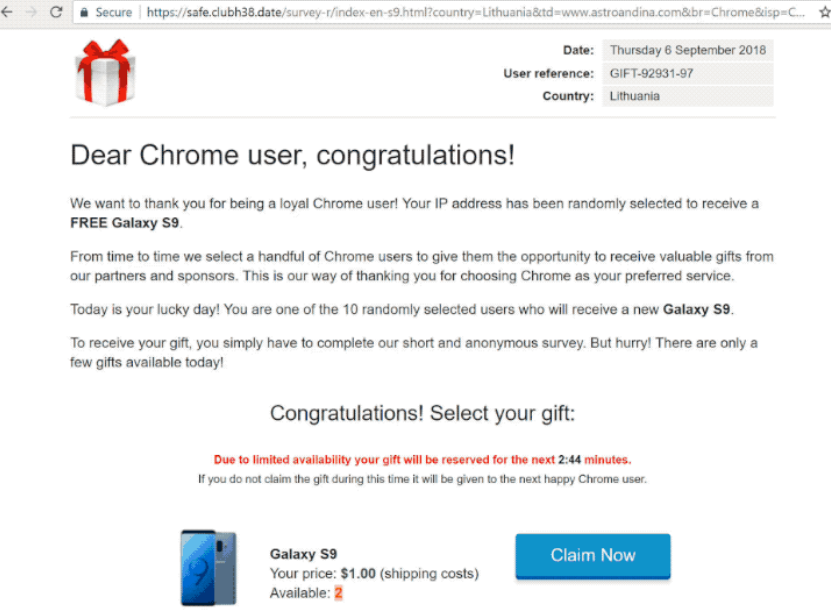
Fofy Virus Redirect – How to Remove It
Fofy redirect (fofy.com) is a hoax website that might affect commonly used and credible internet browsers. Due to its suspicious activities, it can be classified as a regular internet browser hijacker that aims to collect information from all individuals who…