This blog post has been created to explain what is driver.exe cryptocurrency miner Trojan and show how to remove it from your computer plus protect your PC against future infections as well.
This blog post has been created to explain what is driver.exe cryptocurrency miner Trojan and show how to remove it from your computer plus protect your PC against future infections as well.
A new cryptocurrency miner malware, using the process driver.exe has been detected by malware researchers. The malware is known to be one of the most dangerous out there, since it uses the resources of the computers that are infected by it in order to generate cryptocurrency tokens at the benefit of the cyber-criminal who is behind the malware. This may result in multiple negative consequences for victims, including general slowing down of their computers plus their system may crash and freeze at times. In the event that your computer has been infected by the driver.exe crypto miner malware, it is strongly advisable to read this article and learn how to remove it from your PC plus how to protect yourself against future infections.

Threat Summary
| Name | driver.exe malware |
| Type | CryptoCurrency Miner Malware |
| Short Description | Aims to mine for different cryptocurrencies on the victim’s computer after which may begin to |
| Symptoms | The driver.exe miner may begin to slow down your computer by using over 90% of both your CPU and GPU. This may result in your cooling fans to work at higher speeds. |
| Distribution Method | Via bundled installers, fake setups or via other PUP that has already been installed on your PC. |
| Detection Tool |
See If Your System Has Been Affected by malware
Download
Malware Removal Tool
|
User Experience | Join Our Forum to Discuss driver.exe malware. |

Driver.exe Miner Virus – Distribution Methods
Fort this malware to be widespread, various strategies may be undertaken by the cyber-criminals who are behind it. They may include it as an e-mail attachment which pretends to be a legitimate type of document. Such types of files often pretend to be legitimate, such as:
- Invoices.
- Receipts for orders the victim hasn’t made.
- Order confirmation files.
- Files related to an undelivered order.
Such social engineering techniques are often used by hackers to trick victims into opening the malicious files of the malware and hence become infected. If it comes by an attachment, the file may not be directly uploaded as e-mail providers often scan for such files. Instead, most malicious files are often archived in Microsoft Office documents, that aim to obfuscate them from their malicious nature. Some files may even be fake Microsoft Office documents that contain malicious macros and can infect your computer by simply getting you to open them.
Besides this method of infection, there may also be other methods that may cause an infection. They are the passive methods and they often involve suspicious sites. Some lazier cyber-crooks prefer them as they only have to upload the file once on the site and all the victim has to do is search for it. Such fake files may be:
- Fake setups of programs or games.
- Fraudulent key generators.
- Fake cracks for games.
- Pretending-to-be patch-fixes for software or games.
- Fake software activators.

Driver.exe Malware – Malicious Activity
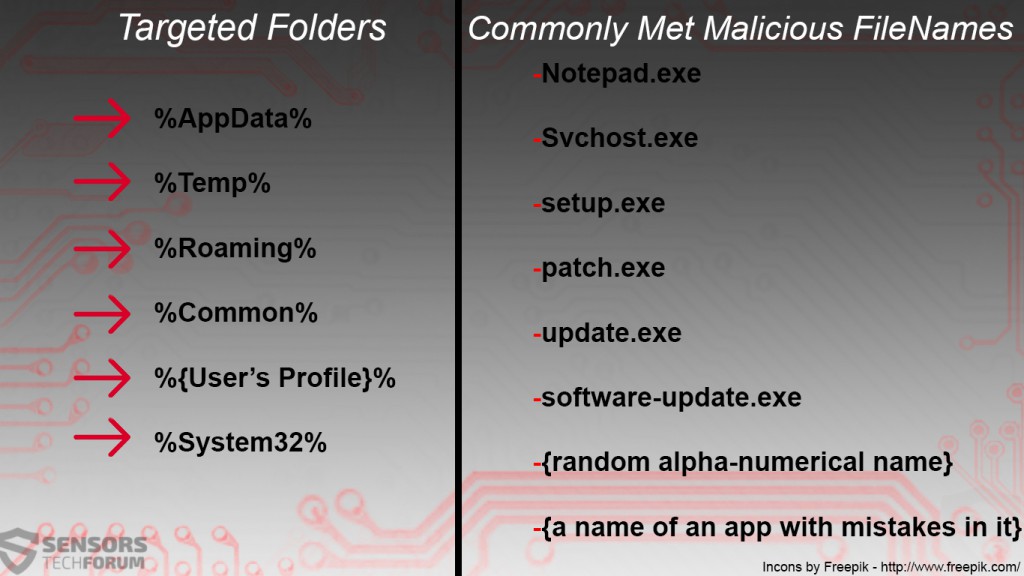
Once an infection by this malware takes place on your computer system, you may immediately notice it, since the infection process triggers the main files of the virus, including driver.exe process. While pretending to be some sort of a driver-related process, this malware may begin to drop it’s malicious files on your computer. The malicious files may be more than one and may exist in the following Windows folders under different names:
After the malicious files are dropped on your computer the virus may create mutexes and execute functions of it’s malicious files that may result in some system files of your operating system to be modified. This is done with the purpose of the virus becoming able to run as an administrator the malicious drive.exe process. The only purpose of this is for the process to connect your computer to a cryptocurrency mining pool. Such pool is basically many miners that join their power together in order to begin generating cryptocurrencies by calculating and assembling hashes. The more hashing power is connected to the wallet of the cyber-criminal who has infected your PC with driver.exe, the more cryptocurrency tokens he or she will obtain for a fixed period of time. This is why most cyber-crooks who are behind miner viruses, like the driver.exe one often aim to infect a lot of people for short periods of time.
In addition to it’s malicious activity as a miner, the driver.exe virus may also perform other unwanted activities on your computers system, since it’s malware. Just like any other Trojan horse, this virus may:
- Steal files from your PC.
- Download and install other malware on it.
- Make sure that it remains on your computer undetected and active, even if you delete some of it’s files.
- Update itself to remain hidden.
- Log your keystrokes.
- Steal passwords from your computer.

