Is Your Business in Need of Pen Testing?
With cybersecurity threats increasing daily, the need to regularly identify and address vulnerabilities to protect against the latest threats is now more critical than ever. Penetration testing, a popular type of ethical hacking assessment, is a crucial way to help…



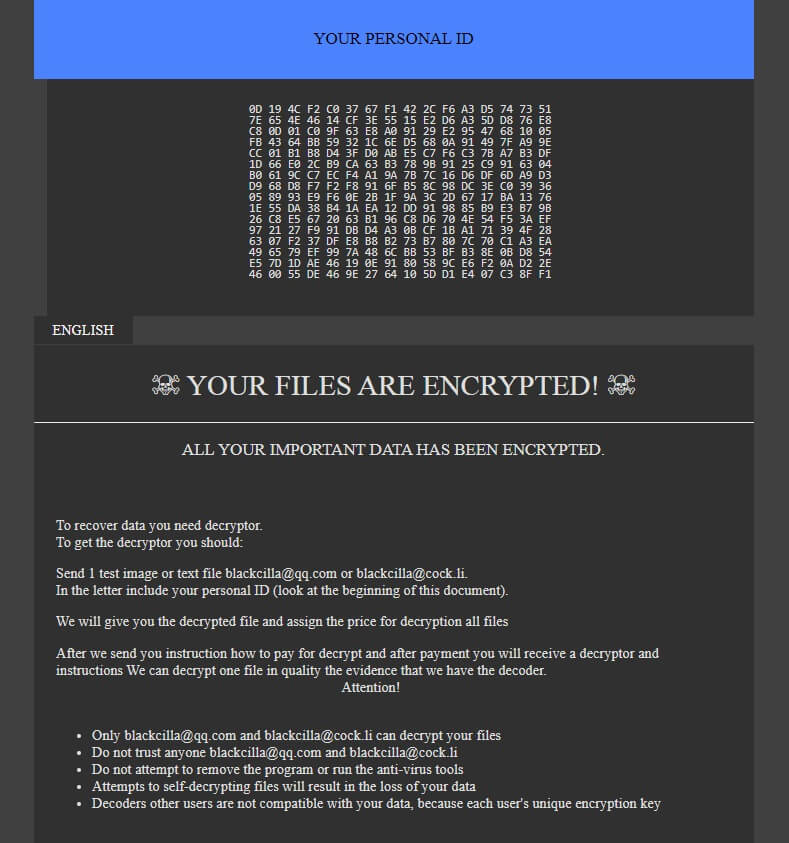





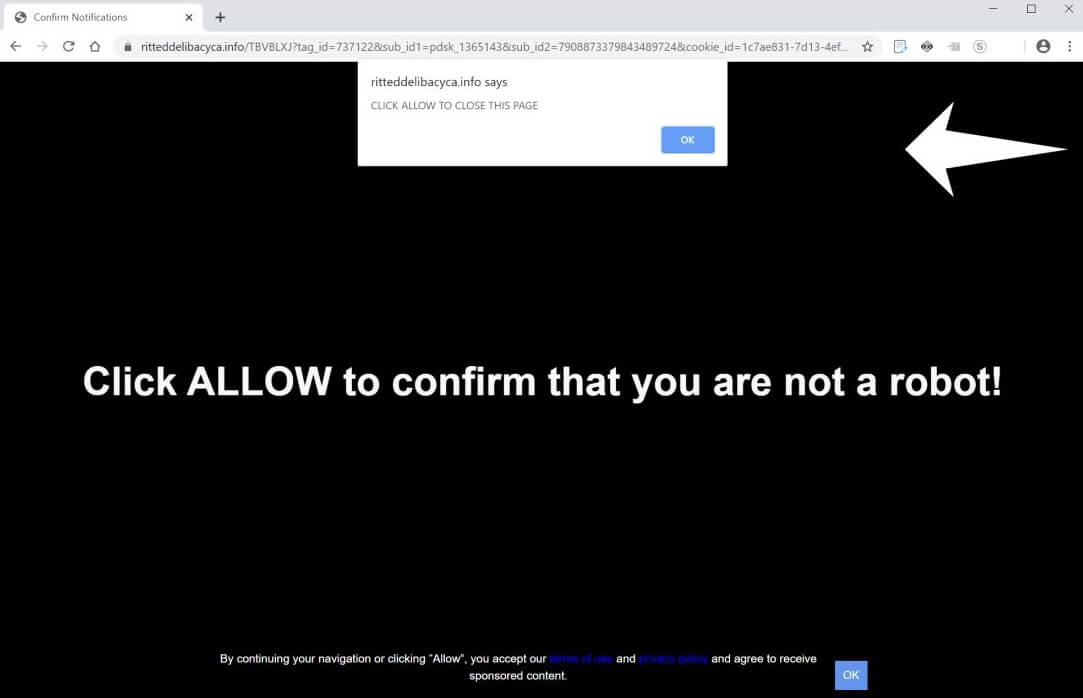
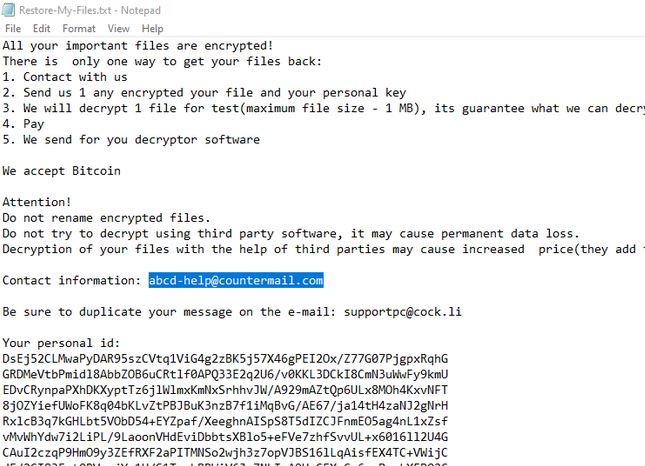



![.[helpnetin@protonmail.com].com Virus File (Dharma Ransomware) – Remove It .[helpnetin@protonmail.com].com-virus-file-dharma-ransomware-note-stf](https://cdn.sensorstechforum.com/wp-content/uploads/2019/12/helpnetin@protonmail.com_.com-virus-dharma.jpg)