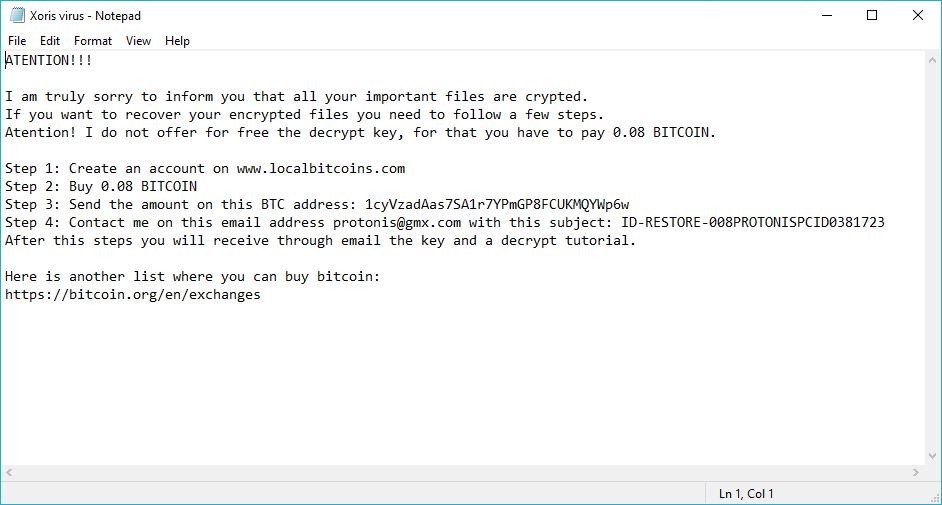
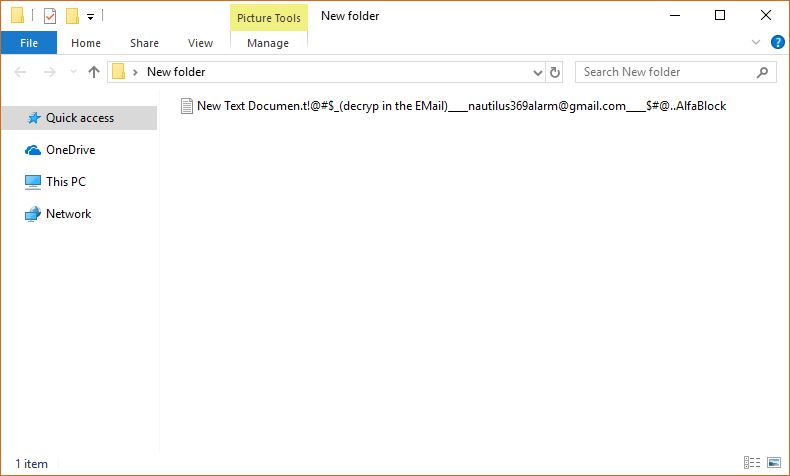
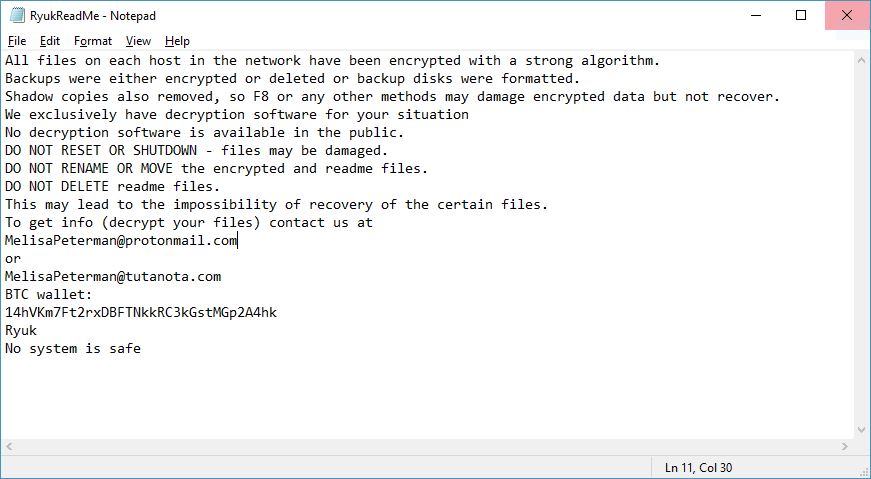
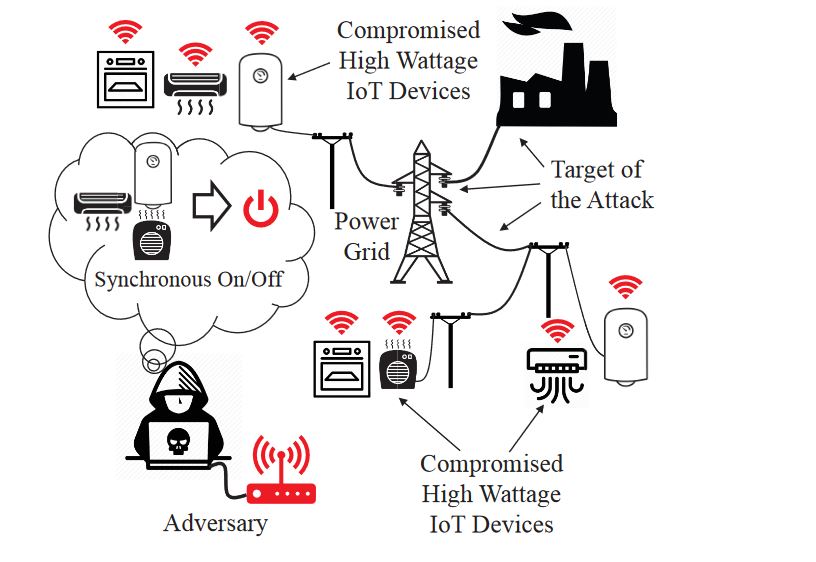
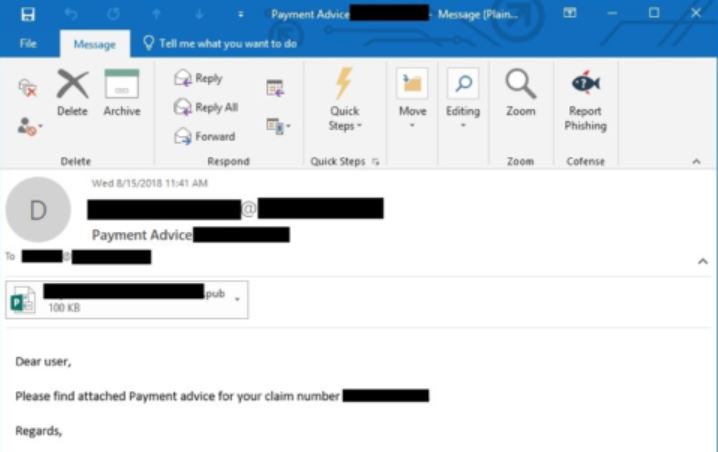
