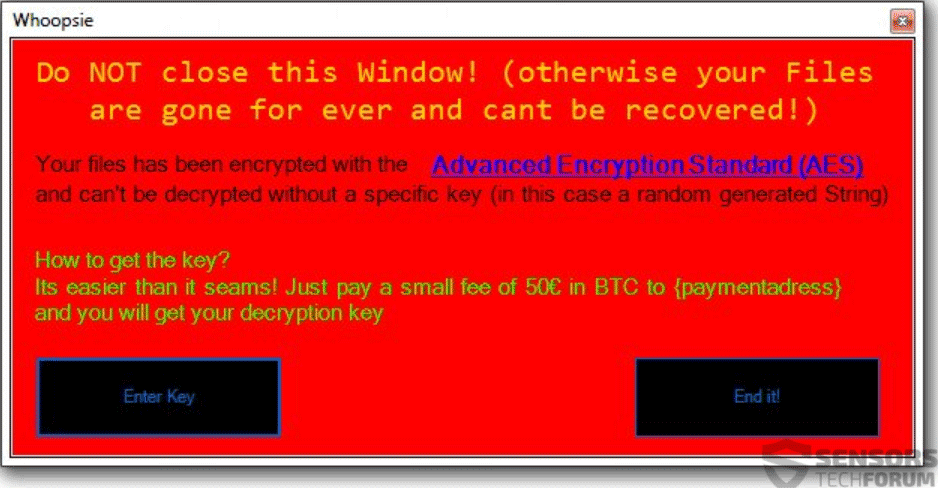
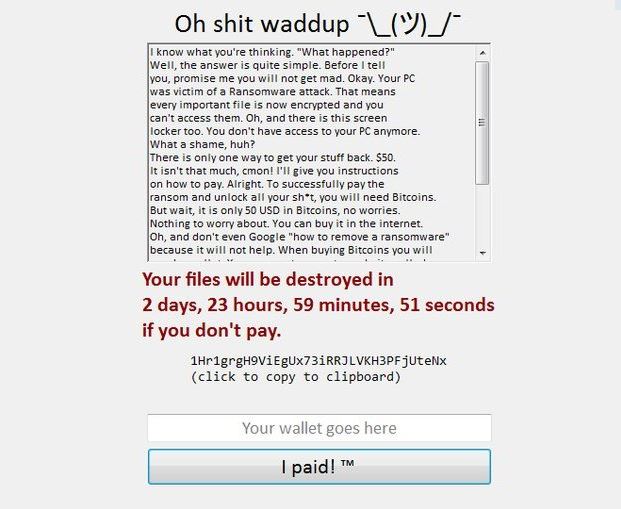
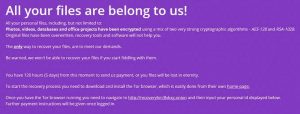
July 2018 Patch Tuesday Fixes CVE-2018-8281, Microsoft Office Bugs
Another set of patches has been rolled by Microsoft in the form of July 2018 Patch Tuesday. The patch batch contains a total of 54 vulnerabilities of which 17 are rated critical. 15 of those critical CVEs belong to Microsoft’s…







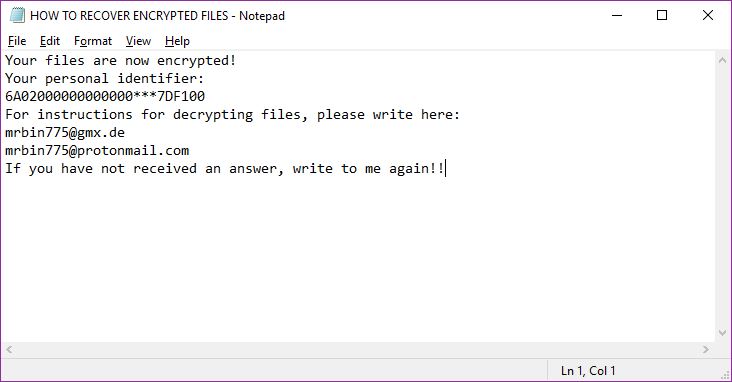
![Remove Everbe Ransomware – Restore .[eV3rbe@rape.lol].eV3rbe Files](https://cdn.sensorstechforum.com/wp-content/uploads/2018/07/stf-everbe-ransomware-virus-how-to-remove-and-restore-eV3rbe-files.png)