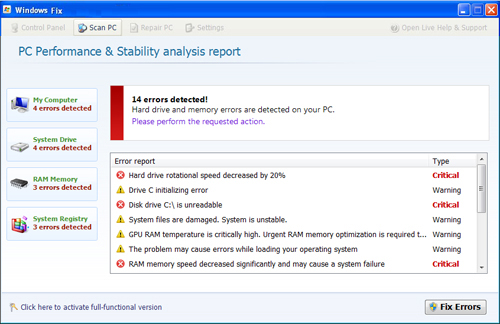
Trojan.Agent.DED Removal Manual
Several security solutions detect Trojan.Agent.DED as a harmful Trojan and recommend its immediate removal. Trojan.Agent.DED allow cybercriminals gain remote access to your machine and perform malicious actions without being detected. Trojan.Agent.DED can be permanently deleted with a trusted anti-malware tool.…