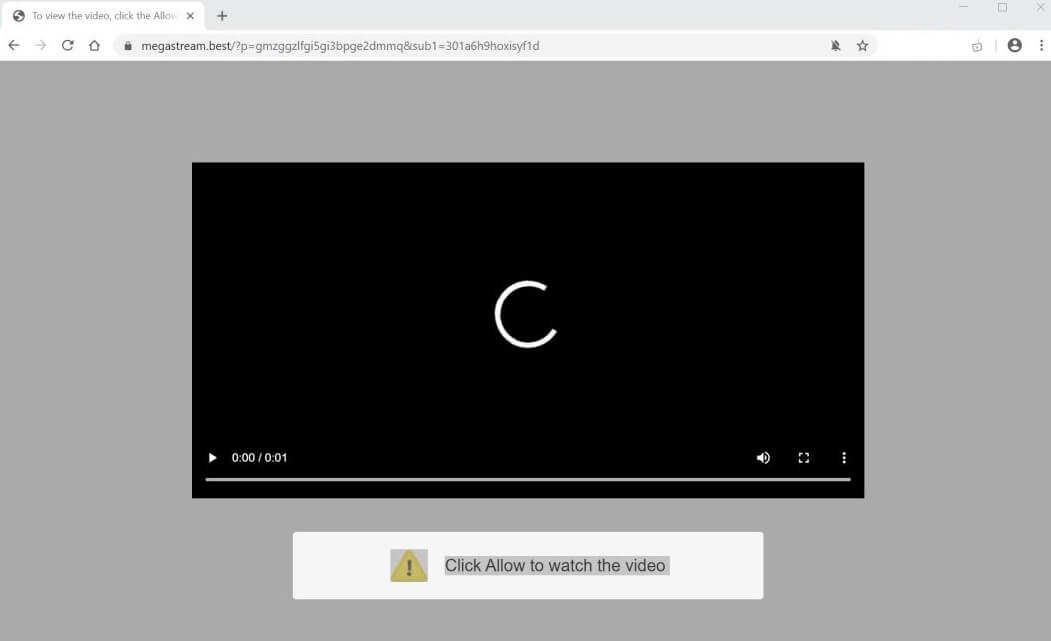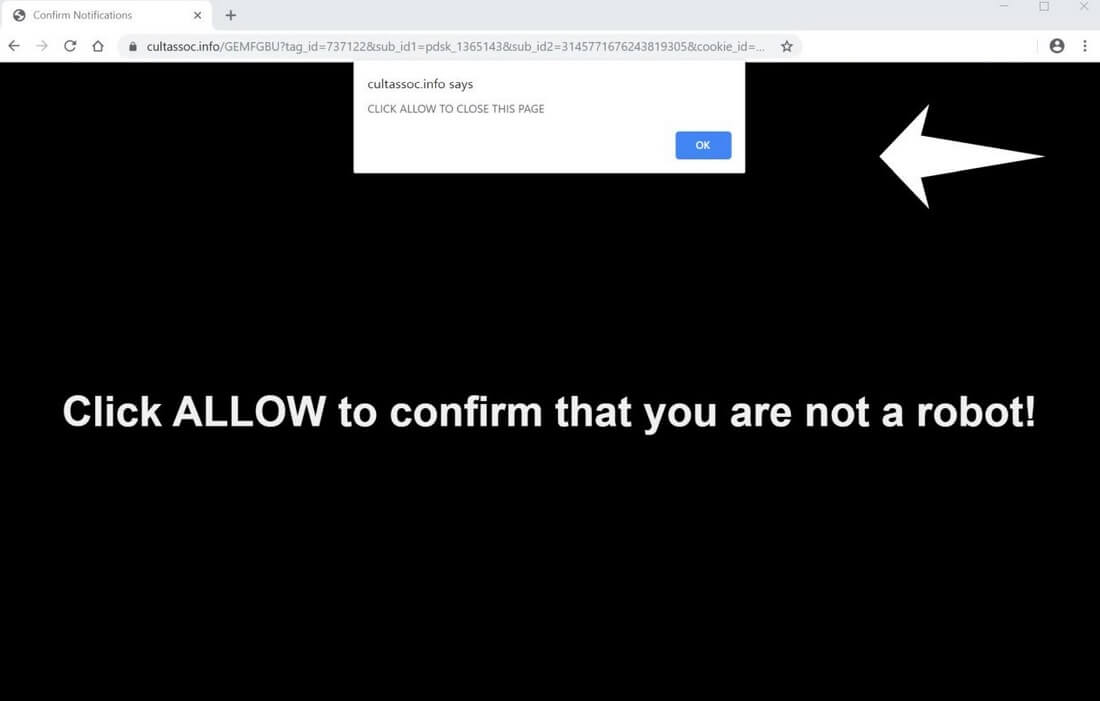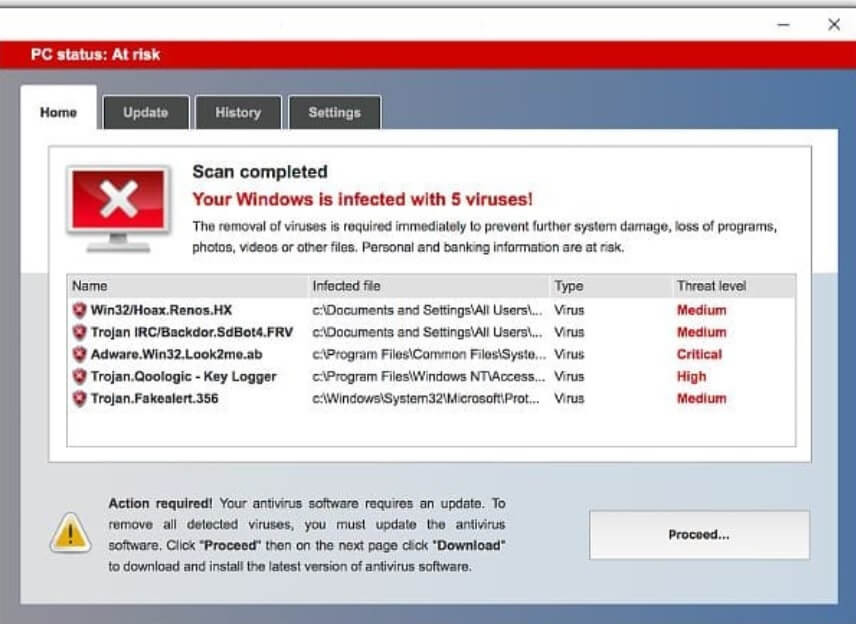
Remove Your Windows Is Infected with 5 Viruses Scam
