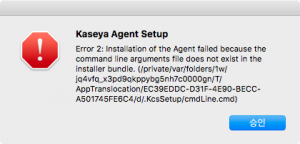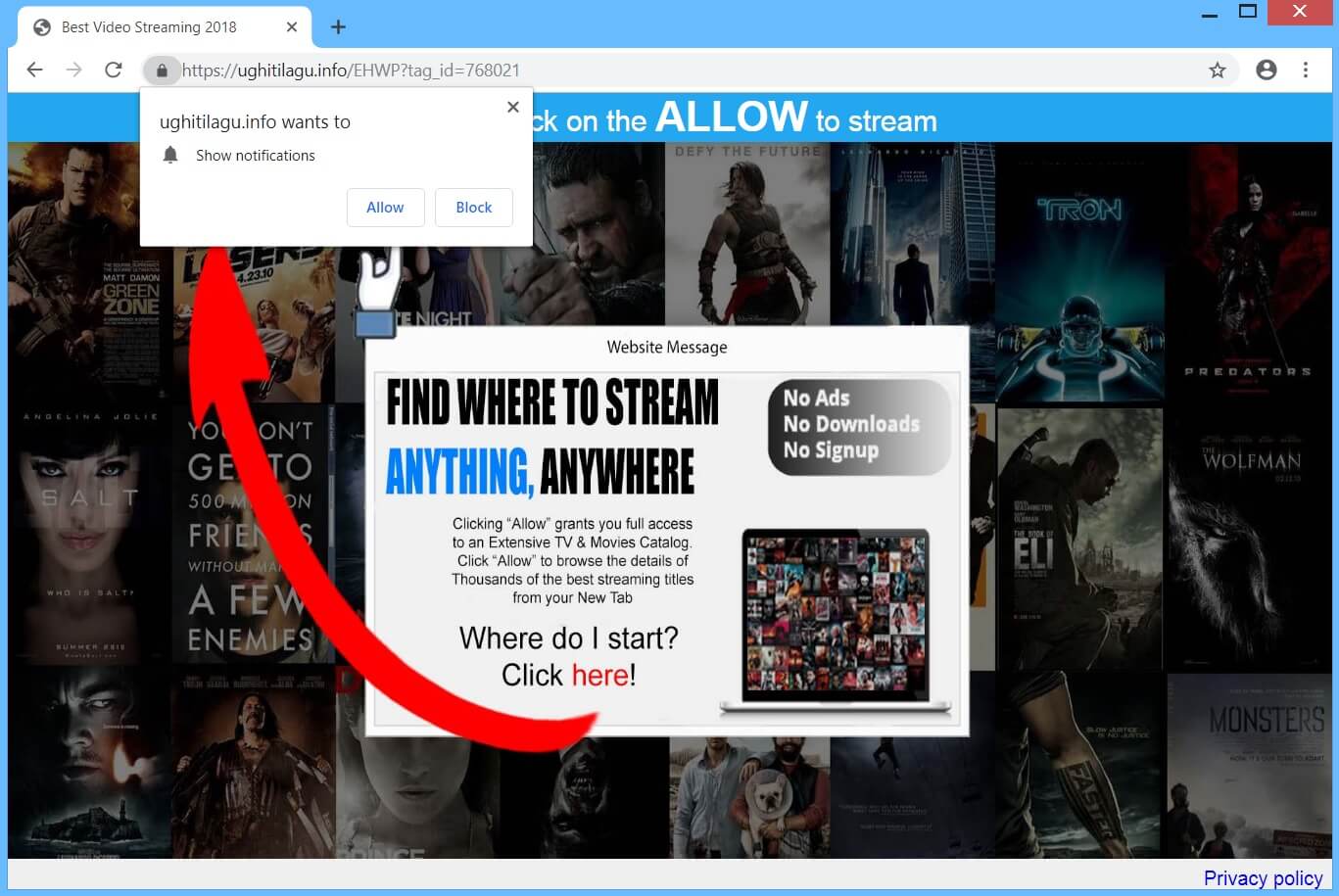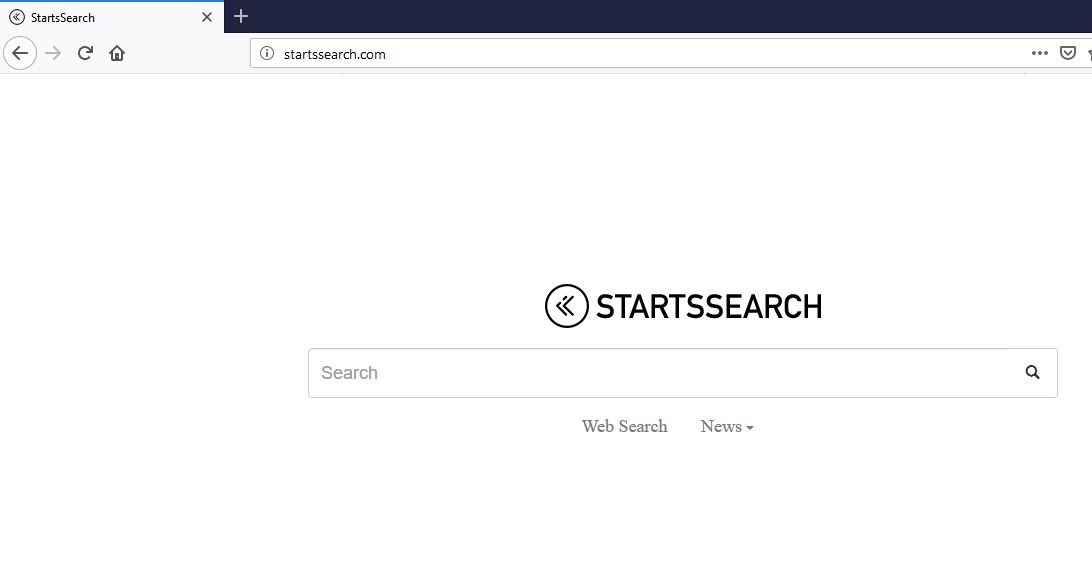