How to Remove Topmedia24.me Ads (Chrome, Firefox, Safari, Explorer)
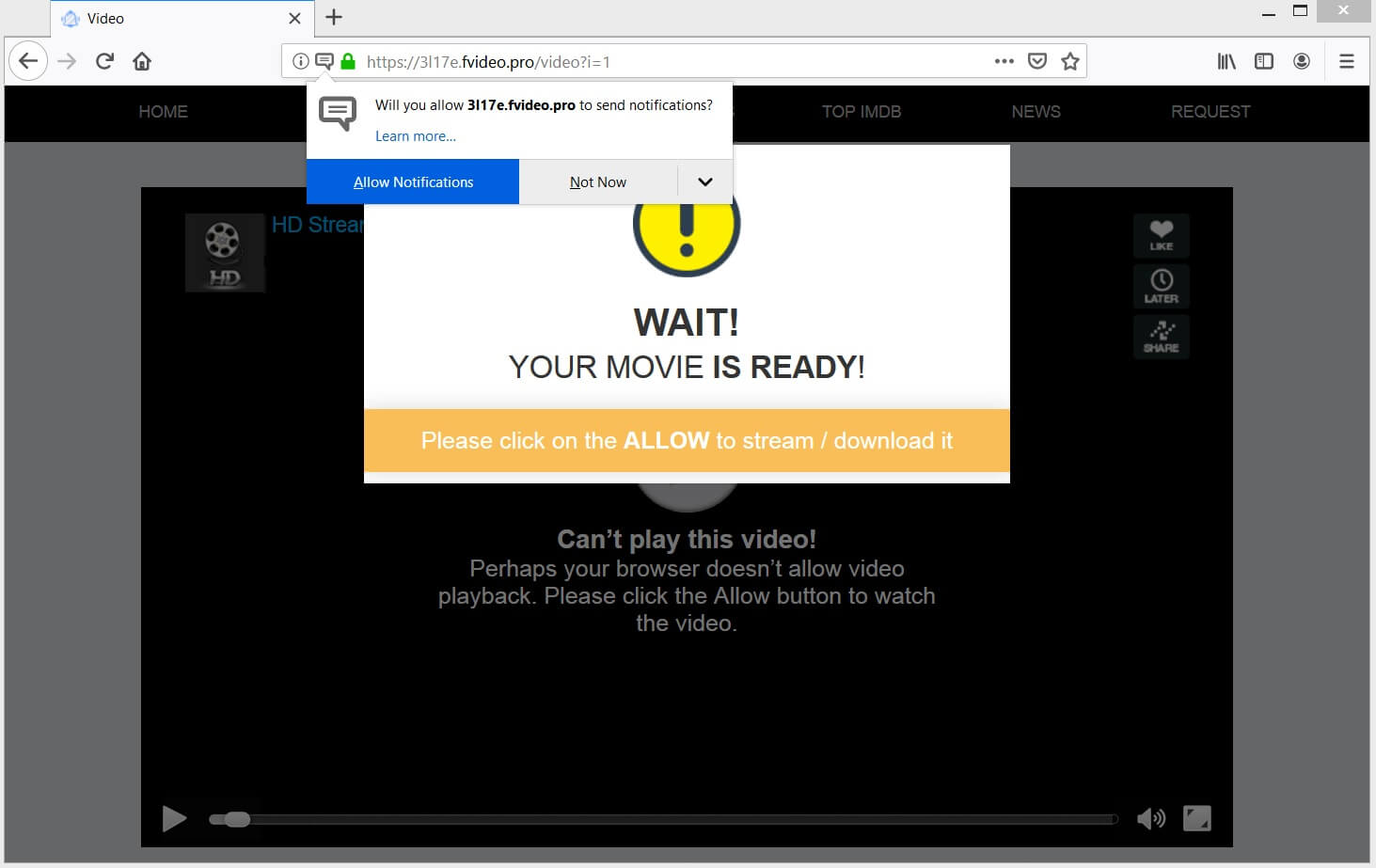
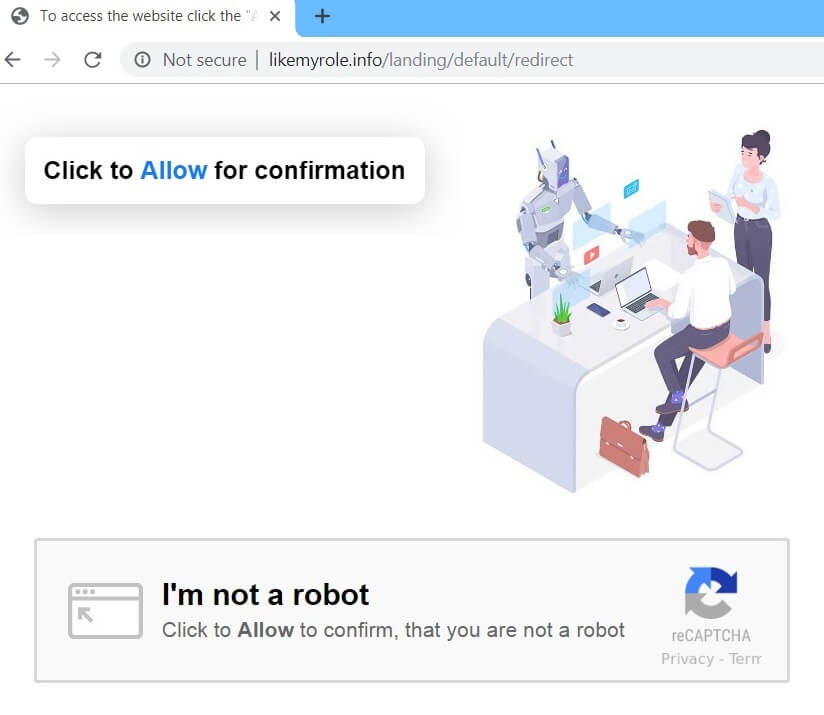
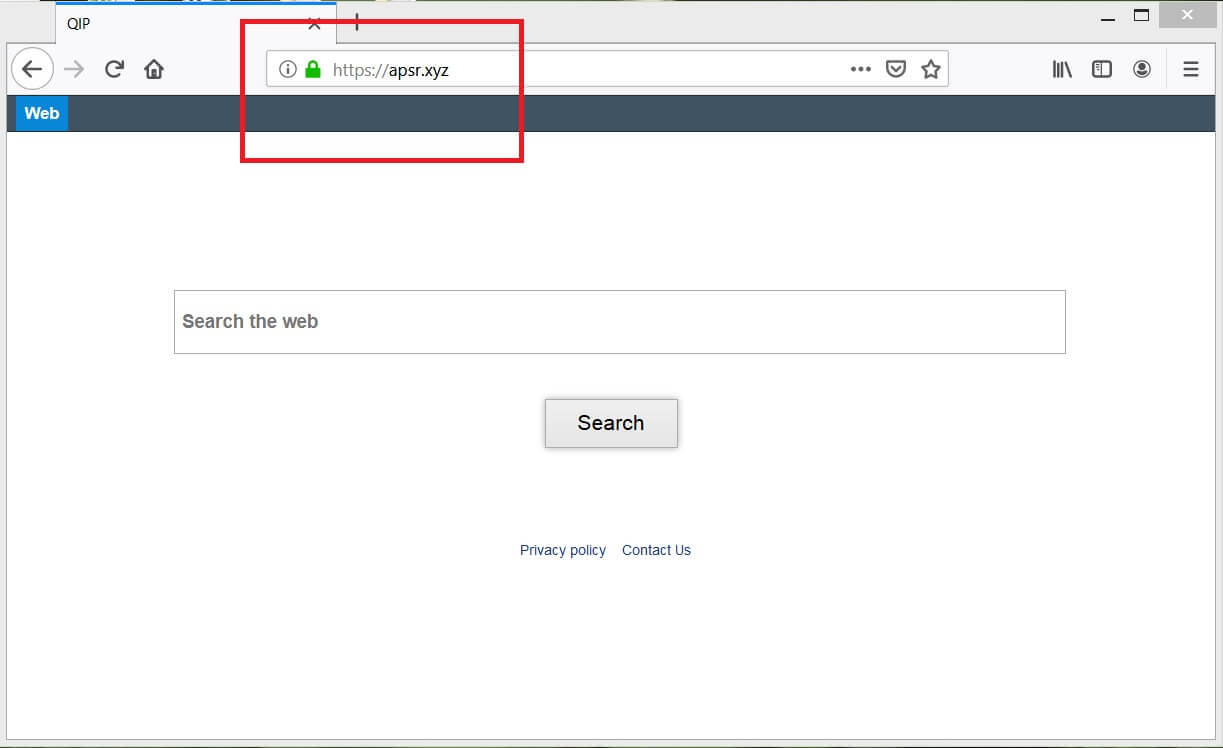
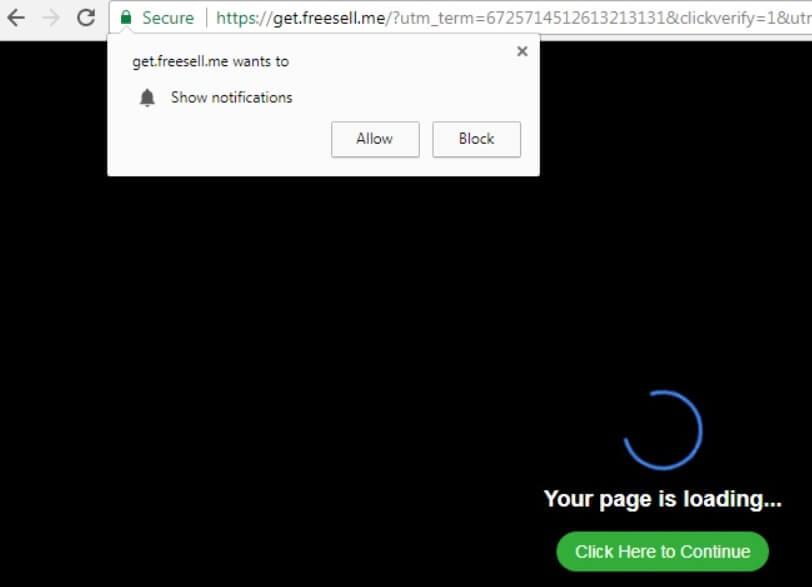
