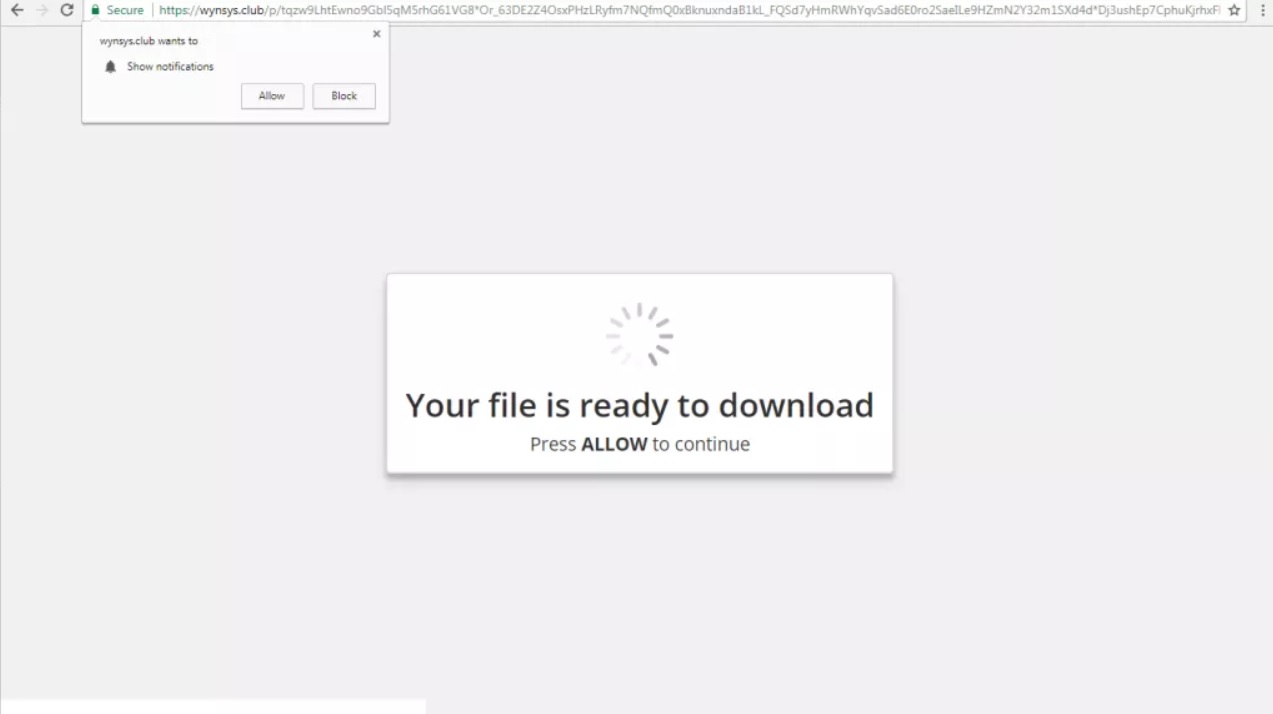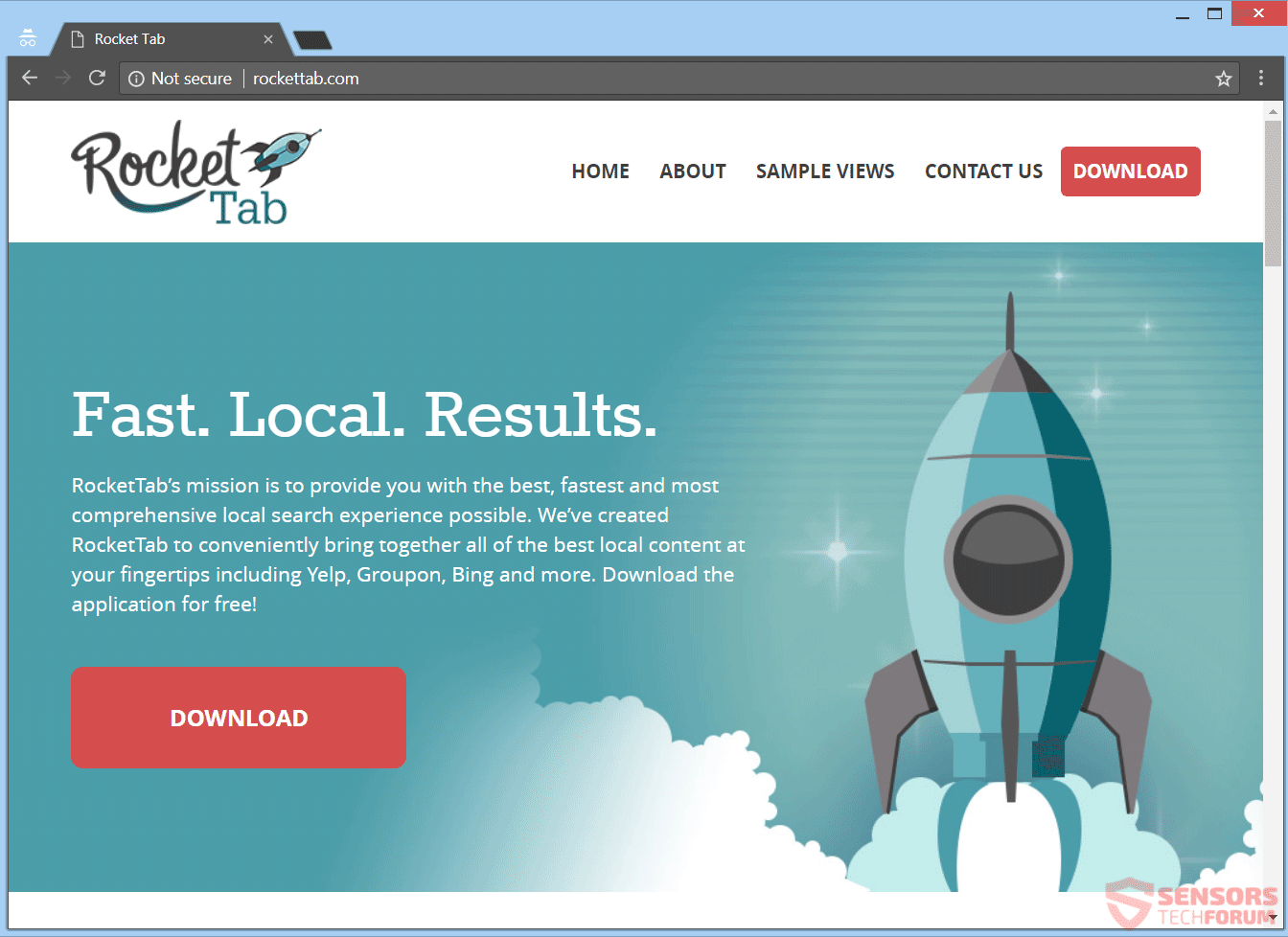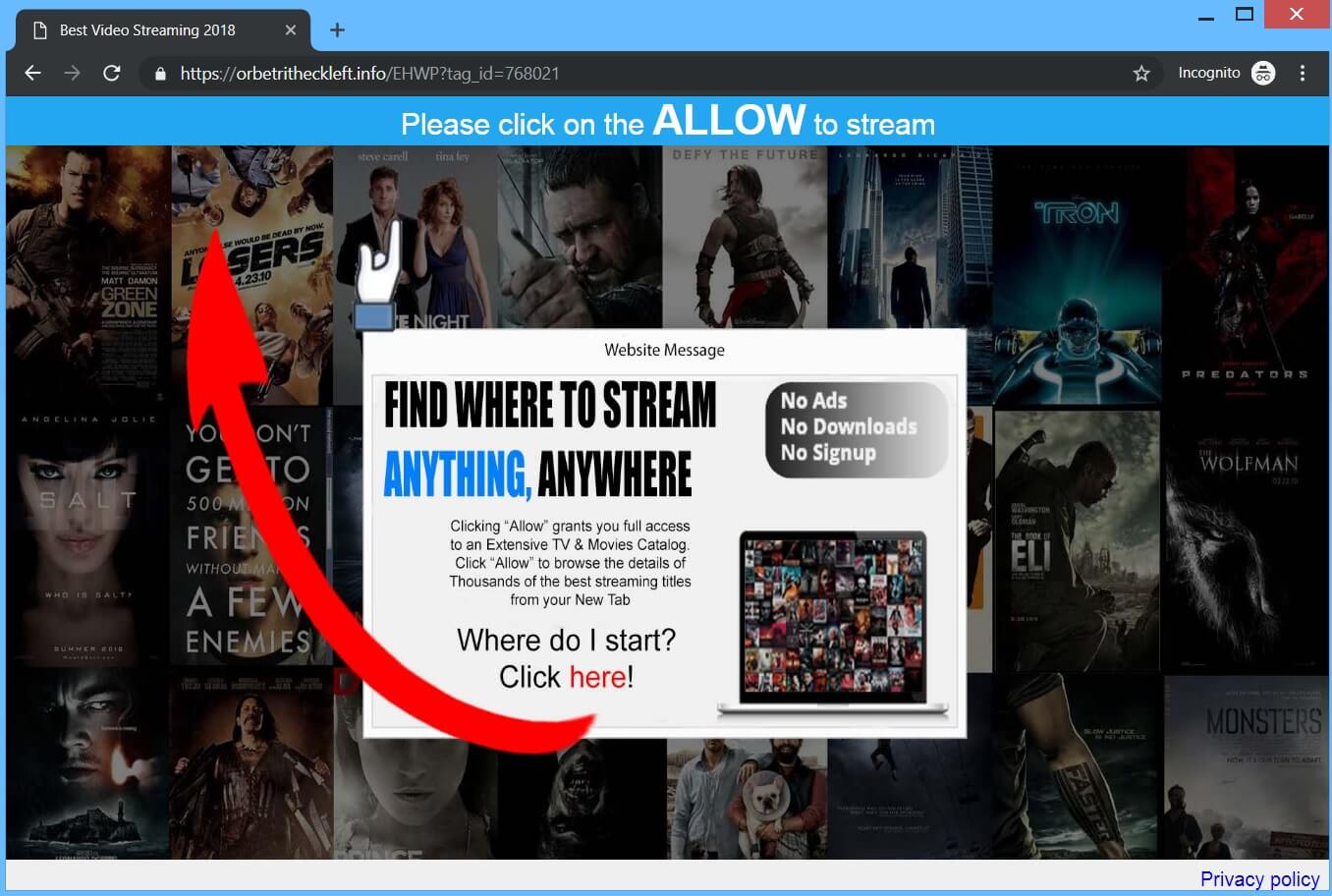