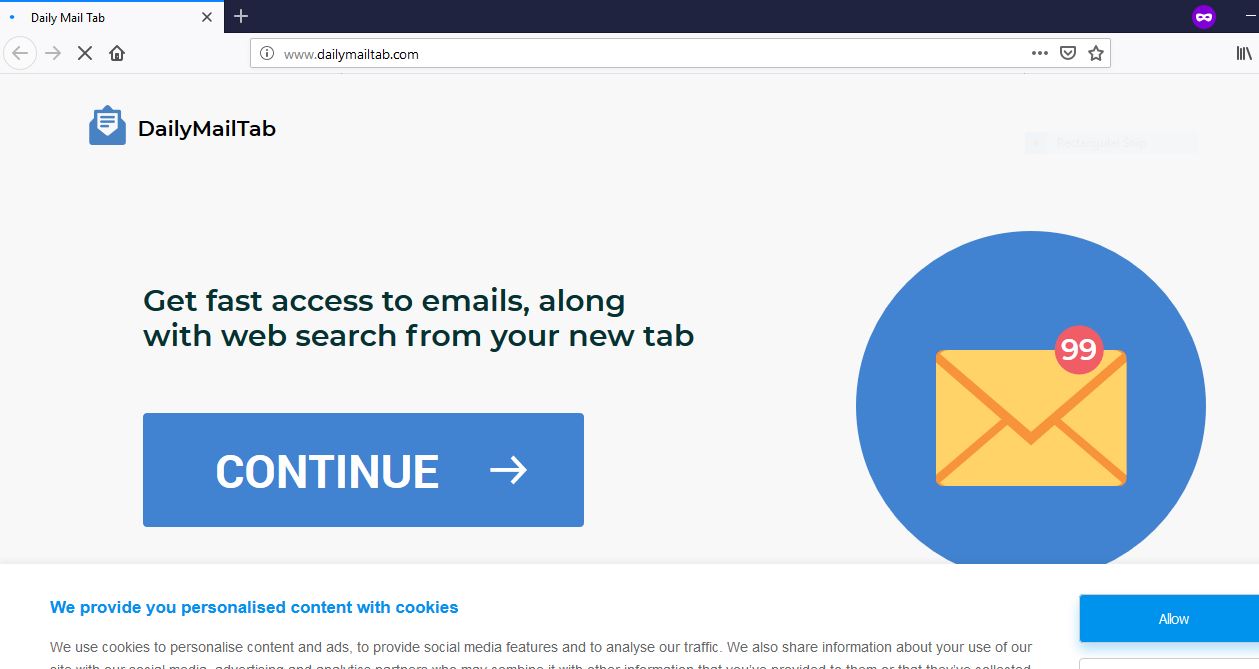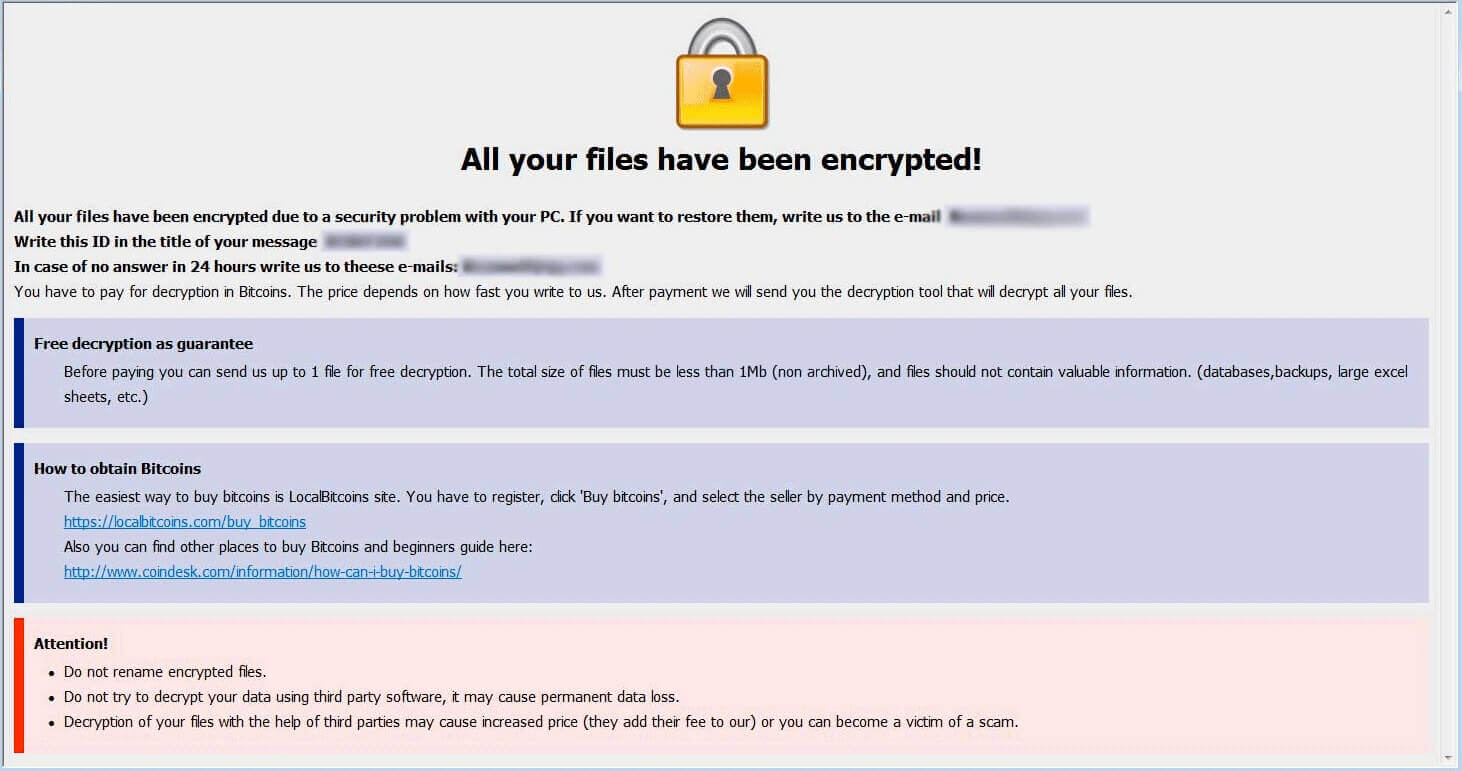