Remove FacexWorm Virus From Your PC
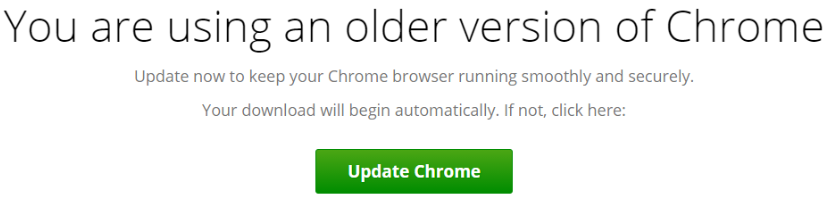
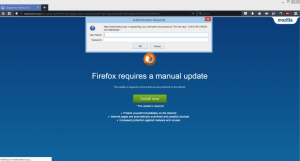
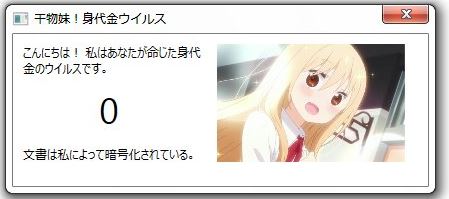
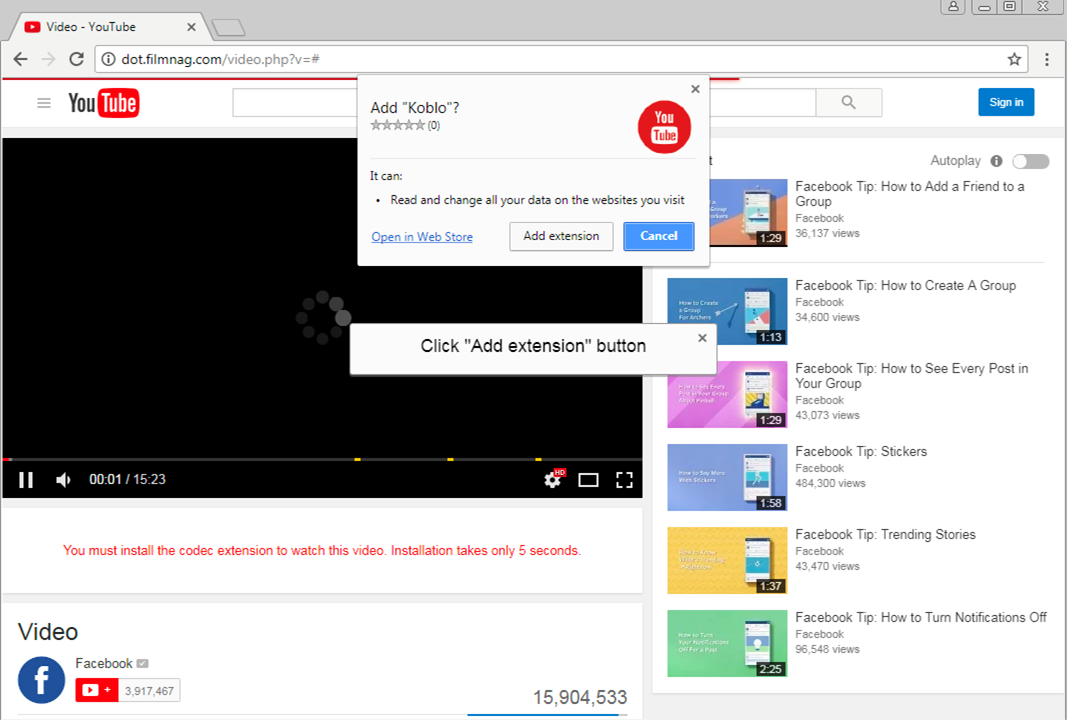
This article has been created in order to help you to learn what is the FacexWorm remote access Trojan and how to remove this malware completely from your computer plus protect your PC against future infections as well. The FacexWorm…