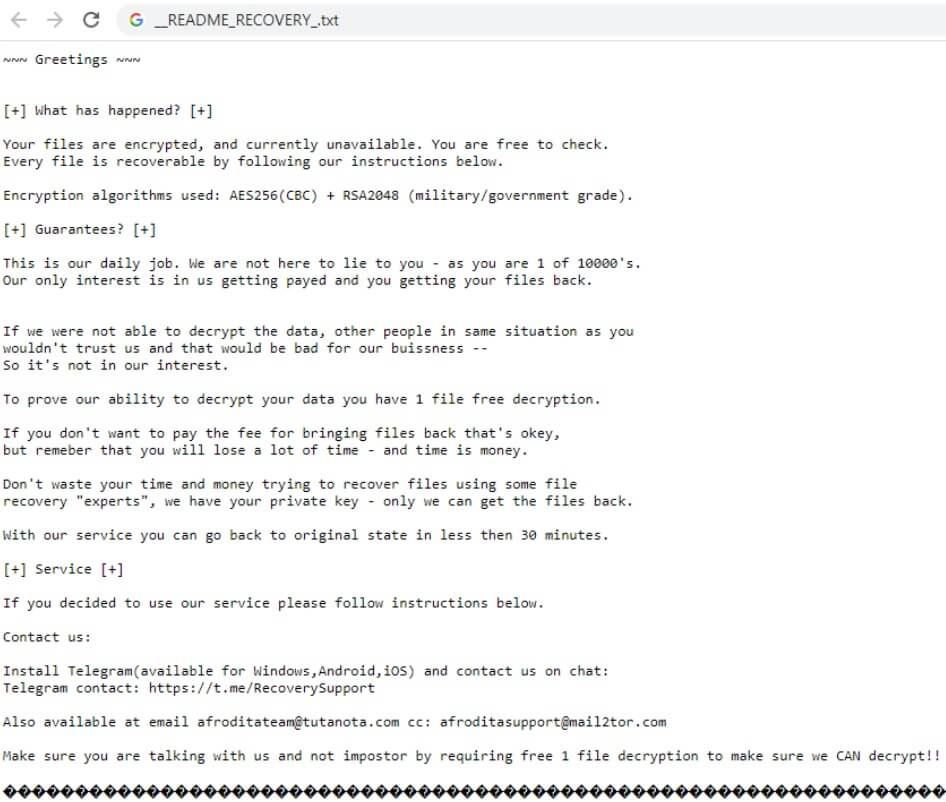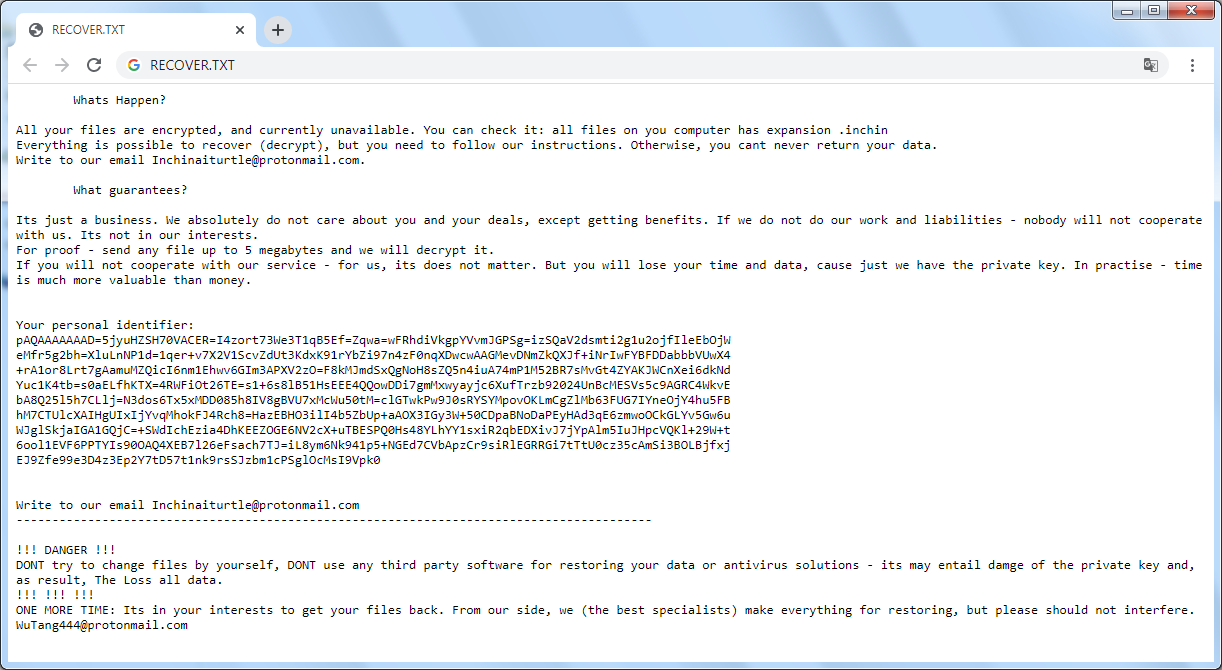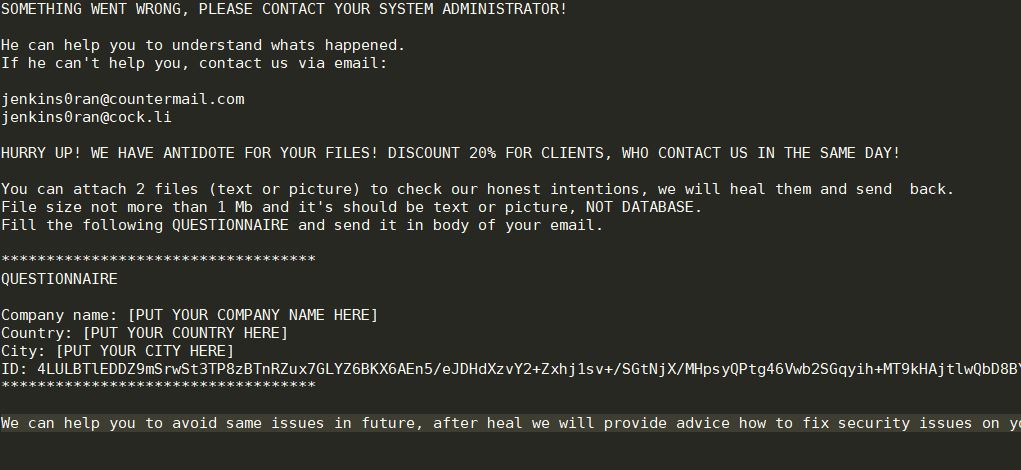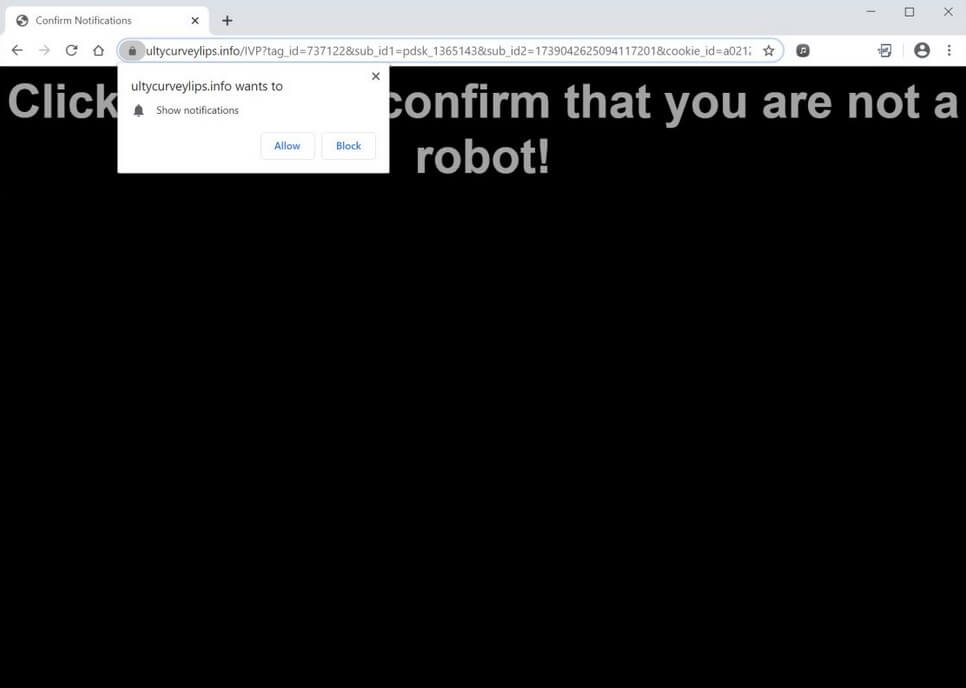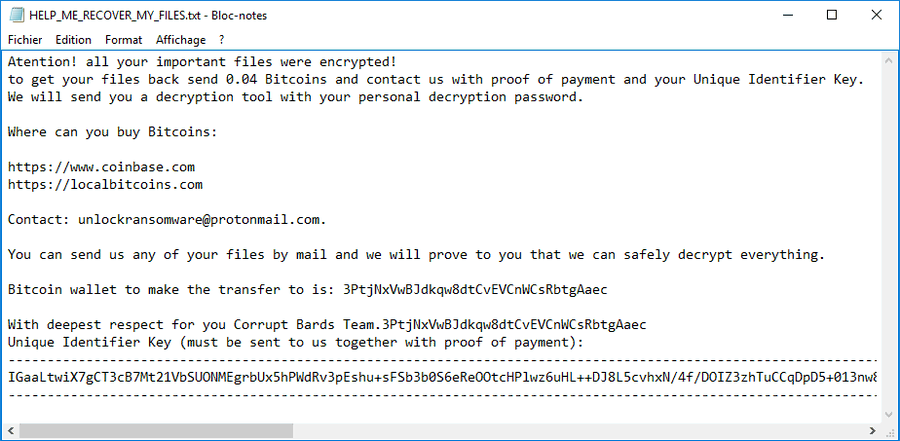