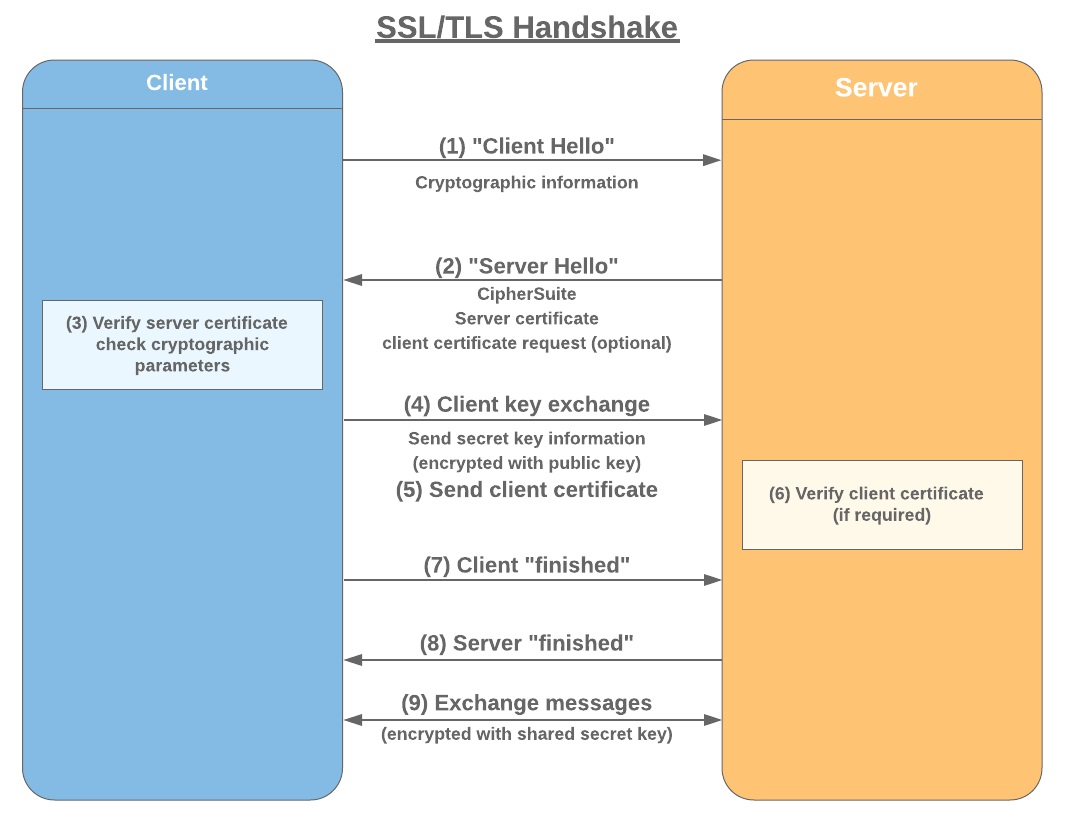
Cipher Stunting – Attackers’ Latest Evasion Technique
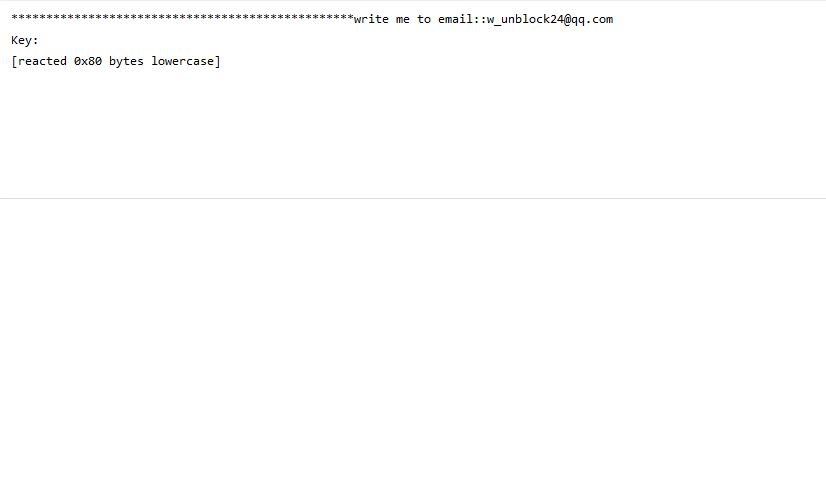
