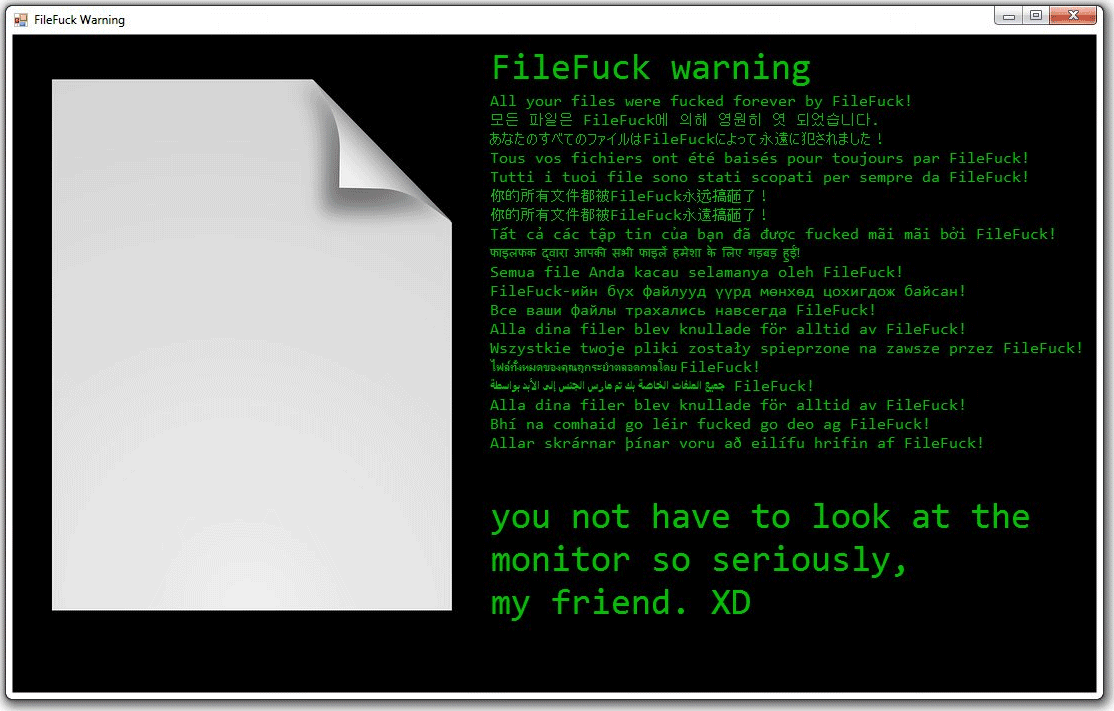
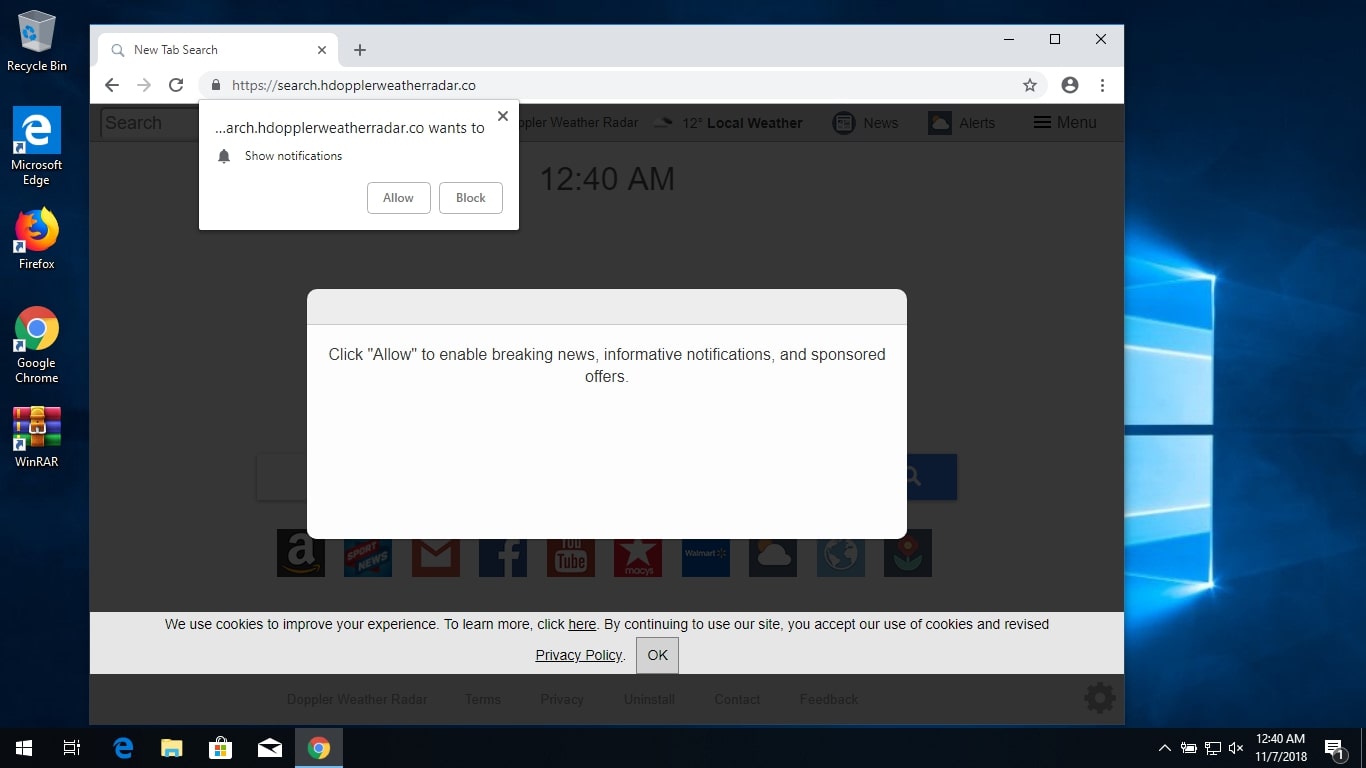
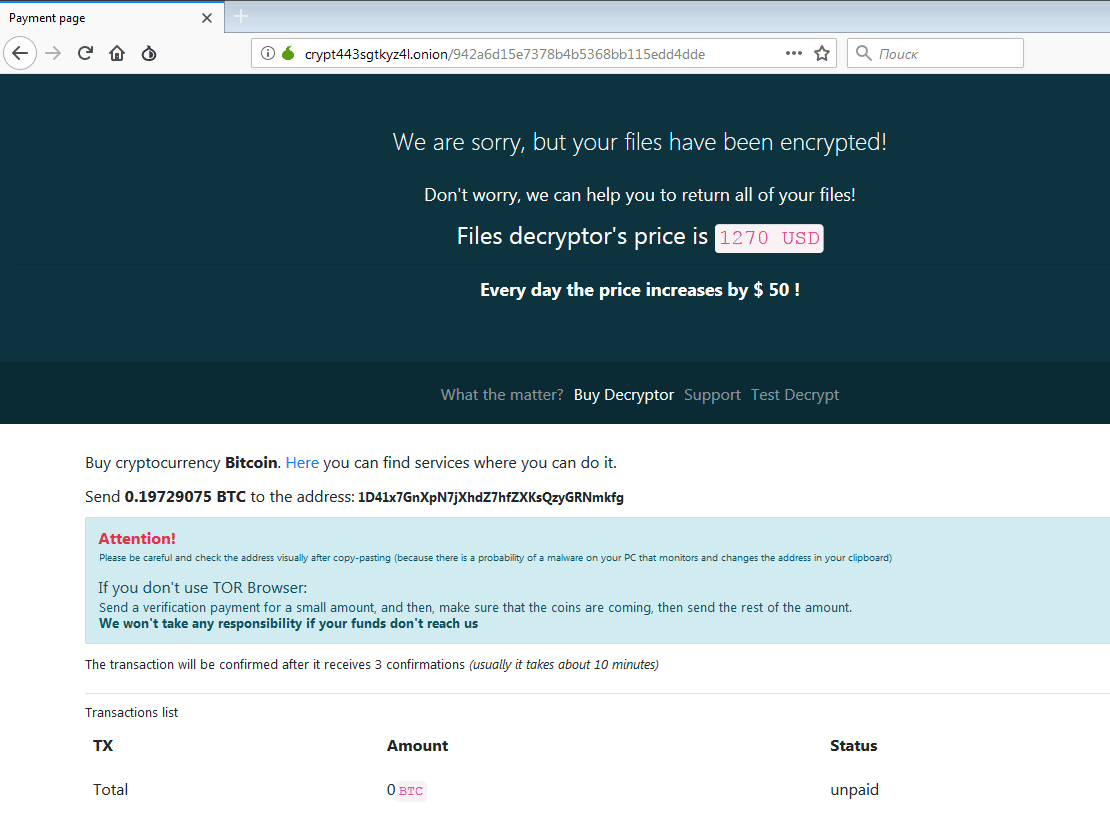
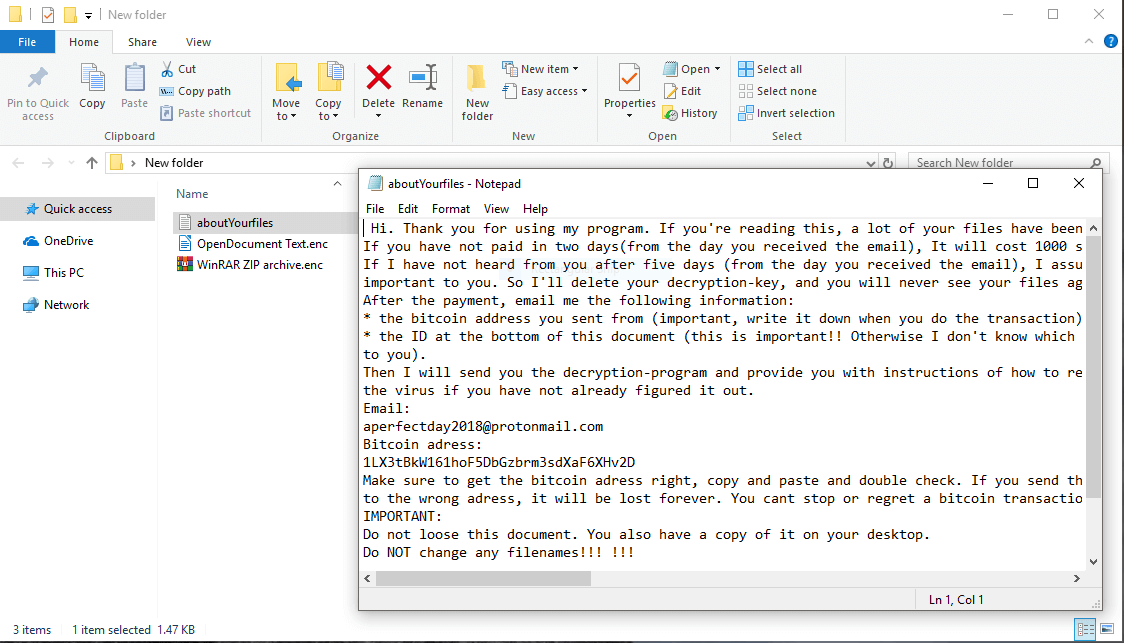
Side-channel Attacks Found to Affect GPU Cards
A new security report shows that GPU cards are vulnerable to new side-channel attacks. These exploits target both individual end-users that use them in day-to-day activities and clusters that rely on GPUs for distributed computing. GPU Cards Follow CPUs By…