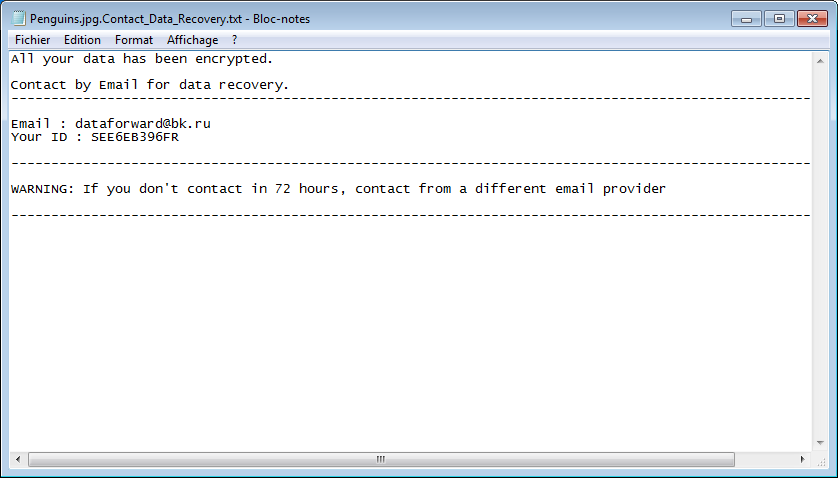
Can Fraudsters Hack Your Contactless Card?
With the introduction of contactless cards into the financial sector came swift, convenient, and secure payments. However, like any useful innovation, the adoption of contactless payment has seen its fair share of controversy. Perhaps, the most prominent of these disagreements…