Archive Poster Miner Virus — How to Detect and Remove It from Your PC
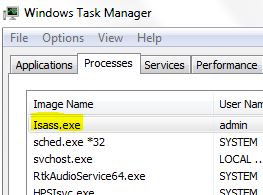
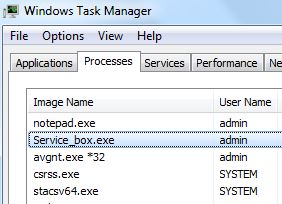
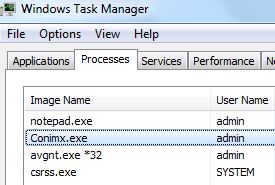
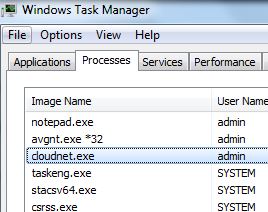
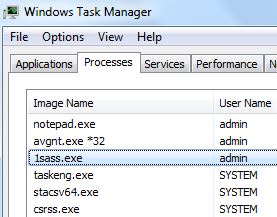
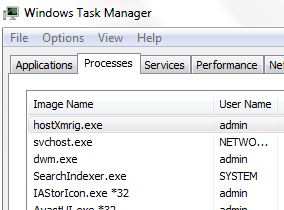
This article has been written in order to help you by explaining more about what is Archive Poster Miner Virus malware process plus how to detect and remove Archive Poster Miner Virus from your computer completely. Independent security experts warned…