Remove Driver.exe Miner Virus and Protect Your PC
Q: How Do I Remove Driver.exe and How Do I Protect Myself In the Future?
A: In order to remove the driver.exe miner, you should first stop the malicious processes of the malware by entering Windows Task Manager and stopping the malicious task by right-clicking on the driver.exe process and clicking on End Process or End Process tree. This results in the virus stopping to mine. After doing so, you may want to remove the malware preferably by following the automatic or manual removal instructions below, if you have removed malware manually and have the experience. Be advised that security experts strongly recommend to remove the driver.exe miner malware automatically by downloading an advanced anti-malware software, that aims to scan for and erase all malware from your system plus protect it against future infections as well.
Preparation before removing driver.exe malware.
Before starting the actual removal process, we recommend that you do the following preparation steps.
- Make sure you have these instructions always open and in front of your eyes.
- Do a backup of all of your files, even if they could be damaged. You should back up your data with a cloud backup solution and insure your files against any type of loss, even from the most severe threats.
- Be patient as this could take a while.
- Scan for Malware
- Fix Registries
- Remove Virus Files
Step 1: Scan for driver.exe malware with SpyHunter Anti-Malware Tool



Step 2: Clean any registries, created by driver.exe malware on your computer.
The usually targeted registries of Windows machines are the following:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
You can access them by opening the Windows registry editor and deleting any values, created by driver.exe malware there. This can happen by following the steps underneath:


 Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.Step 3: Find virus files created by driver.exe malware on your PC.
1.For Windows 8, 8.1 and 10.
For Newer Windows Operating Systems
1: On your keyboard press + R and write explorer.exe in the Run text box and then click on the Ok button.

2: Click on your PC from the quick access bar. This is usually an icon with a monitor and its name is either “My Computer”, “My PC” or “This PC” or whatever you have named it.

3: Navigate to the search box in the top-right of your PC's screen and type “fileextension:” and after which type the file extension. If you are looking for malicious executables, an example may be "fileextension:exe". After doing that, leave a space and type the file name you believe the malware has created. Here is how it may appear if your file has been found:

N.B. We recommend to wait for the green loading bar in the navigation box to fill up in case the PC is looking for the file and hasn't found it yet.
2.For Windows XP, Vista, and 7.
For Older Windows Operating Systems
In older Windows OS's the conventional approach should be the effective one:
1: Click on the Start Menu icon (usually on your bottom-left) and then choose the Search preference.

2: After the search window appears, choose More Advanced Options from the search assistant box. Another way is by clicking on All Files and Folders.

3: After that type the name of the file you are looking for and click on the Search button. This might take some time after which results will appear. If you have found the malicious file, you may copy or open its location by right-clicking on it.
Now you should be able to discover any file on Windows as long as it is on your hard drive and is not concealed via special software.
driver.exe malware FAQ
What Does driver.exe malware Trojan Do?
The driver.exe malware Trojan is a malicious computer program designed to disrupt, damage, or gain unauthorized access to a computer system.
It can be used to steal sensitive data, gain control over a system, or launch other malicious activities.
Can Trojans Steal Passwords?
Yes, Trojans, like driver.exe malware, can steal passwords. These malicious programs are designed to gain access to a user's computer, spy on victims and steal sensitive information such as banking details and passwords.
Can driver.exe malware Trojan Hide Itself?
Yes, it can. A Trojan can use various techniques to mask itself, including rootkits, encryption, and obfuscation, to hide from security scanners and evade detection.
Can a Trojan be Removed by Factory Reset?
Yes, a Trojan can be removed by factory resetting your device. This is because it will restore the device to its original state, eliminating any malicious software that may have been installed. Bear in mind, that there are more sophisticated Trojans, that leave backdoors and reinfect even after factory reset.
Can driver.exe malware Trojan Infect WiFi?
Yes, it is possible for a Trojan to infect WiFi networks. When a user connects to the infected network, the Trojan can spread to other connected devices and can access sensitive information on the network.
Can Trojans Be Deleted?
Yes, Trojans can be deleted. This is typically done by running a powerful anti-virus or anti-malware program that is designed to detect and remove malicious files. In some cases, manual deletion of the Trojan may also be necessary.
Can Trojans Steal Files?
Yes, Trojans can steal files if they are installed on a computer. This is done by allowing the malware author or user to gain access to the computer and then steal the files stored on it.
Which Anti-Malware Can Remove Trojans?
Anti-malware programs such as SpyHunter are capable of scanning for and removing Trojans from your computer. It is important to keep your anti-malware up to date and regularly scan your system for any malicious software.
Can Trojans Infect USB?
Yes, Trojans can infect USB devices. USB Trojans typically spread through malicious files downloaded from the internet or shared via email, allowing the hacker to gain access to a user's confidential data.
About the driver.exe malware Research
The content we publish on SensorsTechForum.com, this driver.exe malware how-to removal guide included, is the outcome of extensive research, hard work and our team’s devotion to help you remove the specific trojan problem.
How did we conduct the research on driver.exe malware?
Please note that our research is based on an independent investigation. We are in contact with independent security researchers, thanks to which we receive daily updates on the latest malware definitions, including the various types of trojans (backdoor, downloader, infostealer, ransom, etc.)
Furthermore, the research behind the driver.exe malware threat is backed with VirusTotal.
To better understand the threat posed by trojans, please refer to the following articles which provide knowledgeable details.