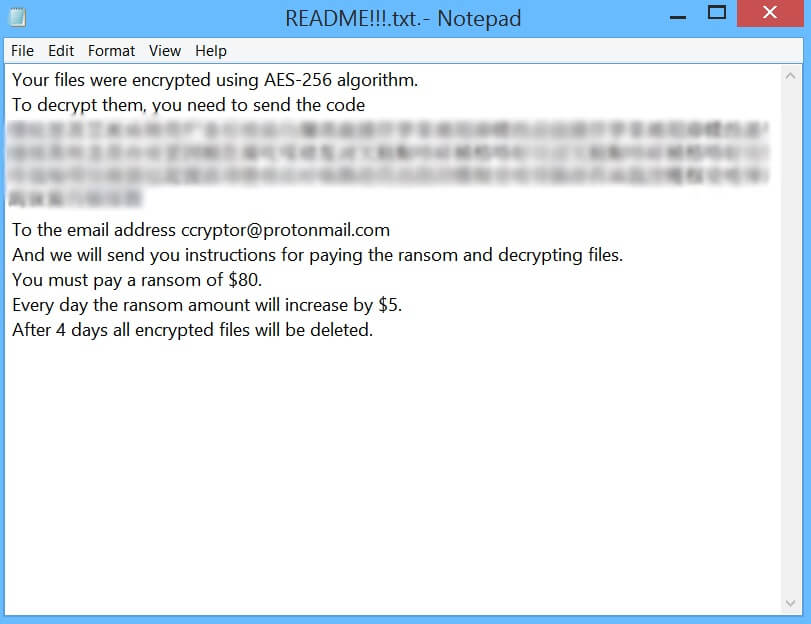
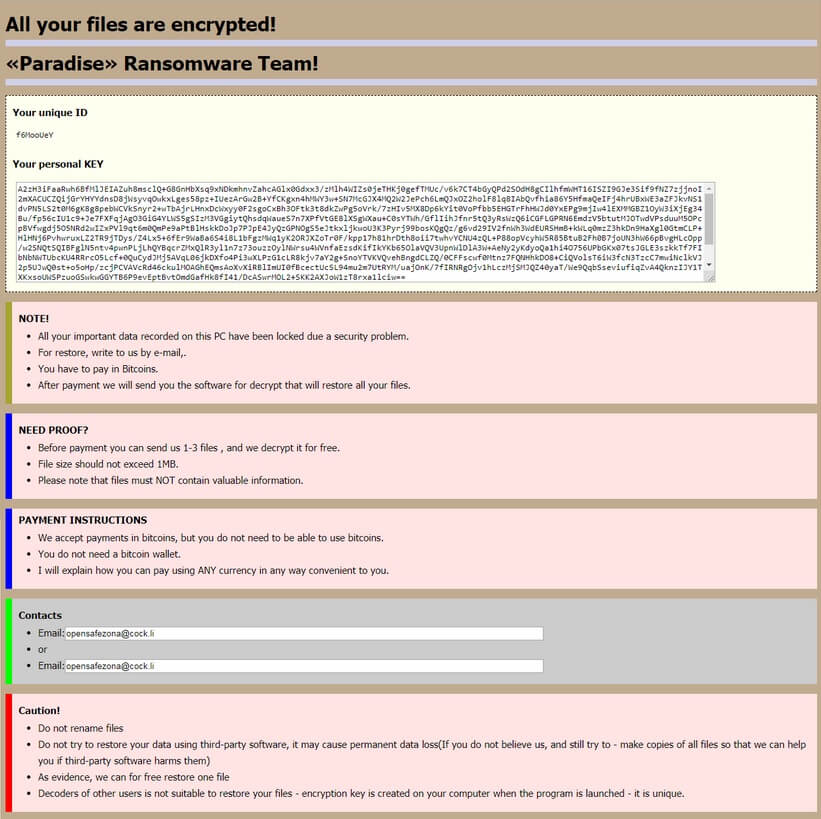
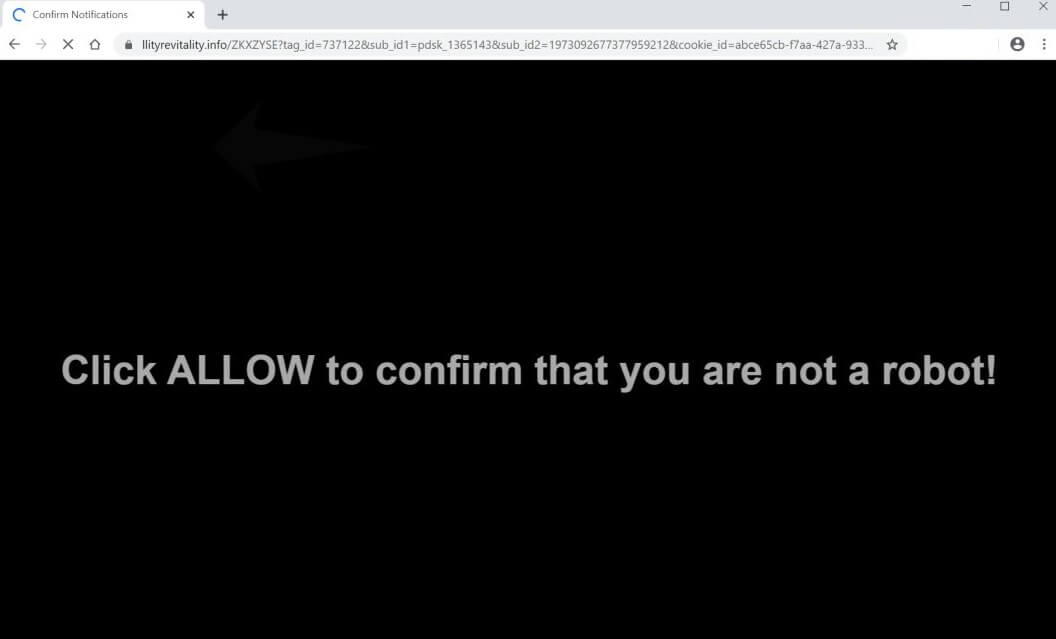
What Is Your Windows Is Infected With 5 Viruses? Can Your Windows Is Infected With 5 Viruses messages be caused by malware? Is your computer infected? Your Windows Is Infected With 5 Viruses is a technical support scam that will…