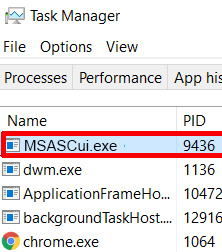
MSASCui.exe Monero Miner Virus – How to Detect and Remove It
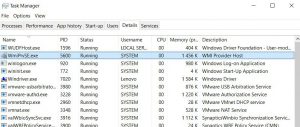
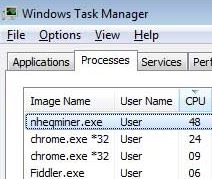
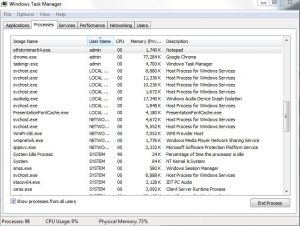
Article created to show you what is the MSASCui.exe process, how to detect the MSASCui.exe miner malware and how to completely remove it from your computer system. New miner malware which uses the same name of the original Microsoft Security…