A new DDoS attacks trend has been observed by security experts. The new method relies on a Domain Name System (DNS) amplification that uses text records in order to make the attack more efficient. Cyber criminals have been using parts of White House press releases in their campaigns.
This approach is not brand new, but the Prolexic Security Engineering and Research Team observed an increasing number of incidents in the last month.
Most Targeted Sectors
TXT records have been used in the past in attacks targeting government websites. The new goal of the cyber criminals is to provide a large response size, which guarantees a large impact.
In a typical DDoS attack, the targeted server is being brought down by delivering a huge number of requests to it. This way the information cannot be processed.
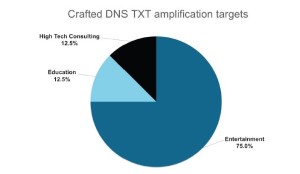
The Research Team reports that these are the mostly targeted sectors:
- High tech consulting – 12.5%
- Education – 12.5%
- Entertainment – 75%
The parts of the original text are taken from the guessinfosys.com domain. They have been used in a DDoS reflected attack. This method involves intermediate victims who reflect the malicious traffic to the hacker’s targets.
A Fifteen-Hour-Long Attack
Inspecting the incidents, the experts revealed that DDoS attacks using the DNS TXT amplification method was a part of longer campaigns, the longest one among which lasted over fifteen hours.
The analysis shows that the hackers used source port 53 for the attacks. The one they were targeting was 80.
In a DNS amplified DDoS attack, the crooks send a request to the server by using the victim’s IP address. This way, as the server returns a response bigger than the request, the packets are sent to the compromised machine and lead to a denial-of-service state. PLXsert reported a peak bandwidth at 4.3Gbps.
Experts recommend using an ACL (access of control list) as a form of defense. This would work only if the bandwidth is more than the attack can produce.