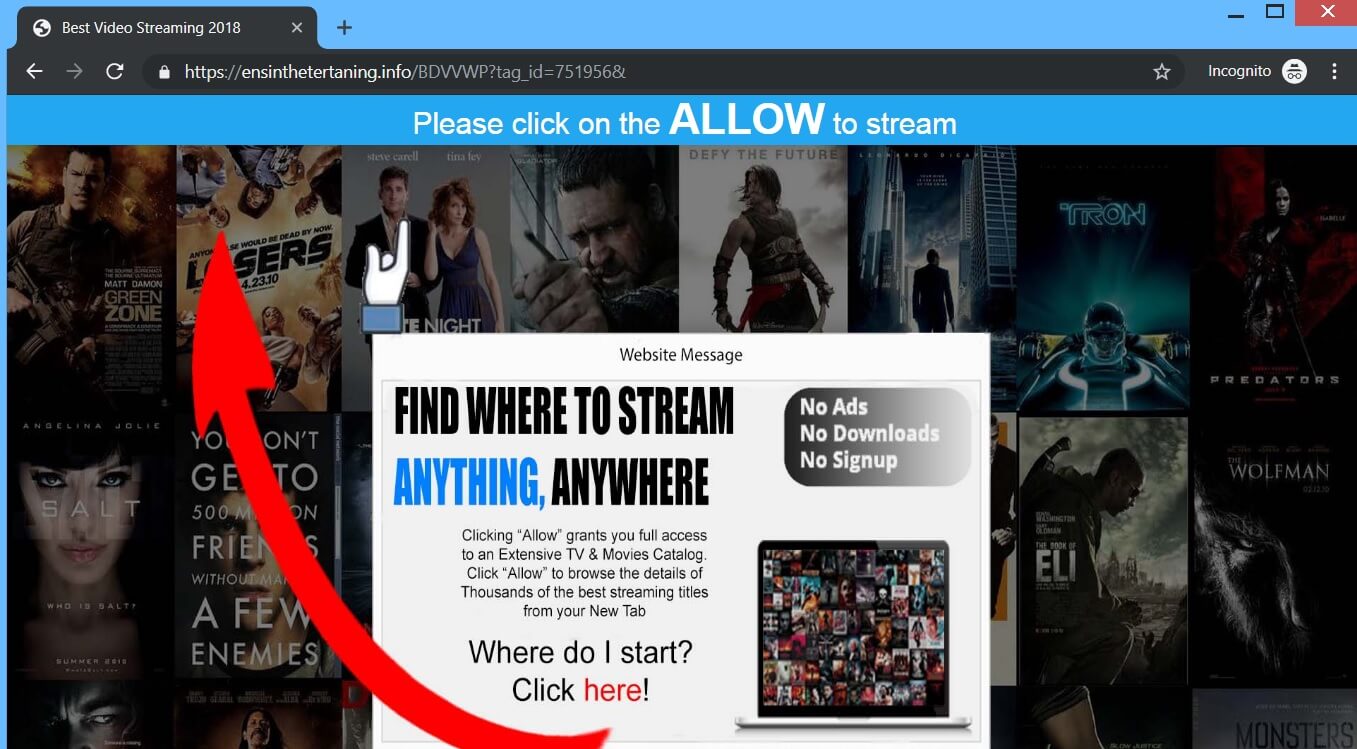
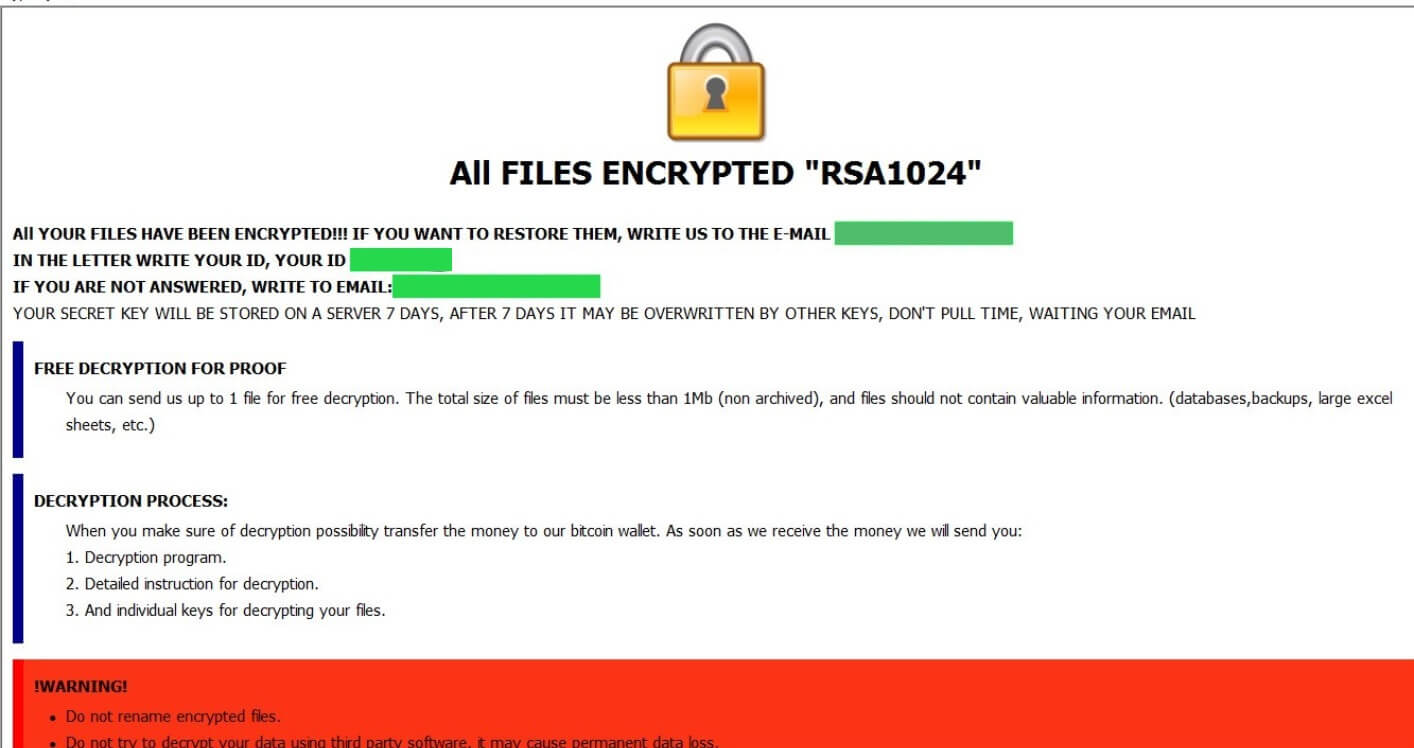
Evasion of detection mechanisms used by security companies has always been a goal for cybercriminals. And it seems they have found a new way to improve these efforts. The new method is based on SSL/TLS signature randomization, and is given…