Turla Trojan Removal Instructions — Restore Your Computer From Infections
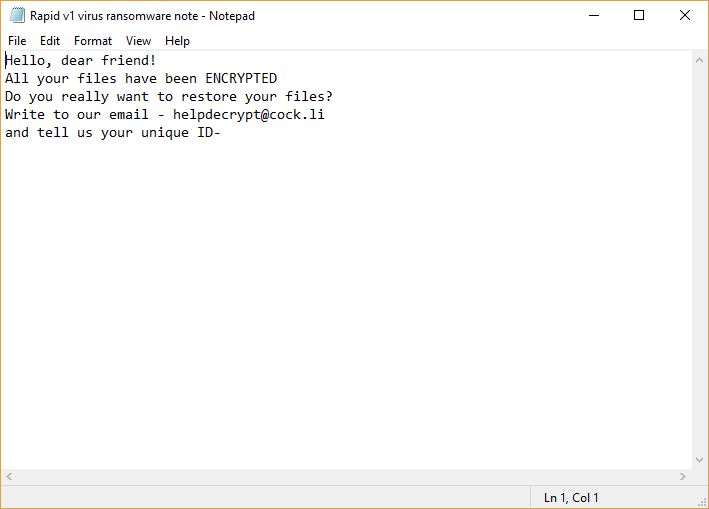
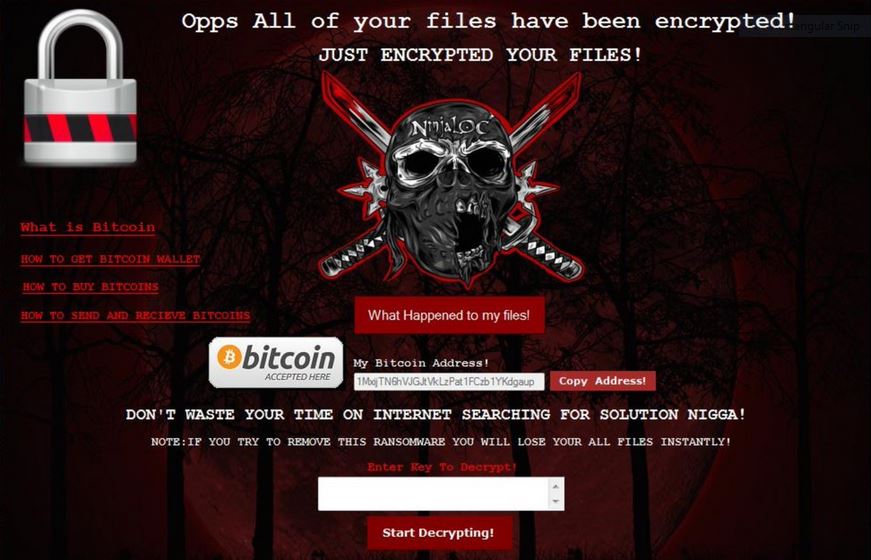
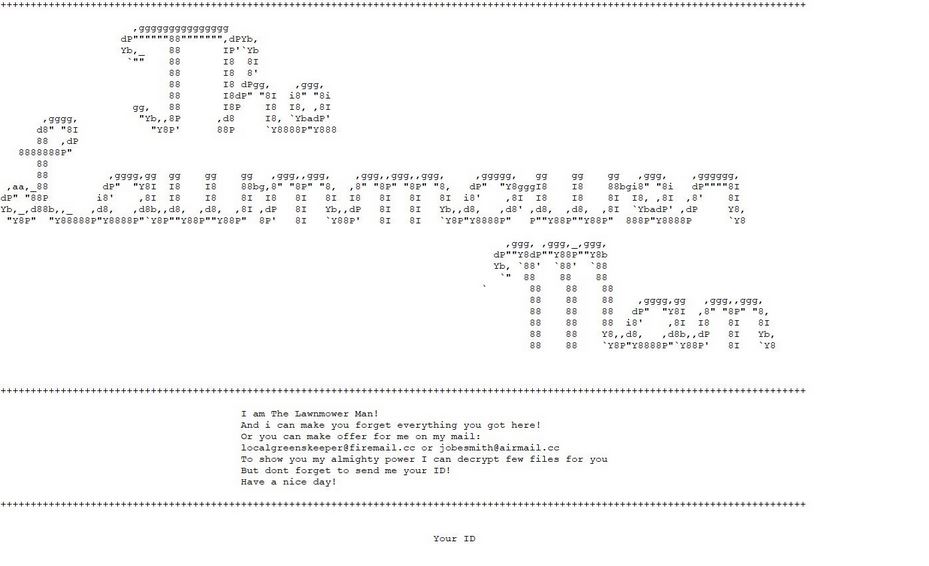
The Turla Trojan attacks are currently infecting users worldwide in an offensive campaign. The captured samples showcase that the threat can cause widespread damage on the compromised hosts. Our article provides an overview of the virus operations and it also…