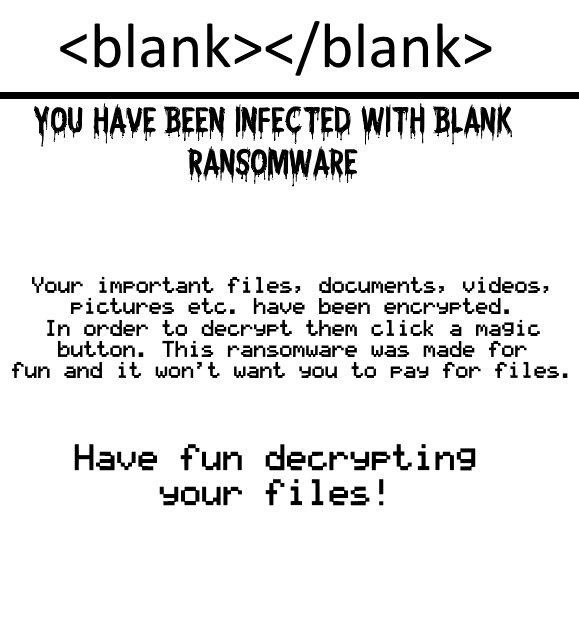
Topher Crypter Virus — How to Detect and Remove It from Your Computer
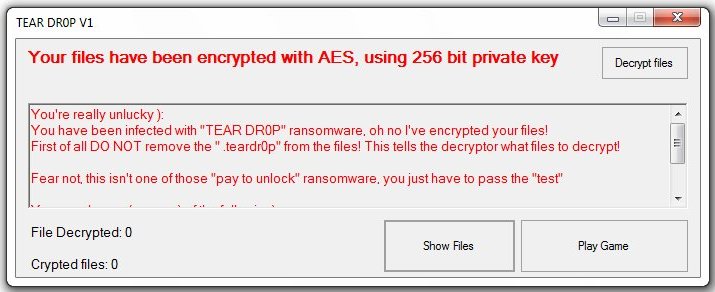
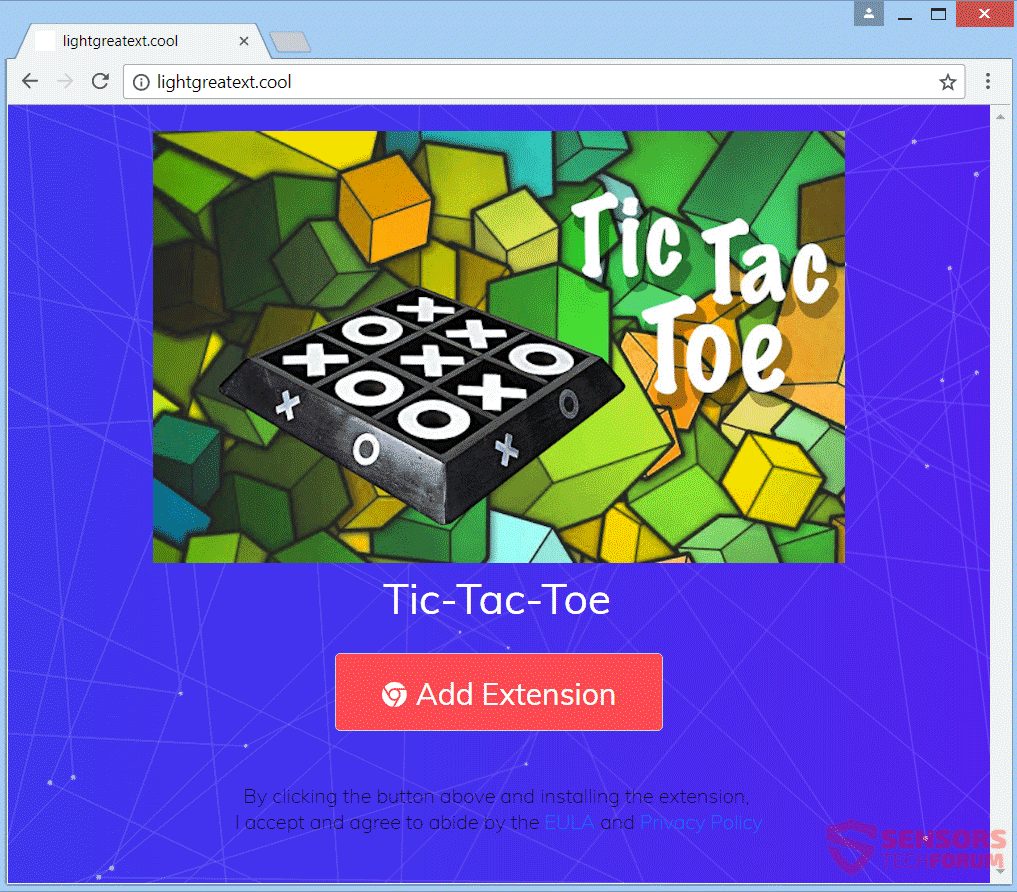