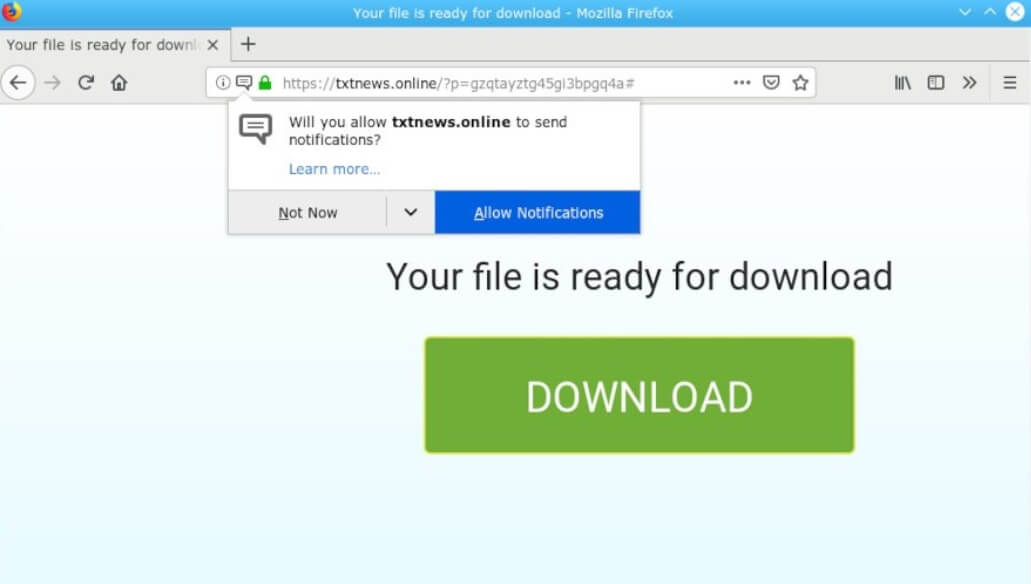
Remove Txtnews.online Redirect
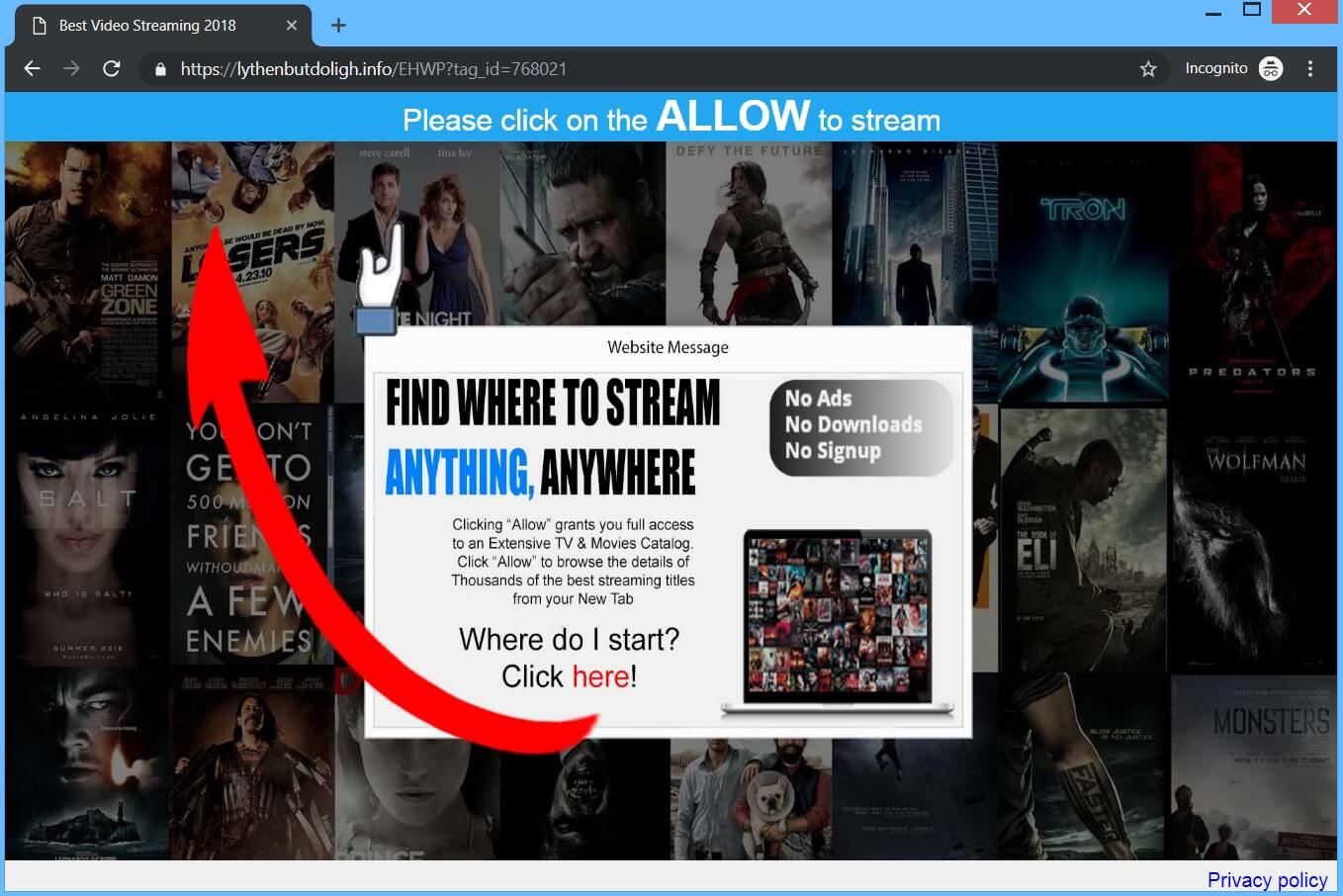
Can Txtnews.online pop-ups affect your browser? Is Txtnews.online a redirect? Does Txtnews.online spam you with pop-up ads? How to remove Txtnews.online redirect? Txtnews.online is a malicious URL address used for the purposes of redirecting users to sites containing spam, advertisements…