Topmedia24.me is a website with questionable reputation that affects popular web browsers and generates annoying pop-up ads. Its unexpected appearance may be supported by a potentially unwanted program that is running on the computer. Have in mind that the information…


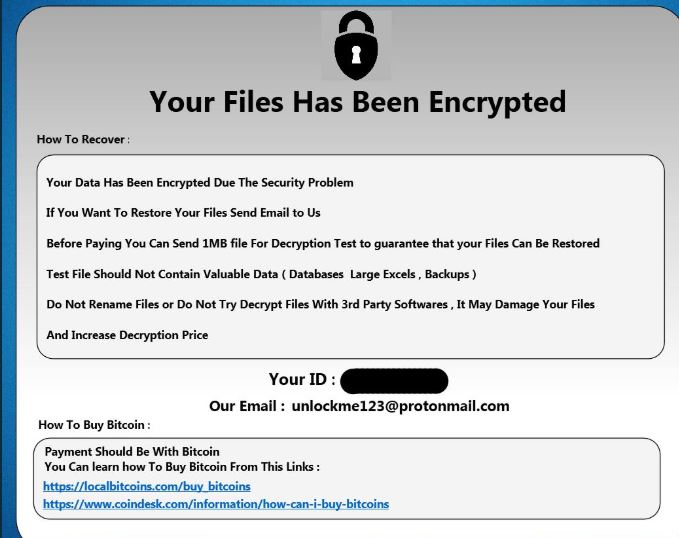
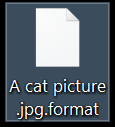
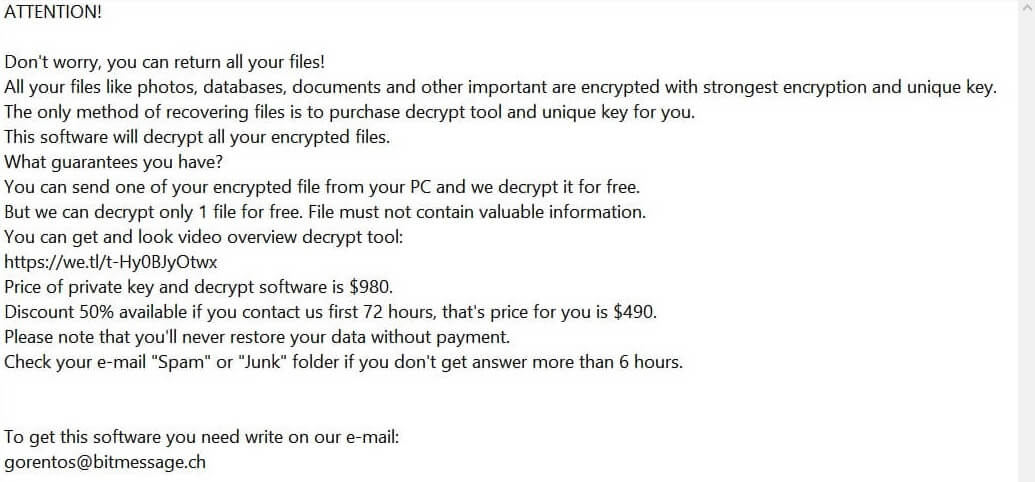
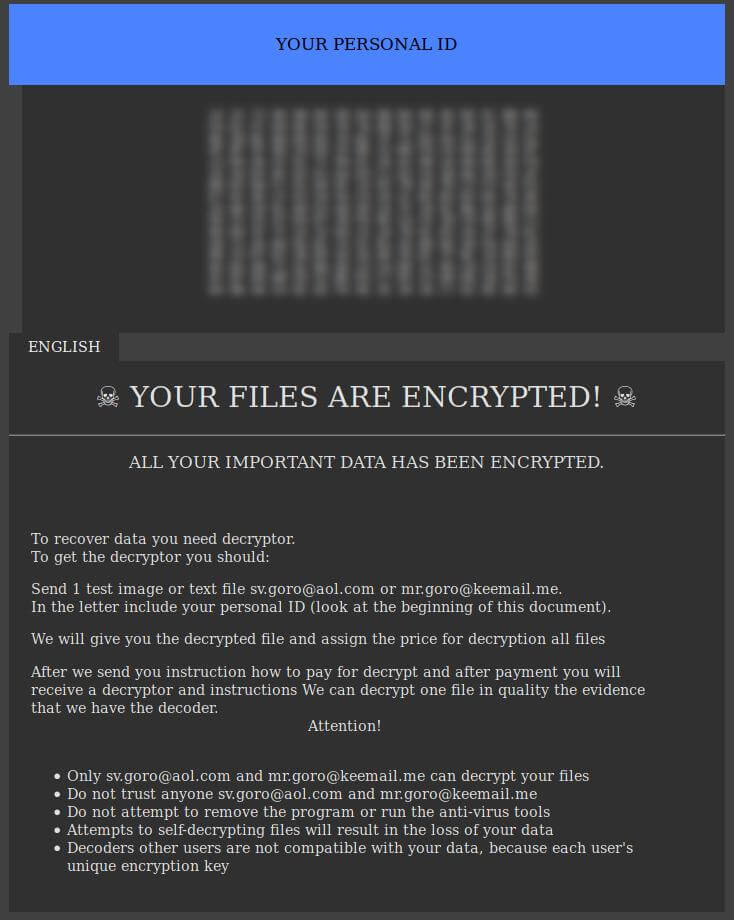



![[grethen@tuta.io] Virus (.[grethen@tuta.io] File) – How to Remove .[grethen@tuta.io] Ransomware virus remove](https://cdn.sensorstechforum.com/wp-content/uploads/2019/08/grethen@tuta.io-virus-image-sensorstechforum-com.jpg)