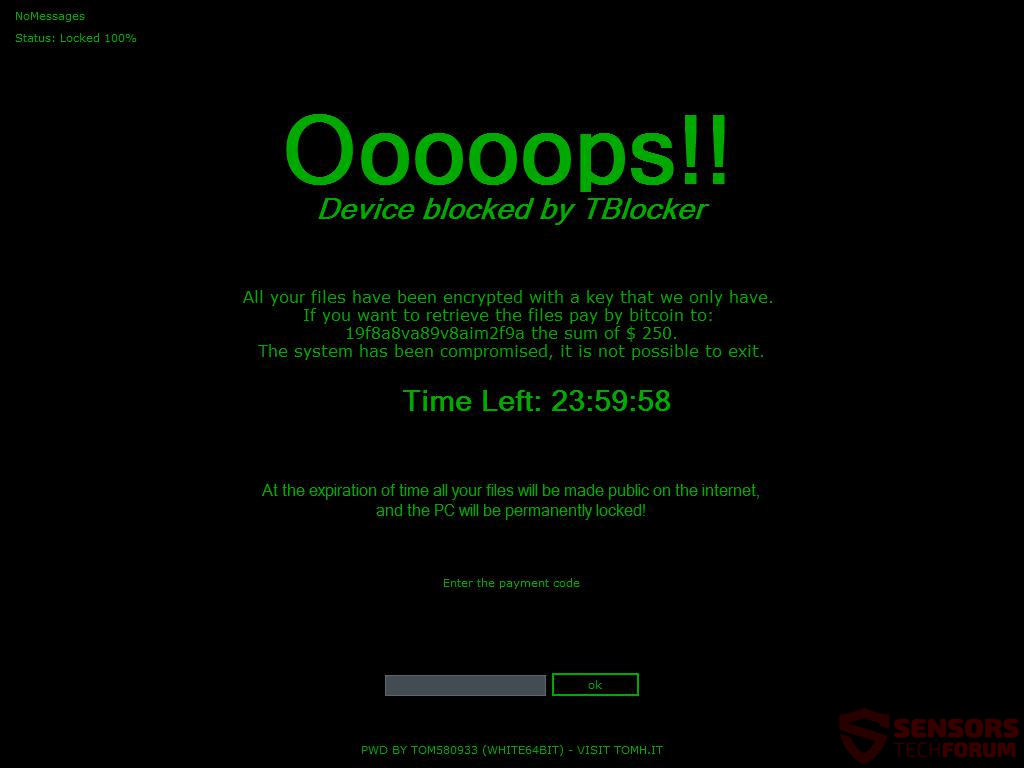
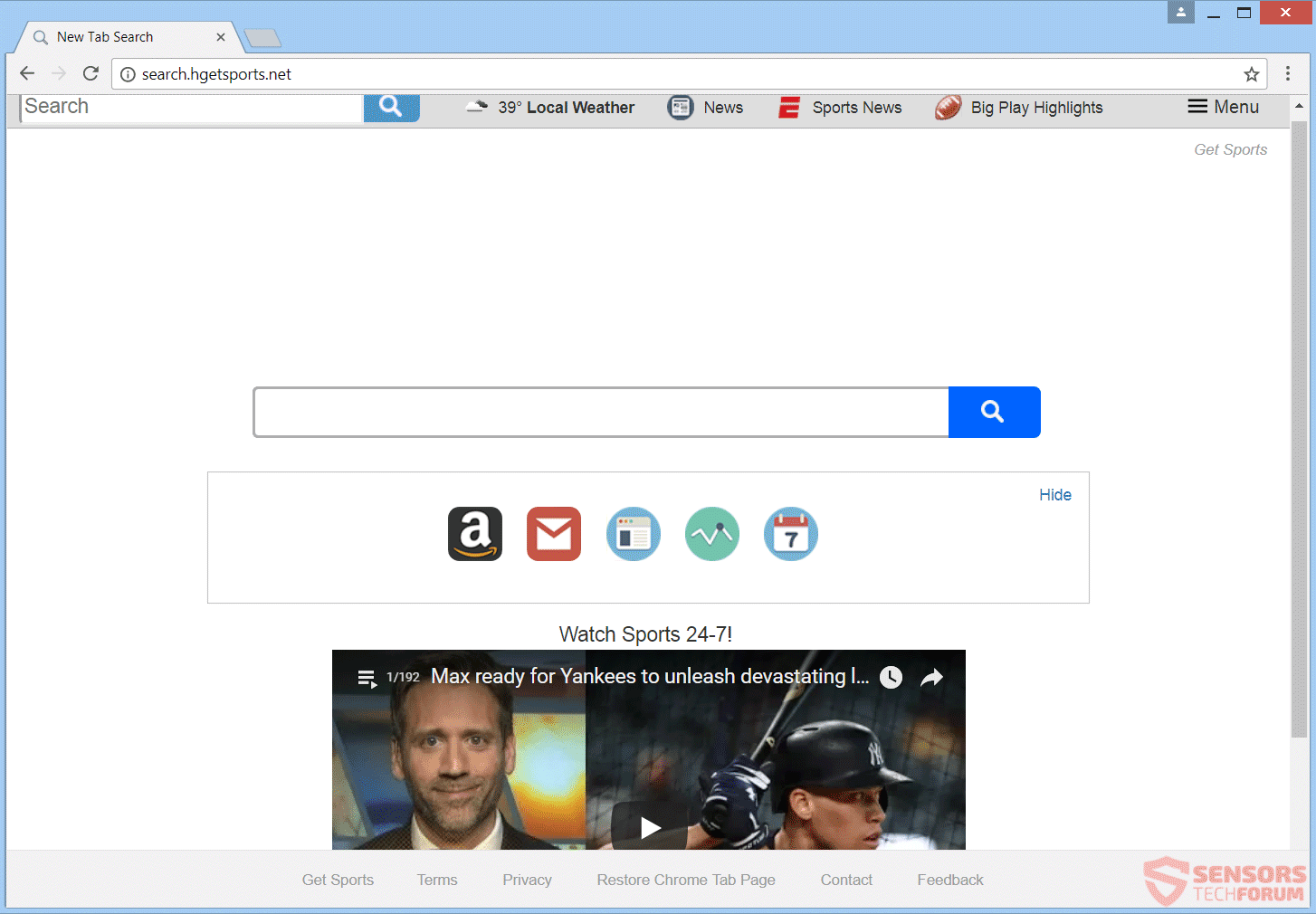
The TOPHER Crypter virus is among the most dangerous hacking tools of late. It provides the most advanced infiltration options and can completely take over the victim computers leading to further virus infections. In the majority of cases may not…