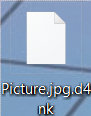
.D4nk File Virus Remove and Restore Encrypted Files
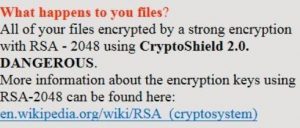
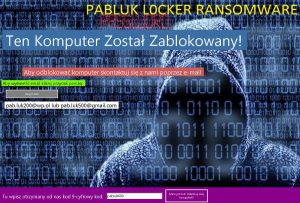
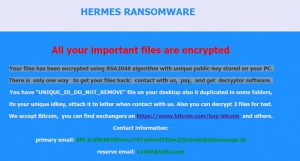
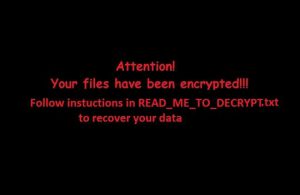
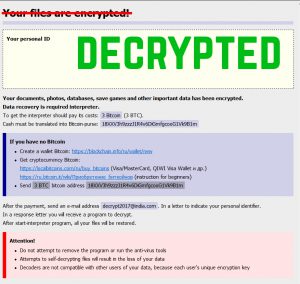
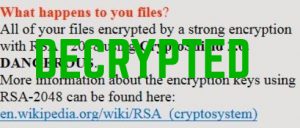
Article created to help you remove PyL33T ransomware infection from your computer and restore files encrypted with the .d4nk file extension embedded in them. A ransomware infection, called PyL33T ransomware has been reported by malware researchers to be causing infections…












![[KASISKI] File Virus (Restore Files)](https://cdn.sensorstechforum.com/wp-content/uploads/2017/02/ransomware-file-encryption-malware-kasiski-sensorstechforum.jpg)