A new type of ransomware virus has been detected by victims and researchers in China to be spread in a global outbreak, calling itself hAnt threatens to burn down your AntMiner if you don’t pay 10 BTC.
A new type of ransomware virus has been detected by victims and researchers in China to be spread in a global outbreak, calling itself hAnt threatens to burn down your AntMiner if you don’t pay 10 BTC.
The ransomware is not only a ransomware virus, but some twisted form of [wplinkpreview url=”https://sensorstechforum.com/doxware-new-type-ransomware-viruses/”]doxware as well. It aims to attack cryptocurrency mining equipment, like all of the AntMiner iterations and then leave behind a nasty ransom note that threatens victims that if they do not let the miners mine for the hackers, they will break down their AntMiner hardware. This virus can cost thousands, if not millions to miners who own crypto mining pools all over the world.

The hAnt Virus Threatens to Burn Your Miner Down And It’s For Real
The hAnt virus is a virus problem that is very difficult to solve. The malware aims to take control of a cryptocurrency miner by attacking the mining machine’s SD card, where it’s firmware is located. Once there, the miner virus is very complex and difficult to remove. Chinese victims report that it took IT experts up to 4 days to solve the problem.
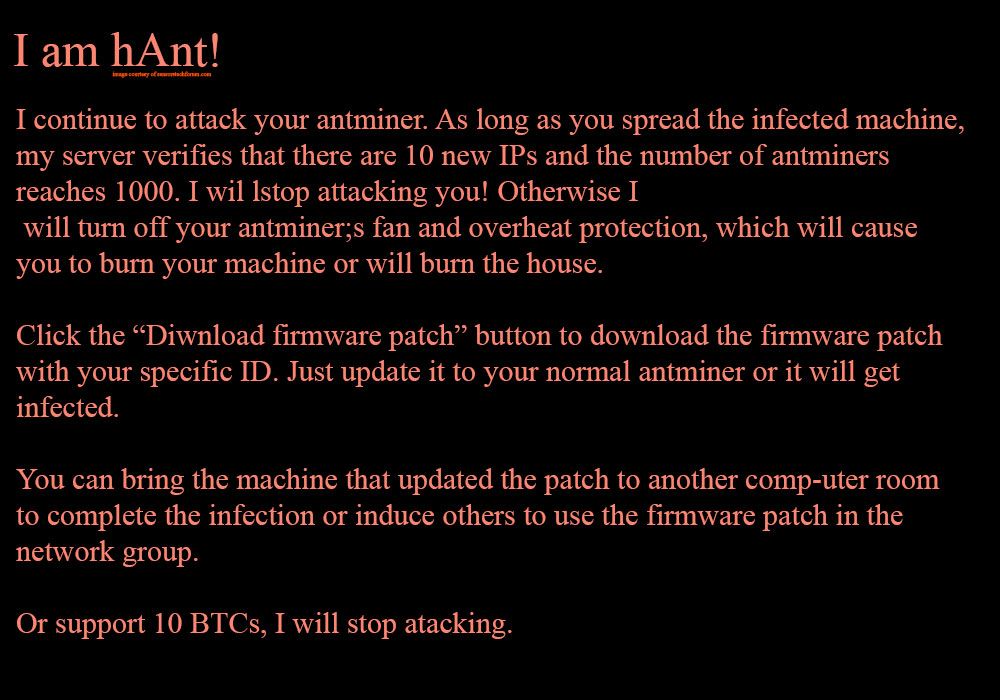
Once this miner has already attacked the AntMiner or other mining equipment, it sets it’s scary message on the victim’s computer. The message looks like the image below shows:
Text from Image:
I am hAnt!
I continue to attack your antminer. As long as you spread the infected machine, my server verifies that there are 10 new IPs and the number of antminers reaches 1000. I wil lstop attacking you! Otherwise I will turn off your antminer;s fan and overheat protection, which will cause you to burn your machine or will burn the house. Click the “Diwnload firmware patch” button to download the firmware patch with your specific ID. Just update it to your normal antminer or it will get infected. You can bring the machine that updated the patch to another comp-uter room to complete the infection or induce others to use the firmware patch in the network group. Or support 10 BTCs, I will stop attacking.
What is most interesting about the hAnt virus is that it demands from the victims that they either pay 10 BTC, or spread it’s malware to other miners. The malware threatens something that must not be taken lightly – it will overheat the components of the attacked mining hardware, making it suffer breakage and it can even burn down due to overheating, which can even be dangerous to miners’ property and their lives as well.
The crooks want the victims to attack specific number of AntMiners – 1000 and they want to remain persistent on them and if the victim helps attack other miners, they can be freed from the virus.
The hAnt Outbreak – What Can Be Done?
Researchers report that this problem has started first in August 2018 and researcher Yu Hai, COO Yuyang, told blockchain reports that it has been growing ever since.
According to most recent analysis, the minin g machine is infected as a result of running on mines that contain the virus and this is probably the main method by which this virus attacks. So one way to stop it is to check for most Mining Pools and other mines to see if they have a virus and use a killswitch to discontinue the IP adresses of those miners so that they can no longer be controlled.
But the bad news is that removing the virus from th SD cards of the infected AntMiners can take quite some time, so researchers classify it as being as complicated as reinstalling the mining machine from the ground up and adding brand new clean firmware. According to experts, the attacked mining machine can produce up to 8510 USD per 24 hours, which means that hackers can generate a lot of money for short periods of time.
According to Jiang Lai Bite Thatcher who has been tracking this virus for quite some time now, there are several mining rigs that can be attacked by this virus:
- Antminer S9
- Antminer T9
- Antminer L3+ (Litecoin mining machine)
- Avalon Miner
Researchers Jiang Zhoer and Yu Yang are both convinced that the source of this virus is very likely to come from a vulnerability that allows overclocking of the firmware the code for which is likely released by an anonymous hacker or group of hackers.
What is the scariest part though is that the hAnt ransomware can actually do what it threatens by overclocking the miner by taking advantage of the firmware of the Antminer, since the hAnt virus is configured to “poison” the machine with the purpose to take control of it’s hardware.
Researchers have also reported that this infection is highly contagious. It may infect one or more machines, buyt once this happen, the malware rapidly begins to spread to the machines and overclock them to increase their mining capabilities. If you are unaware, overclocking means that the criminals push your mining machine to it’s limits in order to increase the mining power and calculate more hashes per second. This overheats the machine and keeps it’s coolers running at a very high speed.
Researchers advise that if you detect an infection on your Mining rigs with this miner, the firs thing you should do is to isolate the machine and then think about how you can analyse their IN and OUT traffic so that you can establish the source IP addresses the communication comes from in order to report it to authorities and shut the pool of the hackers down.
The bad news is that hackers can use a lot of different methods to monitor what you are doing on the miner and even see if you try to change your passwords, so if you are attacked, chances are that it will be at time, where your are sleeping or not monitoring the mining farm. And researchers also warn of ‘trip-wire” type of attacks, that trigger scripts which can break down your miner once you disconnect it from the internet, so extreme caution should be taken.