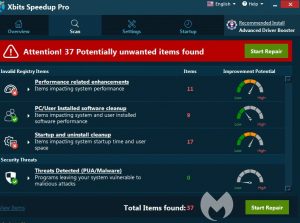
Jeanson J. Ancheta E-mail Scam – Why Did You Receive It?
There is a new email sextortion scam that is extorting users with the pretext that their email accounts were hacked and they have been recorded watching “dirty videos”. In other words, a new blackmail scam is circling the web, this…