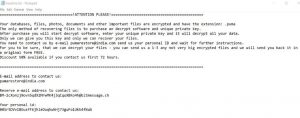
+1-877-842-2107 Comcast Call – Is It a Scam?
This information page has been created to explain whether or not you should trust calls coming from +1-877-842-2107 or if it is a scam number or no. People have summed up online complaints about calls coming from +1-877-842